Cybersecurity andcloud computing assignment on cloud-based security incidents at Kaseya
Question
Task: In your cybersecurity andcloud computing assignmentcollect as much information as possible on new case of cloud-based security incidents from reliable news sources. Use publicly available cybersecurity knowledge base and hypothesis on 2 possible reasons of cloud-based security incident, considering the timeframe of the incident and the date of vulnerability disclosures. Propose two preventive measures, mention rationale for each with description.
Answer
1. Introduction
Cybersecurity entails defending vital data and equipment against online assaults. It is a crucial component of businesses that gather and maintain big databases of consumer information, social media sites where users input their personal information, and government entities that deal with secret, political, and defense material. As per the findings in thecybersecurity andcloud computing assignmentit explains how sensitive government information and personal data are shielded against assaults that might compromise crucial data, whether it is stored locally or across a variety of networks, apps, and devices. To safeguard data & technology, cloud computing environments must follow best practices for authenticated users and permissions, software and hardware privacy, encryption, firewalls, and other safeguards.A branch of cybersecurity-focused to protecting cloud-based systems is called cloud security, also referred to as information security. To safeguard the reliability and privacy of cloud data, technology, applications, and systems protocols, techniques, frameworks, and protocols are all part of cloud security.It is found in the cybersecurity andcloud computing assignmentthat the security safeguards in place maintain regulatory compliance, safeguard data privacy, offer control, manage data security, and regulate identification and data access.Tools, information, and technology are essential for cloud cybersecurity to safeguard cloud applications and systems from online threats. Clients in an organization only have access to the data they require to accomplish the tasks at hand thanks to the concept of least privilege. It is found in the cybersecurity andcloud computing assignmentthat this becomes much more crucial as a business grows and additional employees are hired to access data and complete tasks. To ensure that only the proper individuals have access to the right data, the system administrators establish access limits.
The purpose of this cybersecurity andcloud computing assignmentis to highlight points of cybersecurity and cloud computing and their model and standards. The purpose of this cybersecurity andcloud computing assignmentis to research one case study that discusses the cloud-based security incident of 2021-2022.
Model and Standard of Cybersecurity in the cybersecurity and cloud computing assignment
An organization might employ a collection of rules or best practices known as a cybersecurity standard to strengthen its cybersecurity posture. Cybersecurity standards can be used by businesses to assist them to identify and put in place the right defenses against online threats to their systems and data [6].
ISO 27000: One of the common requirements that a company must follow to create a management system for information security is this one. It consists of a collection of guidelines outlining the rules and conditions that must be met before the organization can be certified by this standard. According to this guideline referred to for thecybersecurity andcloud computing assignment, the firm must maintain its technology at the most recent version, ensure that its servers are secure, and undergo periodic audits to remain compliant. The ISMS policy, which is covered by ISO 27001 practice, must be followed by every organization that provides services to other organizations that comply with the international standard.
PCI DSS: Payment Card Industry Security Standards Standard is referred to as PCI DSS. When accepting payments through their payment gateway, an organization is required to use this standard. Businesses that keep customer information like names and card numbers must implement this standard across their operations. According to this compliance referred to for the cybersecurity andcloud computing assignment, the organization's technology should be current, and its system should regularly go through a security review to make sure it doesn't have any serious vulnerabilities. The group of card brands created this standard.
HIPPA: Health Insurance Portability Act is referred to as HIPAA. It is the norm that hospitals are expected to adhere to guarantee that the information about their patients is completely secure and cannot be compromised in any way. To meet this criterion for the cybersecurity andcloud computing assignment, the hospital must possess a robust network security team that handles all security events, have solid quarterly security reports, conduct all transactions in encrypted mode, and other requirements. This criterion guarantees that the patient's sensitive health information will be kept secure, allowing them to feel secure about their health.
FINRA: The Financial Industry Regulation Authority is known by the initials FINRA. Keeping things secure for financial institutions that manage money or actively engage in financial transactions is the main goal of this standard. The system as per cybersecurity andcloud computing assignmentfindings must adhere to this standard's strict security requirements, and to do so, several precautions regarding user privacy and data security must be considered. All businesses based on money are expected to adhere to these criteria, which are among the most important ones. GDPR: Known as GDPR, this regulation governs data protection. The European Union government, which cares about the privacy of all users, established this guideline. The organization in charge of overseeing compliance with this standard is required to make sure that user data is safe and cannot be accessible without the right authorization. According to its name, this standard mentioned in the cybersecurity andcloud computing assignmentprimarily focuses on the security of the operating system so that they can feel comfortable sharing it with any businesses that are following the Data Protection Regulation.
Cloud-Computing discussed in the cybersecurity and cloud computing assignment
A collective pool of adaptable computing resources (such as connections, servers, storage, programs, and services) The cloud computing approach makes it possible to swiftly deploy and release applications with no administrative labour or service provider participation. There are three standards of cloud computing IaaS, PaaS, and SaaS mentioned in the cybersecurity andcloud computing assignment[4].
IaaS: IaaS stands for access to computer infrastructure, which includes servers, storage areas, and networking resources, that is in the cloud. It is found in the cybersecurity andcloud computing assignmentthat customers may set up, customize, and employ IaaS resources as they see fit. like how they would use on-premises hardware. The provider of cloud-based services is different in that it hosts, controls, and maintains the computational and hardware resources within its data centers. Customers who utilize IaaS access the hardware through an internet connection and pay a subscription or per-use fee for it.
PaaS: PaaS offers a platform in the cloud for managing, building, and running software. servers, as well as all the platform's software and hardware components operating systems, flash memory, connectivity, database management systems, middleware, runtimes, and paradigms, and The cloud service provider oversees and maintains the development tools. They also provide services related to security, able to operate system and software improvements, backups, and other things.
SaaS: Application software that is hosted in the cloud and is ready to use is known as SaaS (or cloud application services). It is fund in thecybersecurity andcloud computing assignmentthat the users who wish to access a full program from an internet browser, desktop client, or mobile app must pay a recurring or annual price. The SaaS provider hosts and manages the application in addition to the entire delivery infrastructure, including servers, storage, middleware, connectivity, software applications, and data storage.
2. Case Detail Discussion
One of the IT solutions offered by Kaseya is VSA, unified remote monitoring as well as management software for managing endpoints and networks. The business also offers professional services management platforms, service desks, and compliance solutions.Over 40,000 organizations worldwide are reportedly using at least one Kaseya software solution. The company's product is made with businesses and managed service providers (MSPs) in mind. Kaseya addressed in the cybersecurity andcloud computing assignmentis a key component of a larger software supply chain because it offers technologies to MSPs, which give services to other businesses[5].On July 2, 2021, Kaseya turned down its SaaS servers and advised its VSA clients to do the same with their on-site VSA servers. Although Kaseya claims there is no proof that any of its SaaS clients have been compromised, it has taken the SaaS servers down out of an excess of caution [7].
3.1 Possible Reason
A ransomware assault that Kaseya, a provider of IT solutions, suffered on July 2, 2021, put thousands of their MSP clients' clients at risk. Hypothetically there are 2 possible reasons for cloud-based security incidents including Weak IAM policies and Misconfigurations.As per the Palo Alto Networks, the numbers of susceptible Kaseya servers that were active, accessible, and available to attackers decreased by 96% from about 1,500 on July 2 to 60 on July 8.
Weak IAM Policies: Because cloud applications are accessed online, hackers only need your credentials to obtain the "keys to the kingdom" with everyone in a cloud environment. Each user in cloud infrastructure has responsibilities and permissions that govern the accessibility they get to certain sections of the cloud. That is the reason why a strong IAM policy is important. Controlling user access and permissions to cloud resources is accomplished through identity and access management. IAM can be viewed as a structure of procedures, rules, and technological advancements rather than as a single software program. Palo Alto Networks mentioned in the cybersecurity andcloud computing assignmentclaims that credential leaks or improperly set IAM policies are the origins of the most well-known cloud data breaches. Researchers discovered that IAM misconfigurations account for 65% of cloud data breaches that have been identified. Poor password usage (53%) and permitting password reuse (44%) came in second and third, respectively.This can be avoided by creating a new access key, updating the application so that it can be used by the updated access key, making the old key inactive by disabling it and after ensuring that the application is accessed by the new access key deleting the old key so that there should be no history of the old key or any risk of accessing the application by the old key or resetting the access key by the help of the last access key.
Misconfigurations: According to VMware's 2021 Condition of Cloud Computing report, one out of every six firms questioned had cloud unauthorized access caused by configuration errors in the previous year. Researchers from other institutions discovered that cloud storage had one of the highest rates of misconfiguration out of all cloud services. Given this in thecybersecurity andcloud computing assignment, it is not unexpected that there are numerous data breaches involving cloud storage in recent years. Just one year ago, approximately 1,000 GB of information and more than 1.6 million data from numerous US towns were exposed due to improperly set up Amazon S3 buckets. Microsoft Azure hasn't fared any better. In 2021, incorrectly designed Azure storage accounts revealed files exposing critical information.Misconfiguration can be avoided in several ways, some of the important ways are like, limiting access to the admin interface means only limited parties should have the access to the admin interface. As per the cybersecurity andcloud computing assignment it can also be prevented by disabling debug, disabling the directory list, the patch ad software should be updated regularly, unused features should be removed regularly, using automation for advantages like running scans, performing audits to find the missing patches, misconfigurations etc.
3.2 Resources mentioned in the cybersecurity and cloud computing assignment
CISA makes these resources available to readers for their knowledge. CISA neither recommends nor attests to the veracity of every non-governmental organization or the associated resources.
3.3 Protocols for General Ransomware Security
To reduce the chance posed by ransomware and support any organization's coordinated and effective reaction to a ransomware event, CISA advises companies—including MSPs—to apply the best practices and hardening advice in the CISA and MS-ISAC Joint Ransomware Guide[1].
3.4 Recommendation
Recommendation approaches to cyber security and cloud computing will vary depending on the specific needs of the organization in question. However, some general recommendations for improving cyber security and cloud computing are mentioned in the cybersecurity andcloud computing assignment:
Two preventive measures of Weak IAM Policies:
Make multi-factor authentication mandatory: In order to access a resource like an application, an online account, or a VPN, the user must first authenticate using MFA, which calls for two maybe more verification factors. MFA is a crucial element of a solid identity and access control (IAM) policy. MFA requests one or more extra verification elements, which reduces the possibility of a successful cyberattack, as opposed to only requesting a username and password.
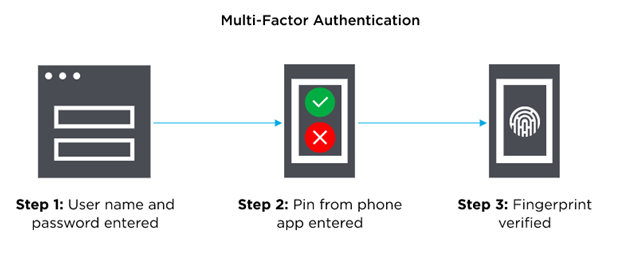
[8] When using long-term credentials, rotate access keys frequently: The advice is for organizations to routinely replace IAM user access credentials as a result of activities [9]. As per thecybersecurity andcloud computing assignmentyou can change your own access keys if your administrator has given you the required permissions.For the passwords of your IAM users, Kaseya can define a specific password protection on their service account that outlines complexity requirements and required rotation intervals. IAM user credentials must adhere to the standard Kaseya web security protocols if a custom identity management hasn't been configured by Kaseya.
Preventing Measures of Misconfigurations in the cybersecurity and cloud computing assignment
Training and Education: Typically, education is the first stage in this process. Ensure that everyone on the team is aware of the value of security and how to spot unsafe procedures [10].Teams should be completely aware of their roles and duties after training, as well as who to contact with any security concerns and where to look for more security information.
Don't let configurations depend on luck: As much as feasible, strive to prevent misconfigurations from ever happening by deleting pointless or potentially susceptible options.For instance, you might reduce system traffic by using whitelisting or uninstalling frameworks or tools that you aren't using.
1. Conducting a risk assessment to identify potential threats and vulnerabilities.
2. Implementing security controls and countermeasures to mitigate identified risks.
3. Monitoring and auditing system activity regularly.
4. Educating employees about cyber security best practices.
5. Keeping up to date with the latest security threats and trends.
3.5 Pros and cons
The cybersecurity andcloud computing assignmenthas found several pros and cons to ransomware attacks on cloud computing. One of the biggest pros is that it can significantly reduce the amount of time it takes to recover from an attack. Additionally, it can also help to prevent future attacks by making it more difficult for attackers to gain access to sensitive data. However, there are also several cons associated with this type of attack. One of the biggest cons is that it can be difficult to determine which files have been encrypted and which have not. Additionally, if an attacker can gain access to the encryption key, they may be able to decrypt the entire dataset, which could lead to serious data loss.
3.6 Learning experiences for Kaseya
Investigations into the full consequences of this occurrence are mostly ongoing. Nevertheless, these are a few takeaways from this episode so far and some general advice[2].Kaseya's openness, the audacious choice to bring down its whole SaaS infrastructure, and the prompt contact with customers all suggest the business is carrying out planned reaction planscreated for this kind of attack. Furthermore, it appears that the plan has been implemented promptly, probably because ofthe training program and readiness.
The following list of inquiries mentioned in the cybersecurity andcloud computing assignmentis for businesses to use the next time they are worried about a cyberattack that has garnered international attention:
• What information are the attackers seeking?
• Can we recognize the danger actor or just a broad profile?
• What development or effect is already known to the general public?
• Is our emergency response strategy prepared to help stop or lessen this kind of incident?
3.7 Consideration of cloud tenants in a multitenant environment.
Security and privacy are of great concern to cloud users. Data security is a complex
multidisciplinary field, and data security in cloud environments is even more challenging[3]. The security threat landscape is changing rapidly, and traditional security mechanisms may not be effective in cloud environments. Hence, a new set of mechanisms is needed to protect data in the cloud. Data security in cloud environments must consider data security mechanisms in both public and private clouds. Further, the data security mechanisms mentioned in thecybersecurity andcloud computing assignmentmust also consider the characteristics of cloud systems, cloud services, and cloud data. There are many types of data security mechanisms, including access control, authentication, encryption, audit and logging, intrusion detection, and so on. In cloud environments, identity management and access control are of particular concern. In cloud environments, identity management and access control are of particular concern. Identity management systems are used to identify end-users and to verify the authenticity of the identity. The identity management system must be able to manage identities in a centralized way.
4. Security model and its framework
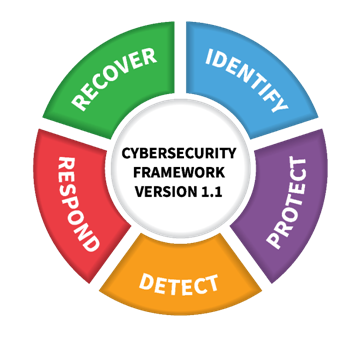
Kaseya is using NIST security model to balance betweenfast changing cyber threat landscape and the need to meet business requirements. This company use this model to manage the risk of cybersecurity and uses cybersecurity framework that addresses threats and aids business. This security model mentioned in thecybersecurity andcloud computing assignmentofferscommon vocabulary that enables employees at all organizational levels and at all links in a supply chain to come to a mutual awareness of their cybersecurity threats. The Framework was developed by NIST in collaboration with Kaseyaand governmental professionals and launched in the beginning of 2014. The 2014 Cybersecurity Enhancement Act recognized the project as a NIST duty because the effort was so successful. This framework includes identification of risk, protect the data from risk, detect the prevention to reduce risk, give a response and finally recover the data from risk.
[11]
5. Conclusion
The conclusion of this cybersecurity andcloud computing assignmentis to identify cyber security and cloud computing according to the given case study. Cybersecurity entails defending vital data and equipment against online assaults. To safeguard data & technology, cloud computing environments must follow best practices for authenticated users and permissions, software and hardware privacy, encryption, firewalls, and other safeguards. In the given case study, the report focuses on the cloud-based security incident at Kaseya Company. ISO 27000: One of the common requirements that a company must follow to create a management system for information security is this one. It consists of a collection of guidelines outlining the rules and conditions that must be met before the organization can be certified by this standard. The Kaseya Company is for managed service providers (MSPs) and small to medium-sized organizations, Kaseya is a leading provider of unified IT management and security software (SMBS). There are different types of cloud services like paas, iaas, and saas.A ransomware assault that Kaseya, a provider of IT solutions, suffered on July 2, 2021, put thousands of their MSP clients' clients at risk. Thus, this cybersecurity andcloud computing assignmentconcludes with the cyber security and cloud-based system.
6. References
[1]j.sattler, "The Kaseya ransomware case continues ransomware groups' abuse of trust - F-Secure Blog", F-Secure Blog, 2022. [Online]. Available: https://blog.f-secure.com/the-kaseya-ransomware-case-continues-ransomware-groups-abuse-of-trust/. [Accessed: 15- Oct- 2022]
[2]c.osborne, "Updated Kaseya ransomware attack FAQ: What we know now", ZDNET, 2022. [Online]. Available: https://www.zdnet.com/article/updated-kaseya-ransomware-attack-faq-what-we-know-now/. [Accessed: 15- Oct- 2022]
[3]2022. [What Is Cloud Computing and the Top Cloud Technologies to Look Out for in 2022
By Simplilearn]. Available: https://www.simplilearn.com/cloud-technologies-article . [Accessed: 15- Oct- 2022]
[4]D. MacRae, "81% of companies had a cloud security incident in the last year", Cloud Computing News, 2022. [Online]. Available: https://www.cloudcomputing-news.net/news/2022/oct/03/81-of-companies-had-a-cloud-security-incident-in-the-last-year/. [Accessed: 15- Oct- 2022]
[5]J. Wendt, "Kaseya’s CEO Response To Its Current Ransomware Attack - DCIG", DCIG, 2022. [Online]. Available: https://dcig.com/2021/07/kaseyas-ceo-response-ransomware-attack/. [Accessed: 15- Oct- 2022]
[6]C. Tunc, S. Hariri, F. De La Peña Montero, F. Fargo, P. Satam and Y. Al-Nashif, "Teaching and Training Cybersecurity as a Cloud Service," 2015 International Conference on Cloud and Autonomic Computing, 2015, pp. 302-308, doi:
10.1109/ICCAC.2015.47.https://ieeexplore.ieee.org/document/7312173
[7]2022. [Important Notice August 4th, 2021]. Available: https://helpdesk.kaseya.com/hc/en-gb/articles/4403440684689-Important-Notice-August-4th-2021 . [Accessed: 15- Oct- 2022]
[8]B. O. ALSaleem and A. I. Alshoshan, "Multi-Factor Authentication to Systems Login," 2021 National Computing Colleges Conference (NCCC), 2021, pp. 1-4, doi:
10.1109/NCCC49330.2021.9428806.https://ieeexplore.ieee.org/document/9428806
[9]N. Djosic, B. Nokovic and S. Sharieh, "Machine Learning in Action: Securing IAM API by Risk Authentication Decision Engine," 2020 IEEE Conference on Communications and Network Security (CNS), 2020, pp. 1-4, doi: 10.1109/CNS48642.2020.9162317.https://ieeexplore.ieee.org/document/9162317
[10] S. Maroofi, M. Korczyski, A. Hölzel and A. Duda, "Adoption of Email Anti-Spoofing Schemes: A Large Scale Analysis," in IEEE Transactions on Network and Service Management, vol. 18, no. 3, pp.
3184-3196, Sept. 2021, doi: 10.1109/TNSM.2021.3065422.https://ieeexplore.ieee.org/document/9375477
[11] NIST releases version 1.1 of its popular cybersecurity framework. NIST. (2022, June 13). Retrieved November 1, 2022, from https://www.nist.gov/news-events/news/2018/04/nist-releases-version-11-its-popular-cybersecurity-framework
https://www.nist.gov/news-events/news/2018/04/nist-releases-version-11-its-popular-cybersecurity-framework












