data privacy policy assignment on data privacy policy development using POPIA act guidelines
Question
Task: How to enhance data privacy using data privacy policy assignment research methodologies
Answer
1. Introduction
As per the data privacy policy assignmentdescriptions, The POPIA Act defines certain material considered "special personal information," which includes a database subject's religious and intellectual views, cultural background, political affiliations, policy position, medical and sometimes sexual relationship, or confidential information (Qin et al., 2021). This section includes suspected illegal crimes as well as legal processes relating to them. In principle, South Africa should receive the user's permission before processing "special personal information." In order to minimise confusion, there must be express permission which includes these precise details. Privacy remains a basic principle that has grown into a heated subject as the internet age has progressed, including individuals consciously, or rather sometimes inadvertently, exposing a vast amount of private material electronically. Controlling privacy seems difficult, given fresh websites appearing on a daily basis plus clients situated across the world, wherein privacy rules differ widely. Individuals who operate websites that collect confidential details must do their part by adopting extensive or perhaps obviously visible protection for private information. Such a privacy plan comprises a declaration that explains why an organization's website would collect, store, secure, and manage personal information supplied by its consumers. The data privacy policy assignmentoutlines how Each South African firm must conform to the Personal Data Protection Act (POPIA), sometimes known also as POPIA Act. Whilst the POPIA Act concentrates on compliance, their method aims to implement rules in a way that creates firm advantage rather than establishing a profit centre or hardship, while also enabling advances in productivity and efficiency while fulfilling mandated standards. The goal of this investigation study includes determining whether South African organizations' webpage (digital) privacy rules (security notifications) conform to data confidentiality standards as well as giving suggestions for improving them.
2. Research Problem
The POPI Act compels enterprises throughout South Africa should restrict their usage of private information, obtain permission prior to utilizing data, as well as allow customers to revoke the agreement at any time. In order to ensure "knowledge," permission, companies in South Africa must disclose various information, which is better accomplished via a Privacy Statement (Swales, Thaldar and Donnelly, 2022). According to POPIA Act, one cannot handle confidential details about a person until this is required by law or users obtain the agreement of that particular individual. Whereas the POPIA Law doesn't really acquire the necessary Privacy Statement, posting such has been the greatest effective approach to meet the transparency as well as permission standards (Swales, Thaldar and Donnelly, 2022).
As per the data privacy policy assignmentfindings, Websites must additionally guarantee that specific conditions for such collection of personal data through webpages, as outlined inside the digital security policies, are satisfied. This Internet Types of Contracts is a legislative document that sets the contract terms that users must adhere to when using the service (Van Niekerk, 2019). Regulations such as POPIA don't really contain privacy standards for interactive web practices. However, there's no uniform or comprehensive collection of standards that specify what should have been contained within the website's personal information.
Regulations such as POPIA don't really contain privacy criteria regarding online website rules. There isn't a uniform or comprehensive collection of specifications that determine what should be contained inside a webpage privacy statement. Companies have been presently grappling with legislation requiring written consent, why to address a compromise if one occurs, privileges to private data privileges, how the company manage customer enquiries as well as staff development, as well as how select the job of the authorized privacy commissioner. They need sufficient supervision, and possibly the dearth of corporate mechanisms to support them achieve alignment towards POPIA. Companies generally do not have the understanding to handle compliance with regard to the safety of private details that they retain. POPIA certification presents several challenges that have an influence on the regional economy. The main issue identified on this data privacy policy assignmentis the way organizations handle as well as keep information; many South African firms currently save paper documentation. It's indeed tough to maintain and remain compliant when information is saved upon paper as well as preserved in several locations. The other factor concerns South African customs, wherein businesses are accustomed to keeping the information in conventional methods. Because of reliance on outdated storing plus administration methods, there is a reluctance to technologies.
3. Research Objective and Research Questions
data privacy policy assignmentResearch Objectives
To investigate the aspects of a website privacy policy should include addressing privacy principles
To examine aspects that are required to address South African website privacy policies principles
To explore strategies South African website owners (organisations) do to improve their website privacy policies.
Research Questions
1. What aspects should a website privacy policy include to address privacy principles
2. Do South African website privacy policies include the aspects that are required to address privacy principles
3. What can South African website owners (organisations) do to improve their website privacy policies
4. Background
Privacy
As per the data privacy policy assignmentinvestigations, the POPIA Act is been brought into legislation in early 2013, however, implementation is already, to put it mildly, delayed. This became primarily due to problems with establishing the Communications Commissioner, which would supervise laws and implementation.
Policy
The organization is currently in effect, including several of its particular guidelines that have been issued (Van Niekerk, 2019). As a result, full implementation is anticipated to follow immediately, and companies must plan to commence completely compliance with its legislation.
Online Privacy Policy
The Online Privacy Policy includes a legislative statement that appears upon that business's webpage and describes how the organization controlling the webpage collects, analyses, explains, as well as maintains the customer's as well as user information. SA wishes to reconcile their valid commercial objectives with customers' justifiable assumptions about privacy by establishing this Privacy Policy. Also, as result, SA would undertake necessary measures to protect against unauthorized entry towards or exposure of customers' Private Details.
Purpose
This Protection of Personally Data Act applies to every general populace as well as commercial organizations within South Africa (POPIA). Personally identifiable information handling throughout all media should comply with its eight standards under POPIA as well as the extra standards. It thus encompasses both printed versions but also electronic private details handling, together with personal data handling via webpages. The data privacy policy assignmentresearch shows that Websites must include a digital privacy strategy, rules as well as restrictions, and perhaps a security statement that informs customers about the way their private data would be treated as well as safeguarded. Webpages must also guarantee that specific conditions for such handling of private material through websites, as outlined within digital privacy policies, have been satisfied.
Consumer Privacy Concern
The vast plurality of customers (87%) indicated people wouldn't do commerce with the firm when they were concerned regarding its privacy policies. 71% stated consumers would cease conducting commerce using a firm if something handed confidential material around without consent (Rath and Kumar, 2021). Just around 10% of customers, for instance, respect consumer packaging products or multimedia as well as entertainment corporations.
Issues
Customers want businesses to protect personal confidentiality. However, the actuality within South Africa is rather the opposite. A major data compromise exposed the sensitive details of hundreds of thousands more South Africans. There exists a significant gap between what customers anticipate as well as what is perfectly allowed to with the work organizations undertake to satisfy their commitments.
5. Literature Review
The data privacy policy assignment research will be conducted in a scoping literature review. Scoping reviews provide an initial evaluation of the possible amount but also breadth of existing study material. As opined by L. Haven and Van Grootel, (2019) the purpose of this study is to determine the kind and breadth of empirical proof. Scoping reviews constitute a way for fully mapping information along a variety of methodological approaches during a specific region in order to shape potential research practices, initiatives, as well as policies. Furthermore, there isn't a uniform consensus on nomenclature, definitions, or procedural stages. The goal aims to learn about the perspectives as well as concerns for undertaking scoping studies through academics as well as social peers. The primary goals became to explain scoping study findings, covering advantages as well as problems, as well as viewpoints on vocabulary, definitions, as well as methodology processes. As per Rethlefsen et al., (2021), Scoping reviews constitute a way for fully mapping findings along a variety of different studies inside a region in an attempt to shape future studies practices, and initiatives, as well as legislation. Nevertheless, there isn't any uniform consensus on nomenclature, definitions, or procedural stages. Scoping reviews have been employed to uncover expertise shortages, define research objectives, plus highlight decision-making consequences. In research, there is inconsistency within execution as well as interpretation of scoping reviews. Researchers did a scoping review aimed to locate articles that used both detailed scoping review procedures, documenting requirements for conducting scoping reviews, plus investigations which evaluated the accuracy of scoping review findings.
The PRISMA Statement's goal identified on this data privacy policy assignment intends to assist writers in improving the documentation of comprehensive preferred reporting items for methodology. Figure (1) demonstrates how the PRISM method provides an innovative principle-based technique that employs a significant technique to integrate sustainability throughout the project's lifetime. As opined by Church et al., (2020), PRISMA might be beneficial for evaluating available published assessments. This PRISMA checklist, on either hand, isn't really a proper evaluation tool for determining the validity of one comprehensive study. The inclusion criteria for the journal include the databases are of from Scopus, IEEE and from ScienceDirect. However, the fourth database that is included in the research paper is the Internet as grey literature. The keywords for the journal search include “privacy”, “policies”, “website privacy”, and/or “POPIA Act”. The journalsare not older than 5 years of its issue, and they are written in English so a mass population can understand. The exclusion criteria, however, includes paper that is not relevant to the study at all and further create misunderstandings about the content inside them, such as privacy in medical field or privacy of children or patients’ information. The information is collected from various journals on Google Scholar. The information was first collected then the researcher examines the entire information in order to get familiar with the information and grasp it thoroughly. After examining the information, the researcher analysed the data to present it in the research. The data privacy policy assignmentresearcher pays great consideration that the information is not biased, and further does not create misunderstandings or provide wrong pieces of information.
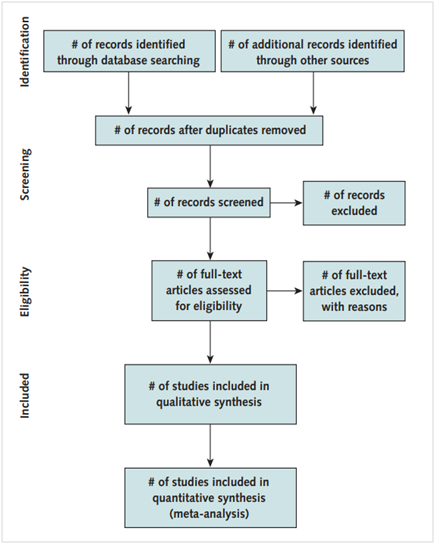
Figure 1: The PRISMA method
Source: (Church et al., 2020)
5.1 Website Requirements Explanation
The researcher selected 10 journals, in the final analysis, to effectively conduct the research on the website privacy policy criteria requirements. The website demands organisations as well as organizations to use extreme caution whenever acquiring as well as presenting unique private information. This journals clearly state that the privacy policy should define the material gathered, the objective for which the material will be used, toward whom or why the material will be disclosed, and the acceptable protection methods that will be used to protect this material.
|
Authors |
data privacy policy assignmentFindings |
|
(Verkijika and De Wet, 2018) |
Organizations should address their clients' privacy worries as well as verify that the techniques they employ to gather and maintain information comply respectively with this same regulation or their clients' standards. Compliant strategies developed by organizations that depend on worldwide best practices might be beneficial. |
|
(Hatamian et al., 2021) |
There is much concern over the confidentiality and safety elements of electronic connection tracing programs, coupled with their possible breach of rules governing consumer defence. As a result, the creators of such applications are continually chastised for violating customers' privacy, ignoring critical security but also confidentiality standards, and designing apps within strict deadlines without addressing privacy or safety through concept. |
|
(O’Brien et al., 2018) |
Customers should be informed about the grounds why personal information is getting accumulated and such amount of period it would be held. A monitoring authority shall be established to handle customers' concerns, including contacting data about this authority should be supplied. |
|
(Harkous et al., 2018) |
The substance for Privacy Policies differs from one company to the following. Each group's website gathers and maintains data differently, as does the way it communicates with other entities. Furthermore, the location of such webpage customers might have an influence upon that firm's Privacy Policy due to worldwide laws that safeguard worldwide customers. |
Table 1: Website privacy requirements
Source: Self-developed
As per Verkijika and De Wet, (2018), the firm webpage, that gathers certain anonymized data every moment a customer visits it, could enhance the general effectiveness of such a customer's web presence. Usually, whenever these privacy policy conditions are met many websites gather users' IP addresses, referrer information, or rather browsers but also system kind. Every firm must establish a privacy statement which is available via their webpage. This privacy policy should define the data gathered, the purposes for which the material will be used, toward whom but also where the material will be disclosed, and also acceptable protective measures that will be used to protect that content. As opined by,Hatamian et al., (2021) all enterprises and websites, including online firms, should use acceptable security standards or even processes when interacting with or acquiring private details. Furthermore, the organisation may acquire critical private material solely with the prior approval of such data's source. The website should additionally offer the consumer the alternative of not providing confidential material. Under a rather circumstance, the employer reserves the option to discontinue delivering the products or even activities requested. Every firm website must maintain a privacy statement which is available on the online website. Usually, websites must contain arrangements in conjunction with a piece of personal information.
As per Tesfay et al., (2018) Usually, websites must contain policies as well as guidelines in conjunction with the privacy statement. This Webpage Rules & Circumstances has been a legislative agreement which outlines the services as well as limitations that users should follow when accessing the webpage. Its webpage provisions as well as terms of the contract ought to contain a waiver of responsibility, an approved usage provision, a modification paragraph, a paragraph indicating the appropriate legislation as well as territory, as well as other contractual data in addition to such licensing of such copyrights inside the webpage. Such privacy laws must employ unambiguous as well as plain wording to guarantee that consumers, as well as website viewers, comprehend whatever personal details the firm gathers as well as how much material would be used. Privacy standards aren't just a smart method to develop confidence and openness amongst company consumers; they have been generally legally mandated as well as mandated by such a majority for third-party programs. Because digital privacy rules, as well as standards, operate across the entire planet, if such a webpage attracts customers who reside outside its region or nation, they must follow customers' national confidentiality rules in addition to their country. It's indeed critical and essential they examine the regulatory requirements relating to the consumer group to verify whether they're following the applicable legislation. Member nations enact digital data safeguards regulations, including a handful of government rules that provide a hodgepodge of customer procedural representation.
The data privacy policy assignmentresearch shows Establishing a clear privacy statement likewise aids in the development of public confidence. As opined by Isaak and Hanna, (2018) consumers would notice that the firm values customer knowledge but also sensitive material plus would welcome their readiness to follow rules together with their own openness in providing it simple to understand whatever knowledge the business collects plus how it does use information. Regardless of whether the business, as well as application, does not gather certain personally identifiable material, they should consider establishing such a privacy policy. Whenever consumers browse a webpage as well as an application, they anticipate encountering a privacy statement, therefore the absence of one may confound as well as misrepresent consumers. Alternatively, include a statement saying that no private knowledge is collected. Such privacy policy must be in place to safeguard everybody, including its website's operator as well as consumers. As a result, Sundler et al., (2019) such official papers must be taken care of by everyone. They must observe a certain collection of guidelines as well as privacy statement requirements every moment they produce privacy settings. They must even recommend obtaining counsel from several of those greatest internet legal assistants. Furthermore, websites must take caution neither to mix up privacy policies with additional comparable digital commitments as well as papers. Whereas if the webpage has to gather personal details using card payment services, then an effective privacy declaration must be developed. An appropriate internet shopping privacy policy, as an example, is required for an online marketplace.
5.2 Guidelines for suggested website privacy settings
• The mains issues identified on this data privacy policy assignmentis that Website policy should state that the business website would capture and process private material submitted to its customers, such as user usernames, domains, contact details, and mailing addresses. This must additionally state that such quantity of knowledge provided is entirely optional; nevertheless, submitting less knowledge may restrict a community's capacity in using many of this same site's services. According to O’Brien et al., (2018), alert the participants whether their organisation gathers consumption data necessary to analyse how visitors accessed or even utilise the website. As per Harkous et al., (2018), this information is useful to the organisation for such variety of business reasons, such as debugging as well as enhancing the web's operation. Feel independent to declare, if relevant, that such material they gather may comprise the participant's Network connection providers, kind of network browsing and maybe os version, Id number, visited webpages, date or even length of website observations, failure reports, or similar website usage statistics. Private user information may be required by the firm for upkeep and updates, updates, new titles, and analytics software evaluation and calculation. Their security policy must state unequivocally that their firm would be compelled to disclose user information through whatever third-party telecom operators it may hire to help with such initiatives. Likewise, the organisation may be asked to disclose customer data without third-party advertisements and marketing agencies. The data privacy policy assignmentshould include a regulatory statement which explains how a website gathers, analyzes, keeps, distributes, as well as secures user information, as well as the reasons for performing such including the consumer obligations in this respect. In some manner, most websites share with as well as gather information on prospective customers.
• In order to avoid being fraudulent or dishonest, webpage, as well as application owners, must declare every precise acquisition as well as utilization of every individually identifying data. According to Barkatullah, (2018) in order to accomplish so, operators must understand whatever knowledge the webpage, as well as application, would gather as well as how this would be acquired. No privacy policy fully educates webpage or application customers without knowing but also these are essential concerns. This would be true for web pages or applications that merely gather email accounts. Contact information including geographical addresses, individual details, and any user id, initial name but also surname, societal insurance numbers, biometrics material, or indeed distinct identifiers whenever packaged with this identifiable information are examples of personally identifying knowledge. Whenever gathered from customers wherein legislation exists, IP identifiers would be deemed highly identifiable information. Conversely, as per Speak et al., (2018) whenever a customer registers onto the webpage or orders a service, this webpage might obtain intelligence. Additional data gathering might happen, however, including the acquisition of webpage statistics as well as aggregated consumption statistics. For example, such geographical position but also the moment a person accesses a domain, this same (IP) location through where a webpage has been reached, the timeframe of every post's session, it’s kind of browsers and also operational platform utilized to connect their online portal. Details might likewise be gathered through contact within the company, including emails, and faxing, but rather telephone calls. Content is also collected via payment card transactions as well as similar third-party apps accessible via a webpage.
• As opined by Nurgalieva, O’Callaghan and Doherty, (2020) operators must indicate how they intended to utilize any material as well as content acquired. For instance, simply storing information inside a consumer contacts dataset without exchanging information must be revealed. Likewise, every privacy policy must identify every other assistance of good’s transactions or collect for subsequent marketing. Websites should identify all viable methods for disclosing information to other entities. This might comprise information sent to advertising providers or prospect generating firms, Search engine optimisation as well as marketing experts, and related corporations, among others. Websites should declare when they gather material as well as enable third entities to obtain personal details via certain service arrangements as well as an application program. As per Staunton and De Stadler, (2019) whenever a customer also isn't fully informed of such possibility regarding this utilization as well as distribution prior to providing any material to any provider or system, such utilization, as well as distribution of data acquired from the webpage users, is dishonest. Such webpage privacy policy must oblige website owners to explicitly tell consumers regarding every one of its methods that webpage gathers individually recognizable data, as well as how much documentation would and might possibly be utilized as well as transferred to other parties. The website should always follow declarations that they would not disseminate personally identifying information from their webpage as well as that all data customers enter would stay private. Alternatively, this operator has been breaking the webpage privacy policy as well as a slew of national data gathering regulations.
• As opined by Aspers and Corte, (2019) website operators should declare all methods of collecting as well as using individually identifiable information. Inside a word, websites must safeguard user information. In addition, the webpage privacy policy must declare that making false representations regarding security measures is forbidden. This same websitedata privacy policy assignmentmust incorporate or otherwise report protocols which are sensible or rather suitable to avoid but rather identify prospective unapproved access to customers' systems, maintain the framework for prospective security breaches, and also transcript but also maintain software details adequate to undertake safety inspections or rather prosecutions. Websites might never save confidential material for inordinately prolonged lengths of duration or within susceptible formats; instead, websites might also employ complex authentication to protect an intruder from acquiring possession of software including accessing private information kept along a channel.
• As questioned by Mpungose, (2020 websites should use easily accessible protection safeguards to restrict accessibility among software within their networks but also across the online; plus, websites should implement adequate protection safeguards to identify unlawful accessibility to private data but rather to undertake security inspections. Websites cannot amend their privacy policies retrospectively towards the prejudice of webpage as well as platform customers. When the website commences to reveal or trade private information given through site/app customers without first notifying such, the website will break the legislation. The website privacy policy should undertake further efforts to notify consumers that their policy was being altered to allow the third-party exchange of identifiable data without specific authorization. Whenever the confidentiality changes significantly, the website must offer extra notification.
• As opined by Staunton et al., (2021) guiding principles include informing viewers regarding updates with privacy policies as well as requesting users to acknowledge the modifications following navigating throughout the modified policy. Provided their approval has been gained, such private details received from prior webpage customers must never be utilized in a fashion that differs from its initial privacy policy. Whenever a customer files a grievance against such webpage provider, they may face severe legal fines as well as customer remedy losses. This must enable such policy to define the types of private data collected by such webpage as well as the intermediaries with whomever such data might well be exchanged. This legislation relates to every webpage that gathers personally identifiable details through website visitors. According to Staunton, Tschigg and Sherman, (2021) every individual that obtains Social Security information within the process of doing commerce must be required to adopt such privacy policy, according to its website privacy policy. This policy should have "posted publicly" through being posted upon the website, as well as it should preserve the anonymity of Social Security information, prevent the unauthorized publication of Social Security statistics, as well as restrict accessibility with Social Security figures.
• Connecticut regulations now compel enterprises to secure sensitive material, computer records, or otherwise agreements comprising personal details from third-party abuse but also to delete, wipe, or render such records, electronic records, including materials inaccessible before disposing of them. The website privacy policy shall prevent making deliberately inaccurate or deceptive statements about the usage of private data supplied by individuals of its community inside a privacy policy accessible online and elsewhere disseminated or broadcast. Through its manipulative as well as illegal corporate practices legislation, the website must contain inaccurate and erroneous representations within privacy policies displayed through the webpage or even transmitted. The website data privacy policy assignmentshould demand that any private details transferred via open networks or via wireless data be encrypted. It extends to anybody who owns, licensing requirements, stores, or maintains personal details regarding the website user. This legislation should additionally mandate that websites encrypt any personal material held upon computers as well as other handheld gadgets. This privacy policy has been essentially a notification intended to avoid fraudulent information-gathering activities. As a result, online services must adhere to the requirements on how as well as where to publish privacy policies. This policy could be hosted on such different websites but also linked to through the software, but also this could be provided immediately inside the platform.
6. Research Methodology
data privacy policy assignment Research Paradigm
The standard approach or model which is considered bya majority of investigators for conducting a research study is known as research paradigm which mainly consists of four types that are positivism, pragmatism, interpretivism and realism (Khaldi,2017). Since this study uses a case study approach regarding the privacy policy of South African websites, therefore the most suitable research paradigm is considered to be interpretivism. This data privacy policy assignmentresearch paradigm is applied because it has an essence of philosophical phenomenologywhich focuses on understanding the individual case and facilitate qualitative research analysis for the investigator (Žukauskas et al., 2018). Furthermore, this research paradigm is based on the assumption that reality is constructed socially, subjective and consists of interpretations of data from multiple perspectives. It alsoenables the investigator to implement their own subjective view regarding the observed phenomenon and also include their personal experience in drawing inferences. Hence the underlying justification for using the interpretivism research paradigm for this study is that it will enable the investigator to observe and analyse data from multiple perspectivesand frame inferences which will fulfil the research questions (Kamal, 2019). Moreover, this research paradigm will alsohelp in analysing the case study from a personal perspective of the investigator.
Research Design
An intensive and systematic study regarding an individual, a group of individuals, an organisation or a notable phenomenon that has created significant impact is considered to be a case study (Heale and Twycross, 2018). It is possible for a case study to have advantages and disadvantages which should be considered by investigators before deciding whether the study is appropriate for their research requirements. The advantages of a data privacy policy assignmentcase study include that it allows investigators to perform a systematic investigationregarding the case which will generate similar results as an experiment performed under a controlled environment (Hayibo and Pearce, 2021). It also allows the investigator to collect extensive information which can be unusual or rare because of the nature of the case study. From suchinformation collected from case studies it is possible to develop hypotheses which can be explored for obtaining meaningful inferences and conclusions. However, the disadvantages of a case study include the absence of scientific rigour and leading to subsequent bias because it cannot demonstrate cause and effect. Moreover, a case study cannot generalise a larger populationwhich also highlights the absence of scientific regard from case studies. Yin (2013) has divided case studies into single case designs with holistic (single unit of analysis), multiple case designs with holistic (single unit of analysis) and single case designs with embedded (multiple units of analysis).
This research study will be using asingle case design with embedded (multiple units of analysis), which will provide means of including qualitative and quantitative research methods within the research study. Since the research design is based on a single case design with embedded (multiple units of analysis) it will be possible by the investigatorto include qualitative and quantitative data collected from different secondary sources. Multiple units of analysis within an embedded case study also ensures that the investigator is able to include different analysesas their findings to answer the research questionsand frame the required inference from them (Bass et al., 2018). Such a case study methodologyrelies on different sources for data collection that gives richness to the data and contributes significantly to the research validity making it stronger. Hence it can be justified that the research design will use a single case design with embedded (multiple units of analysis) for investigating contemporary events regardingprivacy policies of South African websites.
Research Strategy
The data privacy policy assignmentresearch strategy of a study consists of the strategies and methods which has been used by the investigator for acquiring data from different sources (Oliva, 2019). It includes determining which sampling method has been used to select participants and also the selection criteria that has been applied by the investigator. The sampling method which has been used for selecting websites for this study is convenience sampling because it is considered to be most suitable for selecting small sample sizes. Convenience sampling is considered to be a simple and non-probability sampling method which is applied for collecting data from accessible sources and a small sample size (Funk et al., 2021). This sampling technique has been applied because it helps the investigator to conduct the study in a cost effective manner and helps in collecting more qualitative information for the study. The number of observations, studies or participants which are selected or included in a study is known as the sample size. The sample size for this study includes 10 websiteswhich has been selected for collecting information about the research topic. The primary inclusion criterion for selecting the websites was that it should have a clear mention of the privacy policies which are followed by it.
Data Collection
Data collection is the method of collecting information from primary and secondary sources for gaining valuable and accurate insights for the research study (Feng et al., 2021). The different methods of collecting data including collecting raw data from primary sources which is called primary data and collecting data that has been previously collected from different primary and secondary sources which is known as secondary data. Collecting data is considered to be important for a research study because it enables the investigator to explore information related to the study and answer the research questions which has been framed for the study (Loomis and Paterson, 2018). This data privacy policy assignmentstudy uses secondary data collection method for collecting data about the privacy policies of different South African websites. Since the sample size of websites is 10 from which the investigator will collect the information, therefore, the information about the privacy policies of the websites will be downloaded from each website by the investigator. The website was selected considering the primary inclusion criteria which has enabled the investigatorto collect the necessary data for further analysis. Since secondary data is considered to be more reliable, therefore the investigator has collected search data from the website rather than collecting primary data from different participants.
Data Analysis
Data analysis is the process of analysing the collected data for relevant inferences and answering the research questions by the investigator for fulfilling the aim and objectives of the research study (Washington et al., 2020). Data can be analysed through qualitative and quantitative methods whereby the qualitative methods are applied for analysing the non-numeric data for identifying underlying relationship between variables. Quantitative data analysis is about analysing numeric data by using different statistical tools and techniques. This data privacy policy assignmentstudy uses the qualitative analysis method for analysing the collected data using thematic analysis. Thematic analysis enables the investigator to analyse the textual data for identifying a common theme which is analysed for understanding the common ideas, patterns and relationships in the data set (Rajšp and Fister, 2020). It is possible for the investigator using thematic analysis to frame different themes and address the issues of the research study by drawing important inferences and conclusions.
References
Aspers, P. and Corte, U., 2019. What is qualitative in qualitative research. Qualitative sociology, 42(2), pp.139-160. DOI: https://link.springer.com/article/10.1007/s11133-019-9413-7 data privacy policy assignment
Barkatullah, A.H., 2018. Does self-regulation provide legal protection and security to e-commerce consumers. Electronic Commerce Research and Applications, 30, pp.94-101. DOI: https://doi.org/10.1016/j.elerap.2018.05.008
Bass, J.M., Beecham, S. and Noll, J., 2018, May. Experience of industry case studies: A comparison of multi-case and embedded case study methods. In Proceedings of the 6th International Workshop on Conducting Empirical Studies in Industry (pp. 13-20).
Church, S., Rogers, E., Rockwood, K. and Theou, O., 2020. A scoping review of the Clinical Frailty Scale. BMC geriatrics, 20(1), pp.1-18. DOI: https://bmcgeriatr.biomedcentral.com/articles/10.1186/s12877-020-01801-7
Feng, Y., Duives, D., Daamen, W. and Hoogendoorn, S., 2021. Data collection methods for studying pedestrian behaviour: A systematic review. Building and Environment, data privacy policy assignment187, p.107329.
Funk, R.S., Shakhnovich, V., Cho, Y.K., Polireddy, K., Jausurawong, T., Gress, K. and Becker, M.L., 2021. Factors associated with reduced infliximab exposure in the treatment of pediatric autoimmune disorders: a cross-sectional prospective convenience sampling study. Pediatric Rheumatology, 19(1), pp.1-11.
Harkous, H., Fawaz, K., Lebret, R., Schaub, F., Shin, K.G. and Aberer, K., 2018. Polisis: Automated analysis and presentation of privacy policies using deep learning. In 27th USENIX Security Symposium (USENIX Security 18) (pp. 531-548). Available at: https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-harkous.pdf
Hatamian, M., Wairimu, S., Momen, N. and Fritsch, L., 2021. A privacy and security analysis of early-deployed COVID-19 contact tracing Android apps. Empirical software engineering, 26(3), pp.1-51. DOI: https://link.springer.com/article/10.1007/s10664-020-09934-4
Hayibo, K.S. and Pearce, J.M., 2021. A review of the value of solar methodology with a case study of the US VOS. Renewable and Sustainable Energy Reviews, 137, p.110599.
Heale, R. and Twycross, A., 2018. What is a case study. Evidence-based nursing, 21(1), pp.7-8.
Isaak, J. and Hanna, M.J., 2018. User data privacy: Facebook, Cambridge Analytica, and privacy protection. Computer, 51(8), pp.56-59. DOI: 10.1109/MC.2018.3191268
Kamal, S.S.L.B.A., 2019. Research paradigm and the philosophical foundations of a qualitative study. PEOPLE: International Journal of Social Sciences, 4(3), pp.1386-1394.
Khaldi, K., 2017. Quantitative, qualitative or mixed research: which research paradigm to use. Journal of Educational and Social Research, 7(2), pp.15-15.
L. Haven, T. and Van Grootel, D.L., 2019. Preregistering qualitative research. Accountability in research, 26(3), pp.229-244. DOI: https://www.tandfonline.com/doi/pdf/10.1080/08989621.2019.1580147
Loomis, D.K. and Paterson, S., 2018. A comparison of data collection methods: Mail versus online surveys. Journal of Leisure Research, 49(2), pp.133-149.data privacy policy assignment
Mpungose, C.B., 2020. Emergent transition from face-to-face to online learning in a South African University in the context of the Coronavirus pandemic. Humanities and Social Sciences Communications, 7(1), pp.1-9. Available at: https://www.nature.com/articles/s41599-020-00603-x
Nurgalieva, L., O’Callaghan, D. and Doherty, G., 2020. Security and privacy of mHealth applications: a scoping review. IEEE Access, 8, pp.104247-104268. DOI: 10.1109/ACCESS.2020.2999934
O’Brien, P., Young, S.W., Arlitsch, K. and Benedict, K., 2018. Protecting privacy on the web: A study of HTTPS and Google Analytics implementation in academic library websites. Online Information Review, 42(6), pp.734-751. DOI: https://www.emerald.com/insight/content/doi/10.1108/OIR-02-2018-0056/full/html
Oliva, R., 2019. Intervention as a research strategy. Journal of Operations Management, 65(7), pp.710-724.
Qin, Q., Ke, Q., Du, J.T. and Xie, Y., 2021. How Users' Gaze Behavior Is Related to Their Quality Evaluation of a Health Website Based on HONcode Principles. Data and Information Management, 5(1), pp.75-85. DOI: https://doi.org/10.2478/dim-2020-0045
Rajšp, A. and Fister, I., 2020. A systematic literature review of intelligent data analysis methods for smart sport training. Applied Sciences, 10(9), p.3013.data privacy policy assignment
Rath, D.K. and Kumar, A., 2021. Information privacy concern at individual, group, organization and societal level-a literature review. Vilakshan-XIMB Journal of Management. DOI: https://www.emerald.com/insight/content/doi/10.1108/XJM-08-2020-0096/full/html
Rethlefsen, M.L., Kirtley, S., Waffenschmidt, S., Ayala, A.P., Moher, D., Page, M.J. and Koffel, J.B., 2021. PRISMA-S: an extension to the PRISMA statement for reporting literature searches in systematic reviews. Systematic reviews, 10(1), pp.1-19. DOI: https://systematicreviewsjournal.biomedcentral.com/articles/10.1186/s13643-020-01542-z
Rong, S., Wang, L., Peng, Z., Liao, Y., Li, D., Yang, X., Nuessler, A.K., Liu, L., Bao, W. and Yang, W., 2020. The mechanisms and treatments for sarcopenia: could exosomes be a perspective research strategy in the future. Journal of cachexia, sarcopenia and muscle, 11(2), pp.348-365.
Speak, A., Escobedo, F.J., Russo, A. and Zerbe, S., 2018. Comparing convenience and probability sampling for urban ecology applications. Journal of applied ecology, 55(5), pp.2332-2342. DOI: https://besjournals.onlinelibrary.wiley.com/doi/pdf/10.1111/1365-2664.13167
Staunton, C. and De Stadler, E., 2019. Protection of Personal Information Act No. 4 of 2013: implications for biobanks. South African Medical Journal, 109(4), pp.232-234. DOI: https://journals.co.za/doi/pdf/10.7196/SAMJ.2019.v109i4.13617
Staunton, C., Adams, R., Botes, M., de Vries, J., Labuschaigne, M., Loots, G., Mahomed, S., Loideain, N.N., Olckers, A., Pepper, M.S. and Pope, A., 2021. Enabling the use of health data for research: Developing a POPIA code of conduct for research in South Africa. South African Journal of Bioethics and Law, 14(1), pp.33-36. DOI: https://journals.co.za/doi/pdf/10.7196/SAJBL.2021.v14i1.740
Staunton, C., Tschigg, K. and Sherman, G., 2021. Data protection, data management, and data sharing: Stakeholder perspectives on the protection of personal health information in South Africa. PloS one, 16(12), p.e0260341. DOI: https://doi.org/10.1371/journal.pone.0260341
Stratton, S.J., 2021. Population research: convenience sampling strategies. Prehospital and disaster Medicine, data privacy policy assignment36(4), pp.373-374. Available at: https://web.archive.org/web/20210727072206id_/https://www.cambridge.org/core/services/aop-cambridge-core/content/view/B0D519269C76DB5BFFBFB84ED7031267/S1049023X21000649a.pdf/div-class-title-population-research-convenience-sampling-strategies-div.pdf
Sundler, A.J., Lindberg, E., Nilsson, C. and Palmér, L., 2019. Qualitative thematic analysis based on descriptive phenomenology. Nursing open, 6(3), pp.733-739. DOI: https://onlinelibrary.wiley.com/doi/pdfdirect/10.1002/nop2.275
Swales, L., Thaldar, D. and Donnelly, D.L., 2022. Why research institutions should indemnify researchers against POPIA civil liability. South African journal of science, 118(3), pp.22-24. DOI: https://journals.co.za/doi/pdf/10.10520/ejc-sajsci-v118-n3-a9
Tesfay, W.B., Hofmann, P., Nakamura, T., Kiyomoto, S. and Serna, J., 2018, March. PrivacyGuide: towards an implementation of the EU GDPR on internet privacy policy evaluation. In Proceedings of the Fourth ACM International Workshop on Security and Privacy Analytics (pp. 15-21). Available at: https://dl.acm.org/doi/pdf/10.1145/3180445.3180447casa_token=YfQ0lj9zCa4AAAAA:WoAGTv8xH3Qs GJsi3ysU_PwdsjjwjOfvT7rIlSIDkfgnGm5IkxARBp0bzZSBsZal1DAzM4k1xcD6ie0
Van Niekerk, M., 2019. Providing claimants with access to information: A comparative analysis of the POPIA, PAIA and HPCSA guidelines. South African Journal of Bioethics and Law, 12(1), pp.32-37. DOI: https://journals.co.za/doi/pdf/10.7196/SAJBL.2019.v12i1.656 data privacy policy assignment
Verkijika, S.F. and De Wet, L., 2018. Quality assessment of egovernment websites in S ubS aharan A frica: A public values perspective. The Electronic Journal of Information Systems in Developing Countries, 84(2), p.e12015. DOI: https://onlinelibrary.wiley.com/doi/pdf/10.1002/isd2.12015
Washington, S., Karlaftis, M., Mannering, F. and Anastasopoulos, P., 2020. Statistical and econometric methods for transportation data analysis. Chapman and Hall/CRC.
Yin, R.K. (2013). “Case study research design and methods”, (3 rd Ed), Sage Publications, California.
Žukauskas, P., Vveinhardt, J. and Andriukaitien, R., 2018. Philosophy and paradigm of scientific research. Management culture and corporate social responsibility, data privacy policy assignment121.












