Utilization Of Microservices Architecture As A Software Development Philosophy
Question
Task:
Case Scenario
Greer John Wealth Management Pty Ltd is a mature company with a strong base of investment customers who trust it with their investment portfolios. Its core platform for managing its customer’s accounts and investments was built in the early 2000s and was cutting edge at the time. This monolithic platform has served both the business and customer needs well. However, changing times mean that cloud-based solutions offer it greater flexibility and agility.
Several factors have arisen that have made it clear to the executive leadership team that it needs to review its technology strategy:
- Many competitors are evolving their digital platforms to better meet market expectations.
- Regulatory reform in the area of wealth management is likely to require waves of change to various wealth management products managed by Greer John.
The executive leadership team understands it needs to seek out new ways of meeting its customers’ needs. It is investigating a digital strategy that will allow it to steadily and incrementally transition from its old platform into a cloud-enabled solution that will be nimble and agile in responding to its customers’ digital needs.
A team of consultants has been tasked with building a suite of reports as concept briefs to address the different areas of change so that all stakeholders understand what new solutions will require.
As the microservices architecture specialist in the team, you have been tasked with writing a report about the microservices architecture component of the shift to the cloud. This is to help key stakeholders of the executive leadership team be informed what the change will mean for them.
Task Summary
You are required to research and write a report focused on the specific challenges and issues that arise owing to the use of microservices architecture as a software development philosophy. The report length is 1500 words (+/- 10%). You are also required to identify and include risk mitigation strategies that can be applied to minimise privacy and security risk in microservices-architected environments.
Context
Microservices architecture signals a shift from monolithic software applications architecture to different microservices architected to address different functions. Not only is there a shift in how distribution of services impacts on managing security but hosting of services on cloud platforms not owned by the organisation, and the use of communication channels between services adds complexity to managing security.
Equally, additional complexity is provided through the rapid and incremental software development principles associated with Agile and DevOps methods. The organisation as an enterprise has several moral, ethical, and legal obligations regarding privacy and the security of information.
The purpose of this report is to engage you in building knowledge about privacy and security issues with a specific focus on how these manifest in a microservices-architected environment. You are also required to identify and discuss mitigations available to better manage privacy and security risk for the organisation in relation to microservices architecture. Irrespective of your future role, many organisations make it clear that privacy and security is every employee’s concern.
Task Instructions
Write a 1500-word report focused on the specific challenges and issues that arise owing to the use of microservices architecture as a software development philosophy. Identify and include risk mitigation strategies that can be applied to minimise privacy and security risk in microservices-architected environments.
Answer
Introduction
The microservices architecture is an architectural style that organizes an application as an assembly of roughly coupled services. Within the microservices architecture, the conventions are light weighted and facilities are finely grained. When the microservices are utilized successfully, its design provides scalability in the application (Balalaie, Heydarnoori & Jamshidi, 2016). The microservices architecture is also a building style where the applications are testable, maintainable, independently deployable, and loosely coupled. In order to address various functions microservices architecture signals to shift from the monolithic software application architecture to various microservices architecture. Within the advanced cloud computing technologies, the utilization of microservices has been widely addressed because this architecture has a wide set of features. Hence, it is essential to secure the microservices architecture as it is connected with the cloud computing environment.
Therefore, the main objective of this report is to identify the issues and challenges that arise during the utilization of microservices architecture as a software development philosophy. The report will also develop a risk mitigation strategy that helps to minimize the security and privacy risks in microservices architected environments. The report will also analyze the challenges in microservices architecture and propose various solutions to secure the Microservices architecture. Moreover, it is essential for Greer John Wealth Management to shift from monolithic architecture to microservicesarchitecture.
Discussion
Microservices architecture
Microservices are a natural solution for cloud services that have been adopted in the replacement of monolithic systems. it is one of the most emerging trends when it comes to the development, delivery, and design of services to software. The microservices architecture is mainly deployed on the cloud that helps the users to utilize it at low risk, threshold, and cost. Microservices architecture is a real opportunity for the Greer John Wealth Management organization to enhance its integrated system. Monolithic application scaling is quite difficult as they normally offer a wide range of popular services (Sun, Li & Memon, 2017). Popular services should be scaled as they are highly demanding and the whole services needed to be scaled at the same time. As a result, the unpopular services will consume a huge amount of server resources when they are not going to be utilized. Microservices architecture has the following features:
- Microservices architecture has a standardized and open interface that will describe all the specified goals of the organization with available communications methods, efficiency, and effectiveness.
- Microservices architecture can be moved, destroyed, deployed, and moved independently (Salah et al., 2016). Therefore, it cannot be bound for any kind of local resources and the environment of microservices can develop more instances for the same microservices.
- The microservices architecture is fine-grained so each microservice is able to handle its own task.
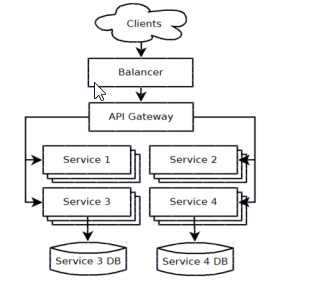
Figure: Micro Services Architecture
(Source:Almeida et al., 2017)
Specific Issues and challenges
Within the monolithic architecture, a single product comprises all the codes, therefore, if a security problem arises while developing software then the whole system becomes vulnerable to attack and can be impacted. Therefore, it is difficult for the Greer John Wealth Management organization to isolate potential security threats in a monolithic architecture (Aderaldo et al., 2017). Moreover, in order to mitigate this specific vulnerability, the organization needs to upgrade from monolithic architecture to microservices architecture.
Within the microservices architecture, a single software product is broken into multiple smaller individual services, each service contains a specific goal and makes the whole system easier to develop and more secure. As in this architecture, every service is developed separately and run on different servers so it minimizing the possibility of entire system breakdown when an attack happens. Therefore, microservices architecture is more secure as compared to the monolithic architecture while developing the software and it minimizing the security risks.
Therefore, it is recommended for Greer John Wealth Management organization to upgrade their system from monolithic architecture to microservices architecture that will provide more security in software development.
Potential Privacy Issues
Microservices architecture has several advantages but it also has some specific security issues. The security issues of the microservices are provided below:
- Service Registry and Discovery: The microservices architecture is designed for distributed computing. In this architecture, an application comprises several fine grain independent services. All the independent services are communicated through a network. Therefore, in order to utilize a service, the user needs to know the exact network location of these specific services (Yu et al., 2019). Therefore, service location discovery is one of the important security of the microservices that will become more complex when the network location of the services changes continuously.
- Unified Access of Services:Microservices architecture can comprise several consumers and several services. Different consumer needs different services and microservices architecture provides unified access to services. Therefore, the unified access of services is security related issue of the microservices architecture.
- Authentication and Authorization: The microservices architecture does not contain any authentication and authorization services that is one of the important security related issues of this architecture (Nagothu et al., 2018). Therefore, in order to secure the services, it is important to implement a centralized authorization and authentication service.
- Debugging and Logging: Within the microservices architecture there are some use cases that span across various services. There are also no common logging services in the microservices architecture and each service needs to develop its own log that is an issue of this architecture. The developed manually analyze a bug to troubleshoot it.
- Configuration: Each service of the microservices architecture is independent therefore, all the services needed to be configured separately (Esposito, Castiglione & Choo, 2016). The separate configuration of each service added complexity to the microservices architecture.
Potential Mitigation plan for the identified challenges
Greer John Wealth Management Pty Ltd can face those significant challenges while implementing or transitioning to a microservices architecture, as this architecture is more complicated as compared to legacy systems. The microservices environment of the organization becomes complex because the teams will have to manage and provision various moving parts. Therefore, Greer John Wealth Management Pty Ltd should focus on the mitigation plan for managing the risks associated with security and privacy. There are some existing solutions to mitigate the issues, which are focused on a layered approach. The layered approach has a security mechanism that can establish trust through the use of MLTS for microservices security. Following are some recommendations to manage the discussed challenges for both security and privacy associated with the microservices architecture:
Solution for service discovery and registry
All the system designers of Greer John Wealth Management Pty Ltd should implement a service registry along with a database of all the available services network locations. The system designers could register for the services by themselves or through a third party for the common registry (Nkomo & Coetzee, 2019). The associated consumers could utilize the service registry to dynamically determine various network locations of the services.
Solution for Unified Access of the Services
The recommended solution for the above-mentioned task is to implement an API gateway, which can act as the single access point for the services. All the customers can call the API gateway and this gateway will route them to their requested services. Moreover, the API gateways could provide different services such as security, aggregation of services, metering, and many others.
Solution for authentication issue
It is recommended to use centralized authentication services that will allow the consumers to be authenticated before getting access to the services. Individual services must be accountable to authorize the respective consumers (Waseem, Liang, & Shahin, 2020).
Solution for logging and debugging
It is recommended to Greer John Wealth Management Pty Ltd to implement a logging service that will be common for all in which individual services could utilize the services for writing the logs.
Solution for configuration issue
The organization should implement a centralized configuration service that could be backed up through a common configuration repository. This will help all the services to send a request for reading all the configurations (Salah et al., 2016).
Conclusion
Microservices architecture is altering the structuring of teams allowing the organizations to develop teams that are focused on particular services and providing them autonomy along with responsibilities in the reserved area. This approach will help Greer John Wealth Management Pty Ltd to quickly adjust in responding to the inconsistent business demands without interfering with the core activities. It can also be concluded that some challenges will emerge during the transition period towards microservices architecture but they can be mitigated through various techniques that are discussed in this report. In terms of software development, microservices architecture is becoming progressively prevalent as an architectural style. Microservices architecture provides services that can be further divided into various minor parts that focus on some specific services and functionalities.
Moreover, the selected organization as per the provided case scenario will have some advantages with the transition to microservices as compared to the monolithic architecture in terms of software development. This can be the increase in the flexibility of the implemented software as a microservice along with an easy scaling for the solution that has been implemented by the microservices. Therefore, the report has analyzed various security issues and challenges that are faced during the transition to microservices by Greer John Wealth Management Pty Ltd and recommended efficient solutions to overcome those challenges.
References
Aderaldo, C. M., Mendonça, N. C., Pahl, C., &Jamshidi, P. (2017, May). Benchmark requirements for microservices architecture research. In 2017 IEEE/ACM 1st International Workshop on Establishing the Community-Wide Infrastructure for Architecture-Based Software Engineering (ECASE) (pp. 8-13). IEEE.
Almeida, W. H. C., de Aguiar Monteiro, L., Hazin, R. R., de Lima, A. C., &Ferraz, F. S. (2017). Survey on microservice architecture-security, privacy and standardization on cloud computing environment. ICSEA 2017, 210.
Balalaie, A., Heydarnoori, A., &Jamshidi, P. (2016). Microservices architecture enables devops: Migration to a cloud-native architecture. Ieee Software, 33(3), 42-52.
Esposito, C., Castiglione, A., & Choo, K. K. R. (2016). Challenges in delivering software in the cloud as microservices. IEEE Cloud Computing, 3(5), 10-14.
Nagothu, D., Xu, R., Nikouei, S. Y., & Chen, Y. (2018, September). A microservice-enabled architecture for smart surveillance using blockchain technology. In 2018 IEEE International Smart Cities Conference (ISC2) (pp. 1-4). IEEE.
Nkomo, P., & Coetzee, M. (2019, November). Development Activities, Tools and Techniques of Secure Microservices Compositions. Microservices architecture assignment In International Conference on Information Security Practice and Experience (pp. 423-433). Springer, Cham.
Salah, T., Zemerly, M. J., Yeun, C. Y., Al-Qutayri, M., & Al-Hammadi, Y. (2016, December). The evolution of distributed systems towards microservices architecture. In 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST) (pp. 318-325). IEEE.
Sun, L., Li, Y., &Memon, R. A. (2017). An open IoT framework based on microservices architecture. China Communications, 14(2), 154-162.
Waseem, M., Liang, P., & Shahin, M. (2020). A systematic mapping study on microservices architecture in devops. Journal of Systems and Software, 170, 110798.
Yu, D., Jin, Y., Zhang, Y., & Zheng, X. (2019). A survey on security issues in services communication of Microservices?enabled fog applications. Concurrency and Computation: Practice and Experience, 31(22), e4436.












