Blockchain Technology Assignment: Q&A Based On MultiChain & Programming
Question
Task:
The blockchain technology assignment consists of the following questions:
Question 1
Compare public blockchain, private blockchain and centralised databases and present your opinion from below aspects:
(a) The differences in characteristics between them.
(b) Their strengths and weaknesses respectively.
(c) Illustrate and discuss scenarios that are most suitable for public blockchain, privateblockchain and centralised database to be applied.
Question 2
Multichain is an extended open source fork of Bitcoin blockchain. Assess the differences between MultiChain and Bitcoin blockchain and answer the following questions:
(a) What is the difference between a native asset on MultiChain and a colored coin?
(b) What is the difference between MultiChain’s round robin consensus protocol andBitcoin’s proof of work protocol?
(c) Why is the mining of native currency not necessary for MultiChain?
(d) What is the name of the MultiChain permission that controls a node’s ability to onlychange connect, send and receive permissions for other addresses?
Question 3
Construct a blockchain network “chain2” and answer the following questions about the settingup of the seed node.
(a) What is the default directory, parameter file name and the parameter that you use to tell the node to stop mining after certain number of rounds if there are no new transactions?
(b) What do the parameter and value “admin-consensus-admin = 0.6” mean?
(c) What is the file name of the file that contains the parameter for controlling the network IP addresses that can connect remotely to your node via RPC? What is the name of thisparameter? What is the value that will allow any network IP address to connect via RPC?
Question 4
Construct a blockchain network “chain2” based on the assumption that the group leader is theowner of Server1 and you are the owner of Server2. The group leader created a seed node for the blockchain "chain2" at IP address 20.184.11.138 and default network port is 2020.
You are logged into Server2 and your objective is to run a multichain node on Server2 to connect to “chain2” via Server1.
Answer each question posted at the end of each independent scenario.
- Scenario A
- $ multichain-cli create chain2
- $ multichaind chain2
- $ multichaind chain2@20.184.11.138. The result shows the error message “ERROR:couldn’t initialise permission database for blockchain chain2.”
- Scenario B
- $ multichain-cli create chain2
- $ multichaind chain2@20.184.11.138
- You are shown message “Node ready.”
- $ multichain-cli chain2 getinfo. The result shows that node on server2 is running.
- $ multichain-cli chain2 getpeerinfo. The result shows that node on server2 is
- Scenario C
You perform the following actions:
What is the problem here? How to fix this?
You perform the following actions:
What is the problem here? How to fix this?
You perform the following actions:
$ multichaind chain2@20.184.11.138. The following message is displayed:
Please ask blockchain admin or user having activate permission to let you connect and/or transact:multichain-cli chain2 grant 13wWJEFYVw1B9122aoA1UvBoetDTUMWKraFAKF connect multichain-cli chain2 grant 13wWJEFYVw1B9122aoA1UvBoetDTUMWKraFAKF connect,send,receive
The group leader performs the following actions:
$ multichain-cli chain2 grant 13wWJEFYVw1B9122aoA1UvBoetDTUMWKraFAKF send,receive
You perform the following actions:
$ multichaind chain2@20.184.11.138
You are still not connected to chain2.
What is the problem here? How to fix this?
Question 5
Construct a blockchain network “chain2” and answer the following questions when connectinga new node to the seed node.
(a) What is the name of the file that is downloaded from an existing node when you perform a peer-to-peer handshake using a new node for the first time? Specify the names of anytwo (2) parameters that do not contain the value “[null]” in this file.
(b) A new node tries to connect for the first time using “multichaind” and receives the errormessage “Error: Couldn’t connect to the seed node”. List down all the possible causesfor this error.
Question 6
(a) How do you check the number of confirmations for a transaction on Multichain givena transaction ID?
(b) How do you find out what is the current number of blocks processed in the server?
(c) How do you check if an address is pending multiple approvers to grant a permission?
(d) How to run multichain-cli to show the help for getinfo from commandline mode forchain2?
Question 7
Create a MultiChain asset “Orange” and answer the following questions.
- Server1 is using an address “1AxZhpXvorakfAfbEKsTvj1ACeM2scSMmVWvXP” with “issue” permission to create a new asset called “Orange”. The asset is required tobe reissuable.
- After Server1 has successfully issued “Orange” into its wallet address, it tries to re-issue another 100 asset using this command:
Server1 creates the asset using this command:
issue 1AxZhpXvorakfAfbEKsTvj1ACeM2scSMmVWvXP {"name":"Orange","open":true} 100
Server1 then runs this command:
getaddressbalances 1AxZhpXvorakfAfbEKsTvj1ACeM2scSMmVWvXP
And the result displays:
[
{
"name" :
"{name:Orange,open:true}",
"assetref" : "216-267-61494",
"qty" : 100
}
What is wrong and how to resolve this?
issue 1AxZhpXvorakfAfbEKsTvj1ACeM2scSMmVWvXP '{"name":"Orange","open":true}' 100
The system returns an error.
Why? How to resolve this?
Question 8
Create asset A and asset B for atomic asset exchange and answer the following questions.
- Server1 performs an exchange of asset A for asset B with Server2 using 2 transactions.
Server1 sends 10 units of AssetA to
Server2.Server2 sends 10 units of AssetB to
Server1.
Why is this not an atomic swap? - Server1 prepares to offer 1 units of Apple for the exchange by issuing this command:
preparelockunspent ‘{“{Apple}”,1}’
The result shows:
{
"txid" :
c0556c42b875d43203c6d6a22f3494747164407697cdccd1d06f0d6c7ea322ce", "vout" : 0
}
Server1 later changes its mind about making the exchange, what command does Server1 use to cancel the offer for 1 units of Apple? - Run the following on
Server1:Step 1:
preparelockunspent ‘{“{Apple}”:1}’
get the {txid} and {vout}from the result and use it in the next instruction.Step 2:
createrawexchange “{txid}” {vout} ‘{“{Apple}”:1}’
get {partial-raw-exchange} string from the result and use it in the next
instruction.Step 3:
decoderawexchange {partial-raw-exchange}
What is the result from the last instruction? Why does the asset parameter of “offer” and “ask” return empty list?
Answer
Question 1
Comparison among public blockchain, private blockchain and centralised databases presented in the blockchain technology assignment
Public blockchain
A public blockchain is basically an open ended blockchain that has similar rights to all the participants. In this blockchain, the information that is represented is public that is used to determine the consensus process and validity of the transactions (Monrat, Schelén, & Andersson, 2019). This type of blockchain is quite different from a private blockchain depending upon the security levels.
Private blockchain
Private blockchain, on the other hand, possesses different levels of protocols that are authority-based. This process means that network owners will not have the permissions to gain control of the participants who are involved in this network. However, they will have the ability to remove or add the participants (Zhou et al., 2020). Thus, in a private blockchain, the level of power can be reduced for the participants.
Centralised databases
The records that have been stored in a traditional database can be stated as centralised. While on the other hand, blockchain is decentralised in its manner. The primary difference lies that since the database is being centralised, each participant who is involved in the blockchain can have the ability to keep a secured copy of the records. This will also permit making changes in the centralised database, which is visible to all the users using the database. Furthermore, the blockchain database is mostly composed of decentralised nodes which are involved in administration for ensuring the entry of raw data in the database.
a. Strengths and weaknesses of public blockchain, private blockchain and centralised databases
Public blockchain
Strengths: One of the biggest pros that can be obscured in the public chain is that it does not involve any trust. As a result of that, everything can be kept recorded, which cannot be changed further. Everyone is enforced to attempt the right objectives which are favourable for the network (Syed et al., 2019). Another advantage is security due to the decentralised form.
Moreover, the public blockchain is also beneficial in ensuring transparency. This has reached verification in all types of data transactions.
Weaknesses: The major concern for public blockchain is speed. The public blockchain, similar to bitcoin, processes only seven transactions per second. The concern of over scalability is also observed in the public blockchain. Other than that, it consumes energy and is also high in this type of blockchain.
Private blockchain
Strengths: The advantage that can be ensured by the private blockchain is speed. More transactions can take place and can process thousands of transactions per second. Another advantage of the private blockchain is scalability. The decision-making process in this type of blockchain is quite faster since the nature of blockchain is centralised.
Weaknesses: One of the biggest disadvantages that are observed is the centralisation of the private blockchain. Since the blockchain is built in order to prevent centralisation, but automatically it becomes centralised because of its private network.
Centralised databases
Strengths: A centralised database can be used to keep clean and maintain the data with accuracy that is verified. This process of data cleaning is performed; it can be used to remove duplicate and outdated entries. Other than that, it also helps in categorising the information and data.
Weaknesses: The centralised databases can show the possibilities of bottlenecks that can occur due to high traffic. Moreover, these types of databases are mostly dependent on the strong connectivity of the network. In addition to that, centralised databases have mostly limited access; one can use the data at one time and is maintained at a specific location.
b. Suitable scenarios of public blockchain, private blockchain and centralised databases
Public blockchain
The public blockchain is the network where any user can join as per their will. In this regard, the example of Ethereum would be appropriate. The public blockchain system is essential for carrying out normal transactions such as crypto trading. However, the security elements if the system can be problematic for the users.
Private blockchain
The blockchains that maintain strict anonymity, like Ripple (XRP), are examples of private blockchain where no user is allowed to enter except the desired grade of permissions. The private blockchain system is more secure and most essential in terms of carrying out secure transactions. However, there are no overseers in this kind of networks.
Centralised databases
The centralised blockchain databases examine and monitor the process of networking under any particular chain. An example of such a system is a mainframe computer. In this centralised database, all the data is stored and managed in a single unit. It is modified using any internet connection through LAN and WAN.
Question 2
a. Comparison between native asset between on coloured coin and on MultiChain
A native asset in the form of the IOTA token is usually referred to as the name of the coloured count. In this context, the specific application is developed, which runs with the help of the function that is being performed with the use of the digitised token. This digitised token is used to represent the finite assent and tamper-proof in the existence of real-world entities. This term of Coloured Coins is used to describe a class of functions (Ismailisufi et al., 2020). The concept of coloured coins is created on the topic of Bitcoin blockchain and is being used to manage the assets of the real world.
On the other hand, the multi-chain assets are used to support the assets natively at the level of blockchain. The quantities and identifiers used for the assets are encoded in this process with the use of each transaction output. It is also encoded with the quality of the native currency of blockchain. In each of the nodes in MultiChain, the verification is performed on determining the quantity of the asset among the transactions. The total quantities are checked for every asset that has been made through the transaction outputs.
Comparison between Bitcoin proof of work control and Multichain round robin consensus protocol
Proof of Work is used to meet the requirement of the nodes on the network. This will provide the actual evidence of the computational power of Bitcoin in order to receive the consensus through the process of decentralised activities. In this process, the prevention of bad actors can be done, which is preventing the use of the network (Ahmad et al., 2019). SHA-256 hashing algorithms can be used to involve interactions in bitcoin. Due to decentralised options, the network using cryptocurrency can be enhanced with security and consensus.
MultiChain, on the other hand, uses the consensus protocol in order to validate the blocks. This validation is achieved through the scheme implemented using the round-robin algorithm and with the help of the mining-diversity parameter. In that case, all the addresses and the nodes involved will have permission in order to validate blocks in the network. The parameter value of mining diversity can be set between 1 and 0 (Polge, Robert, & Le Traon, 2021). In the round-robin scheme, the number of nodes can be determined with the mine permissions used in the network. The default value of the mining-diversity parameter is initialised to 0.3 and cannot be changed after the initialisation.
Reasons for not using mining of Native currency in Multichain
On the assumption, if there is any pre-approved consensus that has been used between miners, then there is no requirement for proof of work. This is a significant way to prevent any actions that can take control of the network. In that case, it is beneficial to define the consensus, which is relatable signatures given on blocks as per the pre-approved consensus. Restriction implemented through mining on a set of entities can resolve the problem that occurs in different private blockchains (Muthuraman, Pichiah, & Anuradha, 2019). The solution can be implemented by applying constraints on the different blocks used and created in an active window for the same miner. This possible process can be used to enforce the round-robin mechanism. In this mechanism, the miners are permitted for creating blocks with the help of rotation prices. This helps in generating a valid blockchain. Other than that, the parameter of mining-diversity also helps to define a scheme that is strict. The value of 1 represents the permission to the miner to execute the rotation, whereas the value of 0 does not represent any restriction.
Name of multi chain permission which controls ability of the node to only change connect
There are several permissions that are defined in the MultiChain, which are necessary in order to assess the global permissions that can be granted on an address. For ensuring the control of the ability of the node to implement only change, connect, send and receive permission from different addresses, the MultiChain command that is being used for this purpose is "activate" (Alimehaj et al., 2021). The permission "activates' ' helps in processing the required permissions like receive, send and connect that arrives from different users related to signing the transactions.
Question 3
a. Default directory, parameter file name and the parameters that are used to stop mining
The default directory of the blockchain is the directory where the original node chain of the process would occur. In this process, it will be essential for the system to analyse the attributes of the directory and the parameter of the file in order to assess its chain nodes.
b. Meaning of parameter and value “admin-consensus-admin = 0.6”
The parameters of the “admin-consensus-admin = 0.6” will be the node that would be connected with both the admin and the system of the MultiChain process (Thin et al., 2018). In this regard, it will be essential to analyse the values that the individual connections of the chain would hold up.
c. File name of the file that contains the parameter for controlling the network IP addresses
Name of the parameter
The parameter that will control the network IP would be connected with the transaction ID of the chain nodes. In this context, the analysis of the individual IDs would be needed. Apart from that, the value that will allow any network IP address to connect via RPC would also be needed to calculate to ensure the scalability of the blockchain network.
Question 4
a. Problem in scenario A
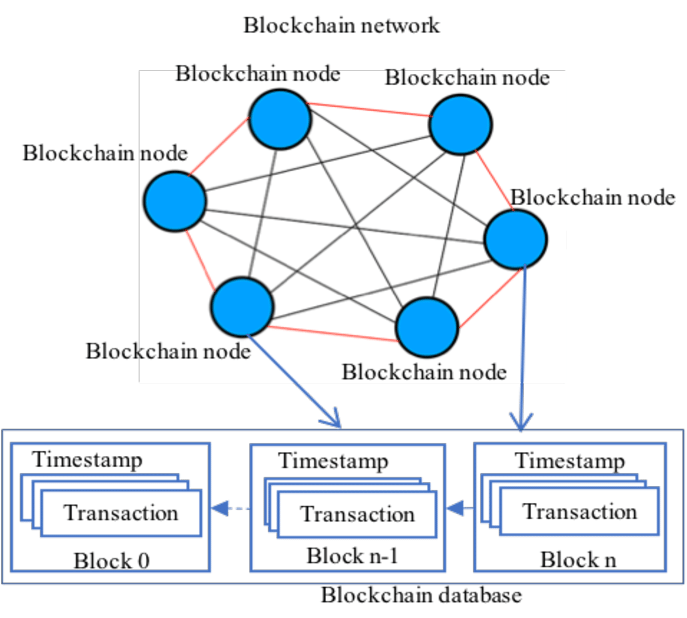
Figure 1: Blockchain Network Chain “chain2”
(Source: Created by the Author)
The problem that can be detected in this network process is that while creating chain2 of the blockchain network using the multichain-cli command is to run a multi chain node for server2 and connect it to server 1 (TANRIVERD?, 2020). As a result of that, the initial permission of the database can be initialised for the blockchain chain2.
Fixing the scenario
After the successful initialisation of the blockchain, the user is informed regarding the denial of permission to connect. In this process, it is required firstly to connect to the first server in order to add the permissions for the connection that is required to connect with the second server. In order to resolve the scenario, it is essential to run this command.
multichain-cli chain2 grant 1.... Connect
b. Problem in scenario B
In this case, the problem which is detected while running the multichaind command in the server at the designated IP shows the message of node ready. However, after generating the getinfo and getpeerinfo the results are not the same for both (Ma, 2018). In server2, the result of the node is shown running while executing the getinfo command, while the result from getpeerinfo command shows the node is already allocated to server2.
Fixing the scenario
As per the evaluation of Muthuraman, Pichiah, & Anuradha (2019), in order to fix the situation, it is required to analyse the multichain server that is running already on both instances. For this purpose, it is required to ensure that which peers are involved in the getpeerinfo. By running the getpeerinfo command, the peer-to-peer information is generated for the node (Zaidi et al., 2021). So, in this case, if the blockchain is running with two nodes, the resultant outcomes from this command will follow the results of another node. In this process, addnode command can also be used in the format of
multichain-cli chain1 addnode [ip-address] add
Problem in scenario C
In this scenario, the activate command needs to be used at the later section after granting permission to the IP address for connecting the server. The user needs to identify the permissions in order to proceed with the “activate” permission. After that chain2 blockchain can be connected to the designated server.
Fixing the scenario
For this process, “activate” permission needs to be added after the IP address has got the permission to connect to the new server in the given IP address.
Question 5
a. Name of the file that is downloaded from an existing node while performing peer-to-peer handshake using a new node for the first time
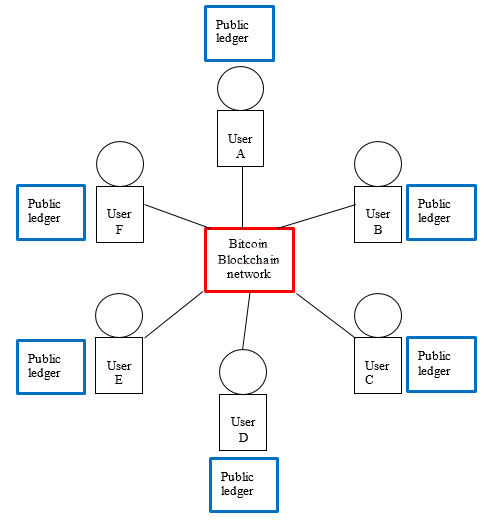
Figure 2: Blockchain Network Chain “chain2”
(Source: Created by the Author)
The name of the file from an existing node was “public ledger”. It was obtained when the system performed a peer-to-peer handshake using a new node for the first time. The connect permission is used to apply for downloading the file from an existing node in order to proceed with peer to peer handshaking between two nodes. Whenever a new node is encountered for the first time, each node proves its ownership in order to access the private key that is allocated with the particular address (Tapsell, Akram, & Markantonakis, 2018). After generating these permissions for connectivity in the network, the permissions are revoked from the address. Furthermore, the nodes are then disconnected from any connections immediately that are used as revoked addresses in the process of peer to peer handshaking.
Two parameters that do not contain the value “[null]” in this file
As per the analysis of Alimehaj et al. (2021), parameters that can be used which do not contain the value “[null]” in this file are anyone-can-connect and anyone-can-count. The anyone-can-connect command puts no restriction on setting up the connection with the network. By default, the value stands false in this case. The anyone-can-send commands are used to restrict sending transactions that are the inputs used for signing transactions. By default, this value can also be found false.
b. Possible causes of error in connecting a new node using “multichaind”
If the server does not have the latest version, there can be chances of showing this error in connecting to a new node in such circumstances. If the issue is still remaining in the process, it has the possibility of relating to the port of the firewalls (Cao et al., 2020). This can be checked using telnet for developing appropriate peer-to-peer connections for checking if the connection is made successfully or not. The possible cause for the errors is:
- Corrupted nodes within the blockchain network
- Issues with the authentication of the blockchain node
If somehow, the blockchain remains private in this case, this blocks the permissions to connect on an immediate basis. This error then occurs if the actual permissions have not been granted by the administrator. For seeking the permissions, it is required to the rand command after running the following code
multichaind chain2@ip-address -daemon
Question 6
a. Check the number of confirmations for a transaction on MultiChain given a transaction ID
Thin et al. (2018) have concluded that whenever a transaction is encountered for the first time in the block during a block in the network, it gets only a single confirmation. With every continuous block that is rebuilt at the top of the existing block, the number of confirmations keeps on increasing by one. The number of confirmations that have been observed for a transaction basically works on the following process on Multi Chain for a provided transaction ID (Kumar et al., 2020). For checking the number of confirmations that actually appears in a transaction or black is made by counting the number of transactions or blocks that are actually buried under the chain that is made in the blockchain network, and one is added to its value. This one is added for counting the block itself or the embedded transactions in the block. For further proceeding with the time, this count of the number of confirmations that are recorded for any of the past events increases its possibilities.
b. Current number of blocks processed in the server
Zaidi et al. (2021) have opined that the use of the MultiChain Command Line Tool offers numerous options in order to identify the number of blocks that have been processed in the server in the blockchain network. Similarly, it is also possible to identify the current number of blocks that have been processed in the server of the blockchain network "chain2". In order to proceed with the counting of the current number of blocks processed in the server, one of the best and easiest ways can be chosen in this porch (Atia et al., 2020). The command preferably used for this is “getinfo”. The “getblockchaininfo” command can be useful in generating the required information regarding the current status of the blockchain in the server.
c. Checking if an address has pending multiple approvers to grant a permission
In a network transaction of blockchain, every permission that is being revoked or granted contain special metadata. This makes it easier to set the permissions through revoke and grant commands which are available for multichain- cli. The first genesis block of the creator gets every regular permission automatically. As a result of that, the administrators have the permissions to grant permission to some different address. This can be performed using activate and admin permissions (Xu et al., 2020). If the MultiChain wallet comprises several private or public keypairs, it will be beneficial in operating restricted operations like stream creation of asset insurance. In this process, one of the keys will be ushered automatically in order to perform that operation.
d. How to run multichain-cli to show the help for getting info from command line mode forchain2?
After setting up the connection of the blockchain in the second server, it is required to run the following code:
multichaind chain2@ [ip-address] : [port]
As per the analysis of TANRIVERD? (2020), after the successful initialisation of the blockchain, the user will be informed, but he will not get permission to connect. It is required to connect the first server in order to add the permissions for the connection in this address for the second server.
multichain-cli chain2 grant 1.... Connect
This will allow me to reconnect the second server again. After the connection is successful, the node will set up the server, and it will display the address of the second node. For proceeding with the interactive node, both the server can use the following command for setting up the connection using the command multichain-cli chain2 (Blaauwendraad et al., 2019). After it is confirmed that the blockchain is working on both the servers, the getinfo command can be used in the command line to see the list of comments available in the network.
Question 7
Creation of a MultiChain asset “Orange”
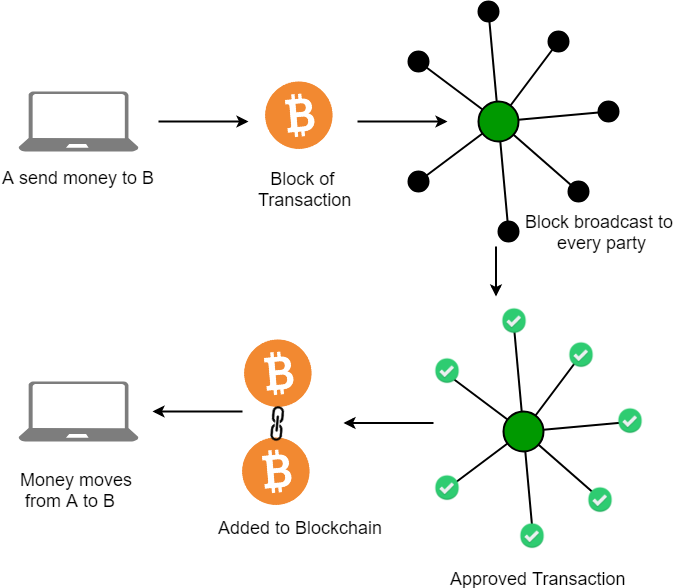
Figure 2: Blockchain Network Chain MultiChannel Asset “Orange”
(Source: Created by the Author)
A. The error which has been found in the multi-chain asset is the server error that occurs due to the applications. While saving the purchase, the error has been caused, which shows that the data class is null. It will prevent the asset from being created and edited effectively. The variation in the error has been found while loading the page in the system where the login details were not appropriate. The error, which has been mainly found in the asset "Orange", has reported an error in the file, which is actually not an error, but there was no helpful information in the file. In order to find the fundamental error in the asset, it is necessary to detect the issue directly via the workstation, which has created a level error, and thus the instruction is seen as an error, with an unexpected error that occurs mainly during the running of the program while uploading the specific file where the product has created the main issue (Ismailisufi et al., 2020). In order to solve the problem, it is necessary to review the systematic management area from where the errors have occurred and thus to monitor the Orange server log, which will help to determine the other product associated with "Orange '' that has caused the issue and hence it is often referred to as the product problem (Avantaggiato & Gallo, 2019). Moreover, suppose the problem product has a data class. In that case, it will appear mainly by editing the CMDB resources, which have been disabled with the help of the Symantec installation manager.
B. While running the system effectively, it has been found that other than the issue of "orange", there are many issues which have another 100 assets, which are mainly that the request of the object in the command is not valid and the parameters which are used for the order are not correct which have caused an internal error (Shrestha, Deters and Vassileva, 2019). Moreover, it has been found that while trying to edit the assets in custom security, it has created a significant issue while running the error. Mainly in the set of "Orange," while adding the dependencies, it has caused problems in the resource types that have formed a solution for the manager. Many times, if the data classes are uninstalled and corrupted, then it may create issues. The data command has been analysed that it has created an invalid address for the public key, which acts as a parameter. According to Oh et al. (2017), moreover, the multi-chain has run out of memory, outperforming the operations. Error is mainly validating the data structure, which has created issues in the command system. In the verification of the data, the whole arrangement has been found disrupted. Many times, the multi-chain is still warming up, which cannot create a response request. In order to resolve the issue, Symantec installation management needs to have repaired of the workstation still effectively (Cao & Wan, 2020). With the help of the CMDB solution, it will help to resolve the overall issue which is being faced by the asset.
Question 8
Creation of asset A and asset B for atomic asset exchange
A. An atomic swap can be discussed as one of the intelligent contract techniques which mainly enables the exchange of the cryptocurrency that has been used without the help of centralised intermediaries, especially the exchanges. Atomic swap mostly takes place between the blockchain with the help of cryptocurrencies. Thus, technology has been popular in every sector. Additionally, nowadays, the process of exchanging cryptocurrencies has been a complex and time-consuming process that occurs due to several reasons. In the above command, it is not an atomic swap as atomic swap includes both the parties which have acknowledged the receipt of funds within a proper time frame, which needs to use a cryptographic hash function. Since one of the parties in the common has failed effectively, then the parties have been unable to confirm the transaction (Gugger, 2020). So, the entire transaction has failed, which has become void and thus, the funds are not mainly exchanged. Atomic chain is primarily a technique of blockchain which has not been able to trade them directly. The nuclear chain is principally associated with the problems in the centralised exchange, which has not been detected in this server. Since the asset has two parties that are using two different transactions, it has been found that an atomic swap will not be conducted in this server.
B. For understanding the exchange offer that is offered by server 1, it is necessary to use createrawtransaction command, which mainly helps to send the quantity of the asset back to the command, and it has been referenced explicitly as changes which are at some point especially tends to be invalid. Another command which may help server 1 is alpha 11, which basically adds a new form of API known as disablerawtransation, which mainly takes care of the exchange offer that helps in preventing the ones which are being used by anyone else. With the help of the createrawtransaction command, it will effectively create a proper unsigned serialised transaction which mainly spends a suitable previous output that has created a new production. This will ensure that it will provide the command of all the products for a raw hex string that will encode all the transactions of the server effectively. The command will effectively help to create the unsigned serialised where no request URL will be shown up.
C. From the last result, it can be stated that the use of effective command will ensure that multi-chain API will also include the command-line tool in order to derive the previous instruction which has been provided in the server. Under the asset parameter, which consists of an offer and asks empty return list, will show the decoderawexchnage command, which has effectively created the 1 unit for asset 5. Node 1 will effectively help to send the output, while node two will send the work with the help of email and other channels, which will ensure that it will create the raw exchange. So, in the last instruction, it has suggested that the apple asset will be the output result.
References
Ahmad, A., Saad, M., Njilla, L., Kamhoua, C., Bassiouni, M., & Mohaisen, A. (2019, May). Blocktrail: A scalable multichain solution for blockchain-based audit trails. In ICC 2019-2019 IEEE International Conference on Communications (ICC) (pp. 1-6). IEEE. https://www.cs.ucf.edu/~mohaisen/doc/icc19.pdf
Alimehaj, V., Halili, A., Dervishi, R., Neziri, V., & Rexha, B. (2021). Analysing and comparing the digital seal according to eIDAS regulation with and without blockchain technology. International Journal of Information and Computer Security, 14(2), 171-191. https://www.researchgate.net/profile/Ramadan-Dervishi/publication/349581298_Analysing_and_comparing_the_digital_seal_according_to_eIDAS_regulation_
with_and_without_blockchain_technology/links/60527844299bf173674e0675/Analysing-and-comparing-the-digital-seal-according-to-eIDAS-regulation-with-and-without-blockchain-technology.pdf
Atia, G. K., Beckus, A., Alkhouri, I., & Velasquez, A. (2020). Steady-State Policy Synthesis in Multichain Markov Decision Processes. In IJCAI (pp. 4069-4075). https://www.ijcai.org/Proceedings/2020/0563.pdf
Avantaggiato, M. & Gallo, P., (2019, June). Challenges & opportunities using multi-chain for real estate. In 2019 IEEE International Black Sea Conference on Communications & Networking (BlackSeaCom) (pp. 1-5). IEEE. https://ieeexplore.ieee.org/abstract/document/8812780/
Blaauwendraad, B., Erkin, Z., Schwabe, P., Ersoy, O., & de Jong, B. (2019). Postquantum Hash-based Signatures for Multi-chain Blockchain Technologies (Doctoral dissertation, Master Thesis). https://www.ru.nl/publish/pages/769526/z05_2019_thesis_breus_blaauwendraad_final.pdf
Cao, L. & Wen, Z., (2020, June). Anonymous scheme for blockchain atomic swap based on zero-knowledge proof. In 2020 IEEE International Conference on Artificial Intelligence & Computer Applications (ICAICA) (pp. 371-374). IEEE. https://ieeexplore.ieee.org/abstract/document/9181875/
Cao, T., Yu, J., Decouchant, J., Luo, X., & Verissimo, P. (2020, February). Exploring the monero peer-to-peer network. In International Conference on Financial Cryptography and Data Security (pp. 578-594). Springer, Cham. https://orbilu.uni.lu/bitstream/10993/42573/1/43.pdf
Gugger, J.,( 2020). Bitcoin-Monero Cross-chain Atomic Swap. IACR Cryptol. ePrint Arch., 2020, p.1126. https://eprint.iacr.org/2020/1126.pdf
Ismailisufi, A., Popovi?, T., Gligori?, N., Radonjic, S. & Š&i, S., (2020, February). A private blockchain implementation using a multi-chain open-source platform. In 2020 24th International Conference on Information Technology (IT) (pp. 1-4). IEEE. https://www.researchgate.net/profile/Nenad-Gligoric/publication/339442490_A_Private_Blockchain_Implementation_Using_Multichain_Open_Source_
Platform/links/5e73dd6d458515c677c6213d/A-Private-Blockchain-Implementation-Using-Multichain-Open-Source-Platform.pdf
Ismailisufi, A., Popovi?, T., Gligori?, N., Radonjic, S., & Šandi, S. (2020, February). A private blockchain implementation using multichain open source platform. Blockchain technology assignment In 2020 24th International Conference on Information Technology (IT) (pp. 1-4). IEEE. https://www.researchgate.net/profile/Nenad-Gligoric/publication/339442490_A_Private_Blockchain_Implementation_Using_Multichain_Open_Source_
Platform/links/5e73dd6d458515c677c6213d/A-Private-Blockchain-Implementation-Using-Multichain-Open-Source-Platform.pdf
Kumar, V. V., Devi, M., Raja, P. V., Kanmani, P., Priya, V., Sudhakar, S., & Sujatha, K. (2020). Design of peer-to-peer protocol with sensible and secure IoT communication for future internet architecture. Microprocessors and Microsystems, 78, 103216. https://drive.google.com/file/d/1vgrlrBl6ete480WG_6YB-Jkz2MvDgLwE/view
Ma, S. (2018). Using blockchain to build decentralised access control in a peer-to-peer e-learning platform (Doctoral dissertation, University of Saskatchewan). https://harvest.usask.ca/bitstream/handle/10388/8401/MA-THESIS-2018.pdf?sequence=1&isAllowed=y
Monrat, A. A., Schelén, O., & Andersson, K. (2019). A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access, 7, 117134-117151. https://ieeexplore.ieee.org/iel7/6287639/8600701/08805074.pdf
Muthuraman, T., Pichiah, P. P., & Anuradha, S. (2019). Block-Chain-Based Security and Privacy in Smart City IoT: Distributed Transactions. In Handbook of Research on Implementation and Deployment of IoT Projects in Smart Cities (pp. 134-148). IGI Global. https://www.igi-global.com/chapter/block-chain-based-security-and-privacy-in-smart-city-iot/233270
Oh, S.C., Kim, M.S., Park, Y., Roh, G.T. & Lee, C.W., (2017). Implementation of blockchain-based energy trading system. Asia Pacific Journal of Innovation & Entrepreneurship. https://www.emerald.com/insight/content/doi/10.1108/APJIE-12-2017-037/full/html
Polge, J., Robert, J., & Le Traon, Y. (2021). Permissioned blockchain frameworks in the industry: A comparison. Ict Express, 7(2), 229-233. https://www.sciencedirect.com/science/article/pii/S2405959520301909
Shrestha, A.K., Deters, R. & Vassileva, J.,( 2019). User-controlled privacy-preserving user profile data sharing based on blockchain. arXiv preprint arXiv:1909.05028. https://arxiv.org/pdf/1909.05028
Syed, T. A., Alzahrani, A., Jan, S., Siddiqui, M. S., Nadeem, A., & Alghamdi, T. (2019). A comparative analysis of blockchain architecture and its applications: Problems and recommendations. IEEE access, 7, 176838-176869. https://ieeexplore.ieee.org/iel7/6287639/8600701/08922632.pdf
TANRIVERD?, M. (2020). Design and Implementation of Blockchain Based Single Sign-On Authentication System for Web Applications. Sakarya University Journal of Computer and Information Sciences, 3(3), 343-354. https://dergipark.org.tr/en/download/article-file/1167051
Tapsell, J., Akram, R. N., & Markantonakis, K. (2018, July). An evaluation of the security of the Bitcoin Peer-to-Peer Network. In 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) (pp. 1057-1062). IEEE. https://arxiv.org/pdf/1805.10259
Thin, W. Y. M. M., Dong, N., Bai, G., & Dong, J. S. (2018). Formal Analysis of a PoS Blockchain. https://research-repository.griffith.edu.au/bitstream/handle/10072/384235/Bai213834.pdf?sequence=1
Xu, Y., Huang, Y., Shao, J., & Theodorakopoulos, G. (2020). Multichain-MWPoW: A $ p/2$ Adversary Power Resistant Blockchain Sharding Approach to a Decentralised Autonomous Organisation Architecture. arXiv preprint arXiv:2004.04798. https://arxiv.org/pdf/2004.04798
Zaidi, S. Y. A., Shah, M. A., Khattak, H. A., Maple, C., Rauf, H. T., El-Sherbeeny, A. M., & El-Meligy, M. A. (2021). An Attribute-Based Access Control for IoT Using Blockchain and Smart Contracts. Sustainability, 13(19), 10556. https://www.mdpi.com/2071-1050/13/19/10556/pdf
Zhou, Q., Huang, H., Zheng, Z., & Bian, J. (2020). Solutions to scalability of blockchain: A survey. IEEE Access, 8, 16440-16455. https://ieeexplore.ieee.org/iel7/6287639/8948470/08962150.pdf












