Network Security Assignment: Discussion OnInformation Security Attacks
Question
Task: One area that has been especially frequent target of attacks is the information technology (IT). A seemingly endless array of attacks is directed at individuals, schools, businesses, and governments through desktop computers, laptops, and smartphones. The Privacy Right Clearinghouse (PRC) is a non-profit organisation which maintains a searchable database of security breaches that impact consumer’s privacy [1].
In this part of the assignment, select any two of the recent attacks by referring to PRC database (https://privacyrights.org/data-breaches). Carry out an in-depth literature review about these two attacks. Your discussion must explain following points with proper in-text citations.
• Identify and discuss main reasons for these attacks being successful.
• Report the importance of key terms in the information security: asset, threat, threat actor, vulnerability, attack vector, attack surface in the context of these two attacks.
• How could these attacks have been prevented if the five fundamental security principles- layering, limiting, diversity, obscurity, and simplicity- had been applied
Answer
Feedback (Part A)
The scores obtained in the previous part are good with a few areas that could have been improved upon. The scores suggest that the background to the network security and the associated security attacks are clear. There is good level of clarity on the attacks that occur and the mechanisms that are used to carry out the attacks. There are different types of security attacks that have been defined and it is always possible to learn more about these classifications. There is further knowledge that can be gained in the solutions and controls to manage the security risks.
Introduction
There are different forms of network security and the information security attacks that may take place. The malware attacks are extremely common and these include the malicious code or algorithm that may serve specific purpose. Some of the malware codes are design to capture the system activity while others may be designed to modify the information in an unauthorized manner. There are different forms of malware that has been developed and Ransomware is one of these forms. It is a malware that carries out the encryption of the file or files in the system or over the network [1]. Due to the encryption, the access of the user towards the files and the system gets blocked. The attacker then demands the user with a ransom to decrypt the files and provide the access. The ransom is charged using the different forms of Cryptocurrencies.
Variants of Ransomware
• WannaCry: It is one of the popular ransomware that is in existence and was identified in 2015. It led to the impact on more than 150 countries and over 1.25 Million systems across the globe. It impacted the systems with Windows operating system due to the underlying vulnerabilities in the OS.
• Cerber: It is the ransomware that targets the cloud-based Office 365 users. The ransomware makes use of the phishing attack to cause an impact on the users.
• Jigsaw: It is a lethal ransomware in which the encryption of the files over a system is carried out and these files are gradually deleted from the system unless the user agrees to pay the ransom amount. The deletion occurs at every hour and the maximum timeframe that is provided is 72 hours [2].
• CryptoLocker: It is the ransomware that was first identified in 2013 and it makes use of the botnet approach to carry out the ransomware attack.
Working Mechanism of Ransomware
There are different mechanisms and approaches that are followed and carried out by the ransomware. The most common approach that is followed is the use of emails which are used to launch and spread the malware on the system. The phishing approach is used by the ransomware codes in which the users are tricked to install the infected files. The use of the suspicious/duplicate links can be done. The attackers obtain the list of the emails usually from the web databases. The use of compromised websites is done to obtain the list of the emails [3].
As soon as the users install the files, there is encryption of the files on the system of the users that occur. Once the files are encrypted, the users are asked to pay the ransom amount to provide the access again. Once the user pays the ransom amount, the attacker may or may not provide the access. The illustration of the basic mechanism that is followed is done in the figure below.
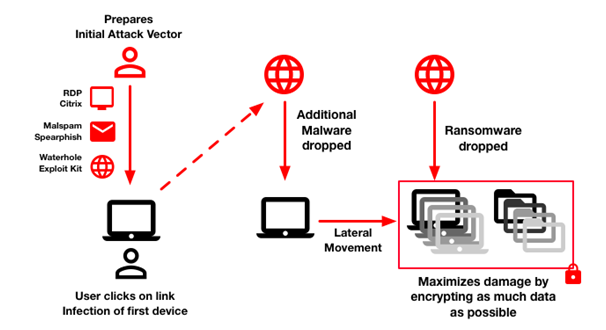
Ransomware Attack Mechanism
Potential Threats posed by Ransomware
There are several threats that the ransomware possesses to the users and the systems.
• The breaching of the information is the primary threat as the information present in the system is accessed and encrypted by the attackers.
• The availability threats are associated with the ransomware in which the access to the files or the system is blocked.
• There are monetary losses that the users face as the access is not provided unless the user agrees to pay the ransom amount to regain the access [4].
• There can be integrity violations that may arise if the attacker modifies the files that are captured.
• The loss of data may occur if the files present in the system are deleted.
Case study – Ransomware Attacks
One of the recent ransomware attacks reported is of Maze Ransomware Attack that emerged in April 2020. The attack impacted the Indian IT firm called Cognizant. The ransomware attack took place and it disrupted the services being provided to the clients.
The Maze ransomware attack first occurred in 2019 and it has gained popularity in early 2020. The Maze ransomware attack is different from the usual ransomware attacks. In this case, the attacker can transfer the files on the attacked system on its own server. This possesses an even severe risk as there may be issues on integrity violations and data loss that may arise. The flow that is involved includes the stealing of the data sets and it is then followed by the access block [5].
Recommendations – Mitigation Tool
The anti-malware tools that have been developed come with the ransomware protection with the increase in the occurrence of the ransomware attacks. The tool that is recommended for ransomware protection is the Malwarebytes anti-malware tool that comes with the ransomware mitigation and protection mechanisms.
Malwarebytes make use of the heuristic analysis to make sure that the new strains of malware are identified and the removal of the same can be effectively done [6]. The tool provides protection from the phishing scams and also ensures that the new infections do not take place. The tool also makes sure that the infected files and software does not get downloaded on the system. The tool comes with a 14-day trial and then the premium version of the tool can be installed. The tool also includes Adwcleaner that removes the unwanted codes and files from the browsers that the users usually use. The tool provides the overall system, information, and network security so that the associated security risks do not occur.
References
[1] A. O. Almashhadani, M. Kaiiali, S. Sezer, and P. O’Kane, “A Multi-Classifier Network-Based Crypto Ransomware Detection System: A Case Study of Locky Ransomware,” IEEE Access, vol. 7, pp. 47053–47067, 2019.
[2] Norton, “Norton,” Norton.com, 2020. [Online]. Available: https://us.norton.com/internetsecurity-emerging-threats-jigsaw-ransomware-wants-to-play-a-game-but-not-in-a-good-way.html.
[3] T. August, D. Dao, and M. F. Niculescu, “Economics of Ransomware Attacks,” SSRN Electronic Journal, 2019.
[4] Arivudainambi D., Varun Kumar K.A., Vinoth Kumar R., and Visu P., “Ransomware Traffic Classification Using Deep Learning Models,” International Journal of Web Portals, vol. 12, no. 1, pp. 1–11, Jan. 2020.
[5] A. Chandrashekhar, “Cognizant hit by ‘Maze’ ransomware attack,” The Economic Times, 21-Apr-2020.
[6] Malwarebytes, “Malwarebytes Cybersecurity for Windows, Mac, Android & iOS,” Malwarebytes, 2019. [Online]. Available: https://www.malwarebytes.com/.












