Computer science assignment on upgrading the computers and the servers of Amcor
Question
Task: Write acomputer science assignment which will include step-by-step help desk procedures. Choose an industry that you are most familiar with so you can add industry specific insights. Frame a proposal for the company to transition to Windows and Linux.
Answer
EXECUTIVE SUMMARY
Amcor private ltd company wants to upgrade their infrastructure from the existing to new with the transition of windows and Linux. In this computer science assignment, the requirement of the company during the transition of windows and Linux with the recommended software and the installation procedures are described.
INTRODUCTION AND BACKGROUND to thecomputer science assignment
Amcor private ltd, a manufacturing company that has its branches all over the states in Australia and they wantto upgrade their computers and the servers on the network they have existing features such as windows server 2012, linux server, mac OS, windows 10, 8.1 , 7 and vista. Now they are planning to transit to windows and linux. This computer science assignmentconsists of information related to the frequently asked questions and help desk procedures that the company can use when they required.
Microsoft timeline
The following are the timeline of microsoft (Horsman, et al., 2021) (ilag, et al., 2022).
In the year 1975, Microsoft is found by gates and allen
In 1978, the company made a profit of $ 1 million
In 1979, the company moves from Albuquerque to Bellevue
In 1981, the first operating system MS-DOS of Microsoft is launched on IBM computers
In 1983, MS-DOS is released on Compaq PC and got the license for its operating system
In 1985, the graphical operating system of Microsoft, Windows 1.0 is launched
In 1986, the company is moved from Bellevue to Redmond.
In 1990, Microsoft office, and windows 3.0 is released
In 1994, Microsoft has a deal with the justice department and it is a starting phase of legal troubles.
In 1995, windows 95 is released.
In 1995, internet explorer is released.
In 1998, the proceedings started in Microsoft and the united states
In 2000, gates has become the CEO
In 2001, Xbox is launched
In 2004, windows XP is launched and it became popular
In 2010, a modern version of Windows OS is released.
In 2012, Microsoft enters the tablet market
In 2014, Ballmer has become CEO
In 2015, the latest version of the windows operating system windows 10 is released.
In 1986, the stock has not increased. Microsoft is traded for $5 and for the past five years, the share market of Microsoft rises from $40 to the current price.
Legacy billing program
Yes, the company considered in the computer science assignmentcan run the legacy billing program that is designed for windows vista. The updated version of windows will have a previous version program with additional features for security and other systems. it is obvious that there will not be any compatible version but the operating system should be 16-bit if the program is designed for the 16-bit operating system.
Advantages of upgrading OS
Updates help to fix security issues
When there is a security issue then it will be a greater possibility for the hacker to get into the system because the outdated software and old software are vulnerable to security attacks and cybercriminals. This is a major flaw in the operating system, browser, or any application. These programs mentioned in thecomputer science assignmentshould be updated regularly to have a secure environment.
New features
In addition to the security flaw, the software updates as per the computer science assignmentalso has improved features with various applications. The existing system will not be combability for the latest software upgrades and so there should be an update of OS too.
Improved efficiency
Software updates provide more security features along with an improved end-user experience. OS updates improve the system’s performance. Developers of the computer science assignmentare looking for new ways to improve the software so that the user can achieve efficient usage.
Low cost
Maintaining the old system, takes more investment rather than upgrading it. So it is benefits to upgrade the system rather than changing the system.
Disadvantages
Compatibility
There will not be sufficient hardware to run the operating system. There will not be enough RAM to upgrade the system. Before upgrading, it should be verified for its compatibility. As per the computer science assignment there is also updated version which is compatibility with the new OS.
Time
It takes more time to upgrade the system. Initially, it will take a few hours but it requires more time to install successfully and to check whether the remaining programs and apps are working correctly. AS per the computer science assignment after installation, it should be checked for system compatibility.
Migrating from the macOS to windows
The following impacts when the marketing department migrates from mac OS to windows
Data loss
When migrating from the Mac OS to windows, it is found in the computer science assignment that there will be a data loss.
Driver issues
If the business environment is suddenly changed then there will be an inconvenience in using the new operating system where there will be driver issues.
Adaptability
When the marketing department has been using the Mac OS for a long time, they will be well experienced in it. When suddenly they are migrating it to windows then it will take time to learn the functionalities of the operating system and to work with it.
Recommended server platform
It is recommended in thecomputer science assignmentto use a virtual box for the organization. It has high features where the performance is also high. It is an open source and there will not be any cost issues. Virtual box can run on windows OS, Linux OS, and many guest operating systems.
VPN INSTALLATION
VPN means Virtual Private Network. It denotes a way to create a secured network connection using the public network. As per the computer science assignmentVPN encrypts the traffic on the internet and modifies the online identity.it is very difficult for the hacker to track the network and retrieve the data. The encryption occurs in the real-time setup (Tonello, 2021).
VPN hides the IP address of the network and directs it using the configured remote server that is run by a VPN host. When the Internet Service Provider and the hackers try to visit the website, it could not be seen. VPN filters the data and turns all the data into gibberish. As per the findings of computer science assignmentVPN connection disguises the traffic in the network and protects it from third-party users. It provides various benefits such as secured encryption, access the regional content, and secured data transfer.
There are different types of Virtual Private Network and they are SSL VPN, site-to-site VPN, and Client-to-server VPN.
SSL VPN
This type of VPN as per the computer science assignmentwill be suitable for users who are working from a different location. When an SSL-VPN solution is used, the users can connect the devices using the respective hardware box. When the user wants to connect, they use HTML-5-Capable browser to call the company’s login page. The browser will be available for the virtual operating system. access is provided using the username and password.
Site-to-site VPN
It is a private network that is suitable for hiding the intranets and allowing the users to secure the network access and their resources. As per the computer science assignment it will be suitable for the organization in multiple locations. It is preferred by large organizations and it is an effective way to communicate between large departments.
Client-to-server VPN
This VPN will be suitable when it is connected to the home PC of the company. The employees can call the company network from the home and get a secure network connection. As per the computer science assignmentVPN should be installed by the client and configured to the company’s network.
Before installing the VPN, it is necessary to know about different methods of installation such as VPN client, Browser extension, and router VPN.
VPN client
Software should be installed in the VPN client. It is configured to satisfy the requirement of the endpoint. While setting the VPN, the endpoint will execute the VPN link and connect to another endpoint.
Browser Extensions
This can be added by the web browser such as google chrome and firefox. As per the computer science assignment it will be easy to switch and configure. It can be used forsharing information on the internet.
Router VPN
If many devices are connected to a single internet connection then it is very simple to connect the VPN to the router rather than installing it on each device. As per the computer science assignment it is useful for protecting the device with an internet connection.
The following instructions should be followed while implementing the VPN connection in windows (Chawla, et al., 2019):
Step 1: there are many VPN services are available which can be downloaded and installed to get ansecure connection.
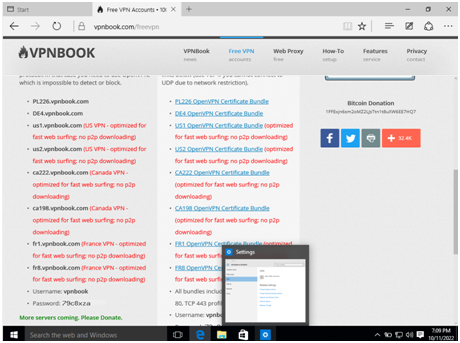
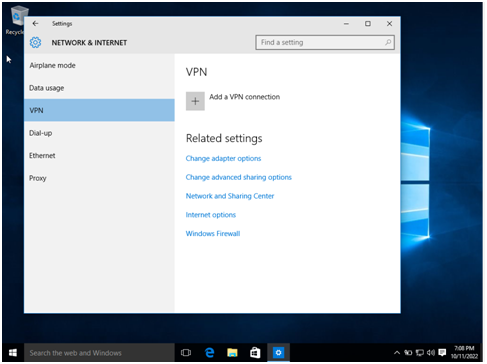
Step 2: In the windows, select the start button and search for settings. In settings select VPN and click on add a VPN connection.
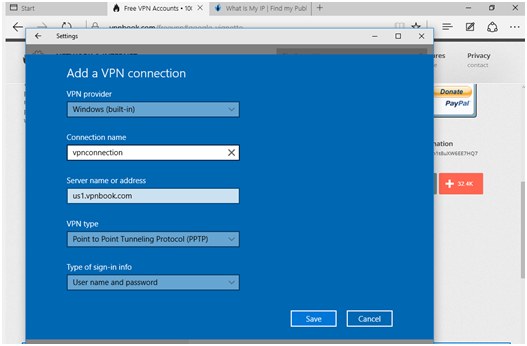
Step 3: In adding a VPN connection, give a VPN provider, connection name, server name or address, VPN type, and type of sign-in info.
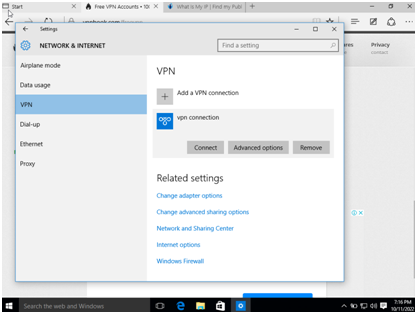
Step 4 in the computer science assignment: After creating a VPN connection, it will ask for connecting, an advanced option, or to remove. If the connection wants to be established then click connect.
Step 6 in the computer science assignment:
While connecting VPN, sign in using the user name and password.
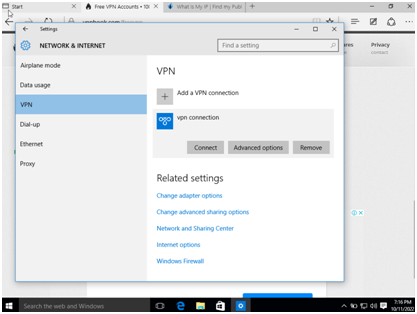
Step 7: After establishing the connection, check for the IP address. A link will be shown to hide the IP address using the VPN.
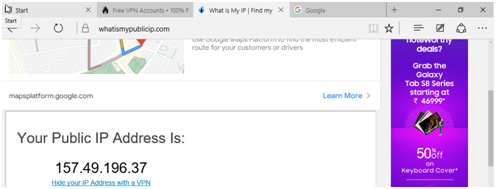
Step 8 in the computer science assignment: Here we can see the IP address is changed using the VPN service.
Multifactor authentication factors
Multi-factor authentication is an authentication method that is used for providing two or more verification factors to get access to the resources such as online accounts, applications, or Virtual Private Networks. It is important as per the computer science assignmentfor implementing the identity and Access Management policy. Instead of asking the username and password, verification factors are considered in the Multiple factor authentication that reduces the occurrence of the cyber attack. It improves the security of the organization where the user will identify them by using additional factors than the username and password. Using the username and password are vulnerable to cyberattack and it can be hacked using the brute force method. In order to ensure security, fingerprint, physical hardware and other elements are considered in the multiple-factorauthentication that increases the security among cyber criminals. As per the computer science assignment the most commonly used Multiple factor authentication is a one-time password. It ranges from 4-8 digits that are received in email, SMS, or other applications. Whenever the user requested to log in, the OTP will be generated (Ibrokhimov, et al., 2021).
Authentication factors:
The factors considered for multiple authentications are as followsin the computer science assignment(Ometov, et al., 2018):
Knowledge factor
This factor is based on the password, PIN generation or answering to the security questions that is known only to the user. To use this factor in the computer science assignment, the user should enter correct information that matches the information which is stored in the database.
Possession factor
Users have smartphones and gadgets so one-timepasswords are sent to access the application. Most of the authentication occurs using the OTP method.
Inherence factor
This factor in the computer science assignmentis based on the fingerprint, scanning of the retina, facial recognition, and voice recognition.
To use multi-factorauthenticity, it requires two different technologies. Using a password and pin setup does not consider to be multi-factor authentication. It includes the combination of PIN and facial recognition.
Multi-factor authentication technologies
The following technologies that usesmulti factor authentication are as follows (Abhishek, et al., 2017):
Biometric authentication
Biometrictechnologiesuse secure authentication using mobile devices. Commonly used biometric authentication methods are fingerprint scanning and facial recognition.
Hardware tokens
Hardware authenticators are easy to access the devices when the device owner carries to access the network. Using OTP as per the computer science assignment, the application is accessed. For example, OTP is required to access the ATM to withdraw money.
Mobile authentication
This type of authentication is to verify the user using the android or iOS devices by itself. It makes the user log in to the secure location to enhance security.
INSTALLING VIRTUAL BOX
Step 1: Download the virtual box 6.1.38 version from https://www.virtualbox.org/. start the setup by giving next (Li, 2010).
Step 2: Select the required features to install the VirtualBox setup.
Step 3 in the computer science assignment:a warning dialog box appears for a network reset connection. Proceed with the installation by giving yes.
Step 4: Installation is in progress.
Step 5 in the computer science assignment:complete the installation by giving finish.
Step 6:After installation opens the virtual box.
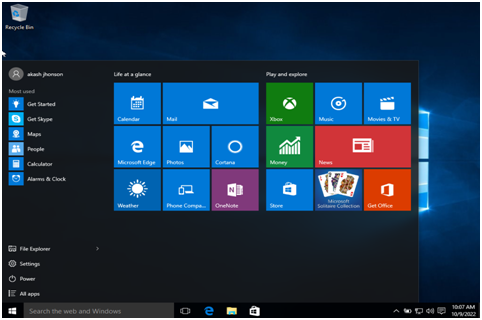
Step 7 in thecomputer science assignment: Go to windows to perform the security settings.
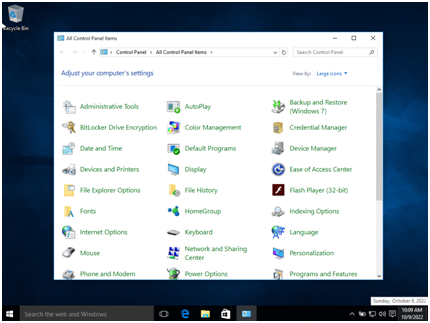
Step 8:Go to the control panel and search for administrative tools.
Create VM
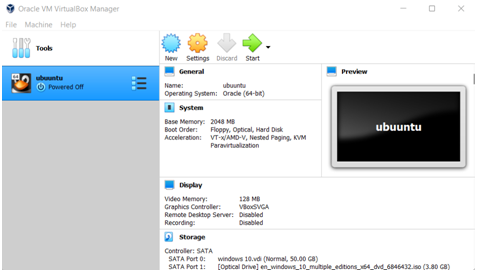
Step 1 in the computer science assignment: open the VirtualBox to create VM.
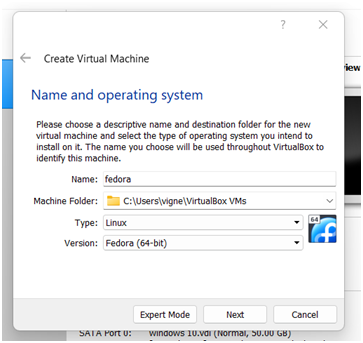
Step 2: a dialog box appears to give the name, machine folder, type, and version.
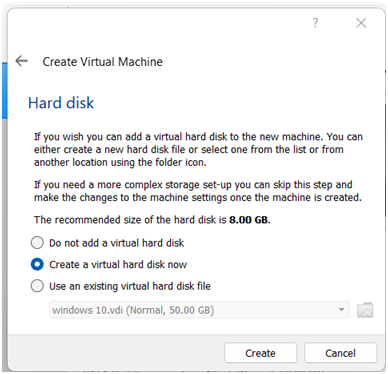
Step 3 in the computer science assignment:Selectthe create a virtual hard disk now option.
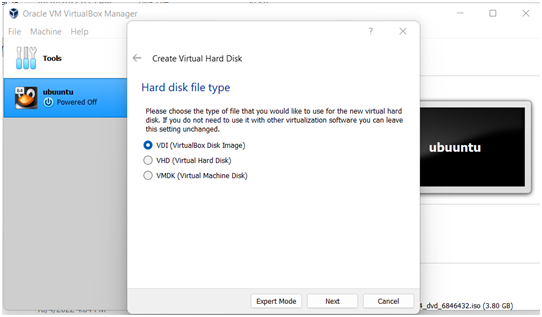
Step 4:Create a virtual hard disk by selecting VirtualBox Disk image.
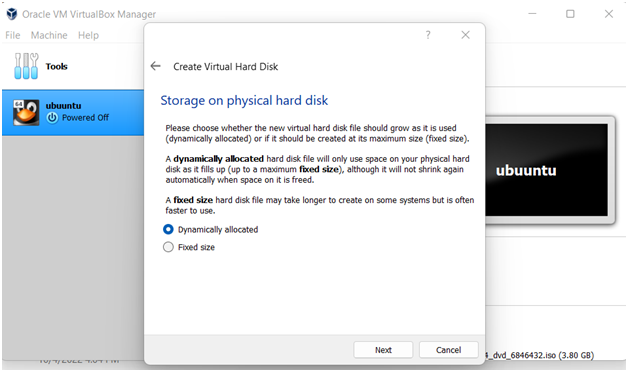
Step 5 in the computer science assignment:Selecta dynamic allocation as a storage option and give next.
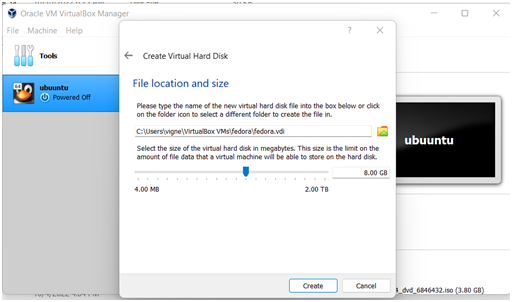
Step 6:Select the location of the fedora, the size of the virtual hard disk, and then select create.
Step 7 in the computer science assignment: Select choose to start the VM creation.
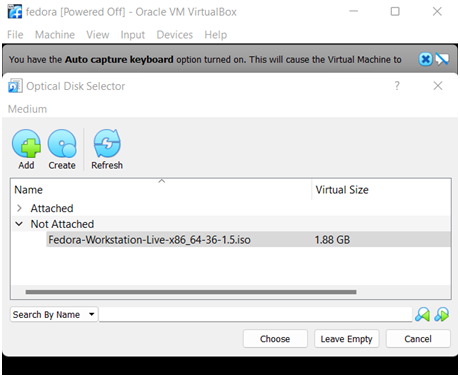
Step 8: Select and virtual optical disk file to start the virtual machine and give a start.
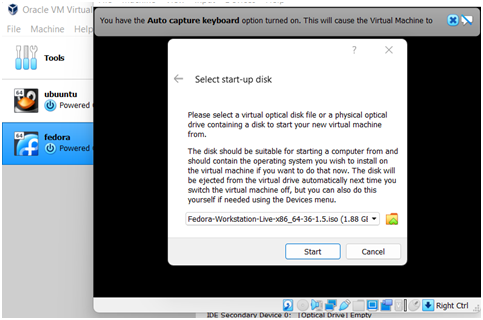
Step 9 in the computer science assignment: virtual machine is started.
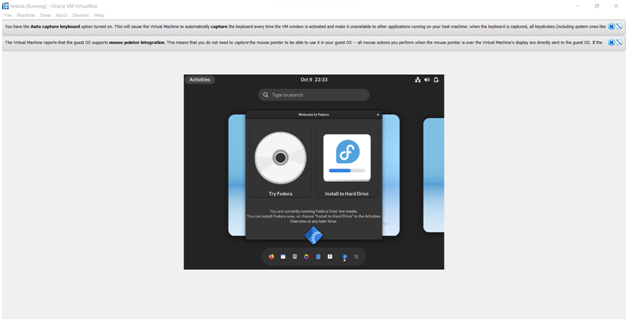
Step 10: installation of fedora is started.
Step 11 in the computer science assignment: select the local standard disk
Step 12: installation summary is shown before installation.
Step 13 in the computer science assignment: installation progress is started.
Step 14: homepage of fedora
Local security policy
Step 1 in the computer science assignment: In administrative tools, select local security policy.
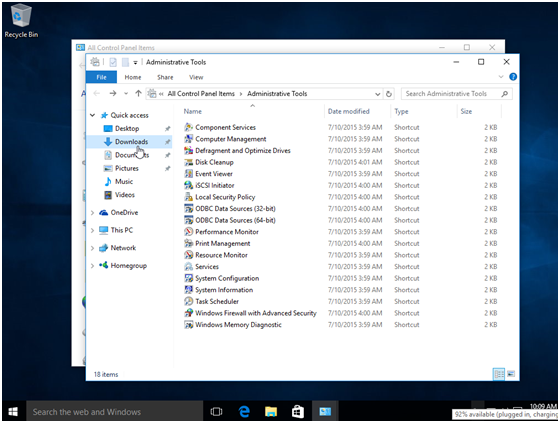
step 2: local security policy dialog box appears.
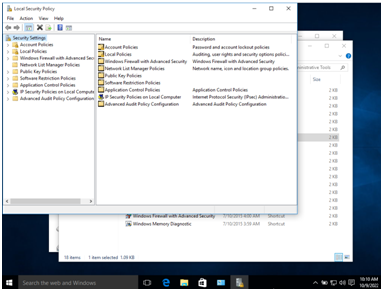
Step 3:
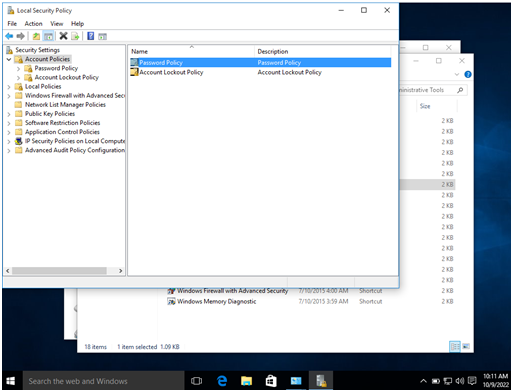
In account policies, go to password policy.
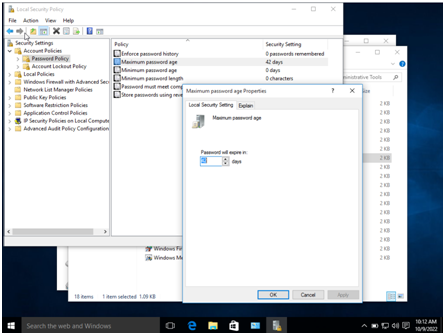
Step 4 in the computer science assignment: set minimum password age, so that it will expire within the given age.
Step 5: in audit policy, select audit logon events to audit the events.
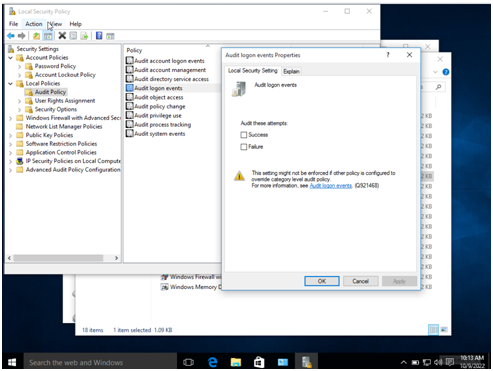
Troubleshootingproblemsand solutions in the computer science assignment The following are the troubleshooting methodology that should be used (Zaripova, 2021):
Identifying the problem
The first method in troubleshooting as per the computer science assignmentis to identify the root cause of the problem. to identify that the user should be questioned. After getting the information, the backup should be taken before starting any recovery process.
Establishing the cause
It is necessary to consider the list of probable cause, prioritize it and questionsrelated to the issue. If the cause could not be determined then it is considered to be ahigher-level problem.
Testing the cause to determine the original cause
From the most common causes, create a theory. If the original cause is confirmed then go to the next step. If it is not confirmed then do step one or two.
Establish the action plan and execute it
For a simple issue as per the computer science assignment, it requires a simple plan but for a complex problem, it requires an action plan. Based on the problem the plan is done.
Verify the system functionality
After executing the plan, it is necessary to verify the functionality of the system. if the problem can be prevented then it can be secured using preventive measures.
Document the troubleshooting process
After completing all the steps, document the process. It is necessary to document the findings, actions and outcome so if any problem gets repeated it can proceed with the troubleshot information.
Six operating systemissuesand solutions
Abnormal Operation system functioning
If the operating system is not responsive then restart the computer and run for virus scan. To solve this issue mentioned in the computer science assignment, install and antivirus software.
Windows do not boot
If there is trouble in booting the windows then it should be solved by reinstalling with the windows recovery disk.
Peripherals issues
Sometimes there will be an issue in connecting with the peripherals such as keyboards and mice. This can be solved by reinstalling the drivers and establishing connection.
Blue screen
This is the most terrible problem where it denotes there is acritical issue in the computer. It results in data loss or even worse. Sometime while updating the OS, blue screen error arises. This can be solved by shutdown the computer and restarting it.
Out of memory
This problem is due to the fragmentation of the C drive. It is not a big issue and it can be solved by basic software cleanup. Go to task manager and run a quick system check to know which application takesthe most CPU resources and RAM resources. Remove unnecessary application that is running in the background.
CONCLUSION
The necessary ugpgradations of the Amcor company are discussed in the computer science assignmentwith step-by-step procedures for installing the software such as virtual box, VPN, and fedora workstation. Detailedinstruction and introductionare given in the computer science assignmentfor the upgradation of windows and Linux operating system.
Appendix
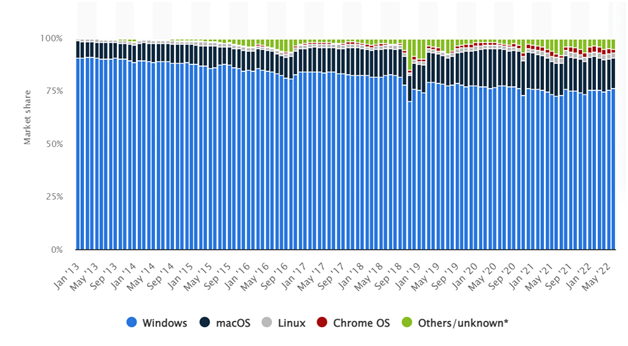
Microsoft market share with competitors
References
Abhishek, K., Roshan, S., Kumar, P., & Ranjan, R. (2013). A comprehensive study on multifactor authentication schemes. In Advances in computing and information technology (pp. 561-568). Springer, Berlin, Heidelberg.
Chawla, B. K., Gupta, O. P., & Sawhney, B. K. (2014). A review on IPsec and SSL VPN. International Journal of Scientific & Engineering Research, 5(11), 21-24.
Horsman, G., Caithness, A., &Katsavounidis, C. (2019). A forensic exploration of the microsoft windows 10 timeline. Journal of forensic sciences, 64(2), 577-586.
Ibrokhimov, S., Hui, K. L., Al-Absi, A. A., &Sain, M. (2019, February). Multi-factor authentication in cyber physical system: A state of art survey. In 2019 21st international conference on advanced communication technology (ICACT) (pp. 279-284). IEEE.
Ilag, B. N., &Sabale, A. M. (2022). Microsoft teams overview. In Troubleshooting Microsoft Teams (pp. 17-74). Apress, Berkeley, CA.
Li, P. (2010). Selecting and using virtualization solutions: our experiences with VMware and VirtualBox. Journal of Computing Sciences in Colleges, 25(3), 11-17.
Malallah, H., Zeebaree, S. R., Zebari, R. R., Sadeeq, M. A., Ageed, Z. S., Ibrahim, I. M., ... &Merceedi, K. J. (2021). A comprehensive study of kernel (issues and concepts) in different operating systems. Asian Journal of Research in Computer Science, 8(3), 16-31.
Ometov, A., Bezzateev, S., Mäkitalo, N., Andreev, S., Mikkonen, T., &Koucheryavy, Y. (2018). Multi-factor authentication: A survey. Cryptography, 2(1), 1.
Tonello, J. S. (2022). Setting Up a Virtual Environment. In Practical Linux DevOps (pp. 23-72). Apress, Berkeley, CA.
Zaripova, D. A. (2021). Network security issues and effective protection against network attacks. International Journal on Integrated Education, 4(2), 79-85.












