Business Analytics Assignment On Security And Privacy Challenges In The Big Data Era
Question
Task: This assessment item relates to the unit learning outcomes as in the unit descriptor. This assessment is designed to improve student presentation skills and to give students experience in researching a topic and writing a report relevant to the Unit of Study subject matter.
INSTRUCTIONS
Perform a literature review on a known topic in business analytics. It can be any topic on tools, methodologies or applications.
Some examples include, but not limited to:
1. Use of predictive analysis in healthcare industry
2. Comparison of BI tools
3. Techniques of predictive analysis
4. Methods of representing multi-dimensional data in visualisations
5. Analytics techniques to improve logistics management
6. Security of data and privacy concerns in analytics
Please note that this is an individual project. Discuss with your lecturer before week 7 to decide on a topic. The topic needs to be chosen before week 7.
Based on your review you need to submit a report in IEEE format; see the word file in the moodle. Submit your report in a word or pdf format. Your report should be limited to 1200-1500 words.
Answer
ABSTRACT – As there is a wide variety of data in world which is mainly brought by mobile technologies, wearable devices and internet of things (IOT), so for that data analysts are looking for solutions like Big Data so that it will help them to gather more and more information and grab new opportunities and values and increasing the productivity of organization. These days’ big data is everywhere right from your social media to your personal medical records. This paper explains characteristics as well as definition of Big Data, its environment and also highlights the security and privacy challenges. This paper helps people to take advantages if big data without compromising their privacy.
INTRODUCTION
The growth of global data by individuals as well as companies contributes partially for rise in unstructured data such as videos, photos and because of social media data production in 2020 in 44 times than that in 2009. Such increase in data production has led to increase in storage space called big data. Big Data these days has become very important for a lot of areas such as government, enterprises, sciences to the extent that government in US has made a report for public which includes the importance of big data as well as challenges which mainly includes security and privacy. All reports says that there should be a legal framework so there is no breach of one’s security and privacy and one can get maximum benefit from Big Data.
Security And Privacy Challenges In Big Data Era
A. Big Data
Big Data is the term which is used for complex or technical datasets which is not managed by software characterised via 5Vs those are Velocity, Volume, Value, Veracity and Variety. Figure 1.1 below shows the same.
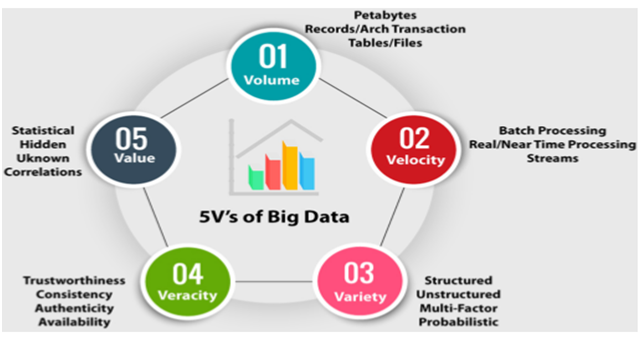
Fig 1: 5 Vs of Big Data
1. Volume-The ability of processing and storing large amount of data is the biggest challenge for Big Data especially when volume is so much and companies find it difficult to find the achieve logs. For example in year 1999 Walmart stored data 1000 TB of data and now in 2012 the data was 2.5 petabytes.
2. Veracity- When people are working with big data there is a possibility of dirty data as well which means data which is not 100% correct. So they should be sure that the source is good because the quality and accuracy of data depends on that.
3. Value- Although there are a many values in using of big data but unless it gives us return on investment installing IT infrastructures system is useless as well as costly.
4. Variety- There are many varieties as well including unstructured, structured or semi structured data which makes it quite challenging for data analysts to classify and their placement in relative database.
5. Velocity- It refers to the speed at which data or information is flowing, created, and stored or being analyzed these days or the hundreds of hours of content uploaded on YouTube every day.
B. Big data security and privacy
Tradition security has brought several changes. Since big data has been introduced to the world, the changes have been made as the traditional options of security weren't enough for these files. Processes like firewalls and complex encryption algorithms helps in identifying security threats. Prevention from the malicious use of some unknown data and prevention of breaking off the network are some other perks of having a good security option.
However, they face a dilemma called security triangle, which states that as employee takes higher security measures it negatively affects the system’s functionality. For example if a specific regulation restricts companies from analysis and manipulation of data then companies will not be able to enhance its business so therefore they will require a balanced approach to analytics and regulations to ensure companies’ right of analysing and manipulating data as well taking care of their personal data. To address these concerns many of the issues related to big data security and privacy are listed but still there is a need for research. Big data challenges from five different perspectives are cloud security, handoop security, key management, data security, monitoring and auditing.
C. Cloud Security
Cloud computing is widely used with reference to big data because of the large number of advantages it provides for example on-demand widespread access, service availability and sharing of resources.
However, cloud computing also has some negatives as it faces security challenges, since it has multiple principals and areas like resource sharing, networking, virtualization, databases and operating systems etc [1]. One of the problems with cloud computing is protecting storage data so for that service providers of cloud computing has come out with more secure ways of sharing the big data on platform of cloud. These providers of cloud computing gives their clients guarantee that they will not face any issues like loss or theft of data.
D. Monitoring and Auditing
Monitoring and auditing is an important security management, it helps providers of service from security breaches by simply checking the traffic on network and using the information taken to apply or adjust some security measures [2]. While monitoring network it mainly focuses on studying and collecting to forecast interventions; network auditing is referred as measurable and systematic security policy, which throws a large impact on security network.
1. Network monitoring: There are few factors that should be analyzed if prevention architecture and intrusion detection to be applied to monitoring security network [3]. Because of the difference in big data, it becomes important to deploy a monitoring system ready for detecting anomalies within the data.
2. Network auditing: It has become obvious that big data has extremely impacted the way of data analytics done in general; there are many challenges also in reference with data auditing when it is concerned with big data availability and integrity.
3. Key Management:In this approach, data can be filtered, reviewed, clustered and finally differentiated based on its level of sensitivity and type, after that certain data nodes are made in database [4]. To give security to certain data nodes, a suite of security was designed which contained many algorithm and security standards in relation of data node.
4. Data security (Anonymization): There are many people who have doubts on harvesting and data collection with reference to the right of user to privacy. The most important responsibility of publishers of data is to assure privacy and data security; though it may seem non-achievable at some point. Privacy Preserving Data Publishing (PPDP) shows us the ways in which they can publish data by giving them guarantee for their right to privacy [5]. There is an urgent need to demise policies for them.
E. Big Data Security and Privacy Analyses
As all know many of the big companies use big data for research or marketing purposes but what they lack is fundamentals, if there is not proper law followed they can place themselves serious problems as this will ruin their company name[6]. As traditional techniques cannot take care of that so people need to look for security and privacy issue that is why all companies need new mechanism. So there are many other mechanisms which are used like encryption lodging and many more.
Big Data not only deals with security problems but also with privacy issues it is as important as security as these days’ data is in petabytes a lot of data is stored including personal data which anyone can take advantage of and intervene in someone’s personal space. But big data analytics helps people in stopping malicious intruders and hence people can protect our privacy.
The personal who has data is king [7]. These days’ people sell data as it is very important so they should protect their personal data from any mis-happenings.
According to the latest news, National Security Agency (NSA) of Unites States is collecting personal data of civilians available on internet in the name of protecting them but these challenges should overcome and that could only be done when there is proper law or rules and regulations are made [8]. According to a study in cloud security alliance privacy and security is divided into 4 categories those are 1- Data Privacy, 2- Infrastructure Security, 3- Integrity and Reactive Security and 4- Data Management as explained below:
1. Data privacy: it includes privacy of data analytics, the encryption of data centers, and its control.
2. Infrastructure Security: it includes nodes, distributive programming, data, and security practice and internodes communication.
3. Integrity and Reactive Security: it includes monitoring of real time data and actions and filtering them.
4. Data Management: it refers to lodging transactions, data storage security, the provenance of data and security.
Conclusion
The main objective of Big Data analytics is to gather information from a large amount of heterogeneous data. However a large volume of data comes with certain security and privacy concern which was discussed in this paper earlier. It was discovered that Big Data has some different requirements regarding security and privacy in different areas like analysis, storage and transfer. On addition to that there are many studies done on big data security and privacy on the basis of that it was found that it was important to monitor traffic on network for detecting suspicious behavior; data which is transferable should be encrypted and personal data should be kept secured. All types of communication should be taken over through secured channels. Personal data should be given priority. There are some advantages as well of big data which includes that there is no need of deleting data or maintaining old logs because there is plenty of space in it. Information might be useful to in future for forensic purposes as well as many other uses like predicting future attacks and also cheaper and smarter security in comparison of traditional methods.
REFERENCES
[1] C. Wang, "Research on the Protection of Personal Privacy of Tourism Consumers in the Era of Big Data," 2018 International Symposium on Computer, Consumer and Control (IS3C), Taichung, Taiwan, 2018, pp. 428-431.
[2] S. Sathya and T. Sethukarasi, "Efficient privacy preservation technique for healthcare records using big data," 2016 International Conference on Information Communication and Embedded Systems (ICICES), Chennai, 2016, pp. 1-6.
[3] Y. Zhu, Y. Zhang, J. Wang, W. Song, C. Chu and G. Liu, "From Data-Driven to Intelligent-Driven: Technology Evolution of Network Security in Big Data Era," 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 2019, pp. 103-109.
[4] S. Arora, M. Kumar, P. Johri and S. Das, "Big heterogeneous data and its security: A survey," 2016 International Conference on Computing, Communication and Automation (ICCCA), Noida, 2016, pp. 37-40.
[5] M. M. H. ONIK, C. KIM and J. YANG, "Personal Data Privacy Challenges of the Fourth Industrial Revolution," 2019 21st International Conference on Advanced Communication Technology (ICACT), PyeongChang Kwangwoon_Do, Korea (South), 2019, pp. 635-638.
[6] P. Johri, A. Kumar, S. Das and S. Arora, "Security framework using Hadoop for big data," 2017 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, 2017, pp. 268-272.
[7] H. Imabayashi, Y. Ishimaki, A. Umayabara and H. Yamana, "Fast and space-efficient secure frequent pattern mining by FHE," 2016 IEEE International Conference on Big Data (Big Data), Washington, DC, 2016, pp. 3983-3985.
[8] G. Wang, R. Lu and C. Huang, "PSLP: Privacy-preserving single-layer perceptron learning for e-Healthcare," 2015 10th International Conference on Information, Communications and Signal Processing (ICICS), Singapore, 2015, pp. 1-5.












