Information security assignment: discussion on e-fail and KRACK attacks
Question
Task: This assessment asks you to apply what you have learnt on the module to two recently discovered, very high-profile vulnerabilities, are commonly referred to as E-FAIL (original paper here: https://www.usenix.org/conference/usenixsecurity18/presentation/poddebniak) and KRACK (original paper here: https://papers.mathyvanhoef.com/ccs2017.pdf). Answer the following questions in part a for E-FAIL, and part b for KRACK. I expect answers to be between 4 and 8 pages in total.
Question 1:
Research each attack and explain the cryptographic weaknesses that make the attack possible, and explain how the attack is performed.
Question 2: 30%
Explain what can be done with the E-FAIL and KRACK attacks What do each of them allow an attacker to do, and what kind of access does the attacker need
Question 3: 30%
Assume you have been asked by a business to assess the risks these attacks pose to them. Write some advice for the business. Can the business know if the attacks were used against them? State what the impact of the attacks might have been and what the business should do.
Answer
Introduction
Information security is essential for every business organization. There are new forms of security attacks that are emerging in the markets and cryptographic attacks are new inclusions in the list of attacks. There are two security attacks that have been seen that use cryptographic weaknesses for execution. The discussion of these two attacks, viz. e-fail attacks and KRACK attacks is done with coverage of their execution process and mitigation strategies. The security recommendations and guidelines that the business firm shall follow are also covered.
Answer 1
E-Fail Attacks
There are certain cryptographic weaknesses that make it possible for the malevolent entities to carry out the e-fail attacks. The emails that are shared using the email servers and the clients are said to be secure as the applicable standards make use of encryption techniques. The two popular standards as PGP and S/MIME are said to be secure as they incorporate the encryption mechanisms. However, there are cryptography weaknesses that are associated with these encryption mechanisms enabling the attackers to have access to the plain text in the email. The use of the email access along with the HTML tags can be done by the attackers to manipulate the encrypted mails and gain access to the secure content present in the emails. It is necessary that there are certain pre-requisites or conditions that are met before the attacker may give shape to these attacks. The compromised email server is one of the most common ways through which the attackers can access to the mail content. The emails that are encrypted using the S/MIME certificate may also be exposed to the e-fail attacks.
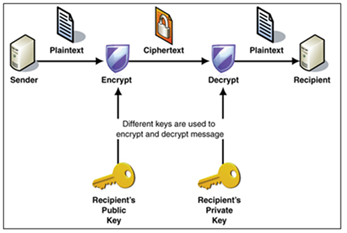
Above image is the representation of the private and public key exchange during secure email exchange.
There are certain steps that the attackers usually follow so that they may succeed in carrying out the e-fail attacks.
- The attacker appends the malicious HTML tags, such as the image tag to the encrypted mail which is protected through the standards, such as OpenPGP or S/MIME.
- The email client then accidentally parse the HTML which allows the attacker to gain access to the mail (Trendmicro, 2018)
- The recipient decrypts the email and the injected HTML tags get processed in this procedure.
- The email exfiltration occurs which changes the form of the encrypted mail to the plain text without the knowledge of the user.
- This provides the attacker with the access to the plain text.
KRACK Attack
Key Reinstallation Attacks or KRACK attack is a vulnerability that was identified and there were security patches that were installed before it could do some potential damage. There are certain cryptography weaknesses that have been spotted with the KRACK attacks that may enable the attackers to violate the security norms. Majority of the users in the present times make use of the Wi-Fi networks for information sharing and transmission (Vanhoef&Piessens, 2017). The use of the Wi-Fi networks is done and these networks are protected using the WPA2 protocol. There are security vulnerabilities that have been identified with the WPA2 protocol and it may be used by the attackers to give shape to the KRACK attacks. There are specific steps that may be followed by the attackers to carry out the KRACK attacks.

• As soon as a client enters or joins a network, there is a 4-way handshaking process that gets initiated which is done to negotiate on the encryption keys to be used. The installation of the encryption key is done when the third message is transmitted.
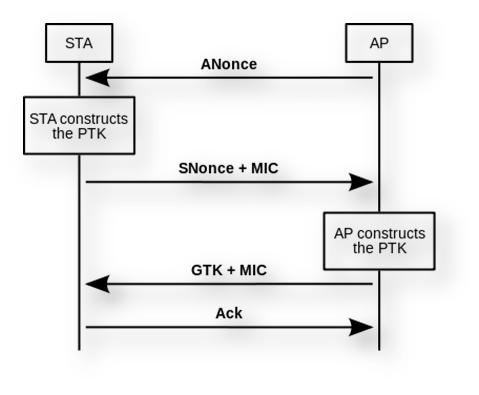
• In the KRACK attacks, the third message is dropped and it does not reach the device. This results in the multiple retransmissions of the message by the network access point.
• This may result in the receiving of the message three by the client several times and the packet counter gets incremented by 1 each time.
• These counters are reset by the attacker and replay of the message three is done to gain access to the encryption key (Krackattacks, 2017).
• This also results in the manipulation of the packets and there may be certain packets that may be dropped as per the intent of the attacker.
Answer 2
There are certain steps that can be followed to avoid and mitigate the e-fail and KRACK attacks. There are also certain pre-requisites that are associated with the both the attack types.
E-Fail Attacks
It is necessary that there are certain pre-requisites or conditions that are met before the attacker may give shape to these attacks. The compromised email server is one of the most common ways through which the attackers can access to the mail content. The emails that are encrypted using the S/MIME certificate may also be exposed to the e-fail attacks. The attacker appends the malignant HTML tags, for example, the image tag to the encrypted mail which is protected through the models, for example, OpenPGP or S/MIME. The email client then accidentally parses the HTML which permits the attacker to access the mail. The recipient decrypts the email and the injected HTML tags get processed right now. The email exfiltration happens which changes the type of the encrypted mail to the plain text without the knowledge of the user (Ashford, 2017). This provides the attacker with the access to the plain text. The attacker will not be able to give shape to the attack if these conditions are not met. The mitigation mechanisms shall, therefore, be based on the same. Mail rendering shall be prevented and it will automatically result in the inability for the attacker to gain access to the mail server. There are no or irregular vulnerability checks and assessments that take place in the organizations. These vulnerabilities allow the malicious entities to carry out the security attacks, such as e-fail attacks. The use of regular security audits, patch management, and security trainings can be done so that there is no scope for any security gap.
KRACK Attacks
There are also some of the pre-conditions that are associated with the KRACK attacks. When a client enters or joins a network, there is a 4-way handshaking process that gets initiated which is done to negotiate on the encryption keys to be used. The establishment of the encryption key is done when the third message is transmitted. In the KRACK attacks, the third message is dropped and it does not reach the device. This results in the multiple retransmissions of the message by the network access point. This may result in the receiving of the message three by the client several times and the packet counter gets incremented by 1 each time. These counters are reset by the attacker and replay of the message three is done to access the encryption key. This additionally results in the control of the packets and there might be certain packets that might be dropped as per the intent of the attacker. The control measures to avoid and prevent the KRACK attacks shall be based on the above conditions. There must be security patches that must be installed on a regular basis. This will keep the security vulnerabilities aside and the attackers will not have any opportunity to violate the security norms. There are newer security protocols that are being developed, such as the Blockchain networks for promotion of the security. The use of these networks and technologies must be explored and included to enhance the overall security. It is also necessary that the administrative changes and updates in the security are done so that the overall security improvement may be done. The security updates shall be installed at the organization level with the inclusion of the network security tools. This will enable the users and the organizations to mitigate the attacks (Krackattacks, 2017).
Answer 3
There are certain steps and processes that the business shall follow so that the e-fail and KRACK attacks along with the other security attacks do not take place.
There are several security tools and mitigation techniques that have been developed. Most of the security attacks occur because of the security vulnerabilities and the business shall ensure that the vulnerabilities are continually assessed and treated. The e-fail and KRACK attacks are also the result of the cryptographic vulnerabilities. The compromised email server is one of the most widely recognized ways through which the attackers can access to the mail content. The emails that are encrypted utilizing the S/MIME certificate may likewise be exposed to the e-fail attacks. The attacker appends the dangerous HTML tags, for example, the image tag to the encrypted mail which is protected through the models, for example, OpenPGP or S/MIME. The email client then accidentally parses the HTML which permits the attacker to access the mail. The recipient decrypts the email and the injected HTML tags get processed at this moment. The email exfiltration happens which changes the type of the encrypted mail to the plain text without the knowledge of the user. This provides the attacker with the access to the plain text (Efail, 2018). The attacker won't be able to give shape to the assault if these conditions are not met. The relief mechanisms will, therefore, be based on the same. Mail rendering will be prevented and it will naturally result in the powerlessness for the attacker to access the mail server. There are no or irregular vulnerability checks and assessments that take place in the associations. These vulnerabilities permit the vindictive entities to complete the security attacks, for example, e-fail attacks. The use of regular security reviews, patch management, and security trainings should be possible so that there is no scope for any security gap.
There are likewise some of the pre-conditions that are associated with the KRACK attacks. When a client enters or joins a network, there is a 4-way handshaking process that gets initiated which is done to negotiate on the encryption keys to be used. The establishment of the encryption key is done when the third message is transmitted. In the KRACK attacks, the third message is dropped and it does not reach the device. This results in the multiple retransmissions of the message by the network access point (Lee, 2018). This may result in the receiving of the message three by the client several times and the packet counter gets incremented by 1 each time. These counters are reset by the attacker and replay of the message three is done to access the encryption key. This furthermore results in the control of the packets and there may be certain packets that may be dropped as per the intent of the attacker. The control measures to keep away from and prevent the KRACK attacks will be based on the above conditions. There must be security patches that must be installed on a regular premise. This will keep the security vulnerabilities aside and the attackers won't have any chance to violate the security standards. There are newer security conventions that are being developed, for example, the Blockchain networks for advancement of the security. The use of these networks and technologies must be explored and included to enhance the overall security(Hardjono& Smith, 2019). It is additionally necessary that the administrative changes and updates in the security are done with the goal that the overall security improvement might be done. The security updates will be installed at the association level with the consideration of the network security tools. This will enable the users and the associations to mitigate the attacks.
The business can know if the e-fail or KRACK or other security attacks have occurred by assessing the information security and system logs. There can be low to significant impacts of the security attacks on the business. The information properties of the data sets may be compromised and the violation of the security parameters may be seen. The customers impacted with the security attack may not wish to carry out their associated with the business which may lead to the loss of the customer base and market shares. The market value may be dropped and there can be legal punishments that may also be experienced. It is necessary that the overall security of the organization and its information sets is upgraded. There are some integrated tools that can be used for this purpose. The use of the anti-malware and anti-denial tools can be done to avoid the security attacks. Most of the security attacks occur because of the network loopholes and vulnerabilities. The automated network security tools shall be done to control these attacks (Yuanyuan, 2018). These will include the intrusion detection systems and scanners. There are also several controls that can be implemented in terms of the administrative checks and validations. The use of regular security updates, security audits, updates in the information security policy, etc. must also be done by the business so that it may be able to maintain and improve the status of information security.
References
Ashford, W. (2017). No need to panic about Efail attacks. ComputerWeekly.Com; ComputerWeekly.com. https://www.computerweekly.com/news/252441102/No-need-to-panic-about-Efail-attacks
Efail. (2018). EFAIL. Efail.De. https://efail.de/
Hardjono, T., & Smith, N. (2019). Decentralized Trusted Computing Base for Blockchain Infrastructure Security. Frontiers in Blockchain, 2. https://doi.org/10.3389/fbloc.2019.00024
Krackattacks. (2017). KRACK Attacks: Breaking WPA2. Krackattacks.Com. https://www.krackattacks.com/
Lee, Y. (2018). Detecting Code Reuse Attacks with Branch Prediction. Computer, 51(4), 40–47. https://doi.org/10.1109/mc.2018.2141035
Trendmicro. (2018). EFail Exploit Exposes Encrypted Email Content - Security News - Trend Micro USA. Trendmicro.Com. https://www.trendmicro.com/vinfo/us/security/news/online-privacy/efail-exploit-exposes-encrypted-email-content
Vanhoef, M., &Piessens, F. (2017). Key Reinstallation Attacks. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security - CCS ’17. https://doi.org/10.1145/3133956.3134027
Yuanyuan, W. (2018). The Establishment and Implementation of Information Network Security Plan. International Journal of Advanced Network, Monitoring and Controls, 3(2), 104–107. https://doi.org/10.21307/ijanmc-2018-050












