Programming Assignment on Password Storage Application
Question
Task: This assignment should be done in groups. The minimum size of a group is 2 and the maximum size is 4. You should organise yourselves into groups and let me know the proposed membership by 10th February. I reserve the right to make changes if I think it is necessary.
Password Storage Application
- The id/password pairs along with a description are to be stored in an encrypted file.
- A master password is set on first use and can later be changed.
- Access to the file is controlled with the master password or any of the currently valid passwords.
- The master-user can add, remove (and modify) all the stored id/password pairs and descriptions.
This description is deliberately skeletal as I would prefer different groups to implement the application in different ways. Lab sessions will be used to support the development and you should also make use of these to discuss your plans.
Answer
Introduction
In the world of internet every web application needs to be having personal space wherein users’ can have access to their personalised applications and accounts as well as they can keep their data safe within the account. Hence every such applications needs to have authentication check that can provide high end security to users. The authentication is the process of allowing users’ already registered with the application prior for their intentions to avail the services. The registration needs user information along with unique username and strong password.
The project focuses on development of web login portal where there is a single admin and multiple users. A master/admin is the sole owner of registration information which is stored in a doc file, allowed to read only via web application because it contains encrypted data. A login applications allows master to register several users; modify and delete them.
The user information for login is stored in a file in encrypted format. MD5 algorithm is used for encryption so that the information is not read by external entity. Master of web application is the first user of the web login application who is responsible for all the user management activities. Encryption is the process of converting plain text into cipher text. Plain text is a simple readable form of information whereas cipher text is the unreadable form.
The need of storing information in encrypted file is to protect it from unauthorised users. The information security is gaining importance due to several misleading and malicious activities being happening all over. It now becomes crucial to focus on users’ personal information as this could lead to something really dangerous.
Development Methodology
Programming Language
For the projects such as web applications with high end security, it is most preferable to use Java. The project highly demands information security at its excellence and Java has in-build libraries that could help programmers to code with ease.
Java
Java is an object-oriented programming language capable of allowing concurrency, multi-threaded, high performance application development that could help achieve developers almost every requirement. It allows programmers to write code once and execute it anywhere, this makes it platform independent. This is possible since it comes with in-built compiler that converts code into bytecode that can be executed on any platform. Java is considered to be one of the most famous coding language among developers for its following perks:
- WORA: Write Once Run Anywhere makes it easier for developers since they do not need to change any code before migrating it to another platform.
- It is portable and cab be easily installed on any machine
- There are several libraries available that covers all the needs of developers from every industry.
- Handles exceptions really well for complex and simple applications too.
- It allows automatic garbage collection.
- Provides high end security.
- Multi-threading and multi-processing is easy with Java
Cryptographic Library
The very well-known and trustworthy encryption algorithm MD5 is used to encrypt data. For this purpose sun.misc.BASE64Encoder is used to perform the encryption. sun.misc.BASE64Encoder is a cryptography library provided by Java. Java 1.7 has in-built library hence no need to download the jar but lesser versions need jar to download and place it in the application’s class-path. The code used for encryption demands the string to be converted in charstream hence
com.google.common.io.CharStreamslibrary is used further more. The library is added to the application’s classpath. With the use of MD5, it possible to generate encrypted text surely irreversible. MD5 algorithm is a cryptographic algorithm that helps in generating 128 bit message digest string on accepting any length of string. The message digest is also termed as hash of the input string.
Approach
The use of above mentioned cryptographic libraries are confined to the small code snippet below:
The messageDigest chooses MD5 algorithm as cryptography algorithm.
quest1 contains user information that needs to be encrypted.
Base64Encoder encodes the given string into digestString. The digestString is the encrypted string.
The user information is stored in the form as:
email~password~title~url
Each user entry is separated by ‘’ i.e.
email1~password1~title1~url1email2~password2~title2~url2…..and so on.
Other Information Safeguarding Approaches
Cryptography is the best way to safeguard information. Many cryptographic algorithms have several benefits and disadvantages as well. Another cryptographic algorithm as SHA and its different variants are also secure and quite trustworthy as hackers cannot easilyreverse the cipher text. MD5 maps the data of any length into fixed length one. SHA algorithm generates strong hash strings for given string. Both the algorithms are considered as secure but MD5 is relatively faster than any variants of SHA.
Implementation and Usage
The project focuses on developing secure web application capable to storing data in encrypted form. For encryption, cryptography algorithm MD5 is used so as to store data securely. For each user information, email, password, title and url; the application generates a message digest which is the fingerprint of given data. The procedure of secure login web application is as given by:
1. First user of the web login application is master/admin. Master needs to register to the system first. On registration page, master has to enter title, url, email and password as his information. If the password file is empty, it allows master to generate the account by adding entered information into the file. If file is not empty, it displays the message: Invalid Credentials. This message doesn’t specify anything particular and hacker would never be allowed to register himself.
2. On master registration, he will be allowed to login to the system. In the password file, first entry is for master login credentials. On login, only first line will be checked for master login check, hence this will prevent from parsing entries of all the users from next line which will save much time.
3. Only master is allowed to add new user to the login application by adding his title, url, email (username) and password. The username is checked for availability and the information is stored only if username is available.
4. Master can modify and delete any user from the web application.
5. Finally, on user login, the password file in encrypted form is decrypted to find the correct credentials for intended user. If these are matched, user is redirected to the home page.
The system is secured as it does not allow registration of master once it is done at the initial time. Moreover, another important feature added is provisions for strong passwords. The system accepts passwords only when it contains a lowercase, uppercase, a special character and a numeric. Also, it has to be at least 8 digit long.
Snapshots
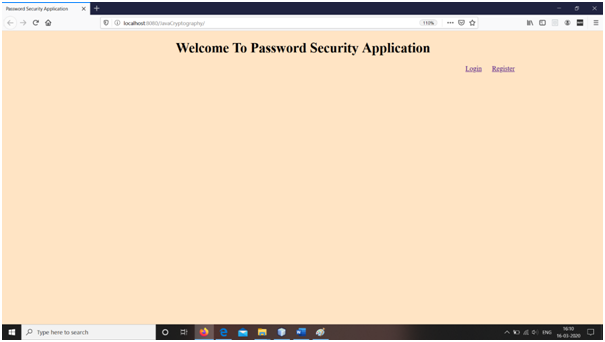
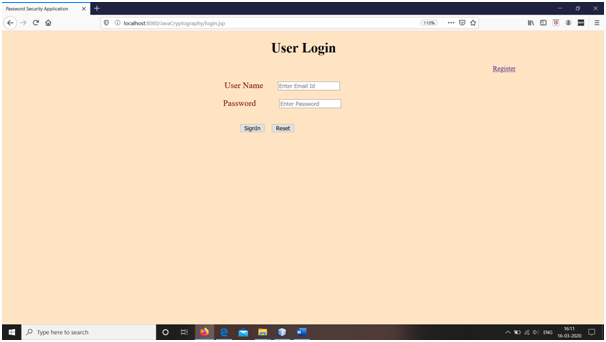
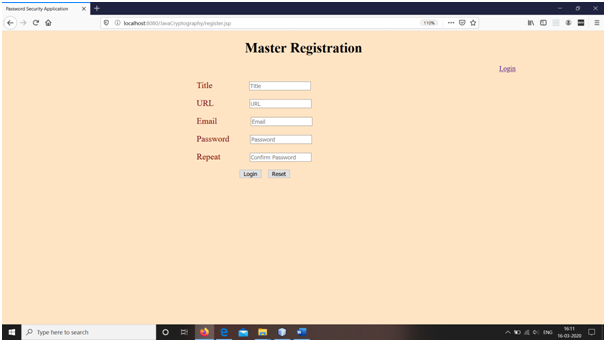
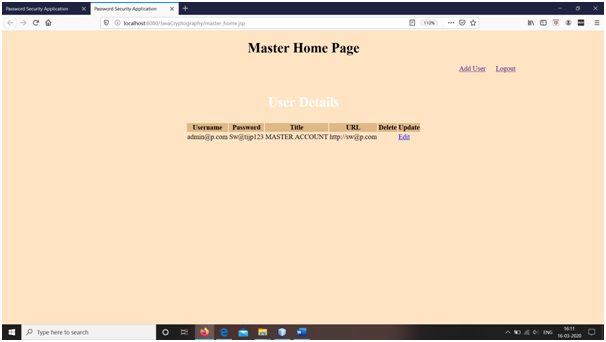
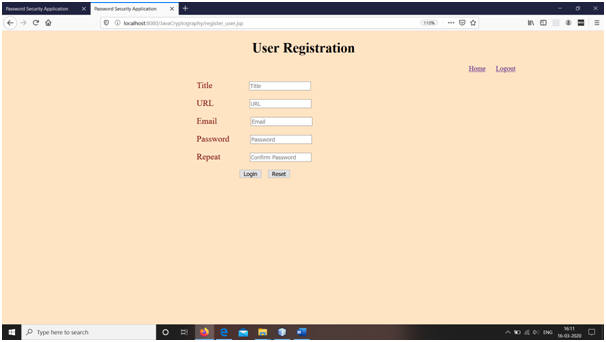
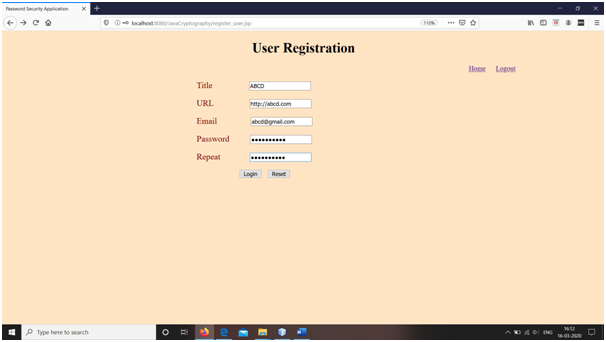
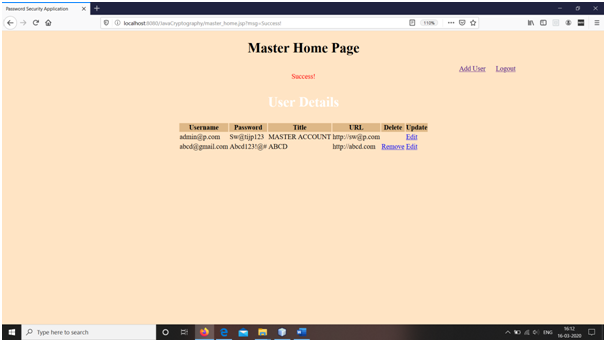
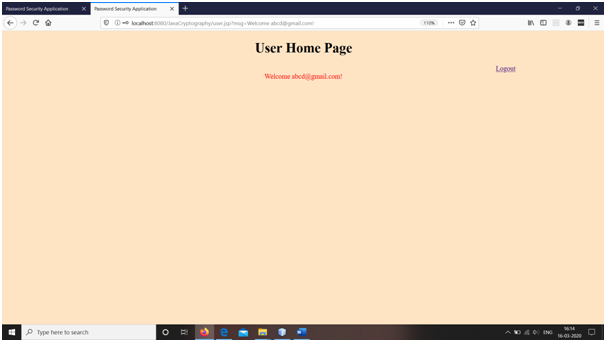
Conclusions
The developed system is secure as it is developed with many security features such as strong passwords, storing data as encrypted data. Also, important feature of the system is to provide high end security for login purposes by allowing registration of master only once at the initial time of the application startup. Java cryptography library used with this project also allows using SHA and its variants. Hence this project can also be claimed to be scalable in every regards.
References
A. J. Raphael, V. Sundaram, "Cryptography and steganography-A survey", International Journal of Computer Tech. Appl., vol. 2, no. 3, pp. 626-630, 2011.
W. Stallings, Cryptology and Network Security: Principles and Practices, Prentice Hall, 2010.
"Standard specifications for public key cryptography” (2000) IEEE.P1363".












