Digital Forensics Investigation Assignment: Critical Review on Digital Investigation Process Models
Question
Task:
1.1. Part A. Digital Forensic Investigation Models
The main assessment task (Part B) will require you to perform an investigation. Numerous investigation models have been proposed in the literature. Whilst theoretical in nature, they are useful for teaching the broad concepts of performing an investigation.
Write a critical review (minimum 10 papers) of previous research and academic proposals relating to digital investigation process models .
Your review should focus on:
1. The applicability of these models to investigations such as live forensics; desktop (deadbox) forensics; network forensics; mobile device forensics; digital video/audio forensics; corporate incident response.
2. The extent of similarity/divergence between the selected models.
You should consider using tables where necessary. However, the table should be used to summarise data and not to replace the main narrative.
Answer
Digital forensic investigations at first was conducted by live analysis, that examined digital media in a direct manner by means of non-specialist’s tools.First sets of digital forensic is based upon computer forensics and currently a significant number of mobile devices for forensics has been developed. Increasing number of criminal activities by means of digital information requires digital forensic investigation tools for finding evidences and prosecuting criminals. The current scope of critical review conducting previous research and academic proposals related to digital investigation process models, to understand application of these models and extent of similar or divergence between the selected models. The selected process models for review includes Abstraction model (Carrier, 2003) and Six step approach (DFRWS, 2001).
According to Yusoff, Ismail, and Hassan (2011) the Abstraction Digital Forensic Model (ADFM) is inspired from the DFRWS investigation model and includes additional three phases. As DFRWS is a six-step model, the Abstract model consists of nine steps altogether. This model has greater applicability and can be applied to live forensic such as desktop (deadbox) forensics, mobile device forensics, network forensics, digital audio/video forensics as well as corporate incident response. The DFRWS Investigative Model (2001) is a more generalized model consisting of six steps. The scope of this model being limited considering the previous model it has lesser applicability in the domains indicated as above.
Satpathy, Pradhan, Ray (2010) discusses the scope of various digital forensic models in a brief manner along with discussion of DFRW model. The article discusses the need for application of data fusion in digital investigation. The Abstraction model is discussed as an extended portion with the need for application of data fusion in digital investigation. The paper discusses the application for the abstraction model to be greater in nature. The primary applications being reliability in findings, completeness, comprehension and improvement.
Montasari (2016) in his article assesses various models of digital forensic investigation to understand their applications in a better manner. The article states that Reith et al’s ADFM model is divided into several steps. The article points out the disadvantages of ADFM model, such as high-level approach in categorizing to be applied in practice. The model cannot easily be tested hence it has lesser applicability as compared against DFRW model. Shrivastava, Sharma, and Dwivedi (2012) analyses the historical evolution of digital forensic models. The models are discussed through their steps and processes along with characteristics. The article also discusses need for forensic models. The ADFM is discussed with its stages and its disadvantages are given. The DFRW model includes some duplicated steps of the Abstraction model and encompasses its disadvantages of those steps as well.
Zainudin, Merabti& Llewellyn-Jones, (2011) discusses the process model through a comprehensive digital forensic investigation model. The model investigation reveals similarity in steps followed by ADFM and DFRW. There is also revealed online social network related applications of the models. These models can be used to perform a number of applications with a selected feature in research. Agarwal, et al (2011) article discusses the ADFM and the DFRW model in a step by step manner. The DFRW model has more detailed steps in comparison to the ADFM and can be used in physical crime investigation as well as digital crime scene. Ademu, Imafidon, and Preston (2011)discusses various digital forensic investigation models. The similarity between the models is to include, examine, analyze and report cases through collection of facts and figures. According to this article there are several advantages of the proposed models which includes their structured framework for developing digital forensic investigations. Garfinkel(2010) develops the article from the age-old era of digital forensic models. The article states current research challenges in evaluating digital forensic investigations. The article states the similarity in the steps followed by the two models ADFM and DFRW along with their application related to conducting live forensic investigations especially in network forensic. Zainudin, Merabti, and Llewellyn-Jones (2011)explains the application of various process models in digital forensic investigations. It analyses ADFM through existing literatures of digital forensic investigations and frameworks. It categorizes specific model for the purpose of investigating online social networks. The scope of DFRW is expanded here to understand ways it can be applied in mobile network cases.
Giova (2011) undertake several literature evaluations for problem solving in a digital forensic case. It applies process model with steps similar to ADFM. It considers DFRW to be inappropriate as against ADFM in resolving complex problems in digital forensic evaluations.
References
Ademu, Inikpi O., Chris O. Imafidon, and David S. Preston."A new approach of digital forensic model for digital forensic investigation." Int. J. Adv. Comput. Sci. Appl 2.12 (2011): 175-178.
Agarwal, Ankit, et al. "Systematic digital forensic investigation model." International Journal of Computer Science and Security (IJCSS) 5.1 (2011): 118-131.
Garfinkel, Simson L. "Digital forensics research: The next 10 years." digital investigation 7 (2010): S64-S73.
Giova, Giuliano. "Improving chain of custody in forensic investigation of electronic digital systems." International Journal of Computer Science and Network Security 11.1 (2011): 1-9.
Montasari, Reza. "Review and assessment of the existing digital forensic investigation process models." International Journal of Computer Applications 147.7 (2016): 41-49.
Satpathy, Suneeta, Sateesh K. Pradhan, and B. B. Ray. "A digital investigation tool based on data fusion in management of cyber security systems." International Journal of Information Technology and Knowledge Management 2.2 (2010): 561-565.
Shrivastava, Gulshan, Kavita Sharma, and AkanshaDwivedi. "Forensic computing models: Technical overview." CCSEA, SEA, CLOUD, DKMP, CS & IT 5 (2012): 207-216.
Yusoff, Yunus, Roslan Ismail, and Zainuddin Hassan."Common phases of computer forensics investigation models." International Journal of Computer Science & Information Technology 3.3 (2011): 17-31.
Zainudin, NorulzahrahMohd, MadjidMerabti, and David Llewellyn-Jones."A digital forensic investigation model and tool for online social networks." 12th Annual Postgraduate Symposium on Convergence of Telecommunications, Networking and Broadcasting (PGNet 2011), Liverpool, UK. 2011.
Zainudin, NorulzahrahMohd, MadjidMerabti, and David Llewellyn-Jones. "Online social networks as supporting evidence: a digital forensic investigation model and its application design." 2011 International Conference on Research and Innovation in Information Systems.IEEE, 2011.
Part B. Expert Witness Report
Guidance on the completion of the expert witness report.
The expert witness report (Part B) has been adapted from the format published by Bond Solon: (https://www.bondsolon.com/media/71366/model-report-for-experts.pdf). In your final submission, you should remove any extraneous material that has been added by the module leader to aid your completion thereof (e.g. footnotes and comments). You should NOT insert your name anywhere. Wherever a name is required, you should insert your student number – this will ensure compliance with the anonymous marking rules. Remove this box in the final submission.
Expert Witness Report
xxxxxxxx v xxxxxxxx
Title of the action
xxxxxxxx
Court reference number
_________________________________________________________________________________
Final report of [INSERT STUDENT NUMBER NOR NAME]for the name of the court
_________________________________________________________________________________
Dated The date you sign your report and send it to your instructing solicitors.
Specialist field: Your specialist field.
On behalf of the Claimant/ The name of the party to the action.
Defendant (or both if single
joint expert):
On the instructions of: The name of the solicitors who have instructed you.
Subject matter: A very brief description of the subject matter.
Your Name
Address
Telephone number
Fax number/Email
Reference
Contents
|
Paragraph number |
Paragraph contents |
Page number |
|
|
|
|
|
1 |
Introduction |
X |
|
2 |
The issues addressed and a statement of instructions |
X |
|
3 |
My investigation of the facts |
X |
|
4 |
My opinion |
X |
|
5 |
Statement of compliance |
X |
|
6 |
Statement of conflicts |
X |
|
7 |
Statement of truth |
X |
|
Appendices |
||
|
1 |
My experience and qualifications |
X |
|
2 |
Experience, qualifications, training of others involved in carrying out any test or experiment |
X |
|
3 |
Statement of methodology |
X |
|
4 |
List of documents that I have examined, with copies of important extracts |
X |
|
5 |
Details of any literature or other material I have relied upon in making this report with copies of important extracts. |
X |
|
6 |
Photographs, drawings, schedules, diagrams, graphs and other graphics |
X |
|
7 |
Chronology |
X |
|
8 |
Glossary of technical terms |
X |
|
9 |
Other |
X |
This contents page is useful even if the report is short. In longer reports, the contents page may need to be more detailed so the reader can easily find their way around the report
Report
1 Introduction
1.1 The writer
I am your full name. My specialist field is your specialist field and give a short summary of the most important qualifications and experience relevant to the case. No more than three lines.
Full details of my qualifications and experience entitling me to give expert opinion evidence are in appendix 1. It is necessary to have these full details as you may be cross-examined on them. Students please note, that given it is impossible for you to include this without identifying yourself (and therefore going against the anonymous marking rules), you should NOT include this. The qualifications requirement is specified here only so that you become aware that in a real report, you would ordinarily include this.
1.2 Summary background of the case
The case examines Fred Bassett after intelligence reports suspected downloading images of Mickey Mouse. The convict tried to hide facts by keeping his computer (IMK/1) below the stairs. The case determines provenance of illegal images of Mickey Mouse and linking suspect to distribution of images. Evidence made from the interview is corroborated to refute the statements made against the convict.
1.3 Summary of my conclusions
Fred Bassett have been identified with downloading several images of Mickey Mouseand keeping them in his computer (IMK/1) beneath the staircase. Bassett was found to express interest in images of Mickey Mouse and having connections with others with similar interest. At the initiation of the interview Bassett said that he had no interests in pictures of Mickey Mouse and those which appeared in pop-ups he deleted them and di not possess them. However, in his computer, there were several images of Mickey Mouse that was found and kept the computer away beneath the stairs. By way of tracing the downloads in history and download tab of internet explorer, the provenance of the illegal images can easily be understood. The linkage to suspecting and distribution of such images can be understood by tracing the email sent along with other modes of distribution. Intelligence report indicated the possession of the images and it was found in his computer though it was made illegal at that time. The suspect tried to move away from the indicated facts by refuting to these statements. Hence, it can be stated that the convict is guilty of the offense and can be held liable for possessing and distributing such images.
1.4 Those involved
The people contacted for the purpose of preparing this report includes the persons, to whom the images has been distributed. These people might reveal information regarding circulation of images of Mickey Mouse. Organizations include local internet service providers, Gmail’s local contact and local police for collecting any other evidence. They will reveal pertinent information related to any mails deleted or images circulated as at particular date and time period.
1.5 Technical terms and explanations
I have indicated any technical terms in bold type. I have defined these terms when first used and included them in a glossary in appendix 8. I have also included in appendix 5 extracts of published works I refer to in my report, and in appendix 6 there are diagrams and photographs to assist in the understanding of the case.
2 The issues to be addressed and a statement of instructions
The substance of all material instructions has to be based upon written instructions. Such instructions include questions regarding opinion sought. There will also be several materials and documents provided and considered that will serve as material evidence for the purpose of collection of data. Expert is instructed by SJE for the collection of information, based upon which assumptions will be developed upon which the case will be pursued.
2.1 The purpose of the report.
The purpose of this report is to state the objectives attained from investigation of exhibit IMK/1;
I. In the process of identifying illegal images of Mickey Mouse and determine their provenance.
II. To identify any evidence based linking suspect to distribution of such images.
III. To consider statements provided by the suspect whilst in interview and then identifying evidences for corroborating or refuting such statements.
3 My investigation of the facts
I. Fred Bassett had downloaded images of Mickey Mouse
a. Source of fact includes pictures of Mickey Mouse being found in his computer hard disk.
b. Recording and methodology of investigation includes tracing download and history of the computer to find data downloaded
II. Fred Bassett tried to hide the facts by keeping the source computer beneath the stairs.
a. Source of fact includes eye witness during investigation
b. Recording methodology has to be picture clicked of the computer being located beneath the stairs
III. Expressing interest in images of Mickey Mouse
a. Source of facts includes various downloaded images of Mickey Mouse at the source computer
b. Recording methodology includes tracing pictures downloaded at the source computer and tracking emails to check emails or any other message formats sent across to other individuals.
IV. Fred Bassett stated that he had no interests in pictures of Mickey Mouse and also did not keep them and he also state deleting them from his computer
3.1 Assumed facts
Competing factual explanations indicating each version of event impacting opinion as it is the court’s role for determining factual disputes are;
I. Presence of image of Mickey Mouse in Bassett’s computer is a pure indication that he downloaded such images and might also have used it for circulation purposes. Possessing illegal images of Mickey Mouse is an offense in itself. The series of events have impacted my opinion and according to me Mr. Bassett has purely undertaken an illegal endeavor by willfully indulging in circulation of images and downloading some circulated images.
II. Bassett can be stated to have distributed images of Mickey Mouse and then deleting them after circulating. His defense statement in the interview where he states that he did not keep them and deleted them is a pure indication of his committing the offense. In my opinion he has deleted the images which he had already circulated within his group of people. His statement where he says that he had deleted the images impacts my opinion and creates inquisitiveness as to why it was done. In my opinion Mr. Bassett is guilty of the offense.
III. Statement made by the suspect in the interview reveals that he is an offender and his statement is indicating his corroboration. While initial interview conducted on Mr. Bassett, he was found guilty as he tried defending himself by stating the images appeared in pop-ups. This indicates that he did not block those pop-ups and this statement of his can be used in covering up for his activity of downloading of the images. This has immensely impacted my opinion and I find him guilty of the case.
3.2 Enquiries/investigation into facts by the expert
According to Civil experts Guidance para 56. Family Experts Practice Direction 25B para 9.1(c) each and every fact established needs to be established by means of examination, tests and investigations. The computer of Mr. Bassett will be checked thoroughly for all images. Images will be checked in C drive, D drive and F drive or E drive (if present) in his computer. All types of images in *.png, *.jpg and all other formats will be searched thoroughly. Then there will be investigation of all emails sent and received by Mr. Bassett as well as emails deleted in Trash folder. This will reveal great details regarding the case as inspection of all images and mails circulated can reveal if at all Mr. Bassett is an offender. The facts were obtained through personal investigation and collection of evidences along with its thorough examination.
3.3 Documents
As per Criminal experts CPS Disclosure Manual Annex K, there needs to be various documents to be included in the report for the purpose of arriving at a judgement. The lists of important documents include prints of all photographs obtained from the computer of Mr. Bassett. These photographs will provide evidence that his computer did contain sufficient images downloaded even after it was illegal. Print out of all emails containing images of Mickey Mouse sent across to various people. These emails retrieved and printed will act as a proof that he did commit the offense. All such emails will be traced back to as much as days as possible. These documents will serve as evidence acting against the convict.
3.4 Interview and examination
Family Experts Practice Direction 25B para 9.1(c) interview with the convict had to be conducted prior to arriving at conclusion regarding the case. The convict will be interview through a set of questions prepared to understand his knowledge regarding the matter. As an expert, I will solely conduct the interview and it will be a one to one interview to understand the facts as stated by the interviewee. I will keep with myself a recorder to record the entire interview. This recording I will review later to understand and arrive at the findings of the case. I will carry out investigation of the computer in physical manner also search for fingerprints on the computer. I will search any storage devise attached to the computer to search for evidence. I will go through any floppy disks, hard disks, pen drives, emails, online drives and any other physically or online connected devise. Investigation will be carried out online to evaluate emails and other online media to understand the circulation mechanism that have been used by the convict. Local internet provider will be asked to retrieve data from the server regarding details of such emails and online circulation of message containing images in straight format or encrypted format.
3.5 Research
There are several literature materials that have been used for the purpose of evaluating the current case which have been enclosed in Annex- 5. According to the literatures used, I have made use of process models for step by step evaluation Lai, and Böhme (2011). I have collected evidence first prior to analysis of facts and arriving at findings related to the study. As per relevant literatures, various formats of images can be kept and enclosed within computers as well as emails. Decrypting them is the primary task of an expert. Through interview there can be some understanding received related to the case, but evidence in the form of data need to be collected so to arrive at final findings (Giova, 2011). A though analysis of his mails has to be conducted to arrive at his circulation offense. But keeping such images or downloading them are there to prove that he is guilty of the offense (Redi, Taktak, and Dugelay, 2011).
4 My opinion
In my opinion, Mr. Bassett is guilty of the crime he committed and there are extensive range of evidence to support such findings. As per CPS Disclosure Manual Annex K, I have concluded that he had willfully possessed the images of Mickey Mouse which was illegal at that time. He had also circulated the images which could be understood from his interview where he stated that he had deleted those images. Hence in my opinion he is the convict and can be accused of the offense.
Statement of conflicts
I confirm that I have no conflict of interest of any kind, other than any which I have already set out in this report. I do not consider that any interest which I have disclosed affects my suitability to give expert evidence on any issue on which I have given evidence and I will advise the party by whom I am instructed if, between the date of this report and the trial, there is any change in circumstances which affects this statement.
Statement of compliance
I understand my duty as an expert witness to the court to provide independent assistance by way of objective unbiased opinion in relation to matters within my expertise. I have complied with that duty and will continue to comply with it. I will inform all parties and where appropriate the court in the event that my opinion changes on any material issues. I further understand that my duty to the court overrides any obligation to the party from whom I received instructions. Parts 33.2 (1), (2) and (3) and 33.4(j)
Criminal Procedure Rules
Declaration of Truth
This statement consisting of......... pages, is true to the best of my knowledge and belief and I make it knowing that, if it is tendered in evidence, I shall be liable to prosecution if I have wilfully stated in it anything which I know to be false or do not believe to be true.
Statement of conflicts
I confirm that I have no conflict of interest of any kind, other than any which I have already set out in this report. I do not consider that any interest which I have disclosed affects my suitability to give expert evidence on any issue on which I have given evidence and I will advise the party by whom I am instructed if, between the date of this report and the trial, there is any change in circumstances which affects this statement.
Signature …………………………………………………………… Date………………….
All reports must be signed and dated, and the Statement/Declaration of Truth must be verified by a signature/date. Therefore, you are advised to include your Statement/Declaration of Truth as your final item in the report, and to follow it with your signature and the date.
Appendix 1
Appendix 1
Appendix 2
Appendix 3
Appendix 4
Appendix 5 – Relevant Research Papers
Giova, Giuliano. "Improving chain of custody in forensic investigation of electronic digital systems." International Journal of Computer Science and Network Security 11.1 (2011): 1-9.
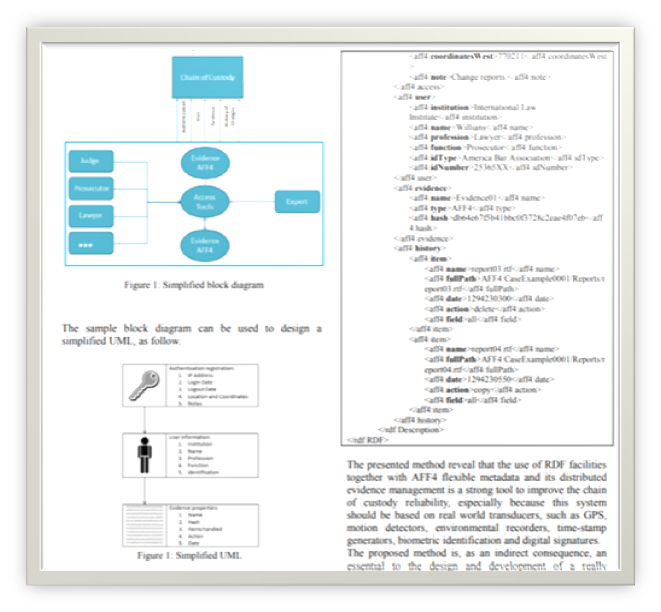
Lai, ShiYue, and Rainer Böhme."Countering counter-forensics: The case of JPEG compression." International Workshop on Information Hiding.Springer, Berlin, Heidelberg, 2011.
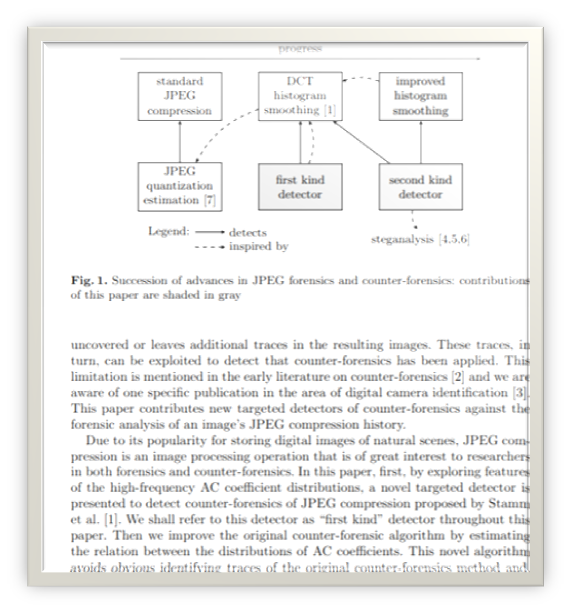
Redi, Judith A., WiemTaktak, and Jean-Luc Dugelay. "Digital image forensics: a booklet for beginners." Multimedia Tools and Applications 51.1 (2011): 133-162.
Appendix 6
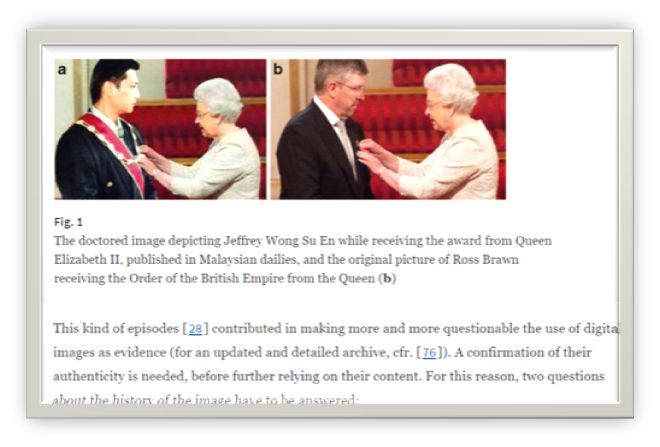
Appendix7.1












