Networking Assignment Illustrating Socio-Technical Concept, SNMP v3 configuration &Wireshark capture
Question
Task:
This networking assignment consists of three parts, Task 1 Task 2 and
Task 3.
Task 1: Discuss your own use case/example to illustrate any two of the Socio-Technical Design concept. You may use the following points for your illustration.
1. Social System
2. Technical System
3. Integration
4. Managing the System
Task 2: SNMP is considered as a de-facto protocol for network management. Several versions of the protocol exist and students are required to configure SNMPv3 using MIB browser in packet tracer.
The following criteria need to be satisfied.
1. A network topology consisting of at least 4 routers and 4 switches need to be built. One of the host/computer needs to be designated as the SNMP manager.
2. A routing protocol of your choice (for example RIP version 2, OSPF, EIGRP etc.) needs to be configured for internetwork connectivity. Use the IP addresses of your choice.
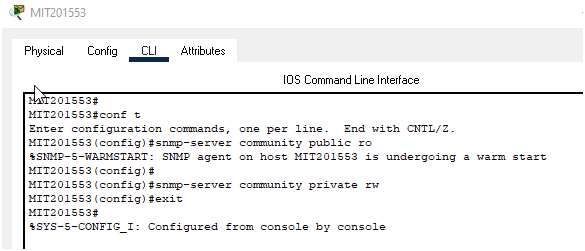
3. Configure SNMP v3 on the routers with community privileges.
4. Perform the following tasks on the host manager using MIB browser and verify the same with the CLI of the device.
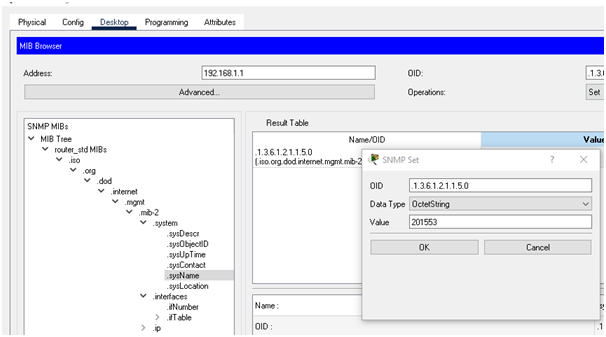
a. Change the hostname of one of the router with your MITID.
b. View the (administrative and operational) status of the interfaces of the one of the routers
c. View the routing table of the two of the routers
d. Show that SNMPv3 uses UDP for communication
e. Conclude the overall working of SNMP.
5. Screenshot needs be included as a proof of your work. Hint: You could use the following link as a reference for SNMP configuration. https://www.youtube.com/watch?v=5h0fN0j2XS8
Task – 3:Wireshark captures data from live network traffic. Investigate streaming audio delivery over TCP by listening to Internet live radio and capturing the transmitted packets. From a second network (Home, work, etc.), students have to chase and capture one more website which has an audio stream (such as radio stations, e.g. https://radio.abc.net.au/stations/news/live). Listen to the audio stream for at least some minutes to capture enough packets for analysis. All captures using Wireshark that must include the following for each group:
a) Start date-time of capture
b) Total number of captured packets for each protocol
c) Total Number of lost packets
d) IP addresses of the client and server
e) Show your performance analysis using Throughput Graph and Time Sequences Graph. Screenshots of the graphs need to be provided and the performance shown in the graph must be discussed in detail by each group.
Answer
Introduction
With this project, the three tasks that will be performed are the illustration of the socio-technical concept, SNMP v3 configuration, and Wireshark capture. In order to discuss the illustration of socio-technical system design, both the social and technical systems will be discussed and software engineering will be considered as an example. In the second task, a network topology has been designed by using 4 routers and 4 switches, and the RIP 2 protocol has been introduced. Then the routers have been configured with SNMP v3 and the SNMP tasks have been performed on PCs using the MIB browser. However, the data packet has been captured using the Wireshark tool in task three.
Task 1
STSD (Socio-technical system design) approach is a design technique that takes into account physical, social, and institutional factors as well as technological elements in the design of organizational structures. It has a lengthy history and is designed to guarantee that a system's technological and functional characteristics are taken into account simultaneously. The use of these methodologies results in a greater knowledge of how personal, social, and institutional aspects influence, how the process is completed and technological systems are used. This knowledge may help with the creation of business structures, business operations, and hardware resources [4]. The socio-technical system includes various functions that are social system, technical system, system integration, and managing the system.In order to evaluate the socio-technical system, all the above functions need to be illustrated. Most business organizations are developing their business operations following the socio-technical systems.
Therefore, it is important to develop the socio-technical architecture for the business organizations which must consider the two design components that are social system and technical system. In this report, software engineering has been selected as an example of a socio-technical system. Both the social and technical aspects are considered in software engineering. Most of the software applications are developed to meet the requirements of society and some specific organizations. There are several factors that can be considered to develop the software engineering operations that can be identified as peoples, hardware, software, laws & regulations, and data design. The use of technical resources and their usages can be enhanced in the software development process. Here, both the social and technical aspects have been illustrated to describe the socio-technical system design.
Social system:The social systems can be improved by considering the requirements of the users.Business organizations are developing software applications considering the latest social trends and market demands.Persons are the first priority to identify the user requirements from the system developed [5]. Here, the user feedback is collected from the existing system and the development process can be initiated following the user requirements.Various social issues can also be mitigated by introducing new features into the software. The smart alarm is an appropriate example that responds against critical situations and the system is developed considering emergency situations. Users share the login credentials on the software interface and most software stores the personal details of the users. Here, data and information protection is a social consideration that must be ensured by the developers. However, the goal and On the other, various rules and regulations are also associated with software engineering services. Here, the process of software development is also responsible for protecting user’s privacy and sensitive information from unauthorized users. Therefore, the developers must consider the ethical considerations to develop a system [6]. The socio-technical system is also restricted by a few laws and regulations that must be followed by the developers. Data and information protection is a major aspect that must be followed by the software engineers and various protective features are enabled into the system developed.
Technical system:
The technical system refers to the technical requirements that are required to develop the software application and other business operations. Various factors need to be considered to identify the technical specifications of the business operation. Both the hardware and software components are accounted for in the technical system.
On the other hand, the data sets are also designed to fulfil the technical requirements of the system. Data sets are protected by using a protective measures like passwords and authentication protocols. Various workstations, frameworks, connecting devices, and other peripherals are associated with the socio-technical system [7]. Without adopting the technical components, no software system can be developed. However, the technical components are also implemented to check the system quality and monitor the entire operational process. The socio-technical system can be implemented into the software engineering process by considering both the social and technical aspects.
However, the socio-technical system is mainly developed to utilize the technical resources in the system development. The socio-technical aspects are also considered to improve the user experience in a particular field. The operational cost of the system could be increased to execute the socio-technical aspects, but, the performance potential can be enhanced by introducing the socio-technical system design.
Task 2
A network topology
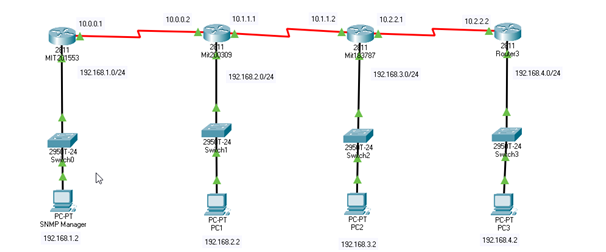
Figure: Network Topology
(Source: Author)
Routing protocol
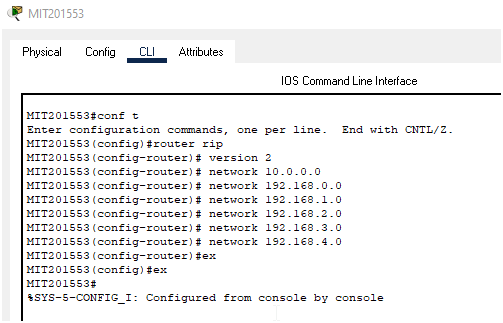
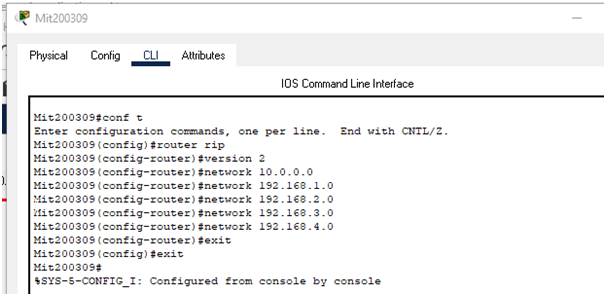
In order to ensure internetwork connectivity, RIP version 2 has been utilized as a routing protocol. The configuration of rip version 2 is provided below:
MIT201533 Router Rip configuration
Mit200309 Router rip configuration
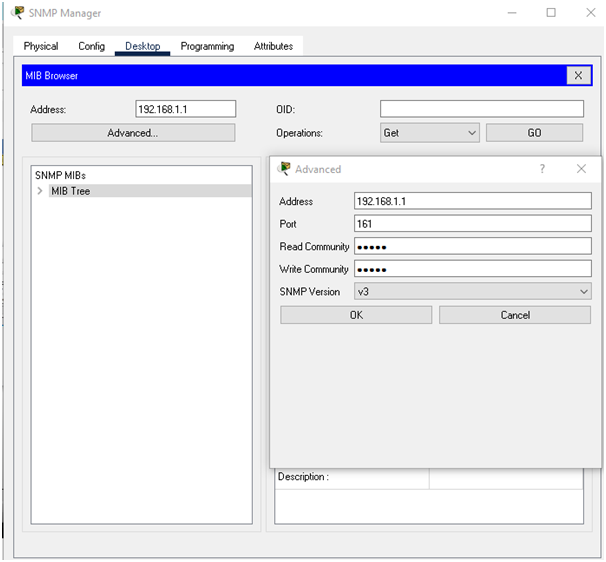
SNMP v3 Configuration
Configuring SNMP v3 on router has been shown in below figure:
Task performance using MIB browser
MIB Browser configuration
a. Changing hostname of router
Verification of hostname changing
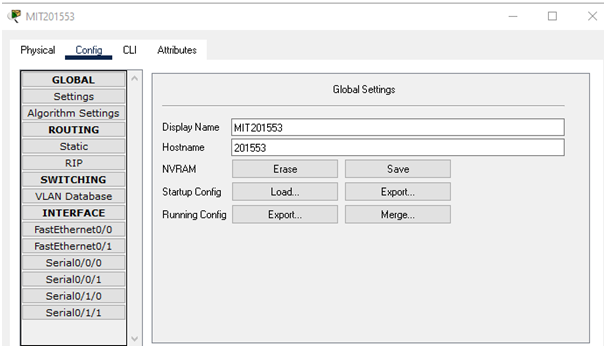
The above figure shows that the hostname of the device has been changed.
b. View the (administrative and operational) status of the interfaces of the one of the routers
Administrative status of the infaces of one router
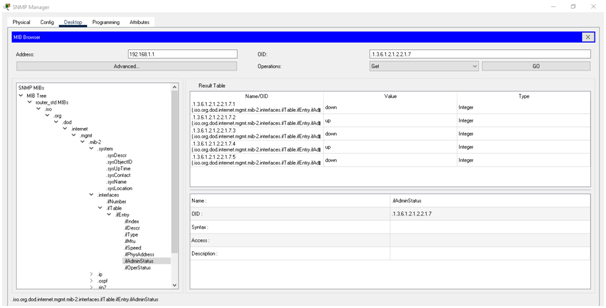
Operational status of the infaces of one router
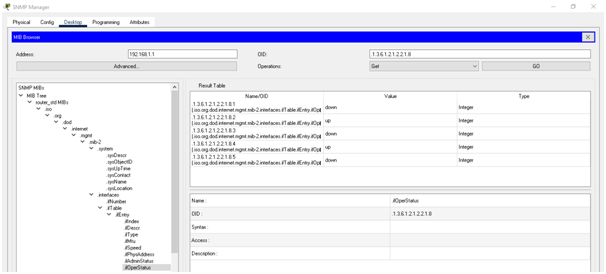
c. routing table
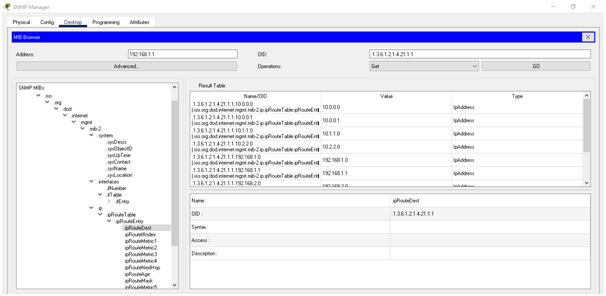
The routing has been shown in below figure:
d. showing that SNMPv3 uses UDP for communication
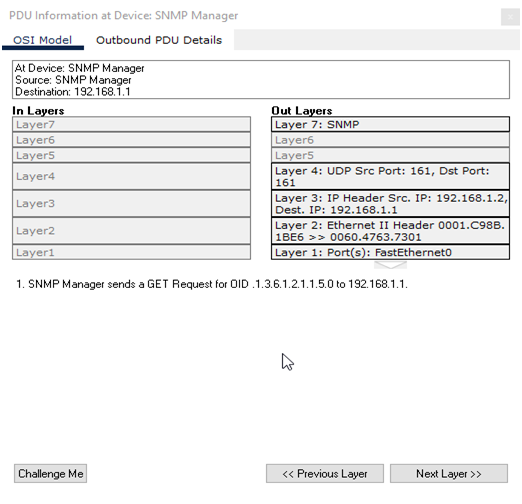
The above figure illustrates that the SNMPv3 utilizes UDP protocol for communication.
e. Overall working of SNMP
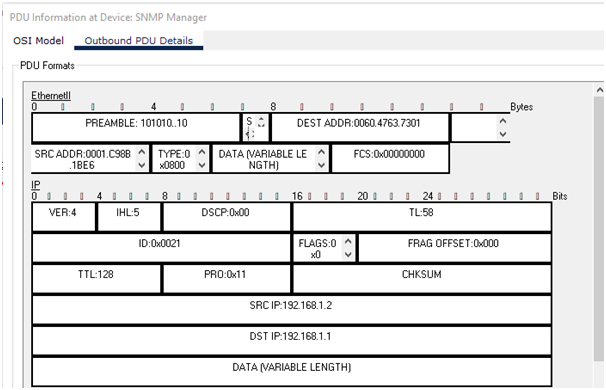
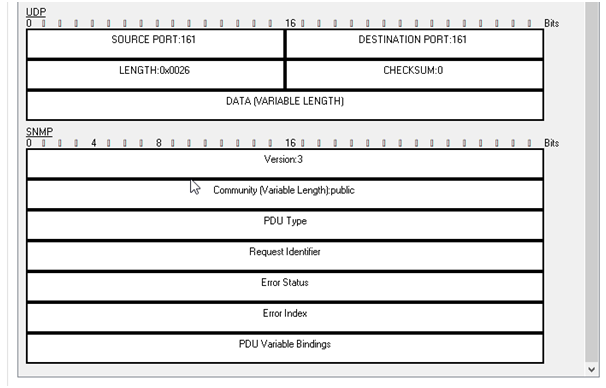
The above two figures illustrate the overall working of SNMP. Here, the version of SNMP is 3. The figure shows SNMP utilizes UDP protocol for communication. Moreover, it is an internet standard network protocol that is mainly utilized for monitoring and management of the network-connected devices [1].
Task 3
For this task, Wireshark network analysis tool has been utilized for capturing and analysing packets. In this task, the packet will be captured from the following websites: ‘https://radio.abc.net.au/stations/news/live’ The website is a radio stations website and the name of the radio station is ABC NewsRadio.
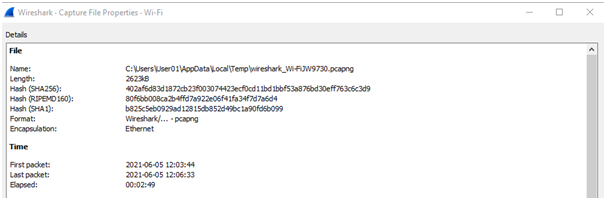
Start date-time of capture
Start date – 5th June 2021.
Start time-12:03:44 PM.
The evidence of start date and time is provided below:
Total number of captured packets for each protocol Ethernet
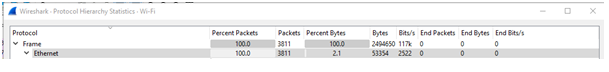
The above figure shows that total number of captured packets are 3811.
IPv6
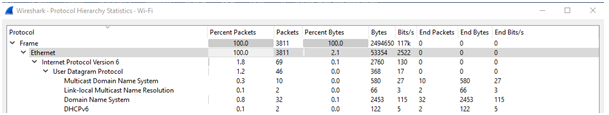
Total number of IPv6 packets are 69.
IPv4
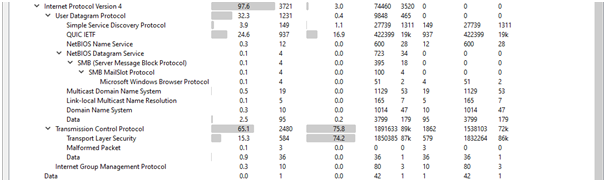
Total of IPv4 packets are 3721.
UDP
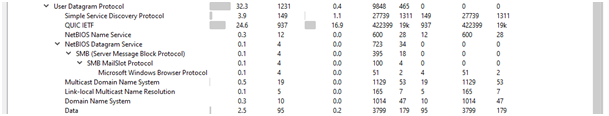
Total number of UDP packets are 1231.
TCP
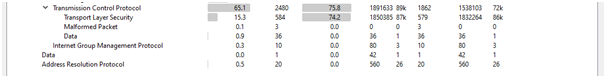
Total number of TCP packets are 2480.
Internet group management protocol

Total number of IGRP protocol packets are 10.
ARP

Total number of ARP packets are 20.
DNS
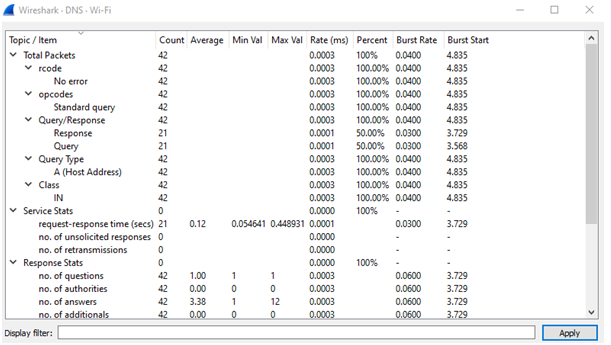
Total number of DNS packets are 42.
Total Number of lost packets
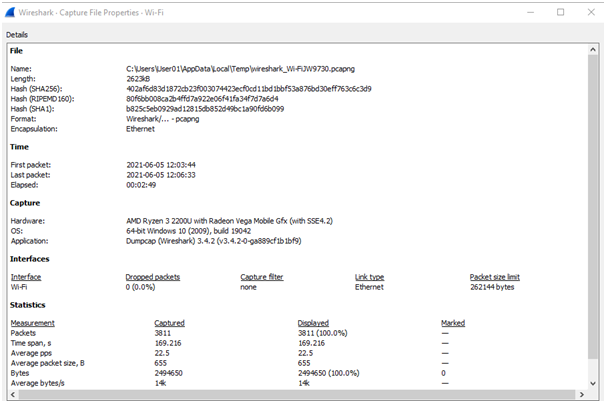
In this captured packet file, there is 0% packet loss. Therefore, no packets have been lost.
IP addresses of the client and server
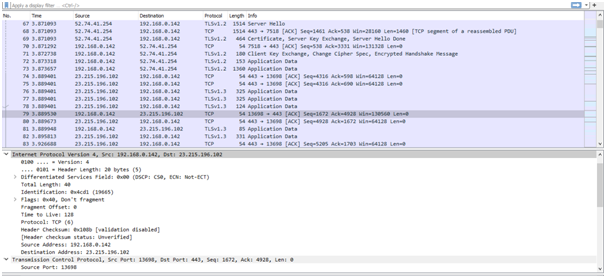
Here, IP address of the client is = 23.215.196.102. IP address of the server is = 192.168.0.142.
Source IP address is 192.168.0.142 and destination IP address is 23.215.196.102.
Performance analysis using Throughput Graph and Time Sequences Graph
Throughput graph
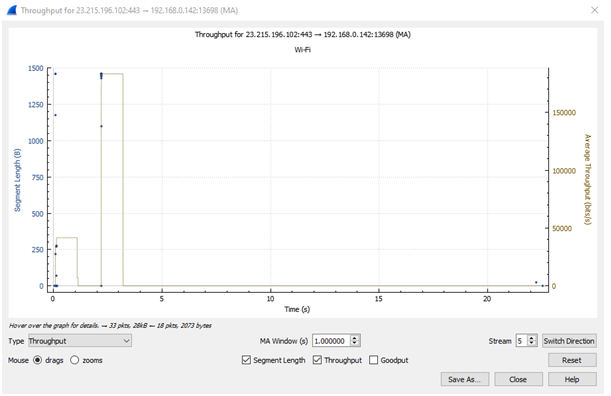
The above figure illustrates the through graph of the captured packet files. Here, the y-axis represents the segment length that is calculated in bytes while the x-axis represents the time that is calculated in second [3]. The above graph mainly shows how much data is transferred from the server in per second interval.
Time Sequence (Stevens) graph
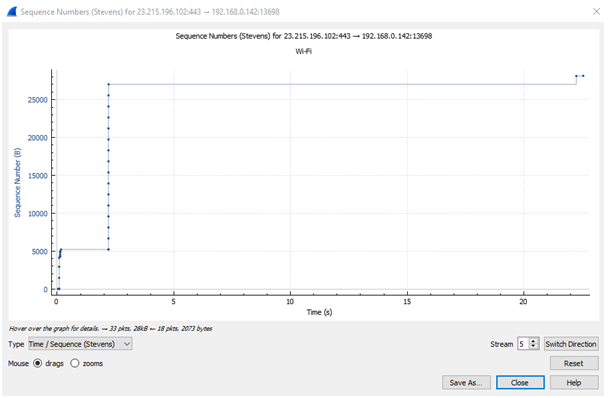
The above figure illustrates the time vs sequence (Stevens) graph of the captured packets. Here, the sequence number is increases with the increase of time.
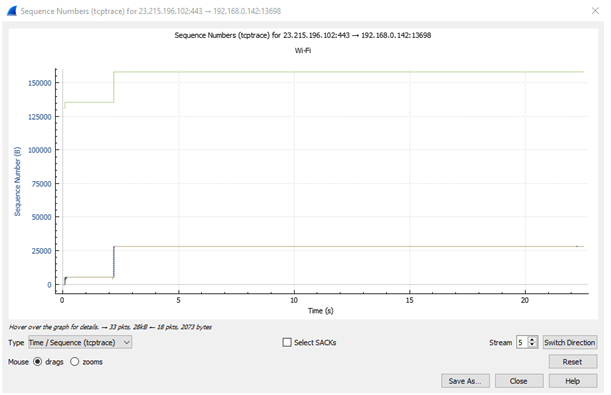
The above figure illustrates the time vs sequence (tcptrace) graph of the captured packets. Both the time sequence diagram mainly shows a data stream over time [2]. These two graphs are very useful to see that the traffic is moving without interruption, long delays, or packet loss. Here, for every 1 byte of TCP data delivered, the sequence number rises by 1.
Conclusion
Three tasks have been completed as part of this project on networking assignment that includes depiction of a socio-technical concept, SNMP v3 configuration, and Wireshark capture. Both social and technological systems have been examined, with software engineering as an example, in order to explain the illustration of socio-technical system design. In the second challenge, a network architecture was created utilising four routers and four switches, as well as the RIP 2 protocol. The routers were then configured with SNMP v3 and SNMP operations were done using MIB browser on PCs. However, in task three, the data packet was collected using the Wireshark programme.
References
[1]X. Zhang, "An Optimization Algorithm of Network Topology Discovery Based on SNMP Protocol", Journal of Computer and Communications, vol. 06, no. 01, pp. 104-111, 2018. Available: 10.4236/jcc.2018.61011.
[2]"Network Traffic Analysis For Diagnosing Network Problems Using Wireshark", Journal of Xidian University, vol. 14, no. 5, 2020. Networking assignment Available: 10.37896/jxu14.5/198.
[3]"Performance of Various VoIP Vocoders using Wireshark with Asterisk PBX", International Journal of Engineering and Advanced Technology, vol. 9, no. 2, pp. 2300-2305, 2019. Available: 10.35940/ijeat.b3652.129219. [4]P. Torres, "An overview on strategic design for socio-technical innovation", Strategic Design Research Journal, vol. 11, no. 3, 2018. Available: 10.4013/sdrj.2018.113.02.
[5]M. Qiu, B. Alexander, A. Simpson and S. Elhay, "A software tool for assessing the performance of and implementing water distribution system solution methods", Environmental Modelling & Software, vol. 112, pp. 52-69, 2019. Available: 10.1016/j.envsoft.2018.10.016.
[6] Amershi, Saleema, Andrew Begel, Christian Bird, Robert DeLine, Harald Gall, EceKamar, NachiappanNagappan, BesmiraNushi, and Thomas Zimmermann. "Software engineering for machine learning: A case study." In 2019 IEEE/ACM 41st International Conference on Software Engineering: Software Engineering in Practice (ICSE-SEIP), pp. 291-300. IEEE, 2019.
[7] Morgan, Njogu. "Cycling infrastructure and the development of a bicycle commuting socio-technical system: the case of Johannesburg." Applied mobilities (2017).












