Cloud Computing Assignment: Measures to Mitigate the Risks Faced by DR Alarms
Question
Task: You are suppose to develop a cloud computing assignment critically discussing about the measures to mitigate all risks for the DR Alarm's current platform of Multi Cloud and Microservice architecture to remain competitive and secure.
Answer
Introduction to the context of cloud computing assignment
Cloud computing refers to the on-demand provision of information system applications without the requirement of customer to directly check the data storage and computing capacity. The term applies to data centres, where a numerous people can access through the internet (Raj &Sadam, 2021).In order to achieve a better feasibility, accessibility and accessibility, the DR Alarms is coordinating the migration of all of its capabilities and data to the cloud. Therefore, this cloud computing mission monitors a thorough review and vital exchange in primary cloud models and their centres and comparative features in order to identify the most appropriate response for DR Alarms. This cloud infrastructure project covers the key elements of cloud assignment along with the threats of a certain kind of cloud-based structure and transmitting models. Furthermore, as cloud computing advances, it draws attention to the areas of interest and difficulties that DR Alarms may face in the course of operation in various areas, for example, disaster recovery, utility resiliency, SLA administration, remote server administration, and so on. When migrating to the cloud network, there are many possibilities to consider, including all future operational, technological, connectivity, and system threats. The report will thus evaluate the critical measures to mitigate all risks for the DR Alarm's current platform of Multi Cloud and Microservice architecture to remain competitive and secure.
Proposed Web Architecture for the Cloud
Based on the DR alarms need, the architecture model of is chosen. DR Alarms can operate the cloud architecture model in two ways. Primarily, the private cloud is available on site or from outside through a third-party vendor. In this scenario, the success of a multiload phase suits the basic needs of the company. Multi-domain has dispersed submitting templates to the cloud in order to execute an app in the most suitable computing environment. Multiload is a single-arrange use of the cloud storage services of IaaS, PaaS and SaaS from 2 or more free cloud providers.
IaaS: Infrastructure as a service is the provision, as a service, of hardware and associated software (Server storage and network). This is a traditional development in hosting which takes no more time to engage and allows users to provide on demand services. Contrary to PAAS, the IaaS provider is only operating the data centre, so the user must instal and manage the computing tools in the context of individual data centre. Amazon Web Services Elastic Compute Cloud (EC2) and S3 are instances of IaaS goods. Infrastructure as a service is a form of hosting. Networking, routing and storage is provided by the software. The IaaS vendor generally offers the hardware and management tools for storing software and operating the network of applications(Ritter, 2020). Bandwidth, disc and memory scale are generally included, and vendors claim the dynamic value and price of their resources for their dynamic offerings. The service provider is responsible for housing, repair and management of the installations. IaaS can be purchased either through pay-as-user or a contract.
PaaS: Platform as a Service (PaaS) refers to a collection of apps and programming tools stored on the servers of the vendor. Google Apps is a well-known service provider for platforms. This is the notion that someone can provide the hardware (as in IaaS) as well as certain application features – such as integrating into a standard programming array or databases – as the basis for the user application. Platform as a service (PaaS) is a development and deployment platform for Web-based applications that is distributed to developers as a service. The way company applications are built and implemented has been radically changed by cloud computing. As SaaS (Software as a service) for end consumers, PaaS is more cost-effective(Arpitha, 2018). Google App Engine is a traditional PaaS frame for developments to write and run their own applications when it comes to adaptability. It also supports developers in data storage and server management. The benefit of PaaS is that the number of users who can create, handle and launch web apps is greatly increased. In brief, PaaS seeks to democratise the design of web applications in the same way as the construction of a client or server application through Microsoft Access.
SaaS: The Software as a service is a security paradigm that focuses on cloud defence, i.e., security supplied by the cloud instead of on-site security solutions. The platform as a service model further improves the versatility of existing on-site depletions by operating as a hybrid solution. As the safety as utility model is adopted for DR alarms, the need for expensive monitoring hardware and complex configurations of security devices will be eliminated. The host safety model can be used to add hybrid features to existing on-site applications(Al-Said Ahmad &Andras, 2019). This will allow the organisation to choose chosen safety options for different remote sites more versatile. The DR Alarm Company can also provide a protection mechanism that is more reliable and faster than most on-site systems with software as a service. A decrease in costs for enterprises without compromising safety is the advantage of providing cloud storage.
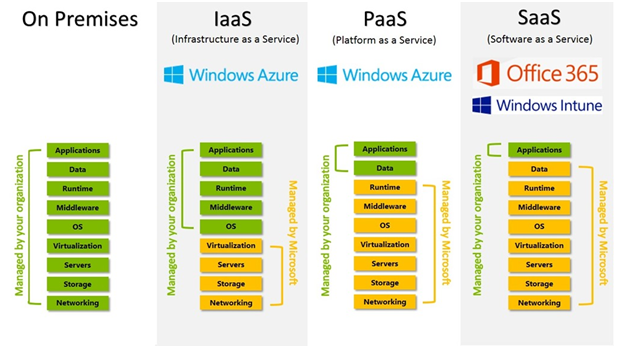
Figure: Cloud Architectural Models
(Source: Al-Said Ahmad &Andras, 2019)
Reasons to deploy suitable cloud architecture
Infrastructure as a service (IaaS) is a category of cloud computing service that provides critical compute, storage, and networking services on demand and on a pay-as-you-go basis. IaaS is one of 4 categories of cloud computing, along with software as a service (SaaS) and Application as a service (PaaS), and serverless. Migrating DR Alarm’s technology to an IaaS solution allows a user of the company to minimise on-premises data centre maintenance, save money on hardware expenses, and gain real-time market insights. IaaS technologies allow users to easily provision new software and improves the overall stability of the underlying infrastructure. DR Alarms can save the expense and hassle of purchasing and operating physical servers and datacentre resources by using MS AzureIaaS. Each resource is provided as a separate service component, and the company will have only to pay for the resources it needs. Thus, for DR Alarms, the platform is managed by a cloud computing service provider, Azure, while the company order, install, customise, and maintain their devices, such as operating systems, middleware, and applications.
Hence, after analysing the case study of DR Alarms, a suitable cloud architecture will be Infrastructure as a Service (IaaS).
DR Alarms are getting rid and are moving to advanced, stable cloud systems in existing data centres and physical servers. Several companies are designing cost-efficient software with better efficiency and easier scalability with a number of advantages of cloud computing, including any access to data, increased disasters recovery, improved flexibility and decreased infrastructure staff load. One such cloud computing model, IaaS, has simplified the lives of both companies and developers by relieving them of the pressure of worrying about technology.
Figure: Reasons to select Microsoft Azure IaaS cloud architecture
(Source:R. &Borse, 2018))
Thus, the Microsoft Azure cloud service of IaaS platform is recommended for DR Alarms and the diagram below is shown:
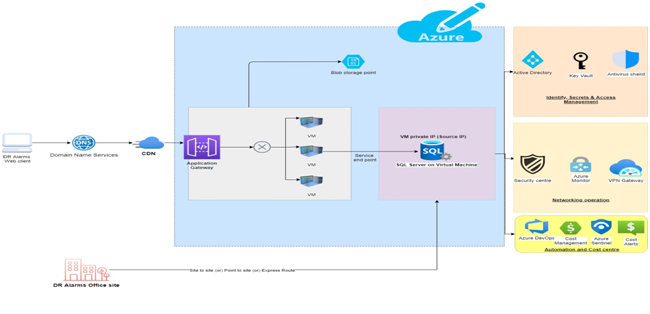
Figure: DR Alarm’s Integrated IaaS model MS Azure Cloud server architecture
(Source: Created by Author)
Benefits of IaaSMicroservices
IaaS is helpful to businesses in situations where scalability and fast provisioning are critical. In other words, companies that are rapidly expanding but lack the funds to invest in hardware are ideal candidates for IaaS models. IaaS may also benefit businesses with consistent application workloads that wish to offload some of the repetitive operations and repairs associated with maintaining networks. There are several benefits of the deployment of this IaaSmicroservice architecture, they are as follows:
- Increase Security: IaaS operators are investing aggressively in safety and skills technologies. The full-time role of this cloud host is to manage protection carefully, which is far more effective than a traditional internal device, in which a DR Alarm is quickly divided between myriad IT issues and sufficient safety.
- Dynamically scale: Using IaaS, it can quickly add capacity and reduce user requirements in peak hours. DR Alarms may provide sales people, freelance workers or distant employees with convenient details through the cloud, to improve the harmony between work and life.
- Self-service provisioning: IaaS model can enable the organizational user to access systems through simple connection of Internet(Salmanian et al., 2020)
- Relocate resources of IT: For higher value DR Alarms ventures, IaaS may free up IT workers. The cloud paradigm provides more stability for its companies by running the server locally. Therefore, if the company requires additional bandwidth, this cloud-based solution will respond to this demand immediately instead of updating the IT infrastructure on a dynamic and costly basis.
- Enable innovation: IaaS will leverage application programming interfaces of various systems of DR Alarms and will add new capabilities
- Disaster recovery: IaaS based model ofCloud allow quick recovery of datain various situations of emergency, ranging from expectedadversities to outage of power.
- Future-proof: IaaS can access to cutting-edge data centres, hardware, and operating systems of DR Alarms by powering automated systems rather than physical goods and hardware, reducing paper waste, improving energy quality, and lowering commuter-related emissions(Dimitri, 2020).
- Loss prevention: With a server of cloud, entire information that DR Alarm uploads to the cloud will be protected and conveniently accessible from every system with the connection of internet, even when the system that the user regularly uses isn't running.
- Automatic software updates and boost speed: TheIaaSCloud-based systems of DR Alarms' can rejuvenate and upgrade themselvesautomatically, rather than necessitating the IT division to execute a physicalassociation-wide update. Once IaaS computers are provisioned, developers can start working on projects. This will save precious IT workers time and resources that will otherwise be spent on outside IT consulting with the firm.
Issues of using IaaS model cloud architecture
The use of IaaS in a company has many advantages, but problems are still present. While advanced planning can resolve some of these barriers, other risks face that a customer needs to weight before deployment.
The following may be the challenges for DR Alarms:
- Unexpected costs: monthly charges could be added or higher than anticipated consumption
- Changes in processes: IaaS can include process and workflow modification(S &Kasmir Raja, 2020)
- Inventory of Runaway: Instances can be deployed, but not decommissioned
- Safety Risks: While IaaS providers protect the networks, the company will be liable
- Failure to provide support: Complex integration is often difficult to provide live support
- Complex integration: interaction challenges with current applications
- Safety risks: A lack of direct control will lead to new vulnerabilities(Sakthivel, 2018)
- Restricted personalization: Public cloud customers can only have limited access and customization capability
- Vendor Lock-In: It can be difficult to move from one IaaS supplier to another
- Broadband Dependence: Just the Internet access efficiency
- Selection Providers: Vetting and selection of vendors can be difficult
- Availability management: And the biggest networks had downtime
- SLAs are confusing: It can be difficult to recognise service level agreements (SLAs)
Threat and Risk Assessment report for services and data in the Cloud
Major Information Security risks that are associated with IaaS Cloud strategy
As DR Alarms migrates to the cloud, the Multi Cloud and Microservices architecture can be subjected to significant threats and challenges. To ensure that the design is secure, DR Alarms must accept all risks and minimise all risks in the following areas of IaaS. To fully understand the benefits of a multi-cloud environment, DR Alarms must build a risk management strategy. This section introduces a risk and safety thread assessment that recognises all potential mitigation steps in a multi-cloud and microservice sense.
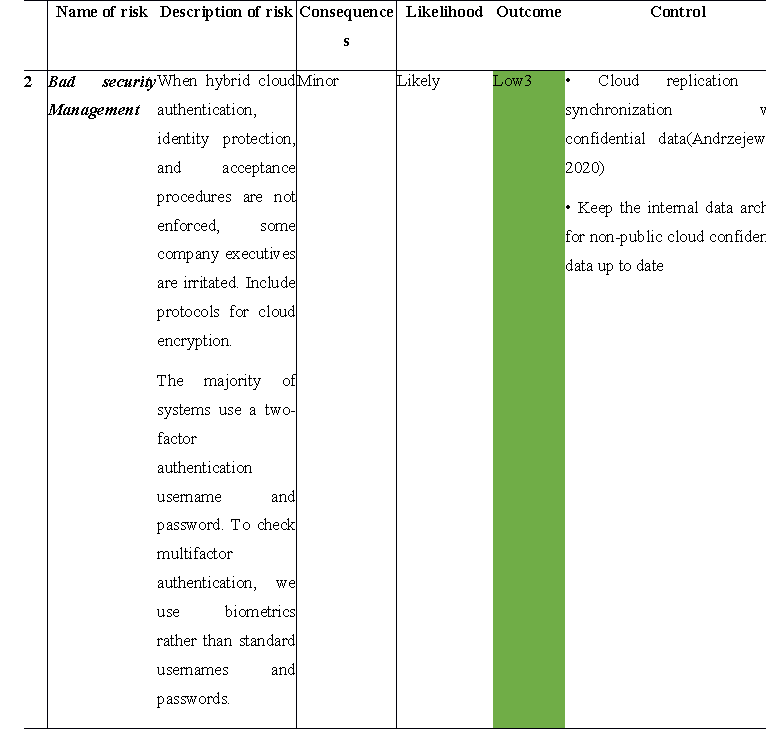
Proposed Information Security controls for the Cloud
Because of the huge attack surface provided by multi-cloud and microservices, shielding them is critical for large networks. The fundamental principles of safeguarding them in the industrial sense to deter infringements are critical to remember, and that is just what this study would do. Any realistic measures to resolve these security concerns will be listed. The primary goal of information management is to keep data within network boundaries and keep those outside of the user's network boundaries secure. There are some important steps of Information security listed below:
- Vulnerability evaluation and scanning: Patch management and assessment are needed since the security scanning section is responsible for detecting and removing trojans in cloud-based application programming interface systems.
- Security monitoring: The process should authenticate common event types such as unauthorised, authentication vulnerabilities, user logins, authenticated user processes, and access to authentication keys, vulnerability information from third parties and cloud service providers, and so on(Kumar, 2020)
- Automation and DevOps: DevSecOps allows for the centralization of protection in the application development process, including review of code testing, managementofpatch and configuration, logging of events and reportingandmanagementofuser access.
- Data Compliance: DR Alarms can thoroughly recognise all regulatory compliance rules and confidential information criteria. It is essential to follow safety legislation. It is important to understand the company's security practises and whether they comply with safety laws and regulations.
- Securing Application Programming Interfaces (API): APIs can enable DR Alarm’s developers to access services on different server systems that are used by the cloud(Duncan, 2020). Assist in preventing unauthorised access to user APIs and ensuring that passwords and other credentials are secured properly in addition to encryption.
Specific controls and steps to achieve data sovereignty
Data sovereignty applies to national laws that mandate that country's law to adhere to all data gathered or stored. This concept differs from data residence, which is a business predominance under which data is stored, while data residence normally represents some data sovereignty legislation in a country.
Since data governance in the cloud exposes businesses, it is essential for them to stay aware and compliant. Here are three strategies for doing that.
- Understanding the backup storages: Automated backups are now needed for DR Alarms. It is because of the cloud's pervasiveness that Box, Dropbox, Google Drive, and OneDrive use and data sprawl are almost ubiquitous in every enterprise(Vatanparast, 2020). The identification and classification of an initial and comprehensive backup must be performed by DR Alarms. Based on the results, any noncompliance will be detected, and any copies will be either dealt with, moved, or deleted.
- Maintaining compliances:The ongoing issue with the global footprint is the maintaining of the compliance with the data sovereignty laws of each territory within which DR Alarms is operating. The strict process of these laws is to apply one method to reduce complexity and apply them equally in all regions whatever other regions require.
- Monitoring the cloud model: DR Alarm’s solution can be found in the cloud itself. Though major cloud suppliers such as AWS, Microsoft and other credit acceptance rates are also an important factor in the focus of customers on cost, usability and flexibility. Most IaaS service providers have data centres in the country so that the first requirement is met.
Proposed BCP for Cloud services
fault-
tolerance and exception-handling.
fault-
tolerance and exception-handling.
fault-
tolerance and exception-handling.
fault-
tolerance and exception-handling
fault-
tolerance and exception-handling
fault-
tolerance and exception-handling
Fault tolerance and exception handling are the application resilience that support the transparent implementation of distributed codes on high performance cluster model of cloud. In both instances, resilience necessitates the use of four components in the application:
- A component of monitoring for detection of errors occurring early,
- An efficientdecisivemethod for determining attribution and effects
- A mechanismofcheckpointing slow overheads, and
- An effectivemechanism of recovery in which, DR Alarms must make certain variations to make sure about maintainability,disaster recovery and backup,resilience, securityandstability of a system to enable object-based storage devices (OSDS) in cloud storage.
A subsystem devoted to application resilience in cloud model thus involves many modules in control of particular activities that contribute to error management and continuous resumption of the application.
DR Alarms wants all resources to be transferred to a cloud platform. To that end, they plan to use the architectures from Multi Cloud and Microservices(Xing et al., 2020). The BCP for DR Alarms should have taken on board unique OSDS needs to ensure the reliability of the software. There are several advantages of hybrid cloud operations but DR Alarms want to make some upgrade to boost security and maintenance, like:
- Use load balancing for safe and non-hazardous data demands.
- For any of the business line applications, selecting a separate space for a more useful way of using applications such that in an emergency, developers of DR Alarms can turn to the space and make changes without intervening.
- To maintain a seamless experience, introduce a user role system for each user.
Backups and Disaster recovery
Since data is the most important thing in DR Alarms, data backup is a critical component of the disaster recovery plan (DR). Their absence will include major deaths, such as productivity, DR alarms, and reputational income. It is very difficult to determine when the disaster happens and the devastation. DR Alarms can do only when they handle a disaster and how they can successfully collect data from it. Via the backup and restore of systems and technology and assistance, a Disaster Recovery (DR) approach can be applied in DR Alarm. For backup and restore as well as for a DR platform, many businesses use the AWS Cloud.
There are some benefits of implementing a cloud disaster recovery plan.
- Scalability could be improved. Moreover, DR Alarms can maximise the backup's resources if necessary.
- They are on a pay-as-you-go basis. In other words, DR Alarms can only pay when it is absolutely necessary(Pardon et al., 2018)
- DR Alarms will be enabling its data to be backed up in several geographical locations. When a single backup location fails, it is often likely to provide several backup copies in different locations.
DR Alarms can establish a comprehensive disaster response plan after assessing above relevance. Initially, the Disaster Recovery Plan would contain the following components by:
- Making a risk assessment report.
- Determining the metrics for prevention, preparedness, and recovery(Kadam, 2017)
- Reviewing and revising DR Alarm’s strategy to response disasters.
Conclusion
The report has aware the CEO of DR Alarms that "unconscious risks, dangers and flaws make an organisation extremely impacted if they are ignored". Thus, in this report, the IaaS cloud model architecture has been selected for the company. Moreover, an Information Security Control Policy for the Cloud is also suggested, along with a Business Communication Plan (BCP) for DR Alarms. As DR Alarms wanted to shift its operations to cloud, the capabilities of Microsoft Azure cloud and its benefits of receiving Microservice-based architecture describes its ability to communicate the venture more productively and rapidly.
References
Al-Said Ahmad, A., &Andras, P. (2019).Scalability analysis comparisons of cloud-based software services. Journal Of Cloud Computing, 8(1). https://doi.org/10.1186/s13677-019-0134-y
Andrzejewski, K. (2020). Security information management systems. Management Sciences, 24(4), 1-9. https://doi.org/10.15611/ms.2019.4.01
Arpitha, R. (2018). Web Services using Cloud as a Platform. International Journal For Research In Applied Science And Engineering Technology, 6(5), 2381-2384. https://doi.org/10.22214/ijraset.2018.5390
Arzt, N. (2020). Application Programming Interface (API) for Immunization Information Interoperability. Medical Research Archives, 8(11).https://doi.org/10.18103/mra.v8i11.2282
Dimitri, N. (2020). Pricing cloud IaaS computing services. Journal Of Cloud Computing, 9(1). https://doi.org/10.1186/s13677-020-00161-2
Duncan, R. (2020). A multi-cloud world requires a multi-cloud security approach. Computer Fraud & Security, 2020(5), 11-12. https://doi.org/10.1016/s1361-3723(20)30052-x
Hubbard, D., Freda, A., &Swanagan, A. (2020). Data Governance 101: IR's Critical Role in Data Governance. New Directions For Institutional Research, 2020(185-186), 51-65. https://doi.org/10.1002/ir.20329
Kadam, D. (2017). Disaster Recovery Plan (DRP) and Business Continuity Plan (BCP) for Financial Cooperatives in New Market Economy. SSRN Electronic Journal.https://doi.org/10.2139/ssrn.2920431
Kumar, A. (2020). Information security controls for multi-cloud and microservices. South Asian Journal Of Engineering And Technology, 10(2), 1-4. https://doi.org/10.26524/sajet.2020.2.1
Pardon, G., Pautasso, C., & Zimmermann, O. (2018). Consistent Disaster Recovery for Microservices: the BAC Theorem. IEEE Cloud Computing, 5(1), 49-59.https://doi.org/10.1109/mcc.2018.011791714
R., T., &Borse, Y. (2018). Implementation of Cloud computing Service Delivery Models (IAAS, PAAS) by AWS and Microsoft Azure: A Survey. International Journal Of Computer Applications, 179(48), 19-21. https://doi.org/10.5120/ijca2018917248
Raj, V., &Sadam, R. (2021). Performance and complexity comparison of service oriented architecture and microservices architecture. International Journal Of Communication Networks And Distributed Systems, 1(1), 1. https://doi.org/10.1504/ijcnds.2021.10034598 Ritter, C. (2020). DISTRIBUTING SERVICES THROUGH THE CLOUD INFRASTRUCTURE: THE CASE OF A NORWEGIAN SOFTWARE FIRM. Aoir Selected Papers Of Internet Research. https://doi.org/10.5210/spir.v2018i0.10503
S, N., &Kasmir Raja, S. (2020). Multi-Core Aware Virtual Machine Placement for IaaS Cloud DataCenters. International Journal Of Engineering Research And Technology, 13(2), 368. https://doi.org/10.37624/ijert/13.2.2020.368-373
Sakthivel, D. (2018). A Study on Security Issues and Challenges in Cloud IaaS. International Journal For Research In Applied Science And Engineering Technology, 6(3), 909-914. https://doi.org/10.22214/ijraset.2018.3143
Salmanian, Z., Izadkhah, H., &Isazadeh, A. (2020).Auto-Scale Resource Provisioning In IaaS Clouds. The Computer Journal.https://doi.org/10.1093/comjnl/bxaa030
Vatanparast, R. (2020). Data and the Elasticity of Sovereignty. SSRN Electronic Journal.https://doi.org/10.2139/ssrn.3609579
Xing, L., Zheng, K., & Wu, B. (2020). System design object-based multi-agent network storage (OBMA-MNSS). Journal Of Physics: Conference Series, 1648, 042116. https://doi.org/10.1088/1742-6596/1648/4/042116












