Cyber-Attack Essay: Strategic Objects of Abacus Property Group
Question
Task: Write a 2000-word cyber-attack essay describing two strategic objectives in your own words. Then, describe two cyber risks that are known to have taken place since January 2018. These two cyber risks must be related to the two strategic objectives- illustrate how the strategic objectives and the cyber risks are likely to impact each other.
Answer
Introduction
Cyber-attacks damage the business of an organisation and effects on the trust of the consumers on it (Arcuri et al. 2020). The Abacus Property Group is mainly a top leading expandable real estate trust of investment in Australia (Abacus Property, 2020).In this case study, there are a total of 2 prime strategic objectives of Abacus Property Group are discussed along with two major cyber-attacks of Australia and the effects of this attack on the company in the future. The company should be very careful about those risks to prevent those hackers from hacking their network and system as well.
Two strategic objectives of Abacus Property Group
The company mainly focuses on some strategic objectives that help the company to gain success in the business market effectively. Two of the most important strategic objectives of the company are;
1. To deliver a better return on investment to investors through digital media.
2. To invest a huge amount of capital in the property that creates opportunities for maximising security holder value as well as driving long term returns effectively.
These two strategic objectives are responsible mainly for the current situation of this company in the business market. The first objective helps the company to measure the actual losses as well as profits, whereas the second objective helps the company to sustain its business with the help of the investors by developing a strong bond with them effectively.
Two Cyber Attacks in Australia
First Attack - There was a massive hacking attack conducted on the network and systems of Australia in 2020 (Roy, 2020). In this year, it had found that the attackers mainly targeted private companies and government organizations. The attackers used simple “copy-paste compromises” that was deciphered on the investigation with the help of exploding code as well as web shells and some other tools. Attackers basically used “remote code execution vulnerability” for targeting the systems and network. The Australian government primarily suspect that china is responsible for this massive hacking attack respectively.
Second Attack - There was also an epic incident of data breaching was conducted in the year of 2020. There was a huge cyber-attack was conducted in the April of this year by the hackers at Australian Government Agency Service NSW. As a result, the personal information of around 1,86,000 consumers exposed by the dangerous hackers (Haworth, 2020). This massive cyber-attack affected almost 47 employees of the information office of government, New South Wales. Thus, the hackers could easily get the access of the personal data. There were almost5 lakh documents were hacked by the hackers effectively. According to the investigation report that was conducted in April month on the same year, it can be argued that there are a total of 1 lakh 86 thousands staffs and consumers were recognised whose personal data were hacked by the hackers with ease.
|
Attacks |
Rating out of 5 (1 is for too low and 5 is for too high) |
Rating out of 100 (1 is for too low and 5 is for too high) Cyber Risk = (Threat*Vulnerability*Information Value) |
Outcome
|
|
First Attack |
Vulnerability – 5 Threat – 4 Information value - 5 |
100 |
The cyber risk of the first attack that was conducted by the hackers in 2020, is high as the vulnerability is too high, the threat is high as well as the information value is too high. |
|
Second Attack |
Vulnerability – 4 Threat – 4 Information value - 5 |
80 |
The cyber risk of the first attack that was conducted by the hackers in April, 2020, is medium as the vulnerability is high, the threat is medium, as well as the information value, is high. |
Table 1: Cyberattacks Ratings
Source: (Developed by the author)
The relation between the two cyberattacks with two strategic objectives of Abacus Property Group
The first important strategic objective of Abacus Property Group is to deliver a better return on investment to investors through digital media. It will help the company to know the position of it in the business market also. According to the first cyber-attack of Australia in 2020, a missive hacking attack was conducted to steal the data of network and system by the hackers. As the company delivers ROI to the investors though online, so there is a chance of hacking those data and stealing as well by the hackers effectively as they easily hack the network and system of Australian Government without recognising by the security department.
The second strategic essential objective of Abacus Property Group is to invest a huge amount of capital in the property, which creates opportunities for maximising security holder value as well as driving long term returns. This will be beneficial for the company in order to develop a strong bonding with investors for sustaining the business of this company efficiently. The second cyber-attack of the hackers was conducted in April, 2020, where almost 500,000 documents were stolen by the hackers with ease. Thus, the hackers can steal the transaction data of the company through the security of the company is strong enough as they were already done this in April, 2020.
Tree scenario analysis of past two cyber-attacks in Australia
The tree analysis of attacks can be defined as a process to create a flow chart kind mapping that helps to describe the procedure of hacking a system effectively (Kong et al, 2018).
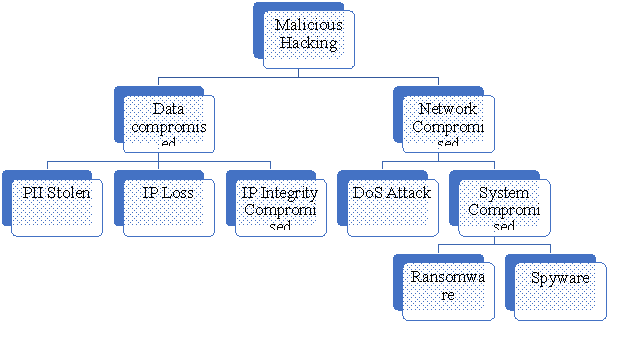
Figure 1: Tree analysis of the first attack in 2020
Source: (Developed by the author)
This tree analysis will help the company to understand the corresponding event that would lead the company to actual outcomes of this malicious hacking. This analysis mainly helps the company to identify the potential risks that the company can suffer in the future. The first malicious attack was conducted on network and security in the year 2020 with the same procedure. As per the analysis, the company should be very careful about the data of PII such as an address or numbers or private information of consumers and the company that can steal by the hackers in the future.Alongside this, the company can furthermore suffer from hacking the data of network system of it that may affect the company negatively. So, the company should be very careful about this to prevent malicious attacks towards it effectively.
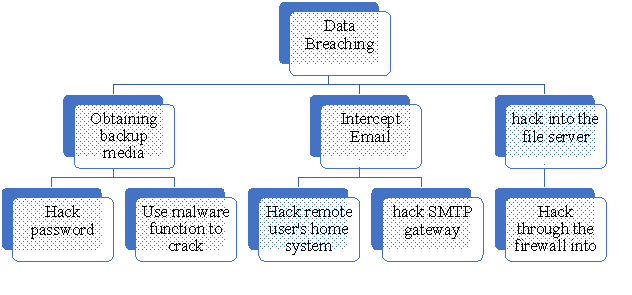
Figure 2: Tree analysis of the second attack in April, 2020
Source: (Developed by the author)
This tree analysis also helps the company to find out the predicted threats related to data breaching in the future. The second attack was conducted by the hackers in Australia where they stole the personal data of more than 186,000staffs and consumers in April, 2020. So, the company should be aware of those dangerous hackers who can steal the data of the users by hacking into the file server of the company. As for this, the company can lose the trust of the consumers towards it. Email is one of the popular media to send important information about any company regarding the business to others privately (Dada et al. 2019). But there is also a chance of hacking. The hackers can hack the remote user's system directly or they can hack the SMTP gateway to hack the personal information that is sent by the user to obtain the access of this information. So, the company should also be well aware of this in order to prevent those hackers effectively.
Organisational Culture
The framework of SWOT analysis helps any organisation in identifying some internal strategic factors effectively (Gürel & Tat, 2017). These internal strategic factors include strengths, weaknesses, organisational culture and more. As the Abacus Property Group is known as one of the most leading companies in the business industry, so the organisational culture of the company is environment friendly and stable that helps the company to build an effective and strong dealer community in the business market (Fern Fort University, 2020). So, the dealers help in promoting the company's product as well as investing to train the sales team of the company effectively.
Environmental Factor
Continuous changes in the factors of the macro-environment can directly impact on Abacus Property Group and others in the business of real. Various markets have several norms and environmental standards that can easily impact on the profitability of every organisation in such markets (Fern Fort University, 2020). Whereas within any country, there are several liability laws as well as environmental laws and these laws can affect the business of every firm. Before initiating any new business or entering the new market every company should well aware of the environmental standards, which are very essential for operating in those markets efficiently.
Impact of internal factor and external factoron Abacus Property Group with tree analysis of cyber risks
The considered internal factor is, the loyalty bonding with investors of Abacus Property Group. Apart from that the external business environment taken into account is Environmental law in Australia that influence the company in operating its business.
The company needs to maintain a well organisational culture in the business environment as it helps the company in building a strong relationship with investors, who play a crucial role in the development of this real estate company in the business industry of Australia effectively.
Whereas, there is also an external factor that affects the business of this company effectively. Implementing well environmental factors helps the company to grow up its real estate business in the Australian market as it impacts on the profitability of the company. It also helps the company to understand the environmental law of Australia that helps it to achieve growth in Australian industry without breaking laws and regulations of Australia.
According to the above mentioned two tree analyses, it can be argued that the company can suffer from above mentioned malicious attack as the company delivers a return on investment to its investors with the help of digital media through online, so there is an easy chance of cyber-attacking by the dangerous hackers. The hackers are expert in breaking security passwords or cracking security passwords to steal the necessary data of any company (Gagneja & Jaimes, 2017, August). So the company may suffer from these risks in the future.
Scenario Analysis
|
|
Cyber-attacks Before 2020 |
Cyber-attacks After 2020 |
|
Organisational Culture |
The organisational culture of the company is in a stable position that helps the company to develop a strong business community in the Australian Industry as well. |
The organisational culture of the company is not in a stable position as the pandemic situation of Covid-19 affects the business of this company very badly. |
|
Loyalty bonding with investors |
The bonding of the company with the investors is so good that the investors not only promote its business but also invest in its business without any hesitation. |
The bonding of the company with the investors is not quite good as the harmful situation of Covid-19 affects the business of this company negatively. |
Table 2: A scenario analysis of Abacus Property Group
Source: (Developed by the author)
First Reason - As per the above discussion, it can be argued that the company can suffer from the malicious attack of the hackers that prevents the company to deliver a better return on investment to the investors through digital media because there is a chance of steeling significance data of the company by the dangerous hackers effectively. As the incident of the first attack is recently happened with ease that is so hard to conduct, so there is a high chance of happening this threat in the future. That’s why the rate of risk level for this threat is 100 out of 125.
Second Reason – As per the above analysis, it can also be argued that the company may suffer from the data breaching risk as the company mainly deals with an online security system to protect all the personal data of the company along with its users. This is very important for the company to be well aware of those hackers who are experts in cracking the security system easily and can steal the data of the company with ease. As the incident of the second attack is not so old so there is also a high chances of occurring this threat very soon. That’s why the rate of this risk level is 80 out of 125.
Conclusion
According to this case study, it can be concluded that as the Australia government recently faced two major attacks in the pandemic situation of Covid-19 in this year, so the Abacus Property Group should be very careful about those massive attacks that were conducted by the expert hackers respectively. So that, the company should need to be very careful about this as well as the company should take some effective steps to prevent those hackers effectively.
?
References
Abacus Property. (2020). About Us. Retrieved 2 October 2020, from https://www.abacusproperty.com.au/about-us
Arcuri, M. C., Gai, L., Ielasi, F., & Ventisette, E. (2020). Cyber attacks on hospitality sector: stock market reaction. Journal of Hospitality and Tourism Technology, 11(2), pp. 277-290.
Roy, K. (2020). Retrieved 3 October 2020, from https://idsa.in/idsacomments/decoding-cyberattack-on-australia-kroy-140720
Dada, E. G., Bassi, J. S., Chiroma, H., Adetunmbi, A. O., & Ajibuwa, O. E. (2019). Machine learning for email spam filtering: review, approaches and open research problems. Heliyon, 5(6), e01802.
Fern Fort University. (2020). Abacus Property Group [SWOT Analysis] Weighted SWOT Matrix. Retrieved 2 October 2020, from http://fernfortuniversity.com/term-papers/swot/nyse/5987-abacus-property-group.php
Fern Fort University. (2020). Abacus Property Group PESTEL / PEST & Environment Analysis[Strategy]. Retrieved 2 October 2020, from http://fernfortuniversity.com/term-papers/pestel/nyse4/5987-abacus-property-group.php
Gagneja, K., & Jaimes, L. G. (2017, August). Computational Security and the Economics of Password Hacking. In International Conference on Future Network Systems and Security (pp. 30-40). Springer, Cham.
Gürel, E., & Tat, M. (2017). SWOT analysis: a theoretical review. Journal of International Social Research, 10(51).
Haworth, J. (2020). Service NSW confirms 186,000 customers’ data breached in cyber-attack. Retrieved 3 October 2020, from https://portswigger.net/daily-swig/service-nsw-confirms-186-000-customers-data-breached-in-cyber-attack#:~:text=A%20cyber%2Dattack%20at%20Australian,office%20for%20New%20South%20Wales.
Kong, H. K., Hong, M. K., & Kim, T. S. (2018). Security risk assessment framework for smart car using the attack tree analysis. Journal of Ambient Intelligence and Humanized Computing, 9(3), 531-551.












