Marketing Assignment: Business Opportunities & Challenges In China
Question
Task:
Cyber Security Assignment Instructions: Part A is mandatory, and you can select any two tasks in Part B.
Part A
-
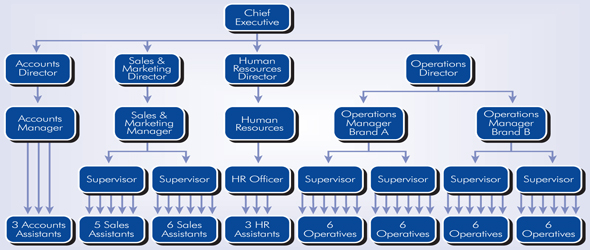
Describe the Australian Government's ISM and PSPF with emphasis on information classification. Develop an organizational structure to implement the requirements of the standards. –
Source : https://www.protectivesecurity.gov.au/Pages/default.aspx
You can refer to the Video by guest lecture on Week 1.
-
Run “netstat -an” on your own computer. You can investigate the services running on your machine and explain it in detail. You could look for any malicious or fictitious connections.
Note : netstat will work in Windows and Linux OS.
Part B
-
Charlie and Iris are working in the same company but a different department who meets during lunch time to discuss about their work. Today Iris discussed about a new position being created and Human Resources department starting advertising the position. Charlie then tell Iris “ I have a friend who runs a placement service and an find the right person. Once the position is filled, I will split the finder’s fee with you” .
Iris knows that her company may pay as much as half a years’ salary for the placement services. Charlies friend is likely o pay him a substantial amount if Iris awards the placement contract to them. If she can get a good employee and a little extra money on the side, everyone wins.
However, Iris is not comfortable with such an arrangement, and she’s pretty sure it’s against company policy.
If this comes to pass, is Charlie or Iris doing anything illegal?
What’s ethically wrong with Charlie’s proposal?
- Recently Australian government had released regulation about General Data Protection Regulation and Mandatory data breach notification act. Describe your understanding of GDPR and its implications in Australian businesses.
- Email is a vector through which an organisation's security can be attacked. There are different threats that come through email. What steps would you take to reduce the risks to an organisation's information security? (Hint : How to avoid Social Engineering)
In 2016, Census Australia website was shut down for 40 hours due to DDoS (distributed Denial of Service) attack. Explain what DDoS is, how the attack happened and what are the general countermeasures any web site which expects massive volume of requests should take?
Answer
Cyber security assignment Part A
Question 1
The Australian Government Information Security Manual (ISM) traces a digital security structure that associations can apply, utilizing their hazard the executive's system, to shield their frameworks and data from digital dangers. The ISM is proposed for Chief Information Security Officers, Chief Information Officers, and digital security experts and data innovation directors. This section contains a chief rundown of the ISM and direction on the best way to apply a hazard-based way to deal with digital security, which clarifies the six stages of the hazard the executive's system that the ISM employments.
The ISM speaks to the considered exhortation of the Australian Cyber Security Center (ACSC) inside the Australian Signals Directorate (ASD). This exhortation is given in agreement ASD's assigned capacities under segment 7(1)(ca) of the Intelligence Services Act 2001.
The ACSC additionally gives digital Security Council as customer guides, Australian Communications Security Instructions and other digital security-related distributions. In these cases, gadget and application-explicit counsel may accept priority over the guidance in the ISM.
Associations are not needed as an issue of law to follow the ISM, except if enactment, or a bearing given under enactment or by some other legal position, constrains them to consent. Moreover, the ISM doesn't supersede any commitments forced by enactment or law. At last, if the ISM clashes with enactment or law, the last comes first.
While the ISM contains instances of when enactment or laws might be significant for associations, there is no extensive thought of such issues.
The PSPF structure involves:
Four results that layout the ideal end-state results the Government expects to accomplish. The defensive security results identify with security administration, data security, faculty security and physical security.
Sixteen centre necessities that understand what elements must do to accomplish the administration's ideal defensive security results.
Most centre prerequisites have various supporting necessities that are expected to encourage a normalized way to deal with actualizing security across Government.
The direction that gives counsel on how PSPF centre and supporting prerequisites can be successfully executed.
Question 2
The - a boundary records all the PC's associations and listening ports, while the - n boundary shows locations and port numbers in the mathematical organization. A standard (shortened) result from Netstat - a resembles this:
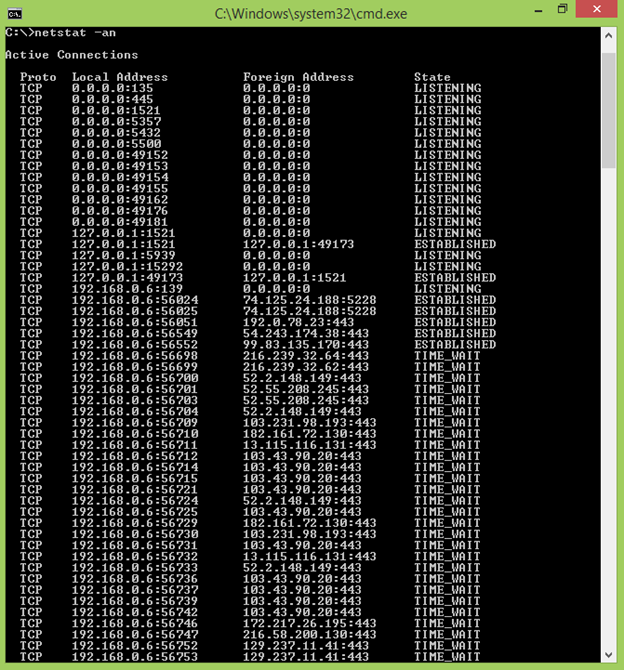
The main segment (proto represents convention) records the entirety of the transmission control convention (TCP) and client datagram convention (UDP) associations on the machine running Netstat. The subsequent segment is the machine's nearby IP address and port number, while the third is the far off or unfamiliar location and port number. The last section is called State, which is the expression that the association, or likely association, is in. "Tuning in" shows an exemplary open port tuning in for inbound associations. "Built-up" signifies there's a real association between your machine and the far off IP and port that can trade traffic. Sporadically, you'll see "CLOSE_WAIT" in this segment, which is a state TCP goes into while finishing a built up association. The residential location starting 127.0.0.1 are measures tuning in for associations from the PC itself, not from the Internet or system. If the IP address in this segment is your nearby system IP, at that point the port is just tuning in for associations from your neighbourhood organize. The port is tuning in for associations from the Internet if it shows your online IP address.
Part B
Question 5
Mobile phones are one of the most addictive as well as quite useful devices in case of emergency as well as personal entertainment. On an average a human being spends more than 119 minutes over cell phone, usage of mobile disturbs various daily activities, as well as in case of office using mobile phone is considered as an offensive act. According to some research, it could be identified that most of the companies have banned the usage of personal mobile phones within their organisations. Some people use mobile phones for communication but some use for making criminal activities, according to a study it has been clarified that use of personal mobile within the office would allow staff to leak various kinds of valuable data or information, due to which these organisation needs to overcome a huge amount of loss (Fujimoto et al., 2016). Some common issues of organisations under staff using personal cell phones within office campus include:
- Sexual Harassment is one of the most common issues which most of the women need to encounter within their day to day life, thus such type of sexual abuse during office hours which distract the mindset of the employee, due to whom the work might get delayed or most of the time employees might fail to complete certain tasks. Therefore it is considered a major issue for the organisation.
- Device attack is another major factor due to which hackers might directly get into companies server and access the data which is stored within the database. If the staffs use his/her personal mobile phone, it gets easier for the attacker to get into the companies database.
- Misusing companies cloud storage, in case if employee’s access companies cloud using his/her personal device, it causes a great threat for the company. As most of the time, the staffs use cloud storage for their personal use, or even sometimes; they might misuse the cloud account (Mojaye, 2015).
Some management methods which the companies need to apply in case of reducing the use of personal mobile phones are discussed in the following section. Use of the company’s laptop and mobile phone for official tasks, this policy must be applied strictly within various organisations which would decrease the threat of loss of data and information. By using only those devices, employees could log in to the company’s website for accessing any official file. Even every file stored within those devices must be password protected loss of company devices might result under great threat. Thus, companies must implement a law under which the loss of the company’s device should be considered a punishable act. Moreover, in case of decreasing the use of personal mobile phone companies must avail of the facility of a common telephone communication system by using which the staff can communicate with others in case of serious emergency (Burke & Noumair 2015). Apart from all such policies, these organisations must strictly follow some efficient rules which are quite necessary, such as every employee must have access to email using a company laptop, as email security is the major factor for keeping the data and information safe and secure from any kind of malware attacks.
Question 6
Different threats can appear there for the organisation from the email, such as different kinds of phishing and the other internal threats. However, taking proper measures, in concern of mitigation of these kinds of risks is highly necessary. Due to mitigating the email attacks and securing the organisational information, few steps need to be taken by an organisation, such as:
- Identification of the threats properly is the first step that an organisation should follow. For instance, the organisation ought to deal with the usual threats, such as the unofficial access towards the organisational PC, quickly and properly, since the organisation computers are always contained with different highly sensitive data, and if the data leaked then the organisation may ruin or face a great loss (Tyler, 2018). So, the organisation should be concerned about the identification of threat ahead of their harming.
- Utilisation secured emails, including end-to-end encryption, is a vital step for reducing email threats. Transacting mails with no encryption allows third party users to access and view the personal conversation between the organisational people. End-to-end encryption refers to a specific and significant technology, which allows an organisation to encrypt all information ahead of transferring it toward a server by a specific and significant key of encryption, which cannot be possessed by that server (Patel et al., 2020). However, it will also support the organisation for the purpose of securing the mails concerning the issue like information leakage, when a breach is present there on the server level.
- Moreover, it is necessary for the organisation to keep a high concern to the cybercrimes and cybercriminals. It will help the organisation to make sure that their organisation has been prepared for all sorts of cybercrime with significant plans and strategies. Furthermore, it is essential for the organisation for keeping details regarding the criminals’ attraction, such as what kind of information they may attack and whatnot (Safa et al., 2018). However, in this case, the development of several plans, including appropriate risk assessments regularly for the purpose of ensuring an efficient solution, is also considered as much necessary.
- Furthermore, properly monitoring the staff is also essential for increasing the information security level of an organisation. Organisational staffs have been considered as a major element of an organisation, since they hold insights regarding the business as well as are also privy towards the organisational functions. It is highly essential for an organisation to ensure that the staffs are not leaking any sensitive information regarding the organisational business to the outsiders. Furthermore, the organisation should maintain backup regarding each and every message, which has been transacted among the staff. A password manager is capable of being engaged in this case, for the purpose of formulating as well as administrating the organisational passwords. Moreover, it is essential to ensure that the organisational staffs have proper knowledge of the different sorts of email attacks and their mitigation techniques (Joshi & Singh, 2017).
References
Burke, W. W., & Noumair, D. A. (2015). Organization development: A process of learning and changing. FT Press. https://books.google.co.in/books?hl=en&lr=&id=ezMqBgAAQBAJ&oi=fnd&pg=PP1&dq=what+are+management+steps+which+
organizations+need+to+implement+for+reducing+the+use+of+personal+mobile+phones+
during+office+hours&ots=5AqR1lc0DP&sig=z_Lw4YFw-x5QPUud_fE1LethkPg&redir_
esc=y#v=onepage&q&f=false
Fujimoto, Y., Ferdous, A. S., Sekiguchi, T., & Sugianto, L. F. (2016). The effect of mobile technology usage on work engagement and emotional exhaustion in Japan. Journal of Business Research, 69(9), 3315-3323. https://www.sciencedirect.com/science/article/abs/pii/S0148296316000849
Joshi, C., & Singh, U. K. (2017). Information security risks management framework–A step towards mitigating security risks in university network. Journal of Information Security and Applications, 35, 128-137.https://www.researchgate.net/profile/Umesh_Singh17/publication/317789811_Information_ security_risks_management_framework_-_A_step_towards_mitigating_security_risks_in_university_network/links/5bb3c81d92851ca9ed34ec61/Information- security-risks-management-framework-A-step-towards-mitigating-security-risks-in-university-network.pdf
Mojaye, E. M. (2015). Mobile phone usage among Nigerian University students and its impact on teaching and learning. Cyber security assignment Global Journal of Arts Humanities and Social Sciences, 3(1), 29-38. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.1058.5381&rep=rep1&type=pdf
Patel, N., Sukhadiya, J., & Fiaidhi, J. (2020). Encrypted Communications: It's not what it seems.https://www.techrxiv.org/articles/Encrypted_Communications_It_s_not_what_it_seems_/ 12089535/files/22228200.pdf
Safa, N. S., Maple, C., Watson, T., & Von Solms, R. (2018). Motivation and opportunity based model to reduce information security insider threats in organisations. Journal of information security and applications, 40, 247-257.http://www.academia.edu/download/61633651/Motivation_and_opportunity_based_model_to_ reduce_information_security_insider_threats_in_organisations20191229-89791-zoples.pdf
Tyler, A. (2018). 10 essential steps for preventing cyber attacks on your company. Retrieved 27 August 2020, from https://www.itproportal.com/features/10-essential-steps-for-preventing-cyber-attacks-on-your-company/












