Cyber Security Assignment: Developing Case Study For Network Incident Detection
Question
Task: Write a cyber security assignment presenting a project proposal on a network analysis case study where a cyber-attack occurs and be investigated in an enterprise infrastructure.
Answer
Introduction
Aim of Cyber Security Assignment
In this digital generation, business communities are accessing computing technologies and digital systems to perform activities and increase organizationalefficiency. The adopted technologies are connected with the internet and communication channels that can be targeted by hackers and privacy of data can be breached easily. Securing data is a challenging task for companies due to which it is easy for the attackers to perform cyber-attacks and security threats over computing networks. The aim of this research is to propose a network analysis program where a cyber-attack occurs and propose effective mitigation actions and controls against identified cyber-attack and risks. Moreover, this research will provide depth insight into working operations of cyber-attacks and the negative implications posed by network traffic on internet networks and businesses.
Project objectives
The major objective of this research is to understand the importance of cyber-security in the enterprises. This research will also perform a cyber-attack detection and network traffic identification from computing networks. Another objective is to generate authentic network traffic and log through packet capturing and ELK stack features. The writer will identify and analyze the implications of cyber-attacks on privacy and confidentiality of data through literature review. Moreover, this research will suggest effective countermeasures and security controls against cyber-attacks
Project deliverables
The rate of cyber-attack is increasing rapidly and companies are less capable to identify and detect the internal risks affecting the privacy of sensitive data. This project will deliver a platform to understand the importance of cyber-security in businesses and will provide a network traffic based case study to examine the traffic signals from computing networks. Mainly, hackers use malicious codes and programs which are capable to produce unwanted and traffic signals over computing networks and increase chances of hacking and data breach (Aggarwal, Gonzalez, & Dutt, 2020).
This research project will cover the communication networks used by the companies and targeted by the hackers to perform cyber-attacks. In order to detect network traffic, one exported dataset from the ELK stack will be included and a capturing packet file from Wireshark will be included so that identification and detection of cyber-attack can be done effectively. Systematic literature will be conducted in order to analyze the findings of previous studies and datasets in regards to cyber-attacks. Moreover, the literature review will provide depth analysis of cyber-attacks and their implications on organizational performance and privacy so that detection of cyber-attacks can be done by enterprises effectively.
Background
Business communities are not dependent on internet networks and information technologies that increase organizational performance but also enable hackers to perform cyber-attacks. Idhom, M., Alit, & Fauzi, (2021) reported that cyber-attacks are capable to produce data breaches and ethical problems in the enterprises due to which the accessibility of sensitive data can be lost. The presence of traffic and unwanted signals in computing networks can lead to affect privacy and data collected from the customers can be hacked by the attackers.
It is important for companies to understand the importance of cyber-security in regards to the privacy protection and confidentiality of personal details. More than 70% of the companies worldwide suffer from cyber-attacks and security threats due to which it is difficult for the management to protect data and business operations from cyber-criminals. Major three factors are identified as leading cyber-attacks in businesses such as lack of experience, miss-configuration of networks and improper security controls (Sikora, et al., 2021).
Due to improper knowledge about cyber-security, it is difficult for the employees or users to manage internal security risks and vulnerabilities and increase the chances of a data breach. For example, in the year 1999, Jonathan James breached the million of data of US department including passwords, private details and many more. Moreover, Sont Pictures by the Guardians of Peace suffered from the data breach and hacking problems and cyber-criminals demanded 15 million dollars for restoring the personal data of users.
Therefore, it is important for the companies and users to understand the security risks and threats related to computing and communication networks to protect data against cyber-attacks (Toapanta, et al., 2020). This research is mainly based on cyber-attack and will develop a case study from the real-life incident related to a data breach. Effective security programs and systems will be suggested in order to improve the privacy and confidentiality of personal details. The literature review will help to gain depth insight into various cyber-attacks performed by the hackers and will also review the real life incidents posed by the hackers in the last few years.
Results/Deliverables
It is found that cyber-criminals are capable to target computing networks and web servers easily due to which companies can suffer from cyber-attacks and data breach incidents. Most of companies use simple passwords and security programs that are less able to defend against malicious codes and traffic signals (Zeebaree, et al., 2020). This research shows the importance of cyber-security in enterprises and also conducted a traffic detection program to identify and analyze the cyber-attack posed by the hackers.
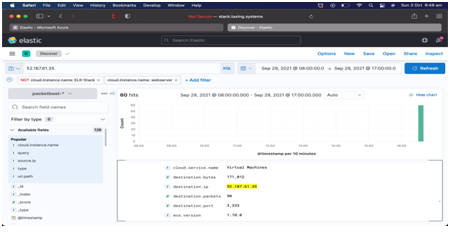
The selected ELK stack database helped to perform traffic detection activities and enabled to improve understanding in regards to the cyber-attacks and threats. In the second attack, the hacking activities performed by the hackers are identified and analyzed based on the collected data from the dataset.
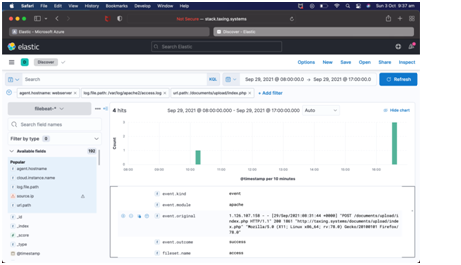
The cybercriminal accessed web browser to gain login details of the user and data packets linked with the systems are hacked easily. In uploading section, the hackers uploaded malicious based packet file that run to the web server and reduced confidentiality of sensitive data.
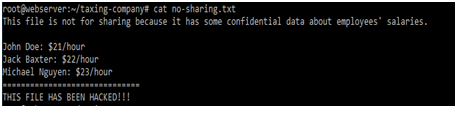
Moreover, the hacker connected internet networks back to the hacking machine and accessed the confidential file. It is observed that the investigator opened the backdoor file and show the content without taking permission of the users.

The included IP addresses and configuration details are also accessed that show the edited confidential file is inserted into the database. It is found that the hackers included network traffic and malicious codes which are capable to target computing networks and servers easily. The hackers were capable to gain login credentials of the users without their knowledge that produced hacking and ethical concerns in the enterprises.
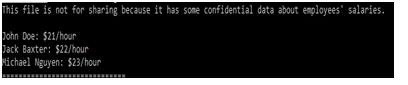
The connected systems with networks are detected and hacked by the attackers through malicious codes and increased chances of the data breach. In terms of security, the included systems are less secured and not connected with any firewall or encryption programs due to which it is easy for hackers to access the personal details and login credentials of users.
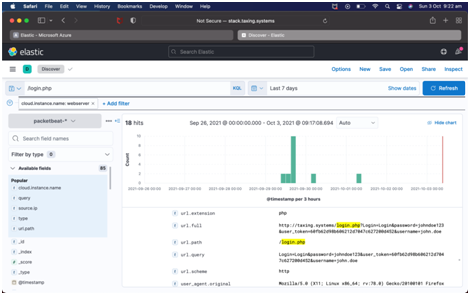
It is found that in the second attack, the cyber-criminals used the credentials to log in to personal accounts that affected the privacy and confidentiality of users’ accounts. As compared to the first attack, the second attack is simple and easy for hackers due to improper security controls and countermeasures. Most of the users include simple passwords for protecting accounts and hackers take advantage of this process to gain confidential data and hack banking details, user names and contact details. From the conducted literature, it is found that miss-configuration of networks with security systems can lead to increase cyber-attacks and security vulnerabilities.
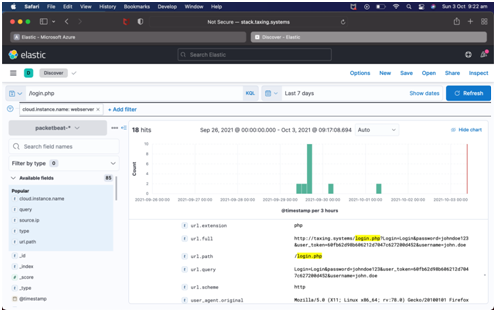
The selected web server in the second attack is not able to detect and identify internal risks due to which the hackers were capable to produce data breach incidents. Initially, the cyber-criminals gained personal details of web servers and computing networks such as IP addresses, connected security protocols. After this activity, the hackers use one of the credentials to login into the webserver and updated the backdoor and malicious based hacking files. Business communities need to focus on privacy while accessing communication networks and web servers so that private details can be protected and hacking problems can be minimized effectively.
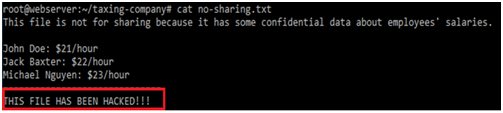
Penetration is an effective technique that can be implemented over web servers in order to detect and examine unwanted signals and unauthorized activities posed by hackers. In order to perform the second attack, the hackers are required to build a strong network traffic program that can help to transfer unwanted signals and increase the chances of a data breach. It is found that the taxing webserver did not contain effective security programs and frameworks due to which it is difficult for the company to manage insider risks and vulnerabilities.
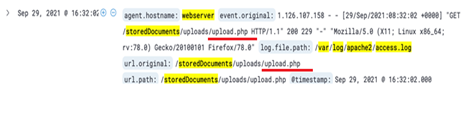
The cyber-criminal uploaded fraud or malicious files into web servers and performed backdoor activities in order to reduce the performance and accessibility of the web facilities. It is true that obtaining login credentials of web servers or portals can enable hackers to change or modify the internal information that can increase ethical and illegal problems in the workplace. The private details of employees including salaries, performance and banking details can be gained without their knowledge and hackers can use such information to perform illegal activities.
Therefore, it is recommended that companies should provide proper training to the employees about cyber-security so that simple passwords can be changed and complex or strong passwords can be applied over personal accounts. In order to manage internal security vulnerabilities and risks from web servers, companies should implement package filtering firewalls due to their potential to detect malware signals from servers and protect data from hacking. Using backup plans can be helpful for companies where cloud servers can be implemented that can store data easily and protect from cybercriminals. The findings show that improper security frameworks and controls over web server’s increases the chances of hacking and it is important for the companies and employees to access websites and accounts through authentic servers only. Moreover, encryption programs should be implemented that can helps to convert data into codes and secure data and account details from cyber-criminals effectively. It is recommended that AES encryption should be applied over web servers and communication networks due to their ability to provide larger private keys by which hacking and data breach incidents can be minimized.
References
Aggarwal, P., Gonzalez, C., & Dutt, V. (2020). HackIt: a real-time simulation tool for studying real-world cyberattacks in the laboratory. In Handbook of Computer Networks and Cyber Security (pp. 949-959). Springer, Cham.
Idhom, M., Alit, R., & Fauzi, A. (2021, May). Implementation of Web Server Security Against Denial of Service (DoS) Attacks. In IOP Conference Series: Materials Science and Engineering (Vol. 1125, No. 1, p. 012037).Cyber security assignment IOP Publishing.
Sikora, M., Fujdiak, R., Kuchar, K., Holasova, E., & Misurec, J. (2021). Generator of Slow Denial-of-Service Cyber Attacks. Sensors, 21(16), 5473.
Toapanta, S. M. T., Cobeña, J. D. L., & Gallegos, L. E. M. (2020). Analysis of cyberattacks in public organizations in Latin America. Adv. Sci. Technol. Eng. Syst, 5(2), 116-125.
Zeebaree, S. R., Jacksi, K., & Zebari, R. R. (2020). Impact analysis of SYN flood DDoS attack on HAProxy and NLB cluster-based web servers. Indones. J. Electr. Eng. Comput. Sci, 19(1), 510-517.












