Cyber Security Assignment Examining The Stuxnet Cyber Security Breach
Question
Task: Can Cyber Security Assignments effectively towards investigating major security threats like Stuxnet?
Answer
1. Introduction
This Cyber Security Assignment focuses on a unique cyber-attack which was noticed by many computer programmers in 2010. Ralph Langner and his team later identified the worm which later came to be known as Stuxnet, a sophisticated malicious worm. Many discussion s came into the forefront regarding the role of cyber-attacks and where the technology comes into picture in the digital world (Singer, 2015)
In early 2010, there were reports of Stuxnet in the media. The US Dept. of Homeland security called it as a ‘game changer’ (Denning, 2012). this Cyber Security Assignment explored factors which led to Stuxnet spreading fast from one affected computer to the other. What was different about this worm compared to the others was that it was set to work once it entered the industrial control system (ICS) which matched the features of the nuclear facility at Iran. The New York Times reported that this malicious worm was developed by United States and Israel (Denning, 2012).
If there were only improvements from the earlier weapon, then Stuxnet would not be called as a ‘Game Changer’ (Denning, 2012). This makes it important to review the analysis methods used by the cyber attackers to prepare a accurate Cyber Security Assignment analysis.
While collecting research for the Cyber Security Assignment , it was identified that in 2012 May, a request from the international Telecommunication Union was received by Kaspersky Lab in order to investigate the malicious virus which had possibly destroyed the files of the company in Iran. There was already an ongoing search for different variants of Stuxnet In June 2010, there was an explosion of a 500 Kilobyte computer worm called Stuxnet which infected about 14 industrial sites in the country of Iran. This also included the Uranium –enrichment plant.
2. Stuxnet Walkthrough
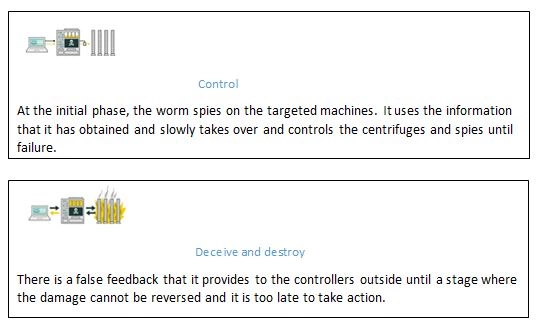
2.1 Stuxnet attack (overview): During the Cyber Security Assignment research it was also identified that three phases of attack occurred by this dreadful worm. Firstly, Microsoft windows machine and its networks were targeted by the worm. This happened by repeated replication of the worm. Secondly, Siemens Step7 software was attacked which also happens to be windows based. This software was used in industrial control system where centrifuges equipment were being used. The worm spied on these industrial system and caused the centrifuges that are spinning at high velocity to breakdown. All these happening discussed on the Cyber Security Assignment occurred without the knowledge of the operators at the plant. However there was no confirmation from Iran that the centrifuges there were damaged by this malicious worm.
Deploying this worm can
- Triggered the race in the cyber world by practical demonstration to rest of the nations of how cyber weapons can be utilized.
- Providing a template so that others can develop their weapons and create a threat.
- Can utilize the cyber weapons as state policies. (Middleton,2016)
The nations that have observed the deployment of Stuxnet and its success may possibly develop cyber weapons that are in line with Stuxnet. ICS devices can be their possible targets, so that they can keep them in cyber arms race. Though the code of this malware was not released to the world many analyst have tried to reverse engineer this in order to identify the code so that other cyber tools could be developed. during the course of preparing this Cyber Security Assignment, it has been identified the most viruses do not require to be developed from scratch, they just need to develop it from modifying existing codes.(Denning, 2012)
2.2 Stuxnet attack methodology:
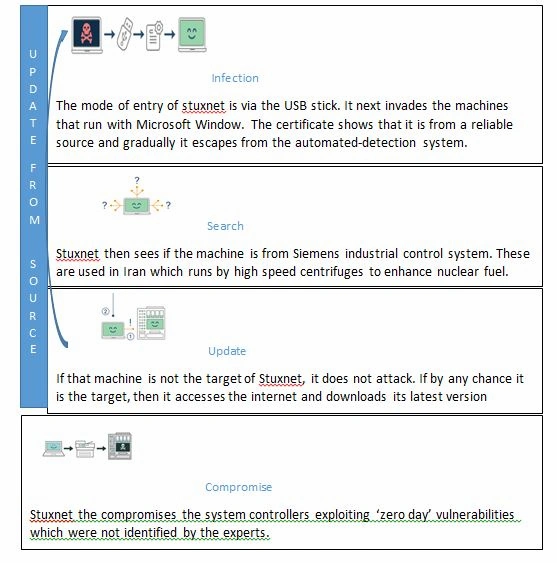
The Zero-day Vulnerabilities included the following CVE’s
- CVE-2010-2568- code when the operator opens a file LNK or .PIL file
- CVE-2010-2729- code when there is a remote procedure call sent by the attacker
- CVE-2010-2772- back end database accessed by local users in Siemens Simatic WinCC and PCS7 SCADA machines. (Rosenberg, 2017)
The Cyber Security Assignment also clarified that worms like Stuxnet can sneak easily between the windows running computers even if it is not connected to the internet. If USB was put into the device the worm spreads to the next machine that reads the USB drive. This could affect all the local networks and the experts thought that this malicious worm had spread around the world.
An attack par excellence was what made Stuxnet different. Stuxnet not only made the file process corrupt by causing technical difficulties but it also attacked the trust of the human operators. The identification of Stuxnet also came as an example as to how ethics plays a role in cyber war. (Singer, 2015)The malware not came as weapon that was designed in a way that damage is physical and that the damage occurs through the digital world. (Singer, 2015).
3. Real World Stuxnet Injection Incident
During the deadly malware perfumed during the preparation of this Cyber Security Assignment it has been identified that such programs can cause the nuclear facility named Natanz to be destroyed. The computers in this facility which were operating the machines were targeted. These machines were used to enhance the Uranium called as Centrifuges. (Lauder, 2016) these machines were attacked by the malicious worm instructing them to spin so that the machines went out of control. Since the machines were moving at high speed the force caused the centrifuges to break. The Virus deceived the operator in the control room that all was functioning smoothly. (Lauder, 2016)
Many such Centrifuges were destroyed over a matter of few years. This was roughly about 20 percent of the centrifuge of Iran. But the experts in the country had no clue what happened and why their centrifuges were getting destroyed and damaged. In all, the attack by Stuxnet was brilliantly deployed. (Lauder, 2016)
To clarify the Cyber Security Assignment continued to investigate Zero Days. ‘Zero Days’ had an anonymous source which said that the US intelligence organization and the National Security Agency had collectively called this Stuxnet plan as Operation Olympic Games. This was functioning smoothly until the country of Israel thought of modifying this code so that the malware could be made more aggressive (Lauder, 2016). In the next five months the analysts started to notice that their computers were shutting down possibly due to a bug. This was first identified in Belarus. Thus there was a hunt to find the cause for this bug. In general a virus code takes only few hours to reverse, but in the case of Stuxnet it took many months. (Lauder, 2016)And the experts were amazed to see a first of its kind malware which destroyed something physically. Until that the malwares could corrupt files in the computer, but this sophisticated virus got into picture that hacking can also overtake machines. (Lauder, 2016)
Though the world knew that it was a joint effort of United States and Israel, they never accepted it. However, the Cyber Security Assignment also identified that Iran tried to improvise on its cyber warfare so that it could deal with such deadly virus.
4. Summary and conclusion
From 1971 to 2012, the milestones of the malware affecting the software has always been in discussion. But with discovery of Stuxent at Kaspersky lab, the cyber weapon has reached a higher level in digital technology. The main idea of the worm Stuxnet was to destroy the nuclear plant in Iran. This malicious worm may someday create a problem and cause harm to its own creators. Millions of dollars are being spent to develop and implement these highly malicious cyber tools which may be increased many fold in the years to come. Following Stuxnet also there have been many cyber-attacks that have been causing damage to the critical infrastructure. Though there has been no attacks following Stuxnet, the implication here could be that the US involvement on the way of use of the cyber tools is largely dependent on the international community. It has been identified on this Cyber Security Assignment, whether these types of attacks have a positive or negative impact on the infrastructure can been known in the coming years. Stuxnet has been termed a cyber-weapon with precision.
Reference List
Denning, DE. (2012). Stuxnet: what has changed? Future internet, Cyber Security Assignment 4, p.672
Lauder, J (2016) Stuxnet: The real life sci-fi story of 'the world's first digital weapon .12 OCT .Available at https://www.abc.net.au/triplej/programs/hack/the-worlds-first-digital-weapon-stuxnet/7926298 Cyber Security Assignment [Accessed Aug 31 2019]
Middleton,A.(2016). Stuxnet: the world’s first cyber…Boomerang? Interstate-Journal of International Affairs, 2015/2016(2), p 1. Available at http://www.inquiriesjournal.com/articles/1343/stuxnet-the-worlds-first-cyber-boomerang[Accessed 31 Aug 2019]
Rosenberg, J. (2017) Security in embedded systems In: Rugged Embedded Systems-computing in harsh environments, pp 149-205
Singer, PW. (2015) Stuxnet and Its Hidden Lessons on the Ethics of Cyberweapons. Case Western Reserve Journal of International Law, Cyber Security Assignment 47(1), pp 79-86
Get Top Quality Assignment Help and Score high grades. Download the Total Assignment help App from Google play store or Subscribe to totalassignmenthelp and receive the latest updates from the Academic fraternity in real time.












