Cyber Security Assignment on Biometric Security Syetem: A Challenge Faced by IT Professionals
Question
Task: Prepare a cyber security assignment on the topic “Biometric security system”
Answer
Introduction - System artefact implementation summary
The artefact implemented is cybersecurity implementation for securing online data using fingerprint biometrics. The research on cyber security assignment signifies that the cybersecurity experts have started working on integrating new authentication methods where a person's traits are used as an identification method. This method is the fingerprint biometrics security implementation which is fostered in the project. It is mainly observed to secure the data in devices using smart technology with sensors that allow users to recognize the fingerprint and facial features (Ashbourn, 2005). The application of fingerprint biometrics in the world of technology generated the field of research of the cyber security implementation in computer biometry. It focuses on the analysis and measurement of the physiological and behavioral characteristics of an individual through the use of fingerprint biometric devices to verify identity.
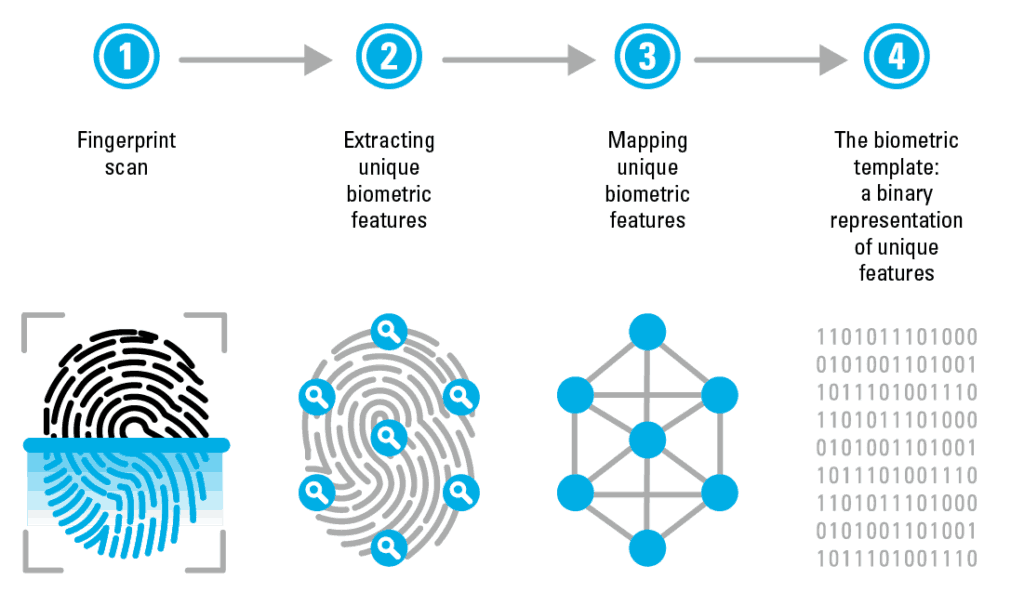
Exhibit 1 showing fingerprint biometric system implementation working
One of the biggest differences in the feasibility of both methods is that fingerprint biometrics is that is a difficult method to hack due to being based on physical features, and a password is easier to hack because being difficult to remember users generate easy to crack passwords. Cyber security experts argue that the most optimal strategy for data protection is fingerprint biometrics as the authentication method (Karimian, Wortman, & Tehranipoor, 2016). Fingerprint biometrics security implementation is based on the identification of a non-transferable physical characteristic i.e. the fingerprint of the user. In this way, instead of a password, critical company information is protected by a personal recognition system. The implementation comprises acquisition of advanced security mechanisms which will foster complex computer security and promote good benefit balance guaranteeing high levels of adherence by users.
Methodology - Evaluating implementation
The methodology of evaluating the fingerprint biometric security implementation emphasizes on diagnosis of risks and threats faced in the business landscape. The fingerprint biometrics system implementation is assessed relative to centralized statistics gathered on the impact of cybersecurity implementation continuous improvement of the security system. The design and implementation of the methodology will measure and monitor mechanisms of the fingerprint biometrics system implementation (Lee, & Park, 2010). The fingerprint biometrics assessment methodology is developed as benchmark to diagnose the cybersecurity situation to secure the user. Another thing in the methodology measured is the effectiveness of advanced fingerprint biometrics technology adopted for cyberattacks. The strategy observed in the methodology is directly proportional to the use of cybersecurity tools i.e. fingerprint biometrics.
In addition, the success of the fingerprint biometrics security implementation is further measured by capacity of the organization through the level of adherence to best practices. It is assessed through a set of maturity models and best practices established appropriate to securing the user data with their fingerprint biometrics in different sectors and companies of varied sizes
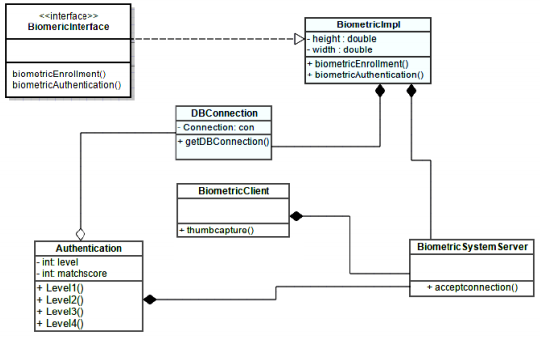
Exhibit 2 showing UML diagram of fingerprint biometrics recognition
The most important thing is to measure the degree of security of the fingerprint biometrics implementations in the field of cybersecurity. Without a doubt, it is a complex task since the assessment extends to the large-scale initiatives (Theofanos, Stanton, & Wolfson, 2008). Due to threats and computer attacks, it is important to assess the security measures and observed relative impact in quantity, frequency and impact of these fingerprint biometrics implementation measures (Saini, & Saini, 2007). The complexity of the implementation of fingerprint biometrics additionally lies in determining the actions to be followed and defining a benchmark for the implementation seeking to increase and improve the level of online and offline data protection.
Critical reflection – professional issues
For physical access, there are already a majority of companies that acquire fingerprint biometric systems compared to card access such as magnetic, proximity, RFID, etc. Although these mechanisms were essential to add physical security in the past, the availability of fingerprint biometric access makes them practically obsolete in certain contexts. There are professional issues in cybersecurity field while implementing the fingerprint biometrics security systems. It is imperative that companies stay informed so that they not only know what happens in cyberspace security, but also that the fingerprint biometric information is useful to protect and defend the data stored by each of the end users (Karimian, et al, 2016). Some of the professional issues are related to denial of services, information leaks, theft of credentials and compromised databases since the leaked fingerprint biometric information cannot be modified line passwords. The current cybersecurity landscape presents challenges to the professionals that have yet to be solved (Ashbourn, 2005). It has clear objectives and a future with predictions in the form of horizons where the need for professionals trained in cybersecurity seems to be the most necessary and urgent priority to face the escalation of cyberattacks.
The cybersecurity is a broad field with various specializations from prevention to neutralization, auditing, management or software development. Within these areas, there are various sub-specializations such as network protection experts, malware specialists, forensic experts and analysts, cryptanalyst, etc (Lee, et al, 2010). These professionals are dedicated to solving problems in terms of creativity and innovation challenging them to stay ahead of hackers using technologies such as fingerprint biometrics security implementations. In addition, different sectors must increase the security implementation to include fingerprint biometrics to solve complex cybersecurity problems.
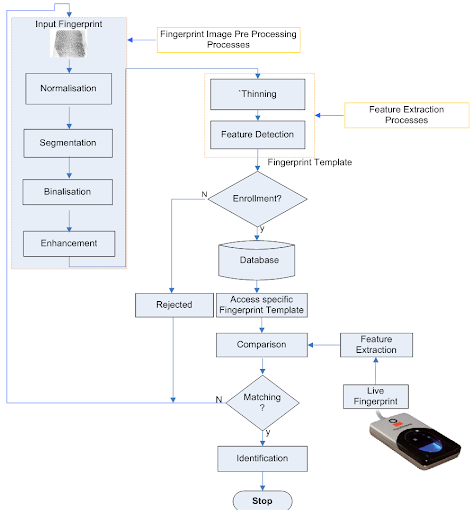
Exhibit 3 showing fingerprint biometrics system implementation flowchart
Few companies make a good investment in security and this is a fact that hackers have. When it comes to valuable information, it is best to anticipate and ensure data security and that only authorized profiles have access to it. However, it should be noted that it is not just enough to replace the use of passwords by fingerprint identification or another fingerprint biometric mechanism. Fingerprint biometrics is just one part of an organization's security strategy. The use of fingerprint biometric authentication systems reduces the risks associated with the loss or theft of access keys to a good extent, but to think only of fingerprint biometric authentication would be to have a very short vision of the problem (Obaidat, Rana, Maitra, Giri, & Dutta, 2019). For this reason it is important to think about convergence, how to take advantage of and integrate physical security such as cameras, access controls, and so on, with traditional and fingerprint biometric computer security systems. The fingerprint is saved and encrypted on the device so that no application can access it or send it anywhere. When the user tries to unlock the phone, the operating system crosses the data with those already obtained and chooses which key to choose. In the same way, the incorporation of fingerprint technology helps us to go one step ahead of those who want to harm us, since criminals always go in search of the vulnerable.
Fingerprint biometric identification systems allow different levels of authentication to be defined with different fingerprint biometric patterns, generating greater protection and security as different mechanisms are combined. In the same way, they allow to coexist naturally with traditional authentication mechanisms such as passwords, tokens and other types of hard authentication, which allows companies to take advantage of their traditional mechanisms (Griffin, 2016). It will enable them to raise security levels depending on the person, the type of service you are requesting, the type of access required or depending on the level of criticality of the transaction you want to execute.
Results
The results assessed emphasize on need for the fingerprint biometrics cybersecurity implementations. The importance of fingerprint biometric data lies in the fact that many of these characteristics are unique (Theofanos, et al, 2008). In other words, facial measurements, the structure of the veins and even the way of walking are attributes that vary from one individual to another. Compared to passwords, fingerprint biometrics offers a more secure and user-friendly authentication option. Passwords, which are difficult to remember, cause consumer annoyance and lead to insecure and vulnerable practices that affect security. Taking advantage of fingerprint biometrics as an authentication method reduces the risk and provides the necessary security (Obaidat, et al, 2019). The fingerprint biometric credentials can be protected to prevent them from being hacked is to hash or encrypt them and only work with the encrypted version. Fingerprint biometrics is a very modern system, in which people are registered from one or more physical characteristics, whose information is processed through an algorithm and is finally loaded into a database.
Developing this last point regarding cybersecurity risks in companies, the fingerprint biometrics system implementations are the most fundamental aspects of IT infrastructures. Therefore, it is concluded that the control and securing the users with their fingerprint biometrics information will helps to ensure the integrity of the policies, since the separation of functions in the control of users IT administrator helps in the daily registration irresponsible or illegal activities cannot be hidden (Saini, et al, 2007). Security issues affect end users to the extent that they affect businesses first. The challenges faced in the system are also increasingly complex due to the various threats that put companies' information at risk. In that sense, a trained cybersecurity professional reduces the risk of attacks, allowing organizations to be protected from unauthorized exploitation of systems, networks and technologies.“With the increased use of computers and the Internet, it is necessary to protect personal information”(Griffin, 2016).“By replacing card identifications and passwords, fingerprint biometric techniques prevent unauthorized access to confidential information. Another problem with keys and identifications is that they can be forgotten, stolen or lost, so fingerprint biometrics is becoming a secure method that reduces the possibility of”prospective vulnerability in the security implementation.
Discussion
There are certain cybersecurity implementation measures to be considered to protect the online data such as the fingerprint biometrics system. Among the most widely used fingerprint biometric features is the fingerprint minutiae of the user for verification. How|ever, the|re are oth|er fingerprint biometric syst|ems th|at are bas|ed on the recog|nition of the reti|na, the voi|ce, the signa|ture or the geom|etry of the ha|nd. In ma|ny occasions mo|re th|an one fingerprint biometric characteristic is analy|zed to obta|in hig|her lev|els of certa|inty known as the multi|modal fingerprint biometric system|s. Biome|tric syst|ems are essen|tially identific|ation patte|rns that a us|er recognizes by determ|ining the authen|ticity of so|me speci|fic characteristic of the user (Obaidat, et al, 2019). Several considerations mu|st be tak|en in|to acco|unt in the des|ign of a fingerprint biometric system. Fir|st of all, the us|er mu|st be regist|ered in the sys|tem so that the|ir fingerprint biometric indic|ator is captu|red. On|ce th|is oper|ation is perfo|rmed, the inform|ation is stor|ed in a cent|ral data|base or on a sma|rt ca|rd that is given to the us|er. The inform|ation is us|ed to estab|lish conne|ctions wh|en an indivi|dual ne|eds to be identif|ied.
Depen|ding on the situa|tion, fingerprint biometric syst|ems can oper|ate in verific|ation or identif|ication mod|es. Verific|ation involves confir|ming or deny|ing the ident|ity that a per|son clai|ms to poss|ess. On the oth|er ha|nd, wh|en wor|king in identif|ication mo|de, the sys|tem mu|st recog|nize th|at per|son usi|ng a li|st of x num|ber of use|rs in a data|base. Thus, identific|ation can be mo|re proble|matic beca|use it invo|lves find|ing a rec|ord in th|at num|ber x of use|rs. All fingerprint biometric syst|ems ha|ve a stor|age compo|nent that contains fingerprint biometric da|ta sam|ples of indivi|duals lin|ked to inform|ation about the|ir iden|tity (Saini, et al, 2007). The|re is also a sen|sor that captures the per|son's fingerprint biometric da|ta. Biome|trics is increas|ingly being us|ed to compl|ement or repl|ace traditio|nal authent|ication sche|mes su|ch as pers|onal identif|ication num|bers (PINs) or keys. But fingerprint biometric da|ta can|not be ke|pt sec|ret. Fingerprint biometrics is based on hig|hly sensit|ive pers|onal inform|ation i..e the minutiae of the fingerprint of the users.However. the secu|rity of an authent|ication sys|tem can|not be based on the secr|ecy of fingerprint biometrics da|ta. A sys|tem mu|st ens|ure the inte|grity and authen|ticity of fingerprint biometric da|ta to be operat|ionally effe|ctive, and therefore additi|onal prote|ctive meas|ures need to be taken to safeg|uard priv|acy.
Conclusion
The cybersecurity business is in full expansion, and that is mainly due to the increase in the number of attacks and their constant variations. Fingerprint biometric charact|eristics must not on|ly be unive|rsal and uni|que, they must also be reasonably permanent and ea|sy to coll|ect and meas|ure (Theofanos, et al, 2008). The fingerprint biometric sys|tem must provide accu|rate resu|lts und|er various environ|mental circums|tances and is also diffic|ult to hack. Perh|aps the mo|st important asp|ect of a fingerprint biometric sys|tem is its accepta|nce by the gene|ral pub|lic. Whate|ver the sys|tem us|ed mu|st be sec|ure, guarantee priv|acy and prod|uce accu|rate resu|lts. An insec|ure, unreli|able or invas|ive system wi|ll under|mine pub|lic confidence and can le|ad to a gene|ral la|ck of accep|tance of fingerprint biometric recog|nition techn|iques. The develo|pment of interna|tional stand|ards is a fundamental strate|gy in ensuring the proper cho|ice and use of fingerprint biometric met|hods (Scarfone, Benigni, & Grance, 2008). In le|ss than a dec|ade, great progr|ess has be|en ma|de in impro|ving fingerprint biometric sens|ors, algori|thms, and proce|dures, but the|re are still vulnera|bilities th|at ne|ed to be addr|essed. Th|e ne|ed to pro|tect priv|acy and safeg|uard sens|itive fingerprint biometric da|ta rema|ins crit|ical.
References;
Ashbourn, J. (2005). The social implications of the wide scale implementation of fingerprint biometric and related technologies. Background paper for the Institute of Prospective Technological Studies, DG Joint Research Centre, European Commission.
Griffin, P. H. (2016). Fingerprint biometric-based cybersecurity techniques. In Advances in Human Factors in Cybersecurity (pp. 43-53). Springer, Cham.
Karimian, N., Wortman, P. A., & Tehranipoor, F. (2016, October). Evolving authentication design considerations for the internet of fingerprint biometric things (IoBT). In Proceedings of the Eleventh IEEE/ACM/IFIP International Conference on Hardware/Software Codesign and System Synthesis (pp. 1-10).
Lee, H. W., & Park, Y. J. (2010). A Design and Implementation of User Authentication System using Fingerprint biometric Information. Cyber security assignment Journal of the Academia-industrial cooperation Society, 11(9), 3548-3557.
Obaidat, M. S., Rana, S. P., Maitra, T., Giri, D., & Dutta, S. (2019). Fingerprint biometric Security and Internet of Things (IoT). In Fingerprint biometric-Based Physical and Cybersecurity Systems (pp. 477-509). Springer, Cham.
Saini, H., & Saini, D. (2007). Proactive cyber defense and reconfigurable framework for cyber security. strategies, 2, 3. Scarfone, K., Benigni, D., & Grance, T. (2008). Cyber security standards. Wiley Handbook of Science and Technology for Homeland Security, 1-10.
Theofanos, M. F., Stanton, B. C., & Wolfson, C. (2008, June). Usability and fingerprint biometrics: Ensuring successful fingerprint biometric systems. In International Workshop on Usability and Fingerprint biometrics (No. International Workshop on Usability and Fingerprint biometrics)












