Data Security Assignment: Privacy Issues In IT Field
Question
Task: Conduct a research on data security assignment evaluating the security issues in IT field.
Answer
Abstract
This research paper on data security assignment proposes the security issues which are being faced. The confidential data associated with Information Technology companies will be discussed in this research paper. The issues of data security will analyse throughout the theory paper. Many times, protected data is leaked out by the unconsciousness of many employees. Using the system without knowing how to properly access it, can be a risk for any business organisation. Every multinational company has their own strategies, facts, software which cannot be accessible by any other people as a general purpose. Even only the authorized person has the permission to access the system in the business organisation. The risks and the challenges faced due to the data security within a business firm will be evaluated in this research on data security assignment. The researcher will discuss the understandable value of protected data for a multinational company. The reasons why a company keeps them from other companies will be discussed in the chapter of literature review. This research on data security assignment will present tables by interviewing the employees and manager of IT companies. The direct questionnaires will support the authenticity of data of this research paper.
Introduction
The businesses are known to stand for losing the confidence of the customers as well as respect when they allow unauthorized access for the customer data. Because of this, the businesses are known to take information security along with cyber security in a serious way. Besides, the significance based on the protection of the customer data, hacks and breaches found to be much more common [1]. This seems to be a result of inadequate measures of security along with the hackers to be better within the businesses for accessing the secured networks. The risks related to the security measures in the IT system are dangerous to a significant number of organizations. It can lead them to face financial and identity loss. The use of information technology has undoubtedly presented the business with certain opportunities that have been undreamt for only some of the decades. However, it has also been considered to introduce several challenges. It has been evidenced in the data security assignment that the businesses spend 5% and above regarding their annual IT budgets based on their protection over the disrupted operations as well as theft because of the information theft. Thus, the threats based on information security are known to be like the software attacks; thefts based on intellectual property; sabotage; theft identity; information extortion and information or rather equipment theft.
1.1 Background of the research on data security assignment
The present research on data security assignment identifies the issues which are generally faced within the field of information technology [2]. It presents the problems related to the data securities for the respective field. However, the causes and effect of the data security and its privacy is also an important aspect which needs to be focused within the respective study. It has been evidenced that the Monetization based on stolen data which is a problem within the cyber criminals is known to be less difficult due to the improvements within the black markets of cyber-crime along with the utilisation of digital currencies.
Cybercrime is responsible for taking several faces through the data breaches for the malicious programs which can attack the network of any business organisation along with disruptive or rather corruptive service based on the corporate data. On the other hand, it has also been evidenced that a quick adoption related to new technologies within the hackers along with an increase of new online users have been some of the reasons regarding the growth of cybercrime [3]. Thus, an increased ease for committing cybercrime has been considered due to its growth being a service.
1.2 Aim of the study
The aim of the research on data security assignment is to examine the issues of data security along with the causes and effects that are related to the field of Information Technology.
1.3 Research objectives
- To describe the security issues as well as the cause and effect related to the data within the IT field
- To explore the security issues within the field of IT along with explaining its causes and effects
- To analyse the extent of data security issues that can impact the organisations
1.4 Research questions for the case of data security assignment
- What are the security issues associated with data usage and computing metrologies?
- What are the challenges associated with security in IT infrastructure?
- What are the impacts of lack of integration in security ecosystem?
- What are the characteristics of database management in implementing cloud computing?
1.5 Rationale
While the businesses are considered to connect their computers and systems, one of the problems of the user can affect each and every one within the network [4]. Besides certain benefits for making use of the networks, networking is known to raise greater potential regarding the security issues like data loss; malicious attacks like viruses and hacking as well as security breaches. Businesses are known to implement the measures for reducing the vulnerability of the networks for unauthorized access or rather damage [6]. This might not be possible or rather economically practical for elimination of all the vulnerabilities that are performing within the risk assessments of IT which is eventually significant for deciding the measures that need to be implemented. The respective challenges and risks of accessing the confidential data seem to be an issue. It has also been evidenced within this data security assignment that the cybercrime issues are increasing regularly [5]. Thus, the present study build in the data security assignment highlights the measures for keeping the data confidential for the business organisations.
1.6 Methodological approach
The study provided in the data security assignment aims to abide by the philosophy of positivism and descriptive as well as deductive research approach. The design for the research will be explanatory as both qualitative and quantitative primary data will be collected and analysed for the study. Surveys will be carried out for retrieving quantitative data while interviews will be carried out for the qualitative data. The sample size for the quantitative data will be 25 employees while for the interview 1 General Manager of an IT firm will be chosen. Random sampling technique will be resorted to, for the study. The secondary research process on the relevant research paper and journals will enhance the current research process on data security assignment with critical information on the security difficulties in the IT system.
2. Literature review
2.1 Introduction
In last few decades, the significance of information technology has been increasing exponentially as global companies adopting internationalization approach. The rapid integration of cloud computing, IoT and global networks increases the susceptibility to information theft, data leakage and identity theft as well. The high computational power associated with cloud computing, big data emerging as tool to high productivity, sustainability and low-cost approach to system architecture and IT infrastructure. SMEs and start-up companies utilizes cloud-based IT infrastructure and big data for analyzing customer trend and interest as well but there is a common trend among these companies to expenses less to secure the IT infrastructure and communication used in the system. Less emphasis on the security measures exponentially increases the data vulnerability which has a negative impact on the data security and productivity as well. The rate of cyber-crimes has been increasing exponentially in last few decades. There are two major objectives associated with current research on data security assignment such as security issues associated with data used and shared in IT field whereas security issues IT field also need to be analyzed in order to identify the impact and challenges [12].
2.2 Security issues associated with data usage and computing metrologies:
Disruptive software programs are deployed to interrupt the IT infrastructure and communication among departments where data have been analyzed and shared for the today basis computing methodologies. There is various disruptive software are in practice to commit cybercrime which causes huge loss the organization and individual perspective. The impact of the cyber threat has huge impact on data security. The below section of data security assignment elaborates various threats associated with data security and IT infrastructure for organizations such as malicious programs, viruses, phishing and denial of service etcetera.
Malicious programs- with the usage of computer and network in global perspective, there is a great deal of risk associated with malicious programs. A virus could be defined as the piece of computer program that is attached with a valid document and valid software programs which could be installed from internet or an unknown source. The objective of the virus or malicious programs mentioned in the data security assignment is to invade into the normal computing process and hijacks data or information from the system to the host server. Most of viruses are not self-activating whereas it is associated with specific triggers which are similar to normal computing techniques. The virus eventually multiplies to a proportion to disrupt normal functionality and corrupts the system [13].
Phishing- in modern IT systems, phishing is considered as the one of the significant cyber-attacks that predominantly sends scamming emails to users to extract valuable information or data. The main target of the phishing email is to extract personal information, banking details or purchase history. Scammers use phishing technique to break into bank accounts or use that personal information to steal personal data or to make false online footprint. The phishing activities have been grown exponentially in last few years where an estimated growth rate of 65% registered in case of data theft and bank fraud. As per the investigation on data security assignment, 75% businesses are globally affected by the phishing activity irrespective of size and business functionality. There is an average of 1.5 million phishing each month affecting businesses globally.
Denial of service (DoS)- malicious cyber actors sometimes acts as disruptive malicious code that prevents legitimate users to get access to the information system, network resources and LAN or WAN. Banking accounts, emails or websites are the most vulnerable target for DoS. The primary methodology of DoS is to torrent traffic to the target user which eventually prevents user to access the files or online accounts. Organizations bear huge loss in terms of money and time due to DoS whereas losing control over resources may cause disruption in process and functionality.
In modern business scenario, cloud computing proved to be an emerging computing technology in terms of cost management, IT infrastructure and efficient computing platform. The usage of cloud computing is associated with various security issues and data vulnerabilities. The below section provided within this data security assignment elaborates prominent security threats associated with cloud computing.
The major concern with cloud computing outlined in the data security assignment is data breach whereas big data associated with cloud computing methodology. A huge amount of sensitive data is associated with the cloud computing methodology. Data breach poses huge security threat for the huge amount of sensitive data such as personal data, banking details and transaction details etcetera.
People used to store sensitive details such as accounts details in online platforms. Account hijacking is one of the major security threats in modern could computing techniques. Two major techniques in case of account hijacking are scripting bug and usage of reused password. In recent times, Man in Cloud attack is proved to be one of the major vulnerabilities for cloud computing techniques.
The malware injection is nowadays proved to be one of the major threats for modern computational processes. These malwares mentioned in the context of data security assignment are embedded as coded instances which used to be executed in the form of SaaS within the cloud server. The malware compromises with the integrity of the sensitive information and steals personal information.
Cloud computing enabled small and medium organizations to access huge amount of data which would be a helpful approach in terms of market analysis and sustainability. The process expansion and huge storage capacity encouraged hackers to host malicious codes such as malwares and unauthorized software into their cloud system that steals sensitive data and account information that would be a huge threat for users and organizations.
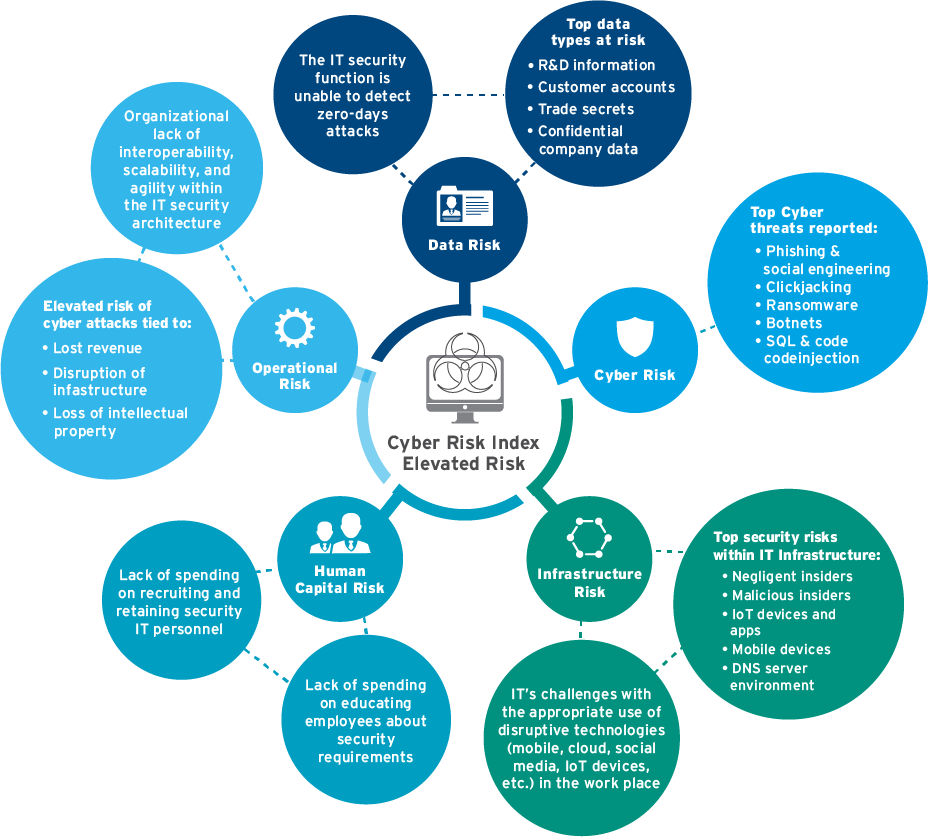
Figure 1: security issues IT infrastructure [14]
2.3 Challenges associated with security in IT infrastructure
There are four major cyber security challenges have been emerging in modern global business scenario as mentioned in below section of data security assignment.
Social engineering attack- there is exponential growth of AI in case of developing malicious codes for cyber-attack such as social media tracking for extracting personal and professional information. That information is acting as new threat component for organizations which comprises of phishing and spear-phishing attacks [16].
Supply chain attack- the risk factors associated with supply chain is not completely understood nowadays where vulnerability is high in terms of cyber-attack and phishing attacks. Cyber attackers associate themselves with the supply chain to gain information or data from the corporations.
IoT and infrastructure attacks – cheap and less secured IoT devices proved to be vulnerable to personal information and data. ransomwares are most active in IoT devices that have security vulnerabilities and suspectable for information theft [17].
2.4 Lack of Integration within Security Ecosystem
Global organizations deploying huge amount of security solutions into functionality which emerges as major security challenge for the productivity and data security. Security solutions from different vendors associated with major integration with the security ecosystem. The lack of integration creates problem for the IT team which emerges security issues for resolving the security threats due to lack of concrete direction and guidelines.
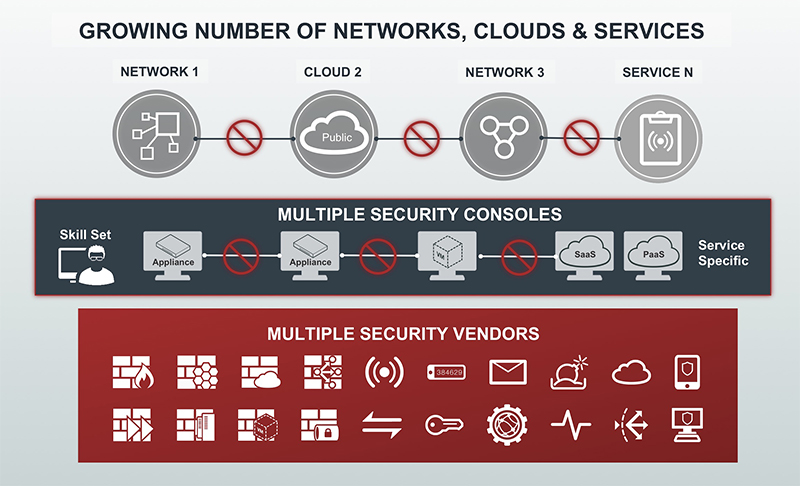
Figure 2: end of end security ecosystem [15]
3. Methodology
The current research paper on data security assignment aims to find the features and characteristics of cloud computing database management. It emphasizes the security measures within the information system. It also finds out the configuration of IoT and its contribution in the database management system. The research paper further focused on the security issues within the computing metrologies. The software used by the malicious users to commit cybercrime is identified in this research paper. The researcher has gone through different survey and experiments to conduct the research process. It elaborately mentions the various threats associated with the IT infrastructure. The research paper has also focused on overcoming the risk factors and secures the data and personal documents of the organization [8].
The current research paper involves a quantitative description of the different given aspect. It examines the relationship between the variables. It is a primary research containing quantitative research approach. It has dealt with various statistical and theoretical experiments to come to a certain conclusion. There are various independent and dependent variables used in this research paper to evaluate the scope of study. The researcher has predicted a model before starting to conduct the current research paper. It has given out a specific ad certain result regarding the two database management systems and their security issues. The data used to proceed with the research are well suited and gathered demographic data that efficiently describe the composition of the sample. The survey and the experiments have been done in an ethical manner. Anyone associated with the research on data security assignment has been credited and acknowledged by the researcher [3].
3.1 Research questions
- What are the security issues associated with data usage and computing metrologies?
- What are the challenges associated with security in IT infrastructure?
- What are the impacts of lack of integration in security ecosystem?
- What are the characteristics of database management in implementing cloud computing?
3.2 Qualitative /Quantitative method
In the research method of discussing the security issues associated with the usage of data within computing metrologies and clod database management, it is very important to adapt a particular method of conducting the research processes [7]. Qualitative research is a range of research method that possesses reliance over the data of unstructured analysis from non-numerical already existing data sources. It deals with interviews, observational courses, and other recordings of video and audio in collecting data.
The quantitative research method considered in the context of data security assignment deals with numerical representations and statistical analysis for the research processes. It deals with quantification of behaviors, attitudes, and opinions along with other factors affecting various variables to make generalizations regarding a larger sample or a larger focus group of population. It aims to understand the relationship between the dependent and independent variables in a particular research population.
3.3 Method used in current research
The current research paper on data security assignment on discussing the security issues of cloud computing in an IT infrastructure deals with the qualitative research method. The qualitative research methods are used to identify the psychological factors in a research subject for answering the probable questions regarding the various opinions, attitudes, and beliefs of the target population. It deals with isolation and identification of various variable factors in determining the main findings [8]. The research problems in qualitative study based on the case scenario of data security assignment are judged in a clear and unambiguous way.
3.4 Application and Importance of method
Qualitative research method in studying the security issues of cloud computing within an IT infrastructure are aimed at gaining a deeper understanding of a particular event. It deals with the surface description of a big population in sampling [9]. It is mainly concerned with the explicit providing of rendered structure in patterns of specific order to form a participant group through ethnomethodology. It does not incorporate manipulations and treatments of imposed variables for attaining operational definitions. It uses the observations in the method of data collection. Observation is utilized in qualitative research method in an extensive way. It is determined to evaluate the outcomes on the basis of the perceived level of observations.
3.5 Problem of the method
Qualitative research methods in studying the security issues of cloud computing within an IT infrastructure are criticized on terms of overusing the interviews and target groups at the other expenses regarding the ethnographic methods in observational analysis of documentary studies. It deals with various strengths for properly conducting the research processes [10]. The rigors include biasness, and small scale anecdotal. The validity of the qualitative research method refers to the contradiction of evidences. It includes the validity in terms of substantiation by a number of technical processes to involve use of contradictory triangulations for validating the respondents in particular terms.
3.6 Data collection method used in the data security assignment
The data collection method in the primary research process will be obtained from the survey process to document accurate data. The analysis process from the primary research will conduct quantitative method to evaluate the research questions. The data collection method in studying the security issues of cloud computing within an IT infrastructure are concerned with previously existing data sources. It deals with secondary research methods and techniques of data collection [11]. The sources of secondary data collection are books, journals, newspapers, articles and so on. Secondary research method used in this data security assignment is a range of research method that possesses reliance over the data of unstructured analysis from non-numerical already existing data sources. It deals with interviews, observational courses, and other recordings of video and audio in collecting data. It will help the current research process to record the findings and data of the current research paper securely. However, it is necessary to back the arguments derived from the interaction process with the research participants by studying other research papers.
The primary research process is necessary for understanding the current situation in the IT field related to the ‘data breaching’ and hacking incidents explored herein data security assignment. The survey process will consider interviewing 25 individuals from the IT filed. They are happened to be employees who are the direct user of technologies. Their perspective will help the current research process in understanding the issues and risks related to the IT security, and how the current organizations are concerned with the security process. The survey process will also include one official from the IT field to understand the responsibility of the organizations in securing the valuable data and documents. The increasing incidents of cybercrime is a concerning factor for various industries. The secondary research process with the relevant research materials that have discussed with the cybercrimes related to the ‘data breaching’ and security hacking process in different IT organizations. It will help the current research process implemented in this data security assignment in establishing a strong background and discuss with the participants with construct data. It will also help in understanding the reliability of the response from the research participants.
3.6 Research Design
Quantitative Research on data security assignment
Survey Questionnaire for 25 employees of Information Technology Company
Q1. How far do you agree with the fact that issues of data security will affect the company?
|
Options |
Response Frequency |
No. of Respondents |
Total No. of Respondents |
|
Strongly Agree |
42% |
10 |
25 |
|
Agree |
32% |
8 |
25 |
|
Neutral |
24% |
4 |
25 |
|
Disagree |
5% |
2 |
25 |
|
Strongly Disagree |
1% |
1 |
25 |
Table 2: Issues of data security affects the company
(Source: Created by self)
Q2. How far do you agree that following issues affect data security most?
|
Options |
Response Frequency |
No. of Respondents |
Total No. of Respondents |
|
Not secured network |
38% |
9 |
25 |
|
Using without VPN |
32% |
8 |
25 |
|
Using public computers |
24% |
6 |
25 |
|
Others |
6% |
2 |
25 |
Table 3: Issues affects data security by most
(Source: Created by self)
4.2 Qualitative Research
Interview questionnaire for the General Manager of an IT company
- What are the challenges of data confidentiality that are faced in IT industries companies?
|
“The challenges are faced that sometimes without knowing the proper process people access the system and there will be chances of many secured data getting public. Sometimes people breaches many protected information whether intentionally or unintentionally.” |
3.7 Research Contribution
This study developed within this data security assignment will generate the data, the software, the strategies, and the systems which are used by the multinational companies to keep the data secured in the field of Information Technology. This study will be used as an expected outcome for the value of confidential data. The study will discuss the reasons why the data in the IT companies are kept with security. The possible risks and challenges and the effects will be taken associated with security data issues in this research paper on data security assignment.
Proposed Time Schedule
|
Activities during research |
1st Week |
2nd Week |
3rd Week |
4th Week |
5th Week |
6th Week |
7th Week |
|
|
Selection of research topic |
ü |
|||||||
|
Composition of the literature review |
ü |
|||||||
|
Methodology followed in the research |
ü |
|||||||
|
Collection of primary data for the research |
ü |
ü |
||||||
|
Data analysis and interpretation |
ü |
ü |
||||||
|
Findings |
ü |
|||||||
|
Conclusion and Recommendation for the research study |
ü |
|||||||
|
Final submission of the research report |
ü |
|||||||
Table 1: Gantt chart
References
- Chandrashekhar, A. M., Revapgol, J., & Pattanashetti, V. (2016). Big Data Security Issues in Networking. International Journal of Scientific Research in Science, Engineering and Technology (IJSRSET), 2(1).
- Chatterjee, C., & Sokol, D. D. (2019). Data Security, Data Breaches, and Compliance. Data security assignment Cambridge Handbook on Compliance (D. Daniel Sokol & Benjamin van Rooij editors, Cambridge University Press, forthcoming).
- A. Cohen, "Cybersecurity for Critical Infrastructure: Addressing Threats and Vulnerabilities in Canada," 2019.
- Rosas, C. (2019). The Future is Femtech: Privacy and Data Security Issues Surrounding Femtech Applications. Hastings Bus. LJ, 15, 319.
- Samarati, P., di Vimercati, S. D. C., Murugesan, S., & Bojanova, I. (2016). Cloud security: Issues and concerns. Encyclopedia on cloud computing, 1-14.
- Singh, A., & Chatterjee, K. (2017). Cloud security issues and challenges: A survey. Journal of Network and Computer Applications, 79, 88-115.
- N. Khan and A. Al-Yasiri, “Identifying cloud security threats to strengthen cloud computing adoption framework,” Procedia Computer Science, vol. 94, pp. 485-490, 2016.
- N. Malik, “Distributed Computing and Security Issues in Cloud Computing,” Distributed Computing, 2019.
- M. Odeh, A. Garcia-Perez and K. Warwick, “Cloud computing adoption at higher education institutions in developing countries: a qualitative investigation of main enablers and barriers,” International Journal of Information and Education Technology, vol. 7, no. 12, pp. 921-927, 2017.
- S. D. Seifu, A. A. Dahiru, J. M. Bass and I. K. Allison, “Cloud?computing: Adoption issues for Ethiopian public and private enterprises,” Data security assignment The Electronic Journal of Information Systems in Developing Countries, vol. 78, no. 1, pp. 1-14, 2017.
- A. Singh, “Security concerns and countermeasures in cloud computing: a qualitative analysis,” International Journal of Information Technology, vol. 11, no. 4, pp. 683-690, 2019.
- Alguliyev, R., Imamverdiyev, Y., & Sukhostat, L. (2018). Cyber-physical systems and their security issues. Computers in Industry, 100, 212-223.
- Aljawarneh, S., & Yassein, M. (2016). A conceptual security framework for cloud computing issues. International Journal of Intelligent Information Technologies (IJIIT), 12(2), 12-24.
- Archibald, N. (2020). Cybersecurity and Critical Infrastructure: An Analysis of Securitization Theory. Undergraduate Journal of Politics, Policy and Society, 3(1), 39-54.
- Esposito, C., Castiglione, A., & Choo, K.-K. (2016). Challenges in delivering software in the cloud as microservices. IEEE Cloud Computing, 3(5), 10-14.
- Hurley, J. (2017). Data-Driven Approach to Protecting Critical Infrastructure. International Conference on Cyber Warfare and Security (p. 509). Academic Conferences International Limited.
- Hussein, N., & Khalid, A. (2016). A survey of Cloud Computing Security challenges and solutions. Data security assignment International Journal of Computer Science and Information Security, 14(1), 52.












