The Growing Impact Of AL And ML Cyber Security Assignment
Question
Task: This assignment is intended to support the development of a clear research thesis proposal through:
- An introduction to the research topic and problem context
- The presentation of a clear aim and set of objectives
- A concise literature survey highlighting the key themes for your proposed project in a thematic manner
- A detailed explanation, with justification, of your chosen methodology for your planned research study
- A summary of any ethical issues that you anticipate and how these will be addressed.
- Consideration of any risks involved with the chosen methodology, and how these will be managed.
- A detailed work plan for the proposed study including Milestones and related tasks.
Answer
1. Introduction
This research proposal on cyber security assignment is based on the impact of artificial intelligence and machine learning on cyber security. It is seen that in today’s world technologies are advancing at a rapid speed. Most of the issues are being solved by these technologies. Corporate is completely dependent on cyber security for the safety of their data. Cyber threats are also growing at a faster pace and hence the technology of cyber security is quite essential (Graham, Olson and Howard 2016). In this report, the problem will be identified first and then aim and objectives will be set. Further, a literature review will be done on the topic to gain basic knowledge. The research methodology explored in this cyber security assignment will be followed to understand the impact properly. Research ethics and expected outcomes will be mentioned in details.
2. Problem Statement
The main issue analysed in the cyber security assignment in this century is regarding the growing rate of cybercrimes all over the world. To handle the situation properly cybersecurity is needed. However, there are many sub-divisions under this section. However, the demand for artificial intelligence and machine learning is growing in the market. As stated by Agarwal (2019), currently, it is becoming difficult to understand which technology is better in cybersecurity. The growing impact is not being analysed properly. This is an issue because AI is a vast subject and ML is an application of AI. Each of these technologies is having some advantages. AI can handle the issue of biometrics and ML is having no human interventions and all the trends are identified easily. This is an issue now because none of the technologies can be ignored in the case of cybersecurity. ML can handle a large amount of data that are multi-dimensional in nature (Azvine and Jones 2019). It is also having wider applications. AI is having a low error rate. There is proper precision, accuracy and speed. All these are leading to positive impact and growth in cyber security.
Artificial Intelligence is related to artificial decision-making and it is equal to decision-making process of human beings. It is based on the certain mathematical calculations and unique algorithm process. AI role is ever increasing and the research related to the sue of AI in cyber security in modern world is very important, in addition, machine learning is very important towards pro-active action in preventing issues and responding towards cyber-attacks in real time. (Forbes.com 2020)
3. Aim and Objectives
The aim of this research on cyber security assignment is to understand the growing impacts of Machine Learning and Artificial Intelligence on Cyber Security.
Objectives
- To identify the need for cyber security in the daily lives of people
- To find the applications and supporting technologies for cyber security
- To know about the growing impact of AI and ML on cyber security
- To analyse the positive scope of cyber security tools and technologies in the market
The aim and objectives outlined in this report on cyber security assignment clearly show that cyber security is needed in the daily lives of people. This report will be analysing the growing impact of ML and AI on this technology. Further, the applications of cyber security need to be studied. There are some positive impacts of cyber security tools and technologies that can handle a large amount of data from hackers without any human interventions. These objectives will be helpful in achieving the purpose of the topic and understanding the views of people on cyber security.
4. Literature Review
Cybersecurity
The process which protects devices, programs, data and network from unauthorized access, damage and attack is known as cyber-security (Joinson and Steen 2018). This is also known as information technology security. This technology is quite important in various fields like financial, corporate, military and government. All the information is collected, processed and stored on computers or any other device. When sensitive information gets leaked then there is exposure to some negative consequences. Cyber security is mainly dedicated to protecting the system (Cavelty and Balzacq 2016). These days most of the businesses are using this technology for handling their management. Some of the common types of cyber threats mentioned in this segment of cyber security assignment for which this process is used are spyware, viruses and Trojan horses. Cyber Security provides in-depth testing of the information system and network.
Theory on cyber security discussed within this cyber security assignment
Computer security is handled by the Moving Target Defences (MTD). This is the game-changing approach. The MTD theory is defining a few concepts to show that the attacker is knowledgeable, has an idea about attack types and instances. However, the relation between MTD and cyber-attacks is not found in some cases. MTD is based on configurable system (Bardas et al. 2017). It can take the values of the adaptive system and hence the goals can be captured. There are three main problems of MTD are selecting the configuration for increasing effectiveness. The next one is adoptive. Just by the mission planning system, nothing is going to happen and the third one to allocating the resources. Further, the attackers are trying to destroy the vulnerability. More concrete code will attack and address the issue properly.
Figure 1: MTD Theory
(Source: Bardas et al. 2017)
Trends in cybersecurity
The proposed cyber security assignment analyses the study of Agarwal (2019) that the latest trends most of the corporate are moving from disruption transformation. In the coming years, the main target will be ransomware, mobile malware and phishing. The vital role of this technology is to protect people’s rights, privacy and physical safety. In today’s world, the role of Artificial Intelligence is increasing for both defence and cyber-attack. AI is having the ability to spot the coincidence pattern and behaviour that signals an attempted attack. It has both defensive and offensive capabilities. There are algorithms of deep learning security, systems of automation which are getting better for human errors and protection of biometric identity. The skills gap in cyber security is increasing each year. Some researches show that cyber-security jobs are unfilled. It is 3.5 million currently. This is a public concern in this decade. There are many frauds taking place and the cyber security teams are unable to handle the issues properly. There is a requirement of investment in this technology and its training. The trends show that data theft and vehicle hacking is increasing (Forbes.com 2020). Cars are having GPS devices, in-car communication and sensors which are quite profitable for hackers.
Issues of cyber security
There is a daily concern for cyber security in professional and personal lives. According to Pour, Anzalchi and Sarwat (2017), cyber security technology is the biggest threat to various economies in the world. It is becoming problematic to detect viruses each day. Some of the most common issues on cyber security are being discussed. Apart from economy Gupta, Agrawal and Yamaguchi (2016) feel that financial crimes are more important. The frequency of crimes is increasing. The main limelight is taken by Ransomeware from the past few years. The attacks from the supply chain and third-party are increasing. In the case of cloud computing, it is necessary to work with third-party vendors for services and software. The exploits of phishing and social engineering are quite common (Alguliyev, Imamverdiyev and Sukhostat 2018). But these crimes are becoming sophisticated. People are aware of suspicious messages and their danger. It is evident from the research utilized to prepare this cyber security assignment that hackers are mainly targeting machine learning and artificial intelligence. Sometimes there is a personal attack. The criminals are agents who are state-sponsored and the critical systems were attacked. There is the technological advancement of interconnectivity which is improving the working experiences of people. But there are risks to the networked devices which are connecting security systems, appliances and phones. There are problems with data integrity and security.
Impact of AI and ML
It is essential to understand about artificial intelligence and machine learning before their impacts are measured. Artificial intelligence is a part of machine intelligence that is demonstrated by machines when compared to the natural intelligence (Thomas, Vijayaraghavan and Emmanuel 2020). Machine learning is just an application of artificial intelligence that is providing the systems to automatically learn and improve their experiences without any kind of explicit programming. This main focus of ML is developing computer programs which can access data. Both ML and AL are the trends of cybersecurity currently. The present cyber security assignment examines the words of Wirth (2019) that the defence of the organization is dependent on artificial intelligence. It is because AI is having some advantages and disadvantages. Better biometric log in technique can be developed. However, there are some drawbacks in AI and for this ML can be used. AI is used as defenders and not as a single solution for all the problems. The overall expenses of the technology are increasing than the traditional method. More training is needed for cybersecurity maintenance.
5. Research Methodology
5.1 Research Philosophy
In a research philosophy mainly handles the sources and knowledge development. In this method, all the information is collected and analysed properly. There are four different types of philosophy Realism, Positivism, Pragmatism and Interpretivism.
Positivism Research Philosophy will be used by the researcher for this report. This means to hold some valuable knowledge. Through this method, the researcher will understand the aim and objectives in details. The methods of natural sciences will be used by the researcher to prepare this cyber security assignment through this method. It will be essential to find out the impact of AI and ML that is growing in cybersecurity. The main emphasis will be on empirical observations.
5.2 Research Approach
There are many assumptions in the plan of the research approach. The research problem will be addressed by the approach (Sekaran and Bougie 2016). Further, analysis and reasoning of data will be done. The two methods are Inductive and Deductive.
In the case of cyber security assignment, the deductive approach will be selected. This technique is on the basis of an existing approach. The hypothesis will be tested by the researcher by making a strategy firstly. The researcher will easily explain the relationship between AI and ML in cybersecurity. All the ideas will be measured quantitatively. All the research findings will be generalized in nature so that the researcher faces fewer complications. This approach will be useful for the researcher because a large amount of information can be gained. However, there will be limited time for completing the study. There will be fewer chances of risk in a deductive approach. The researcher should not opt for inductive approach while developing this cyber security assignment because limited resources will be available. There will be an ample amount of time for this method. But it will be of no use. There will be some risks and hardly any theory will emerge by inductive approach.
5.3 Research Design
There are various components that are usually integrated into the design. Then only overall strategy can be created by the researcher. The different components are used in a logical way so that they can effectively answer all the research problems (Quinlan et al. 2019). Firstly, all the information will be collected and then the measurement will be done. The approach is three different types Descriptive, Explanatory and Exploratory.
The researcher will be using Descriptive method in order to prepare this cyber security assignment. This is a scientific method and the researcher will be observing and then describing the subject behaviour. There will not be any influence in this method. The researcher will be observing the importance of cybersecurity and the usage of AI and ML. The survey will be done and analysed with the help of this technique.
5.4 Data Collection
All the information is collected from applicable sources so that the aim and objective of the research can be fulfilled and this is known as data collection process (Kumar 2019). The hypothesis gets tested and the outcomes are also evaluated through this method. Data collection is having Primary and Secondary methods. The researcher will make use of the primary one. It will simply mean that all the information will be collected and will be quantitative. The survey will be done by the researcher for this report. It will be essential for the researcher to understand the impact of AI and ML. This will be possible knowing the views of cybersecurity teams in various corporate in the United Kingdom. The survey questions will be closed-ended in nature. There will be 15 questions and the answers to all these will solve the researcher's problem. All the data will be calculated in mathematical form.
5.5 Sampling technique
The method of sampling is selecting members from a particular population for including in the study (Lohr 2019). It is difficult to select the whole population and work directly with them. Probability and non-probability are the two types of sampling. The researcher will be using the probability method. The main focus will be on simple random sampling method. This technique will be helpful in saving a large amount of money and accurate results will be gained. The speed of collecting information through the primary method will become fast. There will be an opportunity to process the available information inefficient way.
|
Sampling Population |
Sampling Size |
Sampling Technique |
Sampling Frame |
|
Cyber Security teams of corporates in the United Kingdom |
50 |
Simple Random Sampling Technique |
The questionnaire will be sent to the cybersecurity team through emails. |
5.6 Data Analysis
All the data is extracted from useful content through the process of data analysis. This also helps in the decision making process. Data analysis helps in finding answers to the research problem. This will also include the discussion of information gained. Quantitative and Qualitative are the two main ways. The researcher will be using Quantitative method for the answers that will be gained from the survey. All the mathematical information will be displayed through pie-charts, bar graphs and line charts. The proper calculation will be done so that desired results can be achieved.
6. Research Ethics
This research on cyber security assignment is associated with human participants. There will be certain guidelines which will be monitoring the researcher’s conduct so that high ethical standards will be maintained. The researcher must honestly report all the data, methods, results and procedures. There should be no such misinterpretation of data. Integrity should be maintained by the researcher. All the tasks must be done sincerely. There should be consistency in the work. The researcher must avoid any kind of errors. All the data must be examined carefully. The record for each of the activities must be maintained properly. There should be openness for shared data, tools, results and resources. Biasness must not be done during experimental designs, analysis of data and decision-making. Proper confidentiality must be maintained for the research. The data must be shared with anyone outside the university. There should not be any social harm during the research. Welfare must be promoted so that proper decisions can be made. All the laws of the institution must be followed along with the government ones. The research carried on the cyber security assignment can improve personal competence by learning and education. There should not be any discrimination against any students.
7. Risks involved and how these can be managed
There will be some risks related to the primary data collection method. The research procedures might bring some physical discomfort, injury, illness and pain. There will be some chances that the researcher might lose confidentiality. Social and economic risks will also be visible. The subject might get altered and the wrong set of information will be gained. This will be wasting a large amount of time. However, the risks can be managed by the researcher. It will be essential to cross-check all the information before conducting the survey. Proper confidentiality must be maintained by mitigating the risk. Further, any other risk must be avoided.
8. Work plan
|
Activities |
Start-Date |
End-Date |
|
Research about the information |
1st February 2020 |
7th February 2020 |
|
Planning as per gathered data |
8th February 2020 |
14th February 2020 |
|
Literature Review |
15th February 2020 |
21st February 2020 |
|
Research Methodology |
22nd February 2020 |
28th February 2020 |
|
Data Collection |
1st March 2020 |
7th March 2020 |
|
Identification of the findings |
8th March 2020 |
14th March 2020 |
|
Interpretation and Discussion |
8th March 2020 |
14th March 2020 |
|
Outcomes |
15th March 2020 |
21st March 2020 |
|
Closing the project |
15th March 2020 |
21st March 2020 |
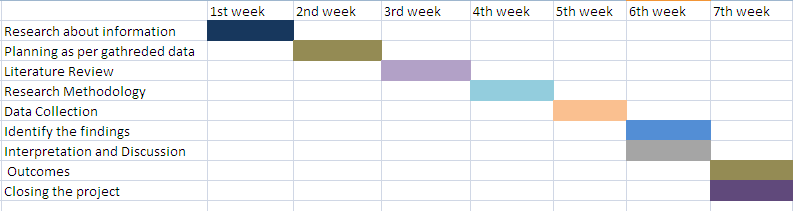
Figure 2: Gantt chart
(Source: Self-Developed)
9. Conclusions
From this research proposal on cyber security assignment, it is expected that the impact of artificial intelligence and machine learning will be gained for cybersecurity. There are some chances that cybercrimes can be managed well by these two technologies. The views of the cybersecurity team will be a guiding path for future research on this topic. The survey results will be indicating positivity about AI and ML. It will show whether cyber security is having in-depth knowledge of the current changes that are taking place in case of technology. As the research will be done in a systematic manner hence, a proper set of mathematical answers will be gained from the analysis on cyber security assignment.
Reference List
Agarwal, N., 2019. Cyber Security Trends to watch out in 2019. Cyber security assignment CYBERNOMICS, 1(1), pp.28-29.
Alguliyev, R., Imamverdiyev, Y. and Sukhostat, L., 2018. Cyber-physical systems and their security issues. Computers in Industry, 100, pp.212-223.
Azvine, B. and Jones, A., 2019. Meeting the Future Challenges in Cyber Security. In Industry 4.0 and Engineering for a Sustainable Future (pp. 137-152). Springer, Cham.
Bardas, A.G., Sundaramurthy, S.C., Ou, X. and DeLoach, S.A., 2017, September. MTD CBITS: Moving target defense for cloud-based IT systems. In European Symposium on Research in Computer Security (pp. 167-186). Springer, Cham.
Cavelty, M.D. and Balzacq, T. eds., 2016. Routledge handbook of security studies. Cyber security assignment Routledge.
Forbes.com. 2020. Cyber security trends. Available at: https://www.forbes.com/sites/bernardmarr/2020/01/10/the-5-biggest-cybersecurity-trends-in-2020-everyone-should-know-about/#471e7fc37ecc [Accessed on 14th January 2020]
Graham, J., Olson, R. and Howard, R., 2016. Cyber security essentials. Auerbach Publications.
Gupta, B., Agrawal, D.P. and Yamaguchi, S. eds., 2016. Handbook of research on modern cryptographic solutions for computer and cyber security. IGI global.
Joinson, A. and Steen, T.V., 2018. Human aspects of cyber security: Behaviour or culture change?. Cyber Security: A Peer-Reviewed Journal, 1(4), pp.351-360.
Kumar, R., 2019. Research methodology: A step-by-step guide for beginners. Sage Publications Limited.
Lohr, S.L., 2019. Sampling: Design and Analysis: Design and Analysis. Cyber security assignment Chapman and Hall/CRC.
Pour, M.M., Anzalchi, A. and Sarwat, A., 2017, March. A review on cyber security issues and mitigation methods in smart grid systems. In SoutheastCon 2017 (pp. 1-4). IEEE.
Quinlan, C., Babin, B., Carr, J. and Griffin, M., 2019. Business research methods. Cyber security assignment South Western Cengage.
Sekaran, U. and Bougie, R., 2016. Research methods for business: A skill building approach. John Wiley & Sons.
Thomas, T., Vijayaraghavan, A.P. and Emmanuel, S., 2020. Machine Learning and Cybersecurity. In Machine Learning Approaches in Cyber Security Analytics (pp. 37-47). Springer, Singapore.
Wirth, A., 2019. Cyberinsights: Artificial Intelligence: Friend and Foe. Biomedical instrumentation & technology, cyber security assignment 53(5), pp.378-383.












