Information Security Assignment: Safety Analysis Of Auto Body Supplies
Question
Task: Prepare a report on information security assignment developing security analysis of existing security status of Auto Body Supplies (ABS).
Answer
Introduction
According to the research on information security assignment, the concept of information security is one of the most critical aspects of the business organizations in the present times. This is because of the varied security risks and attacks that are now possible with the increased use of technology. The information security assignment selected Auto Body Supplies (ABS) and provides the organization with the recommendations on the security enhancement. ABS is still using TrueCrypt which is a major security issues for the business.
The security analysis of the existing security status and the recommendation on the alternative security product is done in the information security assignment.
Threats & Vulnerabilities with TrueCrypt
There are several security threats and vulnerabilities examined in the context of information security assignment that are associated with TrueCrypt. All of these will get associated with ABS as well as it still relies on TrueCrypt for the purpose of security. TrueCrypt has several threats and vulnerabilities that are also present in other encryption software, such as BitLocker. It is essential for ABS to make changes in the security architecture and patterns. The encryption keys that are involved in the security process are stored in RAM in the case of TrueCrypt (Broz & Matyas, 2015). In the case of a regular personal computer, the DRAM will keep these records intact for a few seconds once the power is cut-off. Even in the case of degradation in the memory contents, it will be possible to recover the keys with the application of some of the specific algorithms. This entire process is referred as the cold boot attack. This attack mentioned in the information security assignment usually occurs on a notebook computer when the system is switched on or is suspended or in the screen-lock mode. The use of this attack mode has been done in the past to carry out the TrueCrypt attack.
There are also physical security issues identified in the present study of information security assignment that are associated with the TrueCrypt attack. The documentation that has been prepared for this product states that the product will not be able to safeguard the data if the malicious entity accesses the system physically and TrueCrypt is used again on the compromised system. If the attacker gains physical access to the user’s machine then there are a variety of actions that may be performed. For instance, the installation of hardware or software key-logger may be done (M. & Ying, 2016). The attacker may also install the other malicious components on the system which may give the attacker with the ability to capture the unencrypted data. The attacker will also gain access to the encryption keys. Physical security is one of the basic security aspects and it is not assured with TrueCrypt. The associated security attacks are referred as the evil maid attacks.
The discussion on malware attacks provided in this section of information security assignment are common and these attacks may also occur on TrueCrypt. The product is not efficient enough to provide security to the system if there is any form of malware installed in the system. The malware may be designed to log keystrokes and the passwords/keys may be exposed to the attackers. There was also an independent security audit of the product done in 2015 that revealed the two major vulnerabilities associated with the product. One of these vulnerabilities is in the Windows installation driver that provides the attacker with the ability to carry out arbitrary code execution. Also, privilege escalation is made possible through DLL hijacking (Constantin, 2015).
Another major vulnerability that has been identified in the study of information security assignment with TrueCrypt is the stoned boot-kit. It is MBR rootkit which has been presented in one of the security conferences in USA and it can tamper the TrueCrypt’s MBR. The full volume encryption that comes along with the product can be bypassed as an outcome. There are numerous other hard-disk encryption software packages that can get impacted with such an attack (Bin et al., 2015).
There are two types of attack possibilities noted in this information security assignment that may be present with the boot-kit attack. The first scenario is wherein the user must launch the boot-kit at the time of system start-up and the administrative privileges must be present as well. The second scenario is the required of the physical access to the TrueCrypt-encrypted hard-disk of the user’s machine. The second scenario is applicable in the case of TrueCrypt wherein the hard-disk will be infected with the boot-kit and it will then be kept again in the PC without the knowledge of the user. The occurrence of any of the two scenarios can violate the overall security of the user as the information present in the hard disk will be exposed.
As per the research conducted on this information security assignment, there are also certain security concerns associated with the Trusted Platform Module (TPM) present in the TrueCrypt. This is because if the malicious entity gains physical access to the system and the user accesses the system thereafter, there are chances that the modifications may have been done by the attacker. There may be changes in the hardware keystroke logger that may have been done or other modifications that may allow the attacker to capture the information from the user’s system (Rosenzweig, 2016).
VeraCrypt – Alternative Open Source Product
There are numerous security issues outlined in the context of information security assignment that have been identified with TrueCrypt. All of those security issues and vulnerabilities are resolved by an alternative open source product called VeraCrypt. The product is used for on-the-fly (OTF) encryption. The product can be used for the creation of virtual encrypted disk present within a file or for the encryption of the partition. It can also be used for the encryption of the complete storage device present within the pre-boot authentication (Veracrypt, 2019).
VeraCrypt is an upgrade of the TrueCrypt product and was release in 2013. The latest release of the product came in 2019. There have been several security updates that have been done in VeraCrypt since its release and there are a number of code audit issues that have been treated since then. The product makes use of a number of cryptographic hash functions along with the ciphers for the improvement of the overall performance. The development team associated with the project analysed the security vulnerabilities associated with TrueCrypt and developed a new format which may be incompatible with the one present in TrueCrypt (Tweakers, 2020).
TrueCrypt involves around 1,000 iterations of the algorithm involved in the partitioning of the systems which is 200,000 or 327,661 iterations by default in the case of VeraCrypt. It can also be customized as per the requirement. The product also involves 655,331 iteration of the RIPEMD160 by default or 500,000 iteration of the SHA-2 which can be customized as well. The default settings that are associated with VeraCrypt make it slower at opening the encrypted partitions. Also, the password-guessing attacks become slower with the involvement of these iterations. There is also a new feature that has been added in VeraCrypt called the Personal Iterations Multiplier (PIM). The value of PIM parameter is utilized in controlling the total number of iterations involved in the header key derivation function (Brinkmann, 2018). This makes the occurrence of the security attacks, such as Brute-Force attacks difficult to carry out. The product uses the PIM value for the enhancement of the overall security and it may be altered by the users. The opening of encrypted archives becomes slower with this feature.
VeraCrypt supports the Unicode passwords on all of the operating systems apart for the encryption on the Windows OS. There are also securities vulnerabilities present in the bootloader that have been fixed. The security issues present in ShellExecute were also fixed by the developers in VeraCrypt. The system partitions are carried out using UEFI and there is also an added capability to enable or disable the support for the TRIM command. This includes the system as well as the non-system drives (Brinkmann, 2019). In VeraCrypt, the system encryption keys are removed from RAM at the time of shutdown. This helps in the prevention of the cold boot attacks. There was also an update launched to provide RAM encryption for the passwords and keys in the 64-bit systems.
In the usual process, the encryption keys that are involved in the security process are stored in RAM. In the case of a regular personal computer, the DRAM will keep these records intact for a few seconds once the power is cut-off. Even in the case of degradation in the memory contents, it will be possible to recover the keys with the application of some of the specific algorithms. This entire process is referred as the cold boot attack. This attack usually occurs on a notebook computer when the system is switched on or is suspended or in the screen-lock mode. This mode of security attack was used to attach the TrueCrypt versions. VeraCrypt provides the option to encrypt the in-RAM keys along with the passwords present within. This leads to the prevention of the security issues.
VeraCrypt also provides protection from the malware attacks and issues which are common in the case of the TrueCrypt product. All of these features that are present in VeraCrypt make it a viable choice for ABS as an alternative product in the place of TrueCrypt. VeraCrypt is a secure upgrade of TrueCrypt and most of the securities issues present in TrueCrypt are not there in VeraCrypt. As a result, ABS must make use of VeraCrypt in the place of TrueCrypt so that it succeeds in achieving the aim of promoting the overall security (Yang, 2016).
What is the functioning of VeraCrypt Test Plan in the context of information security assignment? Explain.
The test plan used below within this information security assignment will prove whether VeraCrypt is a viable alternative for ABS to TrueCrypt in securing their information. The software evaluation plan provided in the report of information security assignment will pass through a series of stringent question and analysis detailed below.
- Use of encryption algorithms: A good encryption software should make use of multiple encryption techniques that at least 128-bit and upwards.
- Use of Hashing Algorithms: A good encryption software should make use a good Hashing technique which is at least 128-bit and upwards.
- Does the Application recommends using a complex password?
- Does the Application reject insecure password?
- Does the Application offer password generation?
- Does the Application offer Key File unlock?
- Does the Application offer multiple Password options to set an even more secure password?
- Does the Application make use of any form of Password encryption?
The result:
VeraCrypt makes use of 256-bit and upwards of encryption and hashing algorithms as evident from the below images
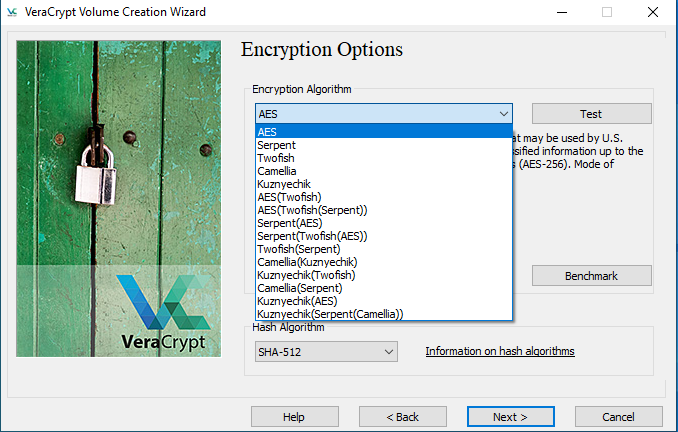
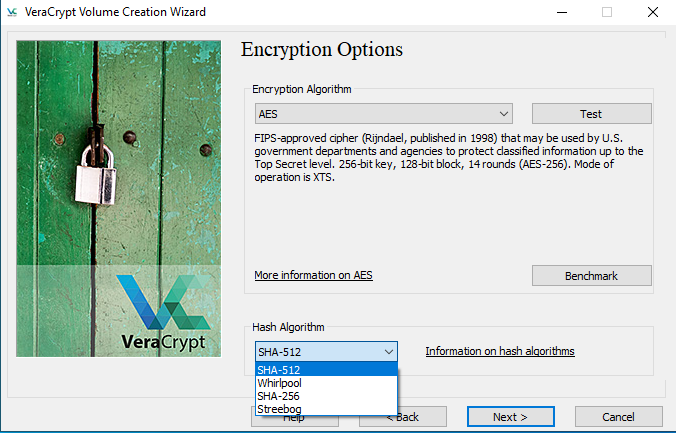
Veracrypt recommends using a complex password and also rejects an insecure password.
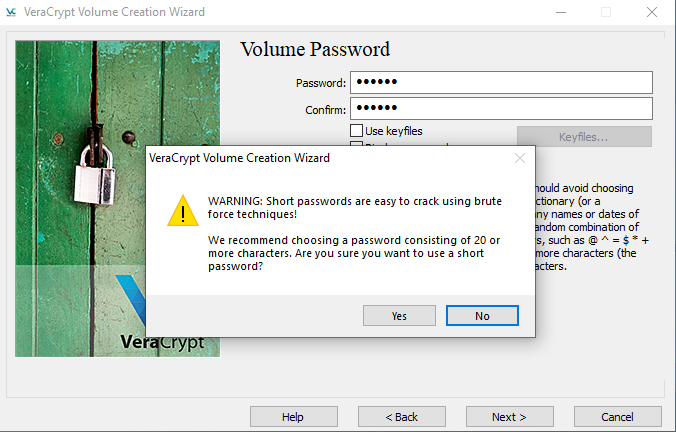
Additionally, it is also stated in this information security assignment that it adds random header data to the file, making it more difficult to break.
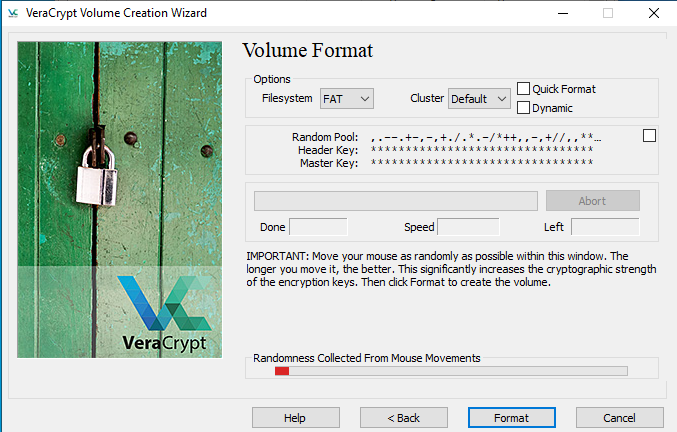
Also, Veracrypt offers Keyfile based encryption which allows a person to use a file as a password which is the most secure way to protect the container.
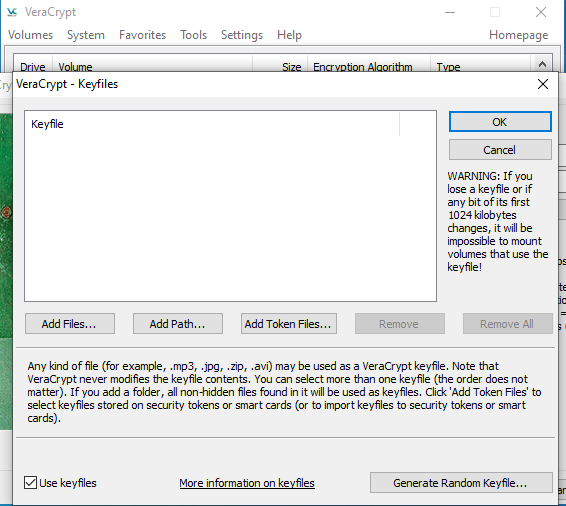
Analysis of VeraCrypt
|
Password Encryption |
Yes |
|
Password Length and Complexity |
Yes |
|
Protection Mechanism |
Asymmetric and Asymmetric |
|
Random Header Data on Password |
Yes |
|
Password Generation |
Yes |
|
Use of Key File to lock data |
Yes |
|
128-Bit+ Encryption |
Yes |
|
Bruteforce Susceptible |
Yes (Using tools such as Kali Tools and Accessdata) |
Conclusion
Considering the overall discussion on this information security assignment, it can be stated that security is one of the key aspects for every business firm and so is the case for ABS. It currently uses TrueCrypt as the security encryption product for hard-disk encryption. There are too many security issues and vulnerabilities that are present in TrueCrypt. These security issues identified in the above sections of information security assignment will automatically get associated with ABS if it continues to use TrueCrypt in its architecture. On the other hand, VeraCrypt offers upgraded security and also makes sure that all of the security concerns associated with TrueCrypt are avoided. The inclusion of VeraCrypt shall be done as the major tool to make sure that the security of ABS is improved and the updates in the overall security are done.
References
Bin, W., Jiang, C. R., & Li, J. (2015). The Research of Hard Disk Encryption System Based on Advanced Encryption Standard Algorithm. Applied Mechanics and Materials, 299, 172–175. https://doi.org/10.4028/www.scientific.net/amm.299.172
Brinkmann, M. (2018). How to change the PIM of a VeraCrypt volume - gHacks Tech News. Www.Ghacks.Net. https://www.ghacks.net/2018/11/26/how-to-change-the-pim-of-a-veracrypt-volume/
Brinkmann, M. (2019). VeraCrypt 1.24 features massive improvements - gHacks Tech News. Www.Ghacks.Net. https://www.ghacks.net/2019/03/04/veracrypt-1-24-features-massive-improvements/
Broz, M., & Matyas, V. (2015). The TrueCrypt On-Disk Format--An Independent View. IEEE Security & Privacy, 12(3), 74–77. Information security assignment https://doi.org/10.1109/msp.2014.60
Constantin, L. (2015, September 29). Newly found TrueCrypt flaw allows full system compromise. PCWorld. https://www.pcworld.com/article/2987439/newly-found-truecrypt-flaw-allows-full-system-compromise.html
M., A., & Ying, S. (2016). Privacy Impacts of Data Encryption on the Efficiency of Digital Forensics Technology. International Journal of Advanced Computer Science and Applications, 4(5). https://doi.org/10.14569/ijacsa.2013.040506
Rosenzweig, P. (2016, June 18). The Strange Demise of TrueCrypt and What It Says About Cybersecurity. Lawfare. https://www.lawfare.com/strange-demise-truecrypt-and-what-it-says-about-cybersecurity
Tweakers. (2020). VeraCrypt 1.24-Update6. Tweakers. https://tweakers.net/downloads/51046/veracrypt-124.html
Veracrypt. (2019). VeraCrypt - Free Open source disk encryption with strong security for the Paranoid. Veracrypt.Fr. https://www.veracrypt.fr/en/Home.html
Yang, H. (2016). Research on Design Method Based on Hardware Encryption and Two-way ID Authentication for Security Mobile Hard Disk. Information security assignment TELKOMNIKA Indonesian Journal of Electrical Engineering, 12(4). https://doi.org/10.11591/telkomnika.v12i4.4995












