Information Security Management Assignment: Case Analysis Of Secure Aussie Bank
Question
Task:
You are required to analyse the scenario of Secure Aussie Bank write a report on:
a) Guidelines for information security risk management for the given organisation. Your discussion should include the following:
- Identifying and prioritising risk factors for information assets in the given scenario
- The risk management framework(s), strategy and process that could be adopted to discover, assess, treat and manage the InfoSec risks for the organisation.
- Strategy of risk acceptance and risk mitigation plan that could be adopted by the organisation.
b) Guidelines for information security certification and accreditation
Answer
Executive Summary
The concept of information security management focused in the present context of information security management assignment represents a group of procedures, policies and strategies which helps to identify and address the technology-related threats and opportunities revolving around information assets. This assignment focuses on the given case scenario to provide recommendations for information security management. The study has analysed the risks associated with the operations currently being carried out by Secure Aussie Bank. Risk priority has been evaluated based on the qualitative method based on its likelihood to occur and the probable monetary losses. This assignment describes how the Secure Aussie Bank will apply the principles of risk management for protecting information security. This will help to develop an information security program for Secure Aussie Bank. The strategies to accept the information security risk and mitigate risks which bring financial loss and reputational damage are described in this assignment. It will help the company control and manage the chances of unfortunate events by implementing the strategies. Further, this information security management assignment helps to understand information security accreditation and certification to an organisation.
Introduction
Information security management represents controls which the company should implement to confirm that they are able to protect the integrity, confidentiality, and availability of information assets from vulnerabilities and threats sensibly. The advanced information technology increase business opportunities over the Internet. Despite these opportunities, the information technology has brought various risks with respect to information security. With the growing security demands, the organisation needs to identify the management roles as well as activities in the data security management in order to understand the data security issues (Soomro, Shah and Ahmed 2016, p. 215). The purpose of this information security management assignment is to understand how to apply the information security management's principle by reviewing existing journal articles and website articles systematically. This assignment helps to explore as well as prioritise the risk factors for the organisation's information assets. Risk management strategy, process and frameworks will be discussed in this assignment which can be adopted to explore, treat, assess and control the information security risks for the Secure Aussie Bank. Strategy for risk mitigation and risk acceptance plan will be described in this information security management assignment. Further, this assignment will provide guidelines for information security accreditation and certification of the Secure Aussie Bank.
a) Guidelines for information security management
Identifying and prioritising risk factors for information assets
Information security risks are the probability of a given threat exploiting the vulnerabilities of one or more assets causing financial losses to the concerned organisation. Currently the Secure Aussies Bank is working on providing online banking service to customers and process loan applications. Some of the operations of the bank are under high risk conducive to theft of confidential data, theft of identity and crude attacks from hackers accessing the funds of the bank. There are some grave risks to the system which need to be explored and their priority assessed.
Risks from individual devices
Secure Aussie Bank has implemented the concept of BYOD for certain sections of its operations. However, the company has not defined any proper policy which can be detrimental for the system. There can be staffs within the company now aware of the cautionary actions necessary to prevent data leaks (Techadvisory.org 2020). Hence confidential data of the company can be accessed from outside and manipulated as per the needs of the attacker. Encryption and strong Mobile Device Management can prevent the outcomes of such unanticipated events. Thereafter unknowingly a specific staffs of the company can download content for recreation. Malicious elements in such content can increase the risks associated with the system leading to confidential data of SAB being accessed.
Risks in internal controls
It can be seen in the given scenario of information security management assignment that Secure Aussie Bank is allowing lending managers to access the financial profile of customers. While it is facilitating the lending process there are risks associated with lending managers receiving access to confidential customer data. Information from financial profiles can be used to access the bank accounts of customers. Further in Secure Aussie Bank marketing managers are receiving access to the customer data and activity history in order to promote new services and products within the bank. The bank has not implemented any methods to protect the crucial data of customers which can lead to intense data breaches in the market. 50,000 customer data once leaked will become accessible to hackers allowing them to smear the reputation of the bank.
Diminished security in clouds
SAB has stored the data of 50,000 customers in Cloud. Product and customer information has been stored in clouds. There are no levels of authority defined for accessing the data on cloud. IT personnel regularly access the data which increases its vulnerability making its susceptible to identity theft. Identity of a person can be used to execute malicious activities within the network. Key pieces of personal identification can be used to impersonate a person and establish new identity (Techtarget 2020.com).
Prioritisation
Qualitative methods have been used asses the risks based on non-numeric categories including low moderate or high. The current risks identified in the present context of information security management assignment are being categorised based on qualitative methods to reach succinct conclusions.
|
Risks |
Monetary Loss |
Risk Likelihood |
|
Risks from individual devices
|
High ranging from 300k to 1 million AUD |
Almost sure to occur |
|
Risks in internal controls
|
Medium ranging from 50k to 300k AUD |
An even chance to occur |
|
Diminished security in clouds
|
Very High above 1 million AUD |
Almost sure to occur |
From the analysis it can be derived that the last risk of lack of authority and access definition in clouds has the highest risk in Secure Aussie Bank. In today’s world, the contemporary organisations are prone to attack by the cyber criminals which will affect their businesses. The valuable information resources can be protected by prioritising security risks.
Risk management frameworks, strategy and process
Risk management framework refers to a structured and disciplined process which helps an organisation to discover possible threats to the business. It also defines a strategy which can minimise or eliminate these risks' impact. According to Joshi and Singh (2017, p.129), the National Institute Standard and technology has developed the Risk Management Framework which covers a set of activities associated with controlling organisational risk. It is also known as RMF. The Secure Aussie Bank company can use the six-step RMF to protect the financial profile of customers and other information. In the RMF, the information system will be categorised by the potential impact of the information on the company. After categorising the information, the Secure Aussie Bank company needs to select the security control systems on the basis of the potential risk' nature in order to protect all valuable information resources. It helps the company to assess the challenges, develop actions, as well as evaluate the plan's outcomes. As stated by Peltier (2016), information protection needs an integrated and comprehensive approach which is generally cost-effective. The information security helps the organisation to protect its valuable information assets as well as meet the objectives of the business.
The SAB organisation has some critical assets including hardware, information technology, software, facilities, environmental, network, technology, services, complex processes as well as people. These assets are all inter-related and support the entire business. Based on Kure and Islam (2019, p. 335), a risk management framework also helps to identify the vulnerabilities of the asset or the system as well as determine the potential threats’ consequences. Security controls need to be selected on the basis of actual risks to the operations and assets of the organisation. The company should apply the security controls as well as maintain a document to record the way the security controls are applied in respect of basic risk management technique and information system. The company should assess all security controls by using concrete measuring systems in order to determine the effectiveness and performance against the given objectives. With the help of the RMF, the company will able to authorise operations on the basis of the data captured, objectives and lastly the level of risk which the company can assume. In the risk management framework, security control monitoring is considered to be essential to understand its effectiveness in respect of changing risks, issues and potential improvements. With the help of these risk management frameworks, the organisation can able to discover, assess, manage and treat the data security risks.
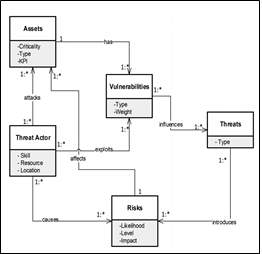
Figure 1: Metamodel
[Source: Kure and Islam 2019]
Considering the scenario explored in the information security management assignment, it can be stated that SAB should identify the potential threats and vulnerabilities by using the Figure model. Assets criticality, type and KPI help to determine the degree of risk (Evans 2016). The company should calculate the assets criticality, KPI and type, vulnerabilities weight and type as well as risks likelihood, level and impact by using the metamodel. Every organisation should consider 5 key components while selecting an RMF. The key components are risk identification, risk mitigation, risk governance, risk measurement as well as assessment and lastly risk monitoring and reporting. These components help to assess the security risk and to develop risk management strategies. The Secure Aussie Bank can adopt various strategies for managing security risks. Risk sharing may help to redistribute the risk over different parties to reduce the burden. On the other hand, avoidance helps to eliminate the security risks by isolating the cause. The company can also use risk mitigation and risk acceptance strategy for securing information assets. They also can use ISO 31000 for managing risk throughout the business activities. ISO 31000 helps the organisation to maximise the chances of accomplishing objectives, use valuable resources for risk management as well as enhance the threat and opportunity identification effectively (Iso.org 2020). ISO 31000 helps to maintain professional reputation, safety and environmental outcomes as well as economic resilience.
Risk management is considered to be an evolving and ongoing process which helps to assess the risks and discover and implement countermeasure. The cloud network of the Secure Aussie Bank is continuously modified and expanded, the components changed, as well as software application updated or replaced with the current version. According to Wangen, Hallstensen and Snekkenes (2018), the changes in the network environment of the organisation make it vulnerable to phishing, malware and ransomware attack. Therefore, the company should adopt the risk management process which will identify the assets, discover possible threats on the basis of the asset explore and assess vulnerabilities, measure frequency as well as identified vulnerabilities' impact. The risk management process should measure security risk in network environment, find and implement countermeasure when asset can be on risk, and report the whole process. Thus, the company will able to manage the security risks.
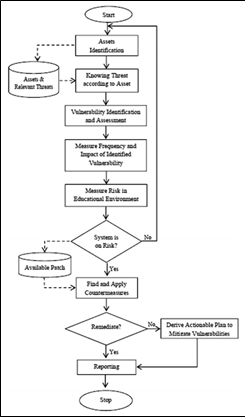
Figure 2: Risk assessment process for quantitative data security
[Source: Joshi and Singh 2017]
Strategy of risk acceptance and risk mitigation plan
With the evolving information technology, information has become a valuable asset which makes the security a business objective. According to Atlantic.net (2020), the range of potential mitigation activities is vast which thwart cyber criminals as well as decrease the information breach risk. Risk mitigation strategy helps to reduce the likelihood of occurrence of the risk. It also can minimise the risk’s impact within the acceptable limits. The Secure Aussie Bank should develop strategies to reduce the security exploits and data breaches. The company needs to update the software regularly. It will confirm that the operating systems and IT software contain latest operational and security patches from vendors. The vendors such as Microsoft introduces monthly updates that need to be applied immediately to avoid exposure to security risks as these updates carry patches which resolve the current known vulnerabilities and exploits. The organisation should also develop risk acceptance strategy to acknowledge the risk’s impact and possible consequences. Risk acceptance means that the company is ready to accept risk’s level related to a given process or activity (Pearsonitcertification.com 2020). The Secure Aussie Bank should accept its identified security risks and not making any plans to minimise the risk.
Figure 3: Risk treatment plan
[Source: Rubino 2018]
Data security risk management process helps to identify, treat, review as well as monitor the risks continuously in order to accomplish risk acceptance. Risk acceptance contains small and infrequent risks which are unable to become a catastrophic. These risks do not bring any big loss to the business; hence the organisations generally decide to not spending money and time to prevent the risks. Self-insurance is considered to be a risk acceptance decision. All and any risks which are not avoided or transferred are generally retained. The Secure Aussie Bank should identify and accept those risks and manage, avoid or mitigate other risks. The company should focus on mitigation activities to protect information assets. According to Rubino (2018), governance system, management system, software or application control, device control techniques, communication controls, and lastly data controls helps to mitigate the security risks. The Secure Aussie Bank should develop and apply governance system and device, information, application and expense management framework to protect the integrity, confidentiality and availability of information assets. The information security department of the company should provide training to all the staff of the company.
Security training should be conducted for all employees to educate them in securing information and protecting the system. The organisation can use risk prioritisation technique to discover and prioritise security risks such as FTA, FMEA and so on. Minimising the chances of occurrence and the consequence’s severity helps the organisation to save financial damage as well as reputational damage. As stated by Rose and Kass (2017), to prevent security risks, the organisation can use anti-virus protection application in every device and system in order to avoid virus spreading to the system. They should empathise on using of physical security, authentication, remote lock, remote wipe, configuration controls, and device activity logging and monitoring. Every system and device in the company should have browser security and password requirements; hence it will minimise the event of cyberattacks.
The security risk can be mitigated by enabling auto-lock and disabling auto-complete. The wireless and network-connected products should be used and managed by authorised users. On the other hand, the company can use virtual encrypted private network. The device backup is the most effective strategy which helps to protect critical information (Greene 2020). The Secure Aussie Bank should engage business stakeholders in order to prioritise cyber threats. Threat should be categorised according to known scenarios and events. The company should secure the infrastructure by monitoring system performance, network traffic as well as user behaviour. Thus, the company may able to mitigate the risks.
b) What are the guidelines for information security certification and accreditation basis the case scenario of information security management assignment?
The information security accreditation and certification is considered to be a process which helps to implement a formal process that ensures the information system's security. It is a two-step systematic procedure for evaluating testing; describing and authorisation activities and systems before or after the infrastructure are in the operation. The Secure Aussie Bank should develop organisation-level activities which may promote cost effective accreditation and certification processes. With the help of information security accreditation and certification, the responsible personnel are able to assess the risk as well as security requirements and baselines (Mile2.com 2020). Security accreditation refers to the management and acceptance of security risks such as risk to organisation operations, individuals which results from an information system's operation and organisation assets. Authorising officials in Secure Aussie Bank should determine the security risk to assets, operations and individuals. Security accreditation activities are a part of the ongoing, dynamic risk management procedure. On the other hand, security certification may not consider the risk's determination to organisation operation, individuals or organisation assets. The Secure Aussie Bank can use various types of assessment techniques for security certification such as inspecting, analysing, interviewing, testing, studying and demonstrating and so on.
The Security accreditation and certification process contain four steps which are initiation stage, security certification stage, security accreditation stage and lastly continuous monitoring stage. The Secure Aussie Bank should be prepared, identify resources, analyse the system security strategy, acknowledge and update in the initiation phase. The company should assess security controls and document security certification in the security certification stage. Security certification supports the security accreditation directly by offering to authorise personnel with essential data necessary to take risk-based, credible decisions. According to Safa, Von Solms and Furnel (2016), an organisation may not able to safeguard the valuable information resources due to the deficiency of information security knowledge or awareness. The Secure Aussie Bank needs to emphasise on sharing and reuse of security control design, enforcement, and assessment-related data while developing strategies for protecting information assets. The Chief Information Officer in the Secure Aussie Bank should design and maintain data security policies, control techniques and procedures in order to address the applicable requirements. The company should oversee and provide training to personnel who have certain duties related to information security. The Secure Aussie Bank should consider the overall information system's inventory when designing appropriate programs for managing organisation-wide risks.
The Chief Information Officer should security make security accreditation in the security accreditation stage. In the last stage, the company should configure management, monitor security control as well as document the status in the report. The security accreditation and certification is flexible process which allows the organisation to achieve the particular tasks effectively in the organisation. This process is applied extensively around the world. The Chief Information Officer needs to encourage sharing and reuse of security associated with data such as vulnerability and threat assessments, internal control assessment results and risk assessment. The Secure Aussie Bank should set up boundaries for complex and large information system. The decisions related to security accreditation from security accreditation and certification processes must be transferred to the owners of the information system. In the security accreditation document, the Secure Aussie Bank should provide system security strategy, security assessment written report as well as action plan and milestones. The company needs to monitor the security controls in the security accreditation and certification process. This will help the Secure Aussie Bank to protect their information assets.
Conclusion
Information security management defines a process which helps to mitigate as well as manage the various vulnerabilities and threats to information assets. The Secure Aussie Bank is a well-known Australian bank which offers financial, investment and banking services. Therefore, the employees need to handle the client’s financial profile and other sensitive information which are valuable assets to the company. This information security management assignment identifies as well as prioritises the risk factors for the Secure Aussie Bank Company’s information assets. The risks may come from individual devices, internal controls, and lastly diminished security in clouds. Risk management process, strategy, and framework which should be adopted to explore, treat, assess and control the information security risks for the Secure Aussie Bank company describes in this assignment. The RMF model is the most suitable which provides a procedure and an action plan to the company to protect the valuable information resources. Strategy for risk mitigation and risk acceptance plan describes in this assignment. The information security management assignment also suggests guidelines for information security accreditation and certification of the Secure Aussie Bank company.
Reference List
Evans, L., 2016. Protecting information assets using ISO/IEC security standards. Information Management, 50(6), p.28. [Available at: http://search.proquest.com/openview/cdc7591e255f2f26cec120736c3fda55/1?pq-origsite=gscholar&cbl=47365]
Greene, S., 2020. Information Security Risk | Security Program And Policies: Governance And Risk Management | Pearson IT Certification. [online] Pearsonitcertification.com. information security management assignment Available at:
ISO. 2020. ISO 31000 — Risk Management. [online] Available at:
Joshi, C. and Singh, U.K., 2017. Information security risks management framework–A step towards mitigating security risks in university network. Journal of Information Security and Applications, 35, pp.128-137. [Available at: https://www.sciencedirect.com/science/article/pii/S2214212616301806]
Kure, H.I. and Islam, S., 2019. Assets focus risk management framework for critical infrastructure cybersecurity risk management. IET Cyber-Physical Systems: Theory & Applications, 4(4), pp.332-340. [Available at: https://ieeexplore.ieee.org/abstract/document/8953050/]
Mile2 Cybersecurity Certifications. 2020. IS Certification & Accreditation - Mile2 Cybersecurity Certifications. [online] Available at:
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for effective information security management. CRC Press. [Available at: https://books.google.com/books?hl=en&lr=&id=mM_LsS-W4f4C&oi=fnd&pg=PP1&dq=information+security+management&ots=WhPXpZiyig&sig=Cuymn-YvAulmyL58JIuGEa9Pecg]
Rose, R.V. and Kass, J.S., 2017. Mitigating Cybersecurity Risks. CONTINUUM: Lifelong Learning in Neurology, 23(2), pp.553-556. [Available at: https://journals.lww.com/continuum/fulltext/2017/04000/Mitigating_Cybersecurity_Risks.16.aspx]
Rubino, M., 2018. A comparison of the main ERM frameworks: how limitations and weaknesses can be overcome implementing IT governance. International Journal of Business and Management, 13(12), pp.203-214. information security management assignment [Available at: https://www.researchgate.net/profile/Michele_Rubino3/publication/329091297_A_Comparison_of_the_Main_ ERM_Frameworks_How_Limitations_and_Weaknesses_can_be_Overcome_Implementing_IT_Governance/ links/5bf508faa6fdcc3a8de63240/A-Comparison-of-the-Main-ERM-Frameworks-How-Limitations-and-Weaknesses-can-be-Overcome-Implementing-IT-Governance.pdf]
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model in organizations. Computers & security, 56, pp.70-82. [Available at: https://www.sciencedirect.com/science/article/pii/S0167404815001583]
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more holistic approach: A literature review. International Journal of Information Management, 36(2), pp.215-225. [Available at: https://www.sciencedirect.com/science/article/pii/S0268401215001103]
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more holistic approach: A literature review. International Journal of Information Management, 36(2), pp.215-225. [Available at: https://www.sciencedirect.com/science/article/pii/S0268401215001103]
Techadvisory.org 2020, Risks to prepare for in business, [Available at: https://www.techadvisory.org/2018/08/4-byod-security-risks-you-should-prepare-for/
Techtarget 2020.com, What is identity theft, Available at: https://searchsecurity.techtarget.com/ [Accessed on: 17th September 2020]
Wangen, G., Hallstensen, C. and Snekkenes, E., 2018. A framework for estimating information security risk assessment method completeness. Information security management assignment International Journal of Information Security, 17(6), pp.681-699. [Available at: https://link.springer.com/article/10.1007/s10207-017-0382-0]












