IT Ethics Assignment: Regulation on Road Safety
Question
Task: Select a media article or a case study in this report on IT ethics assignment and undertake further research about your chosen case and the ethical issue involved.
Answer
Introduction
This has been identified in this IT ethics assignmentthat there are various ethical and privacy issues that have emerged with the increase in the use of the digital technologies and computing mediums. There are ethical norms and principles that are required to be protected and preserved at all times. Information technology (IT) ethics includes the determination of the ethical issues that have emerged with the technological innovation and the implementation of the measures to preserve ethical values and norms. The violation of ethical principles and norms by the users and the business organizations is resulting in the negative implications on the end-users, business organizations, and all of the stakeholders that are associated with the firms(Spinoza et al., 2018).
There are several ethical theories that have been applied to the selected case to understand the aspect of ethics associated with the same.
Background of the Scenario
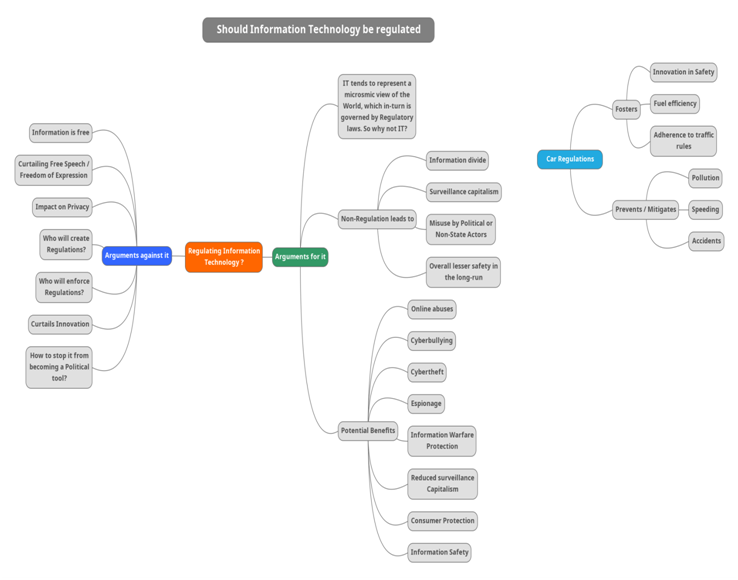
The scenario that has been discussed in the segments of IT ethics assignment explores the aspect of information technology ethics. The article explains the hiring of the chief ethics officers and other resources by the business firms. However, the argument states teaching and regulating IT ethics with the prominent role of the government in the same (Vardi, 2019). The correlation has been presented with the road safety measures that are developed and now implemented due to the various government regulations on road safety rather than the ethics. Ford is the company that came up with the initial model in 1908. The concept of safety was not realized at that time and it has been developed since that time. There are massive developments that have been done in terms of the innovation in safety along with the improvements in the fuel efficiency(Blind et al., 2017). All of this leads to the prevention and mitigation of the issues, such as pollution, speeding, and accidents. The regulations around road safety is one of the primary reasons that has resulted in safer driving practices rather than the involvement of the ethical codes and principles in these cases.
The same concept of car & road safety & regulations is correlated with the information technology regulations. The information is currently available for free which is resulting in the negative impacts on the privacy levels. It may be misused as a political tool and it is essential to have IT regulations in place and to determine the entities that can develop and implement such regulations. The non-regulation of IT can lead to various issues, such as surveillance capitalism, political misuse, compromised safety, and information divide. There are benefits that IT regulation will bring along for the businesses and for the end-users. These include the mitigation of cyberbullying, consumer protection, improved safety, information warfare protection, and many more.
Argument Visualization
The arguments that are discussed and explained in the article are depicted using the MindMup software as presented in the IT ethics assignment.
Application of Ethical Theories
There are several ethical theories that have been developed and these are used to understand the ethical aspects of the issues and arguments that are covered in the article examined herein IT ethics assignment.
Theory of Utilitarianism
The ethical theory of utilitarianism is applied to understand the implementation of the IT regulations or not. The ethical theory evaluates and determines the ethical correctness of the specific action on the basis of the consequences that can arise. If the consequences of an action are positive then the action is considered as ethical and vice versa(Mill & Bailey, 2016).
In the scenario of IT regulations, there are consequences that will arise with the implementation of the regulatory policies and frameworks around IT. Currently, there are numerous issues of cybersecurity and cyberattacks that are present. Some of the most prominent forms of the attacks include cyber theft and cyber-bullying. This is because of the lack of regulations and the easy availability and access to the information sets. These issues and risks will be controlled with the IT regulations in place. The attackers and malicious entities will be aware of the actions and punishments that they will have to face and it will automatically reduce the probability of these attacks. Online abuses and trolling has become extremely popular and the lack of the regulations is one of the major reasons behind the same(Li et al., 2019). With IT regulations in place, it will be possible to control such issues.
The business firms in the present times are making use of the information sets for the purpose of analytics. The profit-making is being done using the information and its analysis. These information sources on the web have become the most important sources for the business organizations. There is modification of the personal information of the user that is also done. The user is not informed about such actions and there are profits that are gained by the business organizations. The IT regulations will reduce and put a check on the surveillance capitalism. The reduction of espionage and the information warfare protection will be possible with IT regulations in place. The users put a lot of their personal information on the web sources. There are privacy and physical risks that the users get exposed to if the information is accessed by the malicious entities. The consumer protection will be assured with the implementation of the IT regulations and it will also guarantee the safety of the information sets (Yeoh, 2015).
All of these consequences outlined with respect to the case scenario of IT ethics assignment are positive and will be beneficial to the parties involved. The IT regulation will make sure that the benefits are possible for the governments as well as the controlling and mitigation of the privacy issues will be possible.
On the other hand, if the information technology regulations are not developed and implemented, there are certain consequences that can be associated with the information sets. Surveillance capitalism is one of the primary issues. The information available can also be misused for the political purpose and the information owners may never get to have the understanding of such usage. The commodified information can be misused and there are significant information safety risks that can arise. The issue of information divide can also be significant.
The analysis of the scenario using the Utilitarianism theory suggests that the IT regulations will have positive influences on the information privacy, end-users, and the business organizations and stakeholders. However, the impacts will be negative if the IT regulation is not in place. As a result, information technology regulation shall be implemented in the organizations and on the national levels(Ivarsson et al., 2016).
Deontology Ethics
This is the ethical theory in which the ethical justification and correctness is based on the specific laws, rules, and protocols around the associated action.
There are various laws that have been developed around information security and privacy. Some of these include the Privacy Act, Intellectual Property Rights, Cyber laws, etc.(Nyoni & Velempini, 2015)There are various cybersecurity risks and issues that are present due to the lack of information technology regulations. Some of the common issues and frequently occurring attacks include cyber thefts, online abuses, and cyber bullying. The impact of such attacks is negative on the involved users and on the associated business firms as well. For example, if the cyber theft issue occurs on the business application of a particular organization, then the customer trust and the brand value of the organization will also be negatively impacted. It will bring down the customer engagement levels and will also cause the monetary losses to the organization.
The issues of information warfare are also common wherein the national security can be put at stake. In all of such scenarios, the violation of the existing laws and protocols is done (Rickaby, 2015).
With the IT regulations in place, it will be possible to have adherence with the defined laws and protocols. These new regulations will also enable the protection of the consumer safety, information safety, and privacy.
As per Deontology Ethics, it is observed that lack of IT regulations is also causing negative implications on the rules and laws that are developed so far. With the development and implementation of the proper regulations, it will be possible to put a check on these issues and concerns.
Virtue Ethics
As per the research conducted on this IT ethics assignment, Virtue Ethics is the theory in which the virtues of the specific users or actors involved with a particular action is considered and analysed. These virtues are used to determine if an act is ethical or not.
The application of the ethical theory is done to determine the decision on IT regulations. There are business organizations that are using the information sets available online and on the web channels to gain business profits. The analysis of these information sets is done without any knowledge to the information owner (Angier, 2018). The information is commodified and it is also being used for political benefits and agenda. The misuse of information for political purpose or surveillance capitalism involves the virtues of selfishness, personal gains, and dishonesty. These are some of the negative virtues that are associated.
The IT regulations will set up the specific protocols and norms to make sure that the guided and controlled access & use of the information is done. This will also ensure that the information flow is proper and the information owners have the controls to preserve the privacy of the information sets. The negative virtues that are listed above will also be removed automatically(Angle & Slote, 2015).
The Virtue Ethics theory, therefore, supports the idea of IT regulations and its implementation.
What is the role Theory of Social Contractin the present context of IT ethics assignment?
The aspects of ethics and social values & norms are very closely associated with each other. There are a few norms and protocols that every society follows and the preservation of the same must be done. The theory of social contract is based on the same and supports the activities that can abide by these social norms and guidelines.
The IT ethics and protocols also consider these social norms. The lack of IT regulations is leading to the negative implications and the violations of these social norms and guidelines. With the limited regulations and the lack of IT regulations in place, it has been seen that the case of information privacy violations, online abuses, espionage, information warfare, information divide, etc. is increasing at a massive rate. The social harmony is getting disturbed because of the occurrences of these issues (Welch, 2016).
Also, without the proper regulations, there is negative influence on the innovations that can also be witnessed. The unregulated use of the information sets as a political tool can also result in the negative impacts on the society.
The lack of IT regulations does not abide by the social contract and it is resulting in the negative implications on the ethical and social principles. As a result, the theory supports the arguments that are presented and states that the IT regulations must be developed and implemented.
Conclusion
The scenario and arguments around the IT regulations are analysed and determined using the four ethical theories in the above context of IT ethics assignment. All of the four theories of ethics support the idea of information technology regulations and its implementation. This is because of the current issues that are identified due to the lack of IT regulations. The non-regulation is leading to increased information divide and enhanced surveillance capitalism. The information safety has gone for a toss and the information is also being used for the political benefits.
The IT regulation is associated with a list of benefits. It will have a major role to play in mitigating and preventing the cybersecurity risks and attacks. The IT regulation will also result in the consumer protection and it will make sure that the information safety is ensured. There will be information warfare protection that will improve. Information and technology are the two key aspects that play a significant role all across the globe. It is essential that the regulation of the same is done. The entities that shall be responsible for IT regulation must be determined. All of the existing gaps shall be considered to have the detailed IT regulations in place. The IT regulations will be beneficial from the security, privacy, ethical, and social aspects. These will benefit the end-users, business organizations, governments, and all of the internal and external stakeholders associated with the business firms.
References
Angier, T. P. S. (2018). Virtue ethics. Routledge.
Angle, S. C., & Slote, M. (2015). Virtue ethics and Confucianism. Routledge, Taylor & Francis.
Blind, K., Petersen, S. S., & Riillo, C. A. F. (2017). The impact of standards and regulation on innovation in uncertain markets. Research Policy, 46(1), 249–264.
https://doi.org/10.1016/j.respol.2016.11.003
Ivarsson, B., Wiinberg, S., & Svensson, M. (2016). Information and/or medical technology staff experience with regulations for medical information systems and medical devices. Health Policy and Technology, 5(4), 383–388. https://doi.org/10.1016/j.hlpt.2016.07.008
Li, H., Yu, L., & He, W. (2019). The Impact of GDPR on Global Technology Development. IT ethics assignmentJournal of Global Information Technology Management, 22(1), 1–6. https://doi.org/10.1080/1097198x.2019.1569186
Mill, & Bailey, A. (2016). Utilitarianism. Broadview Press. Nyoni, P., & Velempini, M. (2015). Data protection laws and privacy on Facebook. SA Journal of Information Management, 17(1). https://doi.org/10.4102/sajim.v17i1.636
Rickaby, J. (2015). MORAL PHILOSOPHY?: ethics, deontology and natural law (classic reprint). Forgotten Books.
Spinoza, Kisner, M. J., & Silverthorne, M. (2018). Ethics. Cambridge University Press.
Vardi, M. Y. (2019). Cars are regulated for safety – why not information technology? The Conversation. https://theconversation.com/cars-are-regulated-for-safety-why-not-information-technology-111415
Welch. (2016). Theory of freedom?: feminism and the social contract. Palgrave Macmillan.
Yeoh, P. (2015). Implications of online funding regulations for small businesses. Journal of Financial Regulation and Compliance, 22(4), 349–364. https://doi.org/10.1108/jfrc-02-2014-0012












