IT Risk Management Assignment: Business Continuity Plan For SoftArc Engineering
Question
Task: SoftArc Engineering Ltd (SEL) is a civil engineering company which works across Australia as well as in New Zealand, Fiji, Vanuatu, Indonesia, Timor Leste and Papua New Guinea. SEL has a small data center at its main site in Bathurst where the company’s servers and data storage is located.
The company has some 70 engineering and support staff that work on different projects for clients in various locations in Australia and overseas. The support staff is mainly based in Bathurst, but engineering staff are located in different parts of Australia, New Zealand, and Papua New Guinea. Most of the support staff have access to a PC, although some support staff share a PC with other staff. The engineering staff all connect remotely to the SEL data centre from their laptops. The SEL data center infrastructure has not been updated for some time and the SEL Board is concerned that they may be exposed to a cyber-attack as they are now starting to work on various Government projects in different countries.
Background:
You have been employed by SEL as their first Chief Information Security Officer (CISO). You have been tasked by the Board to conduct a review of the company’s risks and start to deploy security policies to protect their data and resources.
You are concerned that the company has no existing contingency plans in case of a disaster.
The Board indicated that some of their basic requirements for contingency planning include:
A Recovery Time Objective (RTO) of 4 hours
A Recovery Point Objective (RPO) of 6 hours
Based on these, you now need to determine:
The Maximum Tolerable Downtime (MTD),
The Work Recovery Time (WRT) and
The system and data recovery priority
The Board expects that you will propose a Business Continuity Plan (BCP) for SEL. The Board expects you to use as much of their existing resources as possible for the BCP, but understands that some additional resources may be required. Your BCP proposal must clearly state what additional resources, in terms of hardware, software and locations, are required.
You are to develop a report on IT risk management assignment for a Business Continuity Plan (BCP) for SEL in accordance with the Board's instructions above.
Answer
Introduction
This BCP will be focused upon the company SoftArc Engineering Ltd or SEL where the IT risk management plan for SoftArc Engineering Ltd will be discussed in detail. IT risks are one of the major problems that a company faces and there are various risks like losing data, security breaching hacking, and so on. This BCP will be discussing various aspects that can be implemented by SEL so that they can prepare a proper IT risk mitigation plan.
An executive overview of the BCP
SoftArc Engineering Ltd or SEL is a civil engineering company and as they do not have any proper data security system at their company, they must come up with a plan for avoiding cyber-attacks as they are associated with some of the government work and there is a huge risk of cyber-attack at this moment. This BCP will introduce the maximum tolerable downtime or MTD and work recovery time or WRT based on the recovery time objective or RTO and recovery point objectives or RPO that has already been provided by the company itself. The BCP will also discuss the system and data recovery priority so that a proper business security plan can be created and this BCP plan will also state the resources of the company that will be used and for different locations how the plan will work (Ahmad et al., 2015).
It has been decided that the RTO will be 4 hours and RPO will be 6 hours and based on that the MTD and the WRT can be calculated. Maximum tolerable downtime or MTD is an estimated time for a business that can tolerate the unavailability or the absence of some of the major business functions. The MTD of a business depends on the type of business and usually where the criticality is high there the MTD is shorter. For calculating MTD it is important to know about the RTO and the WRT (Cremen et al., 2020). WRT is one of the segments that compromises the MTD as usually getting the backup of the various critical functions of the business including the hardware, the software, and the data configuration takes time so, if the MTD is estimated to be 3 days then the WRT will be less than that. In the context of SEL, the RTO is given 4 hours and the RPO is given hours so, here the calculated WRT will be 10 hours and MTD will be 14 hours. Based on this time the data recovery and security plan can be deployed so that the recovery process can address the timelines.
Business impact
The business impact analysis can be done based on various factors like RPO, RTO, and MTD, and WRT, and the BIA will help in understanding the data security plan for the company SEL. As SEL has taken up some of the government projects, there is a huge risk of data breaching and losing of data to the hackers and as they do not have a proper IT risk management plan, they need to use their resources like hardware, software, and data configuring and so on so that they can create an effective IT risk management plan which will help the company in securing all the data and control the amount of damage that can happen in near future as there is a lack in the contingency plan (Ghandour, 2014).
The requirement for the recovery time:
There is a requirement for the recovery time at SEL and the requirements are usually related to a few interrelated factors. A figure has been inserted so that the relationship between the factors can be understood.
Figure 1: Recovery time
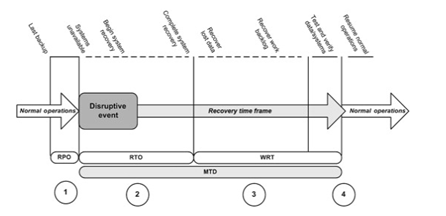
(Source: Ghandour, 2014)
From this image, it can be seen that the factors are RPO, RTO, WRT, and MTD which are associated with the disruptive event and the recovery time frame that are necessary to restore the normal operations. As MTD or maximum tolerable downtime helps in understanding how long a business can run without the availability of the particular functions that are required, it will help SEL in determining how much time they have for implementing the proper risk management that is required. It was calculated that in the case of SEL the MTD is 14 hours before they have to take the proper initiative so that they can resolve the critical situation.
In this context, the RTO will also play a major role for SEL as RTO is known as recovery time objective and it is a segment of MTD which determines the time that is available for recovering the resources and the system that was disrupted by the critical situation that occurred. It has been calculated that the RTO that is available for SEL is 4 hours so, SEL has to wait for this time before their systems can be back to the process and start working in a normal way like before. The next step that is needed to be taken by SEL is that they need to determine in what status their data are and they need to determine their RPO which is very important in this context (Gupta&Ilgin, 2017). The RPO of SEL has been calculated beforehand and it can be seen that they have the RPO of 6 hours. If SEL has a critical mission to handle and that does not properly connect with the computer system they have, they must create a BIA so that all the works can be done manually and SEL can be able to resume their old work routine but in this context, they have to keep in mind what kind of disaster they are facing and that will be helping them to create business continuity plan accordingly.
Incident response
The incident response is necessary for SEL and this is usually done by a team that is responsible for implementing the incident response plan. The team for incident response can be built at SEL by including the IT experts who are eligible for collecting, storing, sorting, and analysing the data that are related to the incident (Torabi et al., 2016). The team of incident response works hand in hand with the lawyers as well so that they can make sure all the legal obligations related to the incident are met properly by the company and the communication is being established properly as well. In the case of SEL if they implement the incident response plan in prior then it will be beneficial for them as their network is not threatened yet and if the network is violated or threatened in the future, they will have a plan that can omit all the chaos that might happen from a cyber-attack (J. Kikwasi, 2018). The threat can be virtual like some of the security threats or virtual breach of the threat can be physical like the power outrages or any kind of natural disaster as well. Threats might come from losing some of the confidential data and crippled functions too. Having a proper IT risk management plan would help SEL in mitigating all these risk factors and the IT risk management plan includes the incident response as having an incident response group will help them in having a proper mitigation plan.
For creating an effective and efficient incident response plan SEL first needs to detect all the critical factors of their network as for protecting the network from any kind of major damage. The best option for SEL would be replicating all the important data of their company and storing them in a remote storage place so that even if any kind of hazard takes place they will not lose the data and have access to it. Prioritising the backup plan and keeping the track of the backup locations would be beneficial for SEL. SEL should have a plan B for all the crucial data of their network and the hardware and the software as well. They need to keep the backup of their staff roles and it is important to identify all the failure points of the network and addressing them as a minimum point of failure can lead up the whole company network to the threats (Mikosch, 2016). Creating a proper workforce design and strategies can help SEL in implementing and managing the incident response plan in the desired way as well because that will make the employees at every level understand their roles.
Backup
Backing up the data from the network is very much essential for a company and in this context, SEL is not an exception. As they do not want any kind of network-related threat to harm their confidential data, they can adopt various methods for backing up their data (Rostami et al., 2017). SEL can choose the proper method for backing up their data based upon how they usually store their data, how their various resources are available, and how their connectivity is working. They can use the electronic backup method as all the data that are stored electronically can be restored after a disruption.
They can use the method of the full backup system as this method is usually used for copying all the data and storing them at another location so that the data can be accessed later as per the convenience of the users. This method can be advantageous but the disadvantage is that it takes a lot of time and the bandwidth and the resources have to be intense (Miora, 2015). Another method that can be used by SEL for backing up their data is incremental backup as it helps in restoring the data that have been lost since the last incremental backup. The last option that can be used by SEL is differential backup as it helps in backing up all the data that have been changed since the last full backup. These methods will be beneficial for SEL as they want to avoid any kind of data loss at all.
Disaster recovery
Disaster recovery planning is used by the companies as it is one of the risk management measures that help in recovering from disruptions and disasters. It helps in withstanding all the outrages and threats that are not usually possible by the companies to prevent properly. Data recovery can be done through backups and by using other redundant systems and structures related to the network (Montshiwa, 2017). If the data is properly stored then it is easy to get the backup and recover the data if any kind of cyber-attack or a breach in the cybersecurity takes place. It is beneficial for SEL that they find a proper redundant infrastructure for mitigating the risk of cyber-attacks. Developing a data recovery plan is slightly different than the planning that is usually created for continuation of the operational functions of a business and the plan for data recovery focuses on the core infrastructure of the network of the company and the IT structure for bringing sustenance in the operational functions of the business.
If a huge cyber-attack takes place at SEL then they will not be able to operate some of their works that are done through networking and various domains (Podaras,2015). When they will consider implementing the data recovery plan they will be able to pay more attention in the area of backing up their data and they can operate that in a large geographical range as they have their branches in Australia, New Zealand, and Papua New Guinea. Implementing the data recovery plan will be very effective for SEL as they will also be able to use their resources properly in all these locations.
Conclusion
In a conclusion, it can be said that SEL is approaching the government projects and eventually they will need a proper cybersecurity system so that, the risks that might come up regarding IT security can be mitigated effectively. For mitigating the IT risks and cybersecurity risks a business impact analysis have been provided where the RPO, RTO, WRT, and MTD have been determined and discussed and other aspects of IT security like incidence response, data recovery and back has also been discussed where the preferable methods have been advised for SEL. It has been found that SEL needs to implement a proper full backup plan so that they can recover the data if any breach happens.
References
Ahmad, M., Zakuan, N., Ahmad, J., &Takala, J. (2015). A meta-analysis of the TQM impact on business performance amongst regions and countries. International Journal of Industrial and Systems Engineering,
20(2), 155. https://doi.org/10.1504/ijise.2015.069546
Cremen, G., Seville, E., & Baker, J. W. (2020). Modeling post-earthquake business recovery time: An analytical framework. International Journal of Disaster Risk Reduction, 42, 101328. https://doi.org/10.1016/j.ijdrr.2019.101328
Ghandour, A. (2014). Identifying dimensions of business continuity plan from common expressions among business continuity professionals. International Journal of Business Administration, 5(3). https://doi.org/10.5430/ijba.v5n3p136
Gupta, S. M., &Ilgin, M. A. (2017). Analytic network process. Multiple Criteria Decision-Making Applications in Environmentally Conscious Manufacturing and Product Recovery, 107-116. https://doi.org/10.1201/9781315119304-9
J. Kikwasi, G. (2018). Critical success factors for effective risk management. Risk Management Treatise for Engineering Practitioners. https://doi.org/10.5772/intechopen.74419 Mikosch, T. (2016). Review of A. J. McNeil, R. Frey, P. Embrechts: Quantitative risk management.
Concepts, techniques, and tools. European Actuarial Journal, 6(1), 283-285. https://doi.org/10.1007/s13385-016-0122-2
Miora, M. (2015). undefined. Computer Security Handbook, 59.1-59.22. https://doi.org/10.1002/9781118820650.ch59
Montshiwa, A. L. (2017). Regional business continuity management comparative analysis. International Journal of Business Continuity and Risk Management, 7(1), 1. https://doi.org/10.1504/ijbcrm.2017.083691
Podaras, A. (2015). A non-arbitrary method for estimating IT business function recovery complexity via software complexity. Lecture Notes in Business Information Processing, 144-159. https://doi.org/10.1007/978-3-319-19297-0_10
Rostami, K., Heinrich, R., Busch, A., &Reussner, R. (2017). Architecture-based change impact analysis in information systems and business processes. 2017 IEEE International Conference on Software Architecture (ICSA). https://doi.org/10.1109/icsa.2017.17
Torabi, S. A., Giahi, R., &Sahebjamnia, N. (2016). An enhanced risk assessment framework for business continuity management systems. Safety Science, 89, 201-218. https://doi.org/10.1016/j.ssci.2016.06.015












