Network security assignment: Technology in Healthcare
Question
Task: In this assignment students have to demonstrate theoretical as well as practical knowledge and skills acquired from lecture and laboratory classes.
The assignment consists of two parts. Description of each section
A. Healthcare Networks
B. Compare Port Scanners
Answer
Healthcare Networks
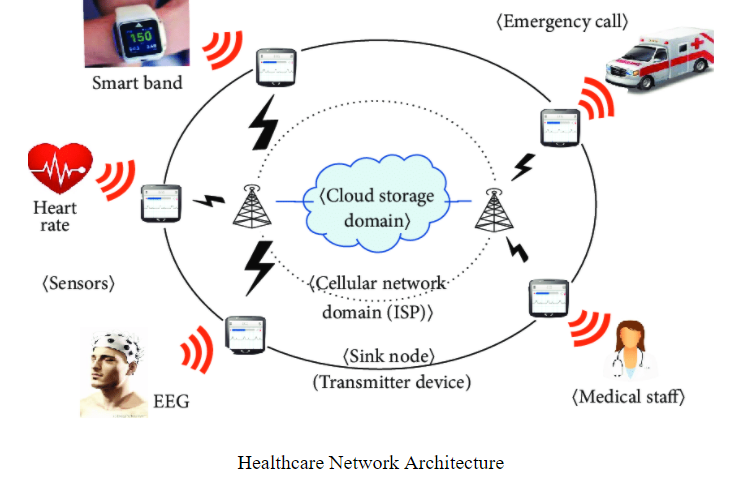
Healthcare Network Architecture
The discussion on network security assignment is built on the increasing use of technology in the healthcare sector. There are a number of healthcare network architectures that are used. One of such architectures is included in the image below within this network security assignment. There are several components that are present in these network architectures with the inclusion of the cloud networks and storage as the primary components [1]. There are varied sensors and nodes that are also present in the healthcare networks. The graphical representation of the same has been shown below in the network security assignment.
Recent Developments
There are on-going developments in the healthcare networks that can be witnessed. There are a number of changes and modifications that have been done as discussed in the network security assignment. The release of the wearable technology has led to the enhancement of the networking requirements along with the integration of the analytical tools on the networking channels. There are developments that are being done to include the smart networks in the healthcare network architecture. These smart networks are now based on the 5G networks and technologies [2]. These 5G networks offer higher network bandwidth and speed. This automatically leads to the enhancement of the transmission speed and the overall network efficiency also improves.
The use of the IoT systems and networks is also a recent development that can be witnessed in the healthcare sector. There are tele-health monitoring applications that have been developed. These applications provide the patients and the medical professionals to be in sync with each other. The IoT-based apps provide the mechanism to integrate all of the information and the data sets and the use of the sensor networks and nodes is done [3]. The IoT apps and combined with the wireless sensor networks for smooth transmission. It also provides the ability to make sure that the real-time access and transmission is made possible.
Security Issues
The use of technology and the digitalization of the medical records have resulted in the immense benefits to the healthcare sector. However, there are also a lot many issues that have been determined with the use of technology and automated sectors.
One of the primary security issues depicted in the context of network security assignment that are observed is the breaching of the data sets. The medical information of the patients along with the rest of the information around the healthcare organization is now transmitted over the cloud networks and wireless channels. There are numerous security vulnerabilities and loopholes that are present on these channels. These vulnerabilities may be utilized by the attackers to carry out the issues around data breaches. For instance, there are a number of patients that now make use of the IoT-based tele-health networking apps. These apps as noted in this section of network security assignment allow the patients to record their health signs, such as heart rate, blood pressure, blood sugar, and likewise [4]. The patients can send these details to their respective medical professionals to obtain the medical feedback and comments. In the case of the usage of the public networks and channels, it is possible that the attackers easily violate the access norms and gain access to the information sets. The private health information of the patients is extremely confidential and the privacy breaches may be done. There are other ways in which the breaching of the datasets can be done through the healthcare networks that are used. The man in the middle attacks is common over the wireless channels. These are the attacks in which the attacks gains unauthorised access to the wireless networking channel and the network eavesdropping is performed. The monitoring of the information transmitted and shared over the network channels may be easily done using these network channels.
There are other security and privacy concerns discussed in the network security assignment that may occur over the healthcare channels. The use of the IoT and wireless sensor networks is often done in the healthcare sector. These are exposed to the node-based security concerns. For example, selective forwarding attacks may occur over the network channels. The information that is shared over the networks is in the form of the data packets. There are hundreds and thousands of data packets that are transmitted by the healthcare organization to the varied entities. In the selective forwarding attacks, the attacker may target a particular node that may divert the route of the data packets or may drop some or all of these packets. As a result, there are major integrity and consistency concerns that may arise along with the issues with the service continuity and availability. These attacks are common in the cloud networks wherein the attackers can have numerous ways to gain access over the cloud networks [5].
Possible Solution
There are certain solutions and countermeasures that can be adopted to make sure that the security issues and concerns are avoided. The issues around data breaches are relevant and need to be resolved. These can be managed using the technical and logical security controls. The use of advanced encryption is one of the most relevant techniques that may be adopted. The information and datasets associated with the healthcare organization shall be encrypted. With the encryption of the datasets, the confidentiality and privacy of the information will be maintained at all times. The readings used to prepare this network security assignment signify that even if the attackers succeed in gaining access over the online channels and the networks, they will not be able to view the private health details of the patients.
There are network security tools that shall also be used to prevent the data breaches from taking place. The use of the advanced network security tools, such as the use of the Blockchain networks can be done. Blockchain is a technology that guarantees the security of the information and the datasets. The technology makes sure that the use of the cryptography is done for the purpose of data transmission and the cryptographic hash functions are used for ensuring the data security [6]. In the network security assignment, the use of the Blockchain networks along with the encryption algorithms and protocols will make sure that the security and privacy concerns over the healthcare networks are avoided. Also, the users must be trained to follow the security practices and protocols at all times.
Port Scanners
Importance of Port Scanners
Port Scanners are the mechanisms and techniques to determine the open ports over the network channels. These are important from the aspect of network security techniques. This is because the determination of the network security vulnerabilities and loopholes can be done using the port scanners. The amount of information being accessed or transmitted by the open ports can be done through the port scanning technique. There are required changes that can be made thereafter to make sure that the overall network and information security is safeguarded at all times.
Port Scanning tools
Zenmap is among the newest network reconnaissance tool in the market and a graphical user interface (or GUI) for Nmap. Like Nmap, it is also a free and open-source, cross - language software intended to make Nmap simple to be used for novice users while offering sophisticated features for advanced Nmap users.
Nmap is a General Public License open source or simply GNU based software. It is a Network evaluation tool and a very valuable tool at that. It is used by Network administrators for identifying, tracking as well as troubleshooting the TCP / IP devices. Nmap's reliable network scanning application suite has already been in steady development since 1997 and develops consistently between each new update. Last updated in August 2019 , the new edition being 7.80.
What are the strength and weaknesses of Nmap and Zenmap discussed in the network security assignment?
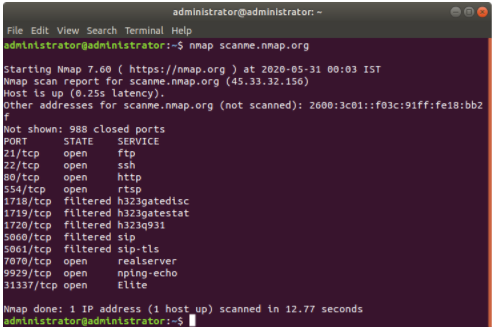
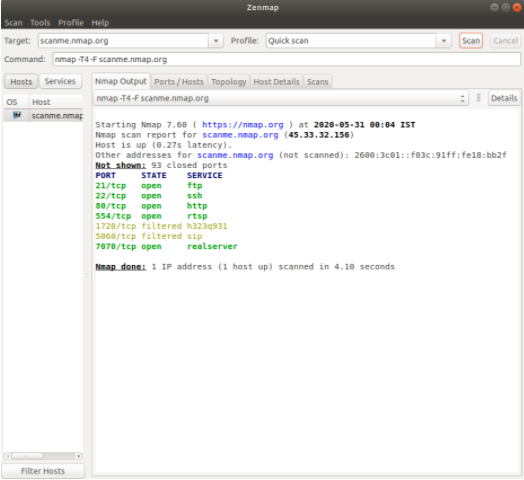
In the below screenshot provided in the network security assignment, both show similar results as they are based on the same underlying technology and will have similar features in terms of port-scanning ability.
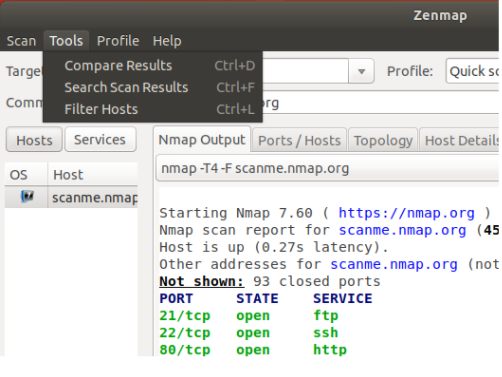
ZenMap has both a filter option as well as the search option, whereas Nmap only has the search option.
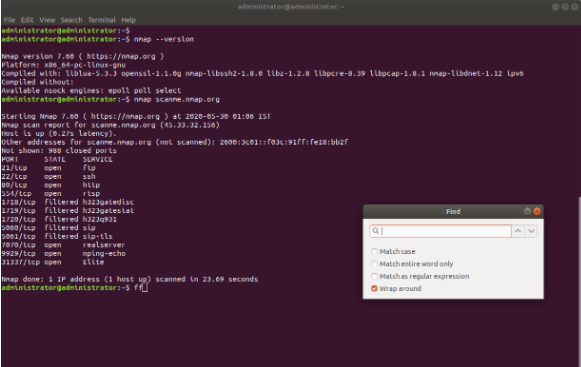
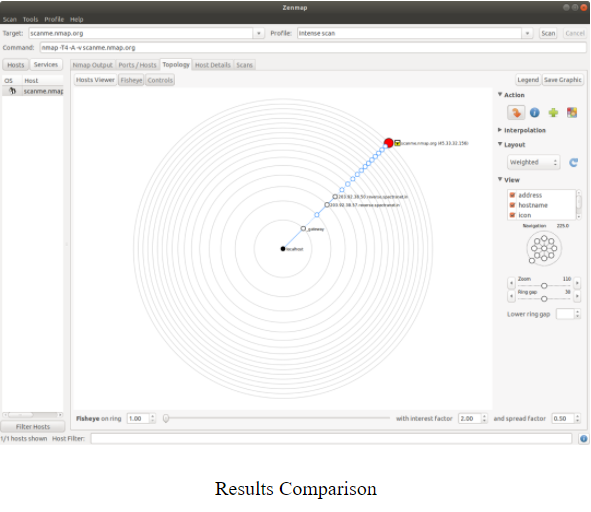
Zenmap also additionally, has a Network topology option that helps visualize the target network’s topology layout, which Nmap does not.
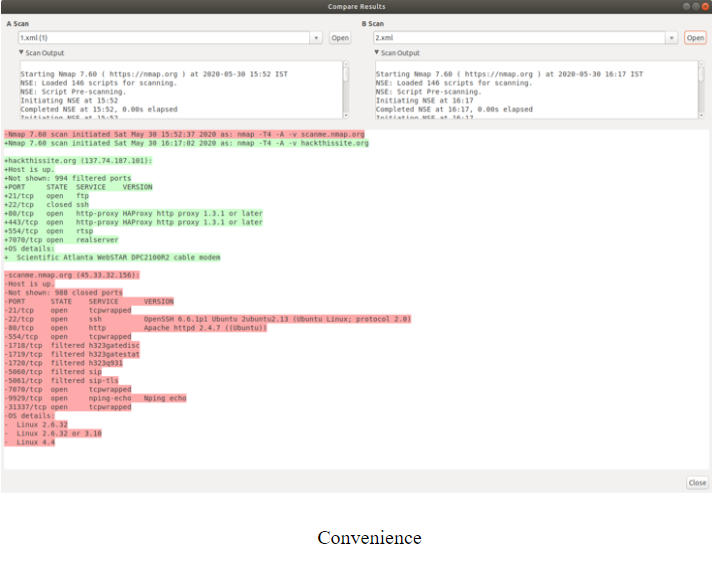
Zenmap has the potential to display the distinction between the 2 scans. One would see what happened over various days or with the scans of 2 separate hosts, or perhaps the scans of the exact sae hosts but with different choices, or maybe any other mixture. It is seen in this network security assignment that this enables administrators to monitor new hosts or services that show up on their networks or helps for better network reconnaissance.
While, Nmap does not have a result comparison feature, what can be done to achieve the same is by having two different windows opened to compare them.
Whereas, Zenmap has in-built results comparison feature.
Nmap does not save scan results into a database. It can generate output. However, Zenmap on the other hand keeps a record of the scanning findings until one decides to delete them. This means that users could even execute a scan and have the results saved until one decides to give them a custom filename or delete it.
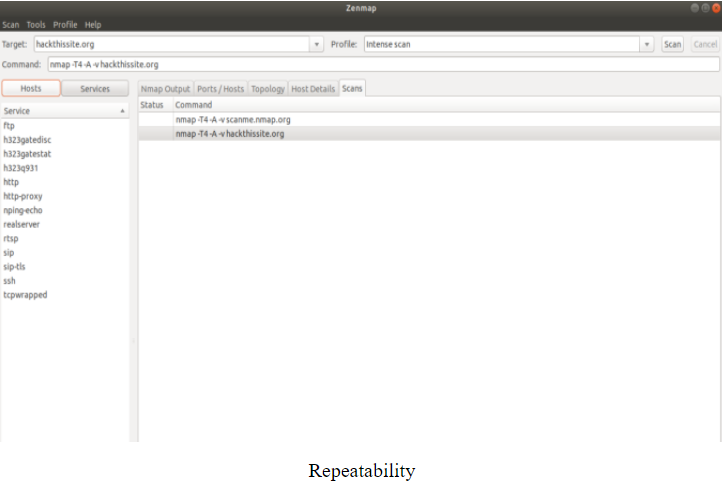
Both, Nmap and Zenmap's mentioned in the network security assignment have the ability to create and load customized profiles. This allows users to not having to create customized scans every time they intend to. This allows performing same scan easily and repeatedly for security and monitoring purposes. The difference is that in Zenmap, it is much easier and convenient to create, save and execute profiles because of its GUI.
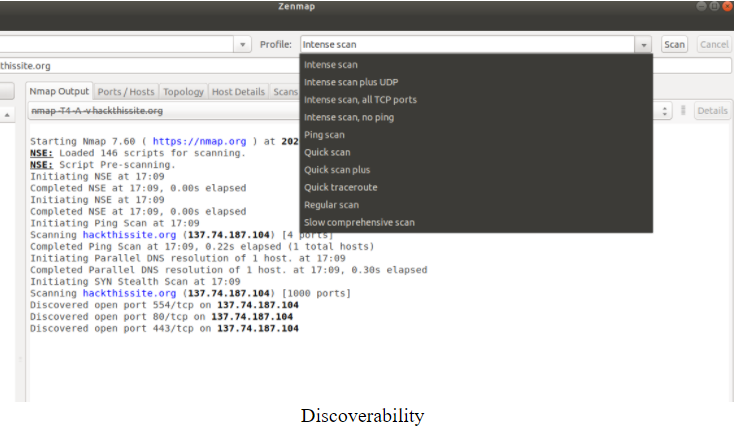
Nmap essentially has variety of options that can astonish newcomers. Zenmap's interface was developed so as to show what command is being run, if it originates via a profile or if it was developed by selecting options from just a menu. It lets the learners know what they're doing learn. This also lets specialist’s dual-check what is going to be done until clicking "Search."
Recommendation
It is evident from the above discussion on network security assignment, that the recommendation for both novice as well as expert users should be Zenmap over Nmap. In essence, Zenmap not only puts the novice users at ease, but it also provides power users with commendable features that makes them feel they are in control.
References
[1] Y. Zhang, L. Yu, and L. Wang, “High Access Performance Strategy for Next Generation Healthcare Networks,” network security assignment Journal of Networks, vol. 9, no. 6, Jun. 2016.
[2] S. Latif, J. Qadir, S. Farooq, and M. Imran, “How 5G Wireless (and Concomitant Technologies) Will Revolutionize Healthcare?,” Future Internet, vol. 9, no. 4, p. 93, Dec. 2017.
[3] M. A. Ghori and D. S. A. Sattar, “IoT Integrated Energy Efficient Wireless Sensor Networks Application for Healthcare,” International Journal of Trend in Scientific Research and Development, vol. Volume-2, no. Issue-3, pp. 2749–2754, Apr. 2018.
[4] F. Kamoun and M. Nicho, “Human and Organizational Factors of Healthcare Data Breaches,” International Journal of Healthcare Information Systems and Informatics, vol. 9, no. 1, pp. 42–60, Jan. 2015.
[5] C. Changchit and K. Bagchi, “Privacy and Security Concerns with Healthcare Data and Social Media Usage,” Journal of Information Privacy and Security, vol. 13, no. 2, pp. 49–50, Apr. 2017.
[6] S. Tanwar, K. Parekh, and R. Evans, “Blockchain-based electronic healthcare record system for healthcare 4.0 applications,” network security assignment Journal of Information Security and Applications, vol. 50, p. 102407, Feb. 2020.












