Networking Assignment Evaluating 802.11 standard of WLAN
Question
You are to perform a study on various 802.11 wireless networks in order to choose a suitable security measures that should be put in place for a given scenario. This networking assignment is divided in two parts. The study will be partially theoretical and technical. The technical part will require you to evaluate the effectiveness of using various standards against known attacks. You will then in part B identify what are the security measures that the company in the chosen scenario should consider implementing.
Part A: Technical flaws research: You will need to research several known security flows on the various 802.11 security protocols. You should also consider the various possible types of deployment such as in infrastructure deployment of 802.11 or in enterprise mode.
- Research how to bypass WLAN authentication if SSID is hidden and if administrators use MAC filtering.
- Research WLAN encryption flaws (WEP, WPA2).
- Research 802.11 clients and identify flaws and they can be exploited.
Part B: Research Based Work: Based on your findings in part A, you are required to analyse results obtained and choose suitable security measures for your chosen scenario. Following this, you are expected to defend your security choices by comparing your justifications with different research papers discussing the effectiveness of wireless security protocols in different environments. Effectiveness of the chosen security measures should be evaluated in term of how they can be exploited (if possible), how suitable they are for the environment they will be used in and the threats that the scenario is subject to.
Answer
Abstract
Wireless Networks with 802.11 standards is gaining popularity because of its flexibility and mobility towards accessing information. The current solutions of WLANs are getting exposed to several security vulnerabilities. After evaluating the 802.11 standard of WLAN, certain technical issues have been identified in the paper. Finally, it has been recommended to use WPA2 security protocol for protecting the network of the small company through the use of 256 bits’ encryption technology and changing the secret key periodically.
Introduction
Wireless network security is the protection of the network from various cyber attackers and unauthorized users by keeping the network secure. ‘A small company that only allows staff to access the network is chosen in this report as a scenario. The report will analyze how to bypass the authentication if the administrator utilizes MAC filtering and if the SSID is hidden. The report will also analyze the flaws within the WLAN encryption. Furthermore, the report will critically analyze the flaws within the 802.11 protocol and provide solutions to secure the wireless network. Finally, the report will analyze the most suitable security measures for this scenario and justify the recommendations.
Technical flaws – Bypassing WLAN authentication
Every access point within the wireless LAN has a network name that is called SSID. The SSID normally is an alphanumeric characters string between 1 to 32. The main purpose of setting up an SSID is to distinguish it from other access points. SSID is normally presented in the various frame types that are Re-association requests, Association requests, Prove responses, Probe requests, and Beacon [16]. Mostly SSID is presented in the beacon frame that is broadcast periodically by the access point within its coverage area. Therefore, within the beacon frame, SSID is required to set to zero to make it invisible. Hidden SSID permits users to hide the SSID of their wireless network to protect the network from hackers. It is accomplished by setting the SSID field to zero within the beacon frame. Therefore, the station is knowing the SSID of the access point to connect it with another access point in a closed network environment.
Most of the cyber attacker utilizes passive scanning to find the SSID of the network. IF the SSID is not set to zero the beacon is not switched off, the SSID of the access point within the Beacon frame is retrieved by passive scanning. When the beacon frame shows the null SSID, there is another way to bypassing WLAN authentication when SSID is hidden [15]. When an associate request comes from a legitimate user that contains the correct SSID, then, there will be also an associated answer frame. All the frame comprises a simple SSID, and in this way, an attacker can sniff the hidden SSID. By continuously testing the prove request it is also possible to steal the SSID and bypass the WLAN authentication.
Every device of the network has a physical address that is called a Media access control (MAC) address. By utilizing the various software package tools like aircrack-ng and Airodump-ng is it possible to bypass the MAC filtering [17]. Therefore, by installing these software packages it is possible to bypass the WLAN authentication when the administrators utilize MAC filtering.
Technical flaws – WLAN encryption flaws
WLANs comprise various network devices including access points and wireless stations and contain various important data. Therefore, in order to secure the network, the wireless network has utilized two types of encryption technology that are WEP and WPA2. The main objective of the wired equivalent privacy (WEP) in the 802.11 standards is to secure the confidentiality of user’s data from various types of eavesdropping [20]. Unfortunately, wired equivalent privacy has several inherent problems and it is unable to meet its security objectives. One of the significant weaknesses of the WEP is that key management is not identified in the WEP standard. Therefore, due to its interoperable key management, keys will tend to be of poor quality, and synchronization of keys is difficult. WEP utilizes an RC4 key that is weaker and makes it difficult to determine which key is difficult. Another flaw of the WEP is that authentication messages can be easily forged within it. Therefore, in order to overcome its disadvantages WPA 2 has been introduced.
WPA2 or Wi-Fi protected access 2 is the advanced version of WEP that utilizes an advanced encryption system instead of TKIP to provide more security to the network. therefore, WPA2 is a widely utilized encryption technique to encrypt the traffic of the wireless network [19]. Along with the several benefits, the WPA2 has some security flaws. WPA2 can be easily cracked by utilizing brute force dictionary techniques. By exploiting the KRACK (Key reinstallation attack), the attacker can easily inject malware into the network [18]. Therefore, the main security flaw of the WPA2 is the KRACK attack. Therefore, all the devices of the network require proper network security configuration to protect it from various kind of attacks.
Figure 1: TCP Flows in Wireshark
Figure 2: Packet Capturing in Wireshark
Figure 3: I/O graph in Wireshark
Both the above figure shows the TCP flows and packet capturing in Wireshark application. Wireshark application is mainly an analysis and packet sniffer tool that captures the network traffic and stores the traffic for analysis. Therefore, by utilizing the Wireshark application, it is easy to identify the WLAN encryption flaws.
Technical flaws – 802.11 client flaws
The WLAN contains of wireless access points and wireless stations. The Access points are the devices that delivers communication with the wired network and monitors the traffic of the network that connects with Ethernet distributed system [9] Therefore, the IEEE 802.11 based networks of WLAN have been deployed widely to deliver persistent access to Internet. The A’'s are critically deployed as majority of the clients in the small company can be in the areas of coverage within multiple access points. The clients always tend to have connected with the access points with a robust strength of signal. It results a poor throughput and overload access points to poor clients. The access points in certain hotspots area might become overloaded and the client’s throughput related with such AP gets dramatically drops [12]. Consequently, when any 802.11 client of the company will choose an AP in order to utilize for communication, he or she should initially validate to it before commencing further communication.
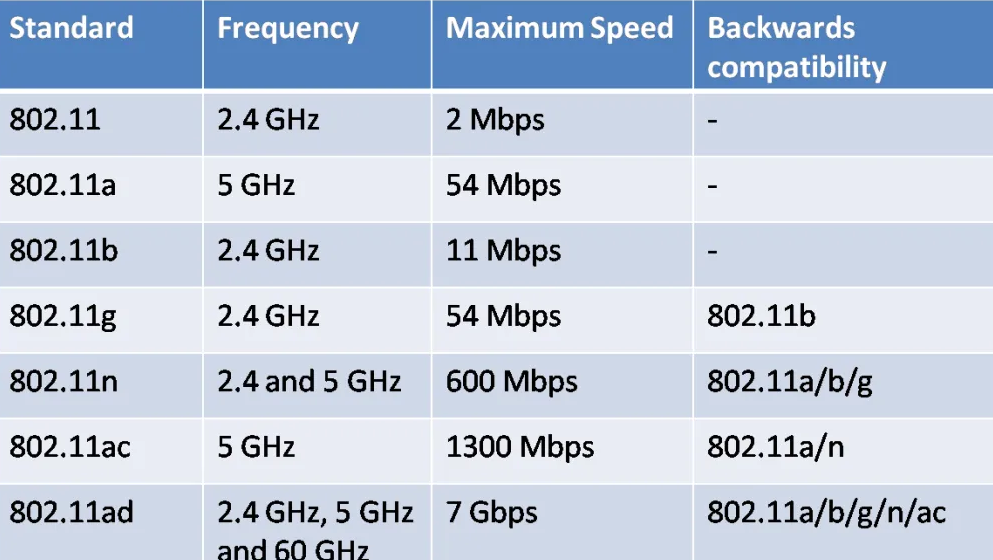
Figure 4: 802.11 wireless standard
Additionally, the portion of the legitimate network is a type of message, which permit the clients and AP to demand de-validate from each other overtly. Inopportunely, the message itself is not legitimate utilizing any input material [10]. Therefore, a hacker might spoof this particular message through either faking to be access point of client and directs it to another portion. The modern standard is the IEEE 802.11n, which was approved in the year 2009 through launching various new aspects like frame aggregation, channel bonding and multiple-input multiple-output (MIMO) [11]. However, in 802.11 WLAN, organizing access points becomes more hectic as the size of the frame, latest dimensions are required to be considered along with the gaps among highest attainable rate of data around 300 Mbps. The lowest compatible rate of data is around 1 Mbps, which is further extended [13]. The conventional strength of and Access point in the realization scheme might result in imbalanced load and inequity between clients. The load balance has been a significant objective of several planned schemes in the fiction.
When there is an increase in number of clients, the entire throughput reduced because of traffic backoffs and collisions [11]. The average throughput of network is reduced by 48.6 percent when the assessments are being conducted utilizing two clients. On the other hand, the while utilizing with 3 clients, the network throughput is 66.5 percent. Therefore, the 802.11 MAC layer integrates the functionality very identically in order to mitigate the issues particular to wireless networks, like coordinating access to radio media, joining and leaving networks and exploring the networks [14]. Hence, these are the technical flaws that emerge directly from additional functionalities and it could be extended by widely categorizing into media access and identity flaws.
Suitable security measures
In the given scenario of a small company allowing only its employees for accessing the network have to consider certain security measures to secure the network from the identified technical flaws. As the paper has identified three important technical flaws for WLAN, the network needs to be more secure to overcome the flaws. Therefore, the most effective method of protecting an 802.11 network is enabling the WPA2 as the organization’s security protocol rather than WEP [4]. WEP has multiple security vulnerabilities having a combination of MC filtering. Moreover, to make the WLAN of the small company more secure, it is recommended to use two hundred fifty-six bits for enabling the encryption, which is considered the strongest encryption at this time [6]. Furthermore, there the small company has to change its key periodically with the implementation of a strong password policy, which will increase the difficulty of the attacker’s attempt to exploit this thing [1].
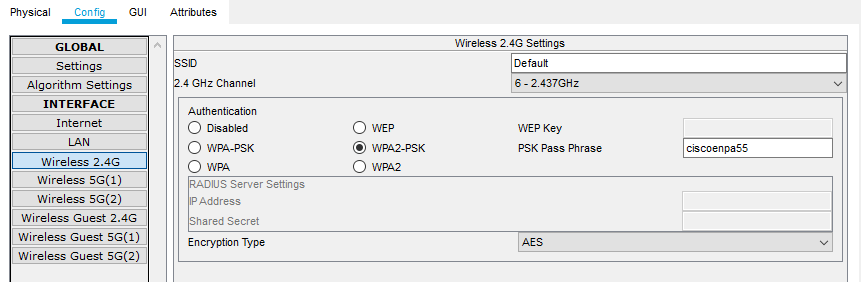
Figure 5: Securing network with password
Figure 6: Securing Router with password
As the small company is using wireless access points for providing wireless access to its staff, it is very significant to check the configuration settings to avoid exploitation of the possible vulnerabilities [3]. It is recommended to use separate administrator access for the configuration of the access points and running the firmware. Moreover, the default login credentials must be changed at the beginning to avoid tampering or unauthenticated access to the configuration settings [2]. So far, the only risk of using WPA2 encryption is password attacks, but it can be mitigated by implementing a strong password for the particular small company network. The significance of a complex password for WLAN is, therefore, cannot be underrated. The company can use a WLAN key having several characters as possible that will be case sensitive along with numbers and special characters [5]. The distribution of characters should be random that will make it more difficult to crack.
Justification of the choices
Through exploring several measures of security, the most effective way to secure the network of 802.11i is deploying WPA2 protocol rather than utilizing WEP. It is so because, WEP has various vulnerability issues in measuring the security evaluation with MAC filtering combination [7]. Additionally, 256 bits will be selected in this case, as this is the robust encryption of all. Moreover, there is also a possibility in shifting the keys intermittently that enhance the complexity while hackers attempt in invading the network [10]. Hence, it is actually evident that the recommendation that has been above mentioned are not adequate on its own in accomplishing a desired level of standard security.
Conclusion
The paper has discussed mainly three categories of technical errors that are linked with a wireless network, especially the protocols associated with the 802.11 standard. The first flaw that has been identified is bypassing the authentication while using a hidden SSID and using MAC filtering by the administrators. This is possible because of the shared secret key authentication that allows an external agent to discover the SSID through passive scanning. The second flaw is associated with the WEP and WPA2 encryption algorithm in which the WEP encryption algorithm can allow attackers to intercept the data. Moreover, the third flaw is associated with 802.11 clients. The report has also provided some security measures that need to be implemented by the small company to avoid exploitation of the flaws in the future.
References
[1]S. Suroto, "WLAN Security: Threats And Countermeasures", JOIV : International Journal on Informatics Visualization, vol. 2, no. 4, p. 232, 2018. Available: 10.30630/joiv.2.4.133.
[2]"Research Methods for Cyber Security", Network Security, vol. 2018, no. 6, p. 5, 2018. Available: 10.1016/s1353-4858(18)30053-9.
[3]Suroto, Suroto. "WLAN Security: Threats And Countermeasures." JOIV: International Journal on Informatics Visualization 2, no. 4 2018: 232-238.
[4]Kyaw11, Ar Kar, Zhuang Tian, and Brian Cusack. "Wi-Pi: a study of WLAN security in Auckland City." IJCSNS 16, no. 8 2016: 68.
[5]Li, June, Kai Yuan, Liang Zhou, Lifang Han, Ling Li, Zhihao Wang, Yinbin Liu, and Wenbin Huang. "A detection method of WLAN security mechanisms based on MAC frame resolution." Wuhan University Journal of Natural Sciences 22, no. 2 2017: 93-102.
[6]Alblwi, Samia, and Khalil Shujaee. "A survey on wireless security protocol WPA2." In Proceedings of the International Conference on Security and Management (SAM), pp. 12-17. The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp), 2017.
[7] Alblwi, Samia, and Khalil Shujaee. "A survey on wireless security protocol WPA2." In Proceedings of the International Conference on Security and Management (SAM), pp. 12-17. The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp), 2017.
[8] Chyrun, Lyubomyr, Liliya Chyrun, Yaroslav Kis, and Lev Rybak. "Information System for Connection to the Access Point with Encryption WPA2 Enterprise." In International Scientific Conference “Intellectual Systems of Decision Making and Problem of Computational Intelligence”, pp. 389-404. Springer, Cham, 2019.
[9] Rybak, Lev. "Information System for Connection to the Access Point with Encryption WPA2 Enterprise." In Lecture Notes in Computational Intelligence and Decision Making: Proceedings of the XV International Scientific Conference “Intellectual Systems of Decision Making and Problems of Computational Intelligence”(ISDMCI'2019), Ukraine, May 21–25, 2019, vol. 1020, p. 389. Springer, 2019.
[10] Martin, Alexander, Basiru Mohammed, and Rajkumar Ramadhin. "WEP VS WPA2 Encryptions." (2019).
[11] Raza, Muhammad Aleem, Muhammad Kamran, and Junaid Akbar. "A Survey on Wireless Security protocols (WEP, WPA and WPA2)."
[12] Carvalho, José Pacheco de, Hugo Veiga, and Cláudia Ribeiro Pacheco. "Performance Research on IEEE 802.11 a 54 Mbps WPA2 Laboratory Links." In WCE 2019-World Congress on Engineering 2019, pp. 571-576. Newswood Limited, 2019.
[13] Sadeghi, Rasool, João Paulo Barraca, and Rui L. Aguiar. "A survey on cooperative MAC protocols in IEEE 802.11 wireless networks." Wireless Personal Communications 95, no. 2 (2017): 1469-1493.
[14] Dasari, Mallesham. "Real time detection of MAC layer DoS attacks in IEEE 802.11 wireless networks." In 2017 14th IEEE annual consumer communications & networking conference (CCNC), pp. 939-944. IEEE, 2017.
[15] Akram, Zeeshan, Muhammad Anwaar Saeed, and Marriam Daud. "Real time exploitation of security mechanisms of residential WLAN access points." In 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), pp. 1-5. IEEE, 2018.
[16]Mishra, Abhishek. "Method, system and apparatus for policy based authorization and authentication of data traffic bypassing mobile network." U.S. Patent Application 15/768,727, filed October 25, 2018.
[17] Fikriyadi, Fikriyadi, Ritzkal Ritzkal, and Bayu Adhi Prakosa. "Security Analysis of Wireless Local Area Network (WLAN) Network with the Penetration Testing Method." Jurnal Mantik 4, no. 3 (2020): 1658-1662.
[18] Pandikumar, T., and Mohammed Ali Yesuf. "Wi-Fi Security and Test Bed Implementation for WEP and WPA Cracking." International Journal of Engineering Science 13571 (2017).
[19]Agbeboaye, Clement, France O. Akpojedje, and Joshua Okoekhian. "SECURITY THREATS ANALYSIS OF WIRELESS LOCAL AREA NETWORK." Compusoft 7, no. 6 (2018): 2773-2779.
[20] Dimitrova, Vesna, and Stefan Pavlov. "A Note on a Successful WEP Attack." (2020).












