Penetration Testing Assignment: Comparison Of PT Methods
Question
Task:
Assignment Brief
This is an individual assessment comprised of two tasks. Task 1 and task 2 carry 50% respectively of the overall portfolio mark. Task 1 will assess your understanding of the statutory and ethical issues surrounding penetration testing and also assess your understanding of the process itself. Task 2 will assess your ability to conduct a full-scale penetration test. You are expected to demonstrate an insight into the implications of the problem introduced in each task by using clear and concise arguments. You will receive formative feedback as part of the module to demonstrate how to be concise in your written work. Please ensure, in completing these tasks you deploy the techniques you have been taught. If you produce work that is not concise and to the point, then marks may be reduced. The reports should be well written (and word-processed), showing good skills in creativity and design. Sentences should be of an appropriate length and the writing style should be brief but informative.
Task 1 – SOP for PenTesting
Task 1 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to undertake research and critically compare the published penetration testing methodologies. You are expected to comment on the statutory and ethical considerations of a penetration tester. You are expected to design/develop a Standard Operating Procedure (SOP), including a decision-making tree, to describe how you will undertake task 2. In particular: intelligence gathering (target profiling), vulnerability identification and analysis, and target exploitation (including post exploitation). An SOP is defined as a set of step-by-step instructions compiled by an organisation to help workers carry out routine operations.
Task 2 – Penetration Test
Task 2 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to conduct a penetration test against a target system that will be provided to you. You are required to present your findings in a factual manner to convince decision makers of a large corporation on business strategies.
Answer
Overview
The research on present penetration testing assignment depicts that as cyberattacks increased; companies began to focus on the safety test of their software applications moreover products. PT is a widely used and most common method to recognize the vulnerable area in the system. It also involves a deliberate attack on a system to recognize a weak area, which might provide a channel for unauthorized or malicious users to attack the system or change its accuracy and integrity. This technology helps to fix various safety errors and vulnerabilities. The main function of this report is to strictly compare the different penetration testing (PT) methods that provide possible solutions. And design and develop standard operating procedures, then the decision tree for task 2. Besides, statutory precautions as legal and ethical considerations for penetration testers will be disclosed.
Background
Penetration testing explored in the penetration testing assignment (also recognized as pen testing) is an assumed cyber-attack on a system of the computer to check for exploitable vulnerabilities. In the context of web-based application safety, PT is often using to enhance a WAF. Pen tests may involve attempts to disrupt some application systems (for example, application protocol interface (API), back-end/front-end servers) to discover vulnerabilities, for example, unfiltered input that is vulnerable to code injection attacks. Penetration testing provides insights that can be utilized to fine-tune your WAF safety policies moreover patch detected vulnerabilities.
PenTest Methodology Comparison
Information System Security Assessment Framework (ISSAF)
ISSAF is the framework illustrated in the penetration testing assignment that supports the concept of PenTesting. ISSAF was developed by OISSG and no longer exists in the existing security practice structure. As the name suggests, the ISSAF framework is completely open-source and can be adopted by any organization seeking security measures. The purpose of the framework is to provide a step-by-step approach to PenTest and use the PenTesting tools separately (Bompard et al., 2009). Also, the ISSAF framework defines basic guidelines for planning PenTesting for specific software through three phases, which include planning and preparation, evaluation and reporting, cleanup and destruction of artifacts ("Ethical Hacker: Introduction" nd). At each stage, PenTester knows how to break down the process into three stages (Klíma, 2016).
Open Source Security Testing Methodology Manual (OSSTMM)
OSSTMM existed when the Institute for safety or Open Methods was launched in 2000. The framework is completely open-source and peer-reviewed by other students in the community. In addition, multiple versions of the same framework have been introduced to show where PenTesting applies to organizations. Also, OSSTMM demonstrated a method for solving distributed vulnerability detection systems inside wireless and intranet networks through different international practices (Tryfonas et al., 2007). Therefore, the framework is suitable for exploring problems that occur on wireless networks and online computer networks. However, it is based solely on auditing resources to protect company assets from vulnerabilities and ignores tools or methods for measuring network security. The OSSTMM and ISSAF PenTesting methods are completely different, as previously mentioned the focus is on the stage of PenTesting for security vulnerabilities (Caceres & Zettsu, 2014).
Building Security in Maturity Model (BSIMM)
The building maturity security model is a study of presented software safety measures. By quantifying the practice of several different associations; we describe what is common to many organizations and the changes that make every organization unique. BSIMM is neither a manual nor a one-size-fits-all prescription. Rather, it reflects software security.
The result is a descriptive model that represents the discovery of this data and provides a baseline for software security activities for an organization. In addition, it is also noted herein penetration testing assignment that the model continues to evolve as the complexity and importance of the security landscape continues to increase. Collect and analyze new data from new community organizations and mature members (Da Veiga & Eloff, 2010).
Metasploit (MSF)
The Metasploit framework is a modular penetration testing platform depends on Ruby that allows you to test, write, or perform exploit code. The metasploit framework includes a set of tools that used to test safety vulnerabilities, enumerate the network, perform attacks, furthermore evade findings. MSF console is the frequent interface utilized with Metasploit framework. The console allows you to perform things such as exploit vulnerabilities, scan targets, and collect data. MSF console is possibly the most famous interface for the Metasploit Framework (MSF).
Open Web Application Security Project (OWASP):
The OWASP is online communities that provide articles, technologies, tools, documentation, and methods that are freely available in a field of Web application safety. OWASP is a non-profit foundation dedicated to improving software safety (Goswami et al., 2012). Throughout the community-led open-source software project, hundreds of local chapters globally, tens of thousands of members, moreover leading training and education conferences, OWASP Foundation is a source for technicians and developers to protect cybersecurity.
- Resources and Tools
- Networks and Communities
- Training and Education
Penetration Testing Execution Standard (PTES):
The Penetration Test Execution Standard is a penetration testing technique develops by a group of Data safety practitioners to meet the needs for complete moreover update standards in penetration test (Hema Shankari & Thirumalai Selvi, 2017). Additionally to mentoring safety professionals, it attempts to provide companies with the information they must suppose from penetration testing as well as guide them in negotiating and identifying successful projects.
PTES procedure:
PTES describe penetration testing in seven major sections as illustrated below within the penetration testing assignment:
- Interaction before interaction: This is a preparation stage for a pen test. It's all about the tools required for document approval and testing.
- Intelligence gathering: At this stage, data about the target system is collected from external sources (such as official records, social media sites). This stage belongs to Open Source Intelligence.
- Threat modeling: It is the process of optimizing network safety by recognizing vulnerabilities and goals furthermore then defining countermeasures to mitigate or prevent the impact of system risks. It’s skipped in a typical translation test.
- Vulnerability analysis: Vulnerabilities are discovered and verified at this stage, which is the threat that an attacker could gain and exploit approved access to application or system.
- Development: At this stage, testers attempt to use previously identified and verified vulnerabilities to achieve the security of the target system.
- After development: This stage maintains control of the target system and collects data.
- Report: Document the entire process in a form that customers can understand. Report on the security of the target system.
Wireshark
The penetration testing assignment examines that Wireshark is a free or open-source packets analyzer. It’s used for analysis, network troubleshooting, communication and software protocol development, or training. Because of trademark issues, the project was named Ethereal, although it was named Wireshark in May 2006. Its cross-platform, utilizes the current version of the Qt widget toolkit to execute its user's interface, or uses a pcap to capture packet (Klíma, 2016).
Kali Linux
For many years, Kali inherited the default root user guidelines from BackTrack. As a part of our evaluation of Kali strategies and tools in the current penetration testing assignment, we decided to change this or move Kali to the "legacy default non-root user" model. This change will be a division of 2020 Releases, which is presently planned for release in late January. Nevertheless, from now on, you will notice this change in the weekly image. Kali Linux is the Debian-derived Linux distribution design for penetration testing and digital forensics (Shamala et al., 2013). It’s funded and maintained by Offensive safety Ltd. KaliLinux has 600 PT programs pre-installed, including Nmap, Wireshark, Armitage, John Ripper code word cracker, Aircrack-ng Software Suite for WLAN Penetration Testing), Burp Suite furthermore OWASP ZAP Web Application safety Scanner.
What is the statutory and legal Consideration of a penetration tester discussed in the context of penetration testing assignment?
There are a lot of different kinds of pen tests. Vulnerable software code reviews can be a part of the pen tests. A ping scan can be a component of the pen test. Detection or exploitation Configuration review
Computer crime law like 18 USC 1030 considered in the context of penetration testing assignment criminalizes unauthorized or unauthorized access and attempts to access a computer network. The people who constitute "authorization" and those who can approve such access rapidly become confused. So when security expert Scott Moulten wanted to connect his network to the county network for which Moulten is providing e911 services, they ran a pen test on the security of Georgia cities. Moulten conducted port scans or throughput tests on the city network to observe if the computer was vulnerable. When Moulten ports scan bare important vulnerability he reported those vulnerabilities to his employers as well as his client counties (Silic, 2013). The regulation makes computers use a felony, and its purpose is to "interfere, interrupt, and in some way interfere with utilize of computer programs or data ... no matter how long change, damage, and malfunction lasts."
Likewise, Stefan Puffer, Houston-based computer safety consultant, and Harris County Central Technical Department chief furthermore a reporter for Houston Chronicle conducted a "War Driving" exercise. Puffer proved the Harris County Clerk's 802.11b network was misconfigured, making it accessible to anybody. Puffer claims to have stopped exercising after seeing a misconfiguration (Sönmez, 2019).
The following authorized considerations provided in the penetration testing assignment must be followed in the documentation provided between the organization and the PT provider.
- Territory boundary legislation: Companies and penetration testers should identify which region or territory boundary legislation must be followed before signatures and documents and exchanges.
- "Get out of prison" statement: A "get out of jail" statement was written in a document in which the organization fully authorized penetration testers to exploit the vulnerability.
- Scope of work: The scope of work stated in the context of penetration testing assignment uses a few parameters (for example the number of networks, subnets, IP addresses, as well as computers) to determine why a penetration test is performed inside the organization.
Standard Operating Procedure
1. Purpose: 2. Overview: 3. SCOPE OF WORK: 4. DEFINITION: 5. RESPONSIBILITIES: The specific responsibilities of penetration testers vary by employer. However, all penetration testers have some common core tasks, such as: Ø Test the network and applications Ø Physical security assessment Ø Conduct a security audit Ø Analyze security policies Ø Write a safety assessment report Ø Specific procedures: Penetration testing will be performed in this procedure method using two test principles. External testing Internal testing Targeted testing |
Decision-Making Tree for Task 2
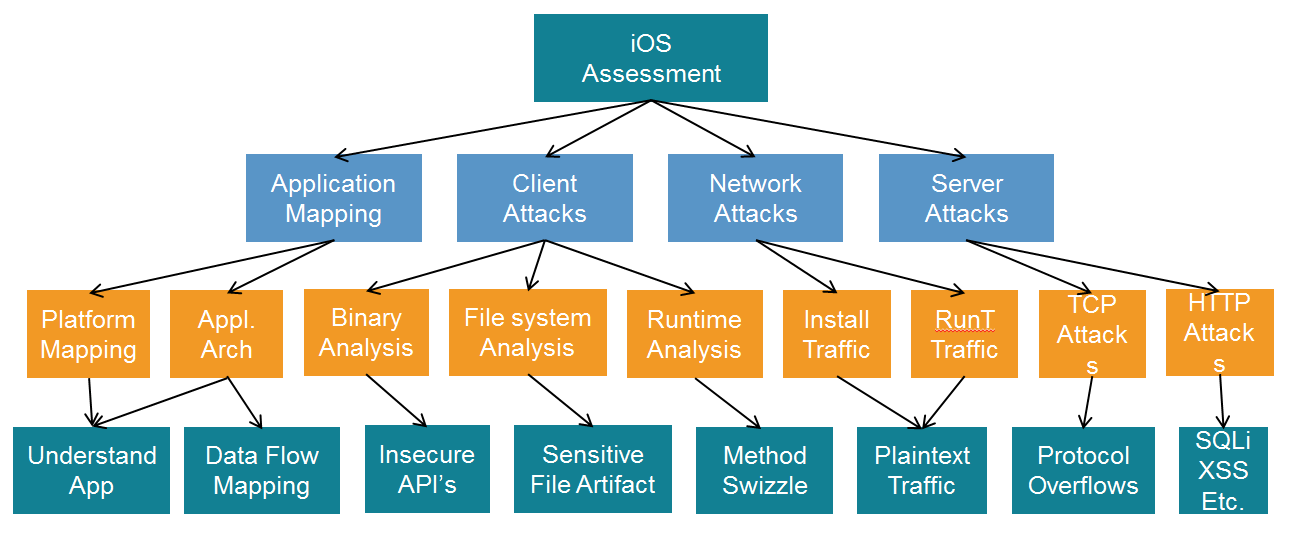
Image: Preparing the security testing plan
Image Source: techbeacon.com
References
Bompard, E., Napoli, R., & Xue, F. (2009). Assessment of information impacts in power system security against malicious attacks in a general framework. Reliability Engineering & System Safety, 94(6), 1087-1094. https://doi.org/10.1016/j.ress.2009.01.002
Caceres, G., & Zettsu, K. (2014). Provenance-Based Security Risk Assessment Framework. Penetration testing assignment Journal Of Information Processing, 22(4), 617-625. https://doi.org/10.2197/ipsjjip.22.617
Da Veiga, A., & Eloff, J. (2010). A framework and assessment instrument for information security culture. Computers & Security, 29(2), 196-207. https://doi.org/10.1016/j.cose.2009.09.002
Goswami, S., Krishnan, N., Verma, M., Saurabh Swarnkar, S., & Mahajan, P. (2012). Reducing Attack Surface of a Web Application by Open Web Application Security Project Compliance. Defence Science Journal, 62(5), 324-330. https://doi.org/10.14429/dsj.62.1291
Hema Shankari, K., & Thirumalai Selvi, R. (2017). Methodology for regression testing with open source tool. International Journal Of Engineering & Technology, 7(1.1), 133. https://doi.org/10.14419/ijet.v7i1.1.9212
Klíma, T. (2016). PETA: Methodology of Information Systems Security Penetration Testing. Acta Informatica Pragensia, 5(2), 98-117. https://doi.org/10.18267/j.aip.88
Shamala, P., Ahmad, R., & Yusoff, M. (2013). A conceptual framework of info structure for information security risk assessment (ISRA). Penetration testing assignment Journal Of Information Security And Applications, 18(1), 45-52. https://doi.org/10.1016/j.jisa.2013.07.002
Silic, M. (2013). Dual-use open source security software in organizations – Dilemma: Help or hinder?. Computers & Security, 39, 386-395. https://doi.org/10.1016/j.cose.2013.09.003
Sönmez, F. (2019). Security Qualitative Metrics for Open Web Application Security Project Compliance. Procedia Computer Science, 151, 998-1003. https://doi.org/10.1016/j.procs.2019.04.140
Tryfonas, T., Sutherland, I., & Pompogiatzis, I. (2007). Employing penetration testing as an audit methodology for the security review of VoIP. Internet Research, 17(1), 61-87. https://doi.org/10.1108/10662240710730506
?????, ?., ?????, ?., & ????????, ?. (2019). Functional model of SOC maturity assessment based on a maturity model. Penetration testing assignment Ukrainian Information Security Research Journal, 21(3). https://doi.org/10.18372/2410-7840.21.13954












