Risk Management Assignment: Discussion On Steganography & Access Control Lists
Question
Task:
Assessment Details:
This risk management assignment is designed to assess your technical skills in investigation IS security, risk threats and management to an organization. The assessment is also assessing your skills to evaluate risk management techniques and IS auditing. You are required to select an organization that uses information systems to perform daily business operations. You have to identify the most valuable assets for the organisations and investigate the security threats and mitigation techniques. You have also to propose/evaluate the risk management techniques adopted by the selected organization to ensure the reliability, confidentiality, availability, and integrity. You have also to discuss audit plan and processes used by the organization and investigate the impact of human factors on security and risk management.
Task Specifications:
This assessment includes three tasks as follows:
Task-1:
Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. Use Steghide tools available in Kali Linux/Linux to hide a text file that includes your group students’ names and IDs on audio file. You have first to create audio file with no more than 30 second to record your group student’s names only. Then, you have to create text file to include group details include names and student IDs. Finally, use Steghide tools (use APIC as passphrase) to embed your text file into the created audio file.
In your report, you have to provide screenshot demonstrate the steps with the commands you followed during the process of installation of Steghide, and the way use used to hide group information text file into audio file and finally the steps to extract the text file from audio for verification of your work.
Task-2:
Access control is granting or denying approval to use specific resources. Technical access control consists of technology restrictions that limit users on computers from accessing data. In this project you have to work in a group to understand Access Control List (ACL) and files system security using Linux environment. You have to complete the tasks using kali Linux or any Linux OS.
In your report, you have to provide screenshot to demonstrate the steps you followed during the process of conducting the assignment tasks requirements according to your group student IDs, first name and last name.
Task-3:
Discuss with clear demonstration, how the Steganography and access control list techniques that you conducted in Task-1 and Task-2, respectively, can achieve confidentiality, integrity, and availability (CIA). You have to provide justification during your discussion.
Answer
Introduction to the context of risk management assignment
There are numerous advancements that are being made in the field of technology. With these advancements, there is also a significant rise in the frequency of the security risks and attacks that is evident. Numerous tools and techniques are developed so as to control and mitigate the security attacks. Steganography and Access Control Lists, ACLs are discussed and explored through the tasks covered below. For Steganography, the Steghide tool is used and the detailed steps are shown.
Task 1
The first step was to install steghide. In order to install steghide, a few package dependencies needed to be updated (Hameed 2015). This was done on the terminal as follows:
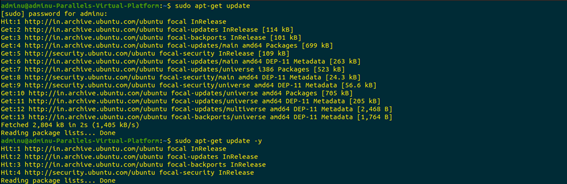
In the next step, Steghide was installed
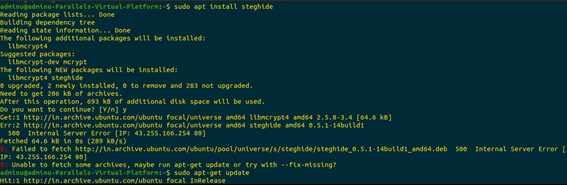
However, as can be seen above, there was an issue with the installation.
So, with an additional command as suggested by Steghide was executed in order to fix the installation.
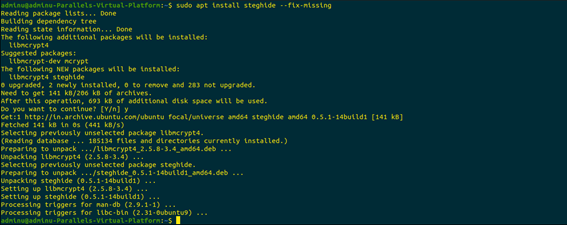
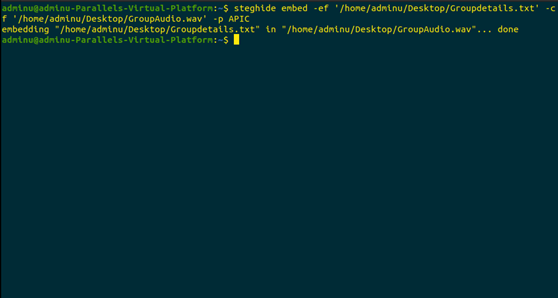
The following text file will now be embedded into the pre-recorded audio file.
The embedding was successful and virtually the embedding did not add any weight to the Audio file and it also plays successfully.
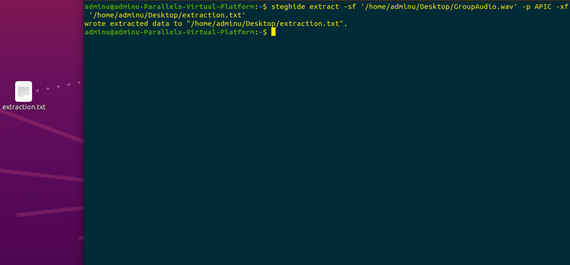
Once the file was embedded, it was also later then extracted to see if the operation works. The below output is the successful result of the extraction (Kolakalur, Kagalidis&Vuksanovic 2016).
Task 2
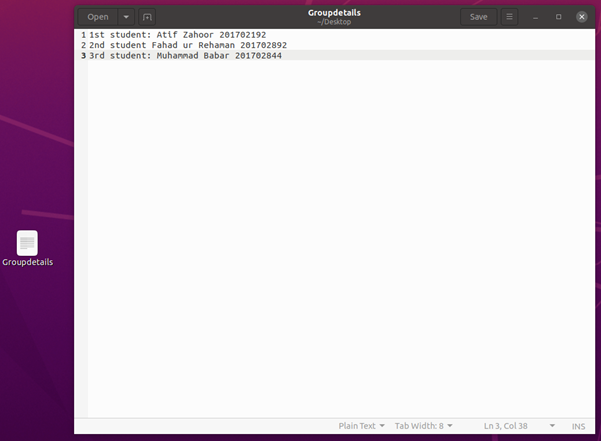
Task 2.1
|
Serial |
Student ID |
First Name |
Last Name |
|
1st |
201702192 |
Atif |
Zahoor |
|
2nd |
201702892 |
Fahad ur |
Rehaman |
|
3rd |
201702844 |
Muhammad |
Babar |
Task 2.2
|
Task needed |
Terminal commands |
|
Create directory named APIC |
Mkdir APIC |
|
Set full access to APIC directory |
Sudochmod744 APIC |
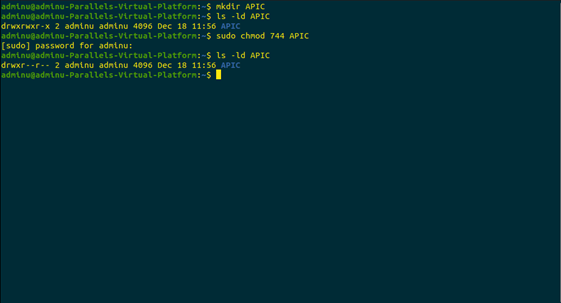
As can be seen from the below screenshot, first the directory of APIC was created using the command. Then its access permissions were changed using the command listed above. With this command, the owner has read, write and execute access to the directory whereas Group and others have read access only.
Task 2.3
|
Directory creation |
Commands |
|
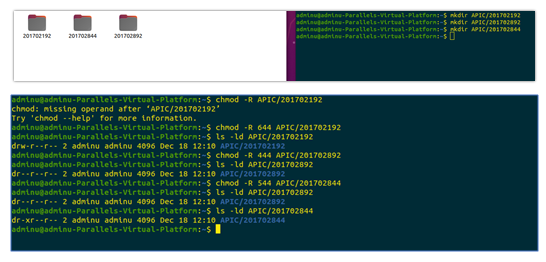
Directory created (ID1) |
mkdir APIC/201702192 |
|
Set read and write access permission only |
chmod -R 644 APIC/201702192 |
|
Directory created (ID2) |
mkdir APIC/201702892 |
|
Set read access permission only |
chmod -R 444 APIC/201702892 |
|
Directory created (ID3) |
mkdir APIC/201702844 |
|
Set read and execute permission only |
chmod -R 544 APIC/201702844 |
Task 2.4
|
Task details |
Terminal Commands |
|
Create user (Firstname1) |
sudoadduseratif |
|
Full permission to ( ID1) |
setfacl -m u:atif:rwx APIC/201702192 |
|
Read and write permission to ( ID2) |
setfacl -m u:atif:rw APIC/201702892 |
|
Read permission only to other directories |
setfacl -m u:atif:r /home/ |
|
Create user (Firstname2) |
sudoadduserfahad |
|
Full permission to ( ID2) |
setfacl -m u:fahad:rwx APIC/201702892 |
|
Read and write permission to ( ID1) |
setfacl -m u:fahad:rx APIC/201702192 |
|
Read permission only to other directories |
setfacl -m u:fahad:r /home/ |
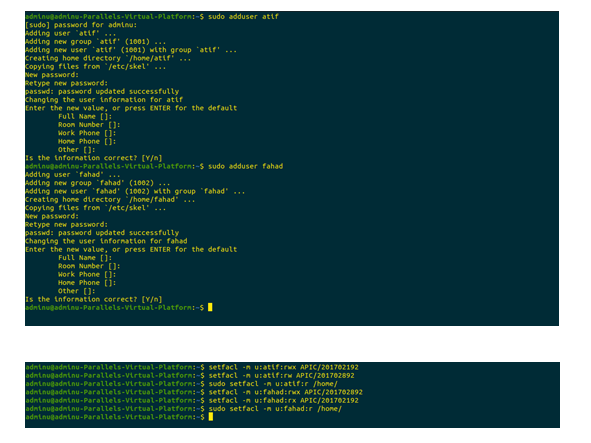
Task 2.5
Below screenshot depicts the total number of users created and their names.
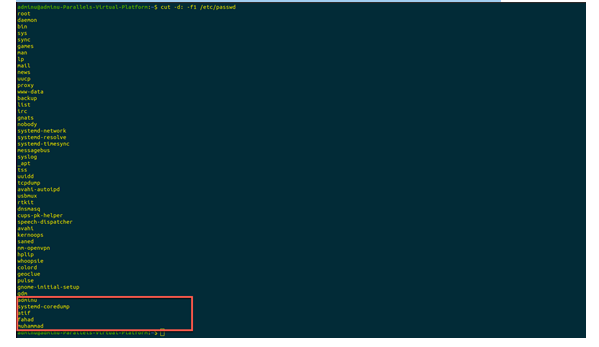
The below screenshot depicts all of the groups currently active in the system
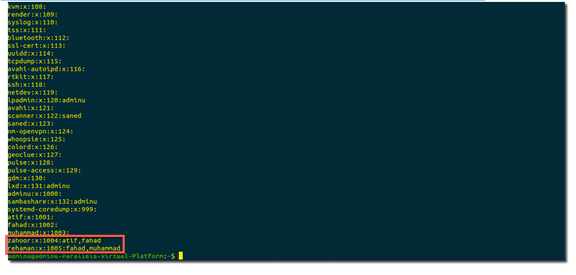
|
Task Details |
Terminal Commands |
|
Creation of the group (Lastname1) |
sudoaddgroupzahoor
|
|
Adding the (firstname1) as well as (firstname2) tothe (lastname1) group |
sudoadduseratifzahoor sudoadduserfahadzahoor |
|
The group users of (Lastname1) group would get full access to the directory ( ID1) and then only read access to directory (ID2) |
setfacl -R -m g:zahoor:rwx APIC/201702192 setfacl -R -m g:zahoor:r APIC/201702892 |
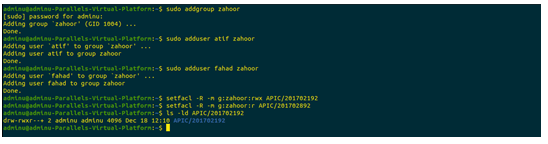
|
Task Details |
Terminal Commands |
|
Creation of the group (Lastname2) |
sudogroupaddrehaman |
|
Addition of the (firstname2) as well as (firstname3) to the (lastname2) group |
sudoadduserfahadrehaman sudoaddusermuhammad sudoaddusermuhammadrehaman |
|
Now, all of the users from the (Lastname2) group will get full access to directory (ID2) and read access to directory (ID1) |
setfacl -R -m g:rehaman:rwx APIC/201702892 setfacl -R -m g:rehaman:r APIC/201702192 |
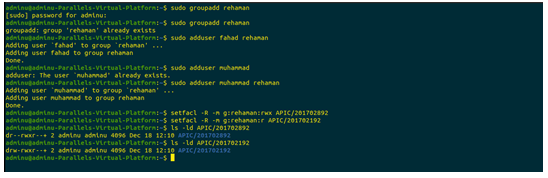
Task 3
Steganography is the technique that involves the use of different methods and mechanisms to hide certain information pieces in the regular data transmission process. There are various techniques that are used to carry out Steganography(Mahima, Siddiqa& Sardar 2019). The technique works in such a manner that the information is hidden without causing any unwanted suspicion. One of the most commonly used techniques is Least Significant Bit, LSB. As the name suggests, the LSB of a media file is used to embed the information that is to be kept hidden during the transmission. For instance, the image files involve pixels that are composed of the three data bytes for the color codes. There is also an additional byte that may be included to represent transparency. The LSB technique changes the last bit of these bytes in the image file to hide the data in one bit. The large information chunk can be kept hidden and transmitted in such a manner (Rahman 2018). This is because changing the last bit of the pixel value does not lead to any major visible changes. It is not possible for a person to view the normal and the steganographic image to spot the difference. The same methodology can be applied in the other digital media files, such as audio or video files. Another technique that is used for Steganography is the substitution technique. It includes the letter or word substitution to hide the information and transmit the same. The embedding technique is also used wherein the data is embedded in the header section of the data packet. All of these make it difficult to detect such hidden information (Shahi 2020).
In the above tasks, the use of Steghide tool is performed to carry out the Steganography and hide the information. There are numerous features that the Steghide tool comes with. There are varied file formats that the tool is compatible with leading to the improved capabilities for the end-users. The information extraction cannot be performed without the tool which can be a limitation with the involvement of the Steghide tool.
Another significant technique that is used in the network and information security is Access Control Lists. These are usually referred as ACLs and are used with the Linux environment and systems (Yadav, Sharma & Arora 2018). The users can have different rights and access permissions in Linux. These are proudly classified in three categories as read, write, and execute. It is important that the access is controlled and properly monitored to ensure that there is no unauthorized access involved at any instance. The ACLs are utilized to grant, modify, and control the access and permissions (Lopriore 2016). These provide an edge over the usual methods of access control as the complex situations and problems can also be managed through the ACLs. The use of the ACL technique can be spotted in the tasks above.
The traditional file permission system and concept may not be suitable in all the access control requirements. The ACLs can be involved in these cases and these enable the allocation or the permissions to the users or the groups. It is not necessary that these users or the group correspond to the original owner or the owing group involved. ACLs are the feature of the Linux kernel and can be used at the application level to manage and control the complex permission concepts. There are various scenarios and situations wherein the ACLs can be used for effective access control and management (Hafizhan, Wahyuddin&Komalasari 2020). Some of these include the replacement of the operating system or server, such as Windows server to be replaced with the Linux server.
The Steghide tool and the ACLs are applied in the tasks above to showcase the different aspects of the information and network security.
Conclusion
It is essential that the techniques and measures are followed to keep the information sets and the network channels secure from the security violations and privacy attacks. The two techniques, Steganography and Access Control Lists, ACLs are explored in the tasks executed. There are several other sub-concepts and techniques under these two methods which can be analyzed and explored in the future.
References
Hafizhan, M, Wahyuddin, MI &Komalasari, RT 2020, ‘Implementasi Packet Filtering MenggunakanMetode Extended Access Control List (ACL) Pada Protokol EIGRP’, JURNAL MEDIA INFORMATIKA BUDIDARMA, vol. 4, no. 1, p. 185.
Hameed, AS 2015, ‘Hiding of Speech based on Chaotic Steganography and Cryptography Techniques’, International Journal of Engineering Research, vol. 4, no. 4, pp. 165–172.
Kolakalur, A, Kagalidis, I &Vuksanovic, B 2016, ‘Wavelet Based Color Video Steganography’, International Journal of Engineering and Technology, vol. 8, no. 3, pp. 165–169.
Lopriore, L 2016, ‘Access control lists in password capability environments’, Computers & Security, vol. 62, pp. 317–327.
Mahima, N, Siddiqa, N & Sardar, TH 2019, ‘Multi-Layered Security System Using Cryptography and Steganography’, risk management assignment International Journal of Innovative Research in Computer Science & Technology, vol. 7, no. 2, pp. 8–11.
Rahman, SA 2018, ‘A comparative analysis of image steganography based on DCT algorithm and steganography tool to hide nuclear reactors confidential information’, Computers & Electrical Engineering, vol. 70, pp. 380–399.
Shahi, D 2020, ‘Reversible Steganography for RGB Images Using Image Interpolation’, Journal of Advanced Research in Dynamical and Control Systems, vol. 12, no. 3, pp. 41–49.
Yadav, SK, Sharma, K & Arora, A 2018, ‘Security Integration in DDoS Attack Mitigation Using Access Control Lists’, International Journal of Information System Modeling and Design, vol. 9, no. 1, pp. 56–76.












