Need Of SOP In Penetration Testing Assignment
Question
Task:
This is an individual assessment comprised of two tasks. Task 1 and task 2 carry 50% respectively of the overall portfolio mark. Task 1 will assess your understanding of the statutory and ethical issues surrounding penetration testing and also assess your understanding of the process itself. Task 2 will assess your ability to conduct a full-scale penetration test. You are expected to demonstrate an insight into the implications of the problem introduced in each task by using clear and concise arguments. You will receive formative feedback as part of the module to demonstrate how to be concise in your written work. Please ensure, in completing these tasks you deploy the techniques you have been taught. If you produce work that is not concise and to the point, then marks may be reduced. The reports should be well written (and word-processed), showing good skills in creativity and design. Sentences should be of an appropriate length and the writing style should be brief but informative.
Task 1 – SOP for PenTesting
Task 1 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to undertake research and critically compare the published penetration testing methodologies. You are expected to comment on the statutory and ethical considerations of a penetration tester. You are expected to design/develop a Standard Operating Procedure (SOP), including a decision-making tree, to describe how you will undertake task 2. In particular: intelligence gathering (target profiling), vulnerability identification and analysis, and target exploitation (including post exploitation). An SOP is defined as a set of step-by-step instructions compiled by an organisation to help workers carry out routine operations.
Task 2 – Penetration Test
Task 2 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to conduct a penetration test against a target system that will be provided to you. You are required to present your findings in a factual manner to convince decision makers of a large corporation on business strategies. Do not provide a narrative of your intelligence gathering activities in the main report. You should include this in an appendix. You can use the VPN for undertaking this activity.
Answer
Introduction
The concept of Pentesting examined in the proposed penetration testing assignment is considered as security assessments, progressions and analysis on applications of mobile, web or API. The pen-testing is defined to penetrate the application and network security for reducing vulnerabilities. Pentest by SOP is the significant process by engaging the high standards of information gathering and routine operation. An SOP is a systematic process that is set to carry out the routine applications through pentest. The task covered in the penetration testing assignment will highlight the need of SOP in pentest methodology. It is significant to identify the steps of identifying the SOP and framework for following the effectiveness of pentest methodologies. Statutory and legal comparison is executed to analyze the penetration tester for SOP and decision-making designs. The study will shed light on defining the methodological approaches for pentest.
Task 1 – SOP for PenTesting
PenTest Methodology Comparison
Pentest or penetration testing can be widely delivered to update and provide standards against cybersecurity vulnerabilities. With increased cyber attacks, it is significant to engage the techniques regarding identifying vulnerable areas within the system (Shapiro and Stefkovich, 2016). Moreover, there are several methodologies of pentest such as OSSTMM, OWASP, NIST, PTES, ISSAF and others. In a study by Niek Jan van den Hout, the OSSTMM framework is considered as the most used standards of pentest methodology. This methodology explored in the sections of penetration testing assignment is effective to determine and provide the scientific way to penetrate the vulnerabilities in the system (Van den Hout, 2019). It is significant to enhance the potential angles of attacks by applying this methodology (Archibald and Renaud, 2019).
This methodology relies on interpreting the vulnerabilities within the network. Unlike other methodologies, this is created to support the team to execute the security manual and network development. On the other hand, in another study by Aileen G. Bacudio, Xiaohong Yuan, Bei-Tseng Bill Chu, Monique Jones, it has been mentioned that OWASP methodology is executed to recognize the well-versed community in the industry (Bacudio et al., 2011). Open Web Application Security Project methodology has the purpose of developing the curb application vulnerabilities within the network security. This methodology discussed in the penetration testing assignment is different from OSSTMM as this is applied only to identify the vulnerabilities that are not commonly found within mobile or web. This methodology helps to penetrate the logical flaws and controls in modern applications with better-equipped security.
Unlike the security manuals, Niek Jan van den Hout, stated that the NIST methodology guides the penetration testers for following the path (Van den Hout, 2019). It provides the recent versions for various regulatory frameworks for American providers. It guarantees security in different industries such as communication, banking and energy. As contradicted by Archibald and Renaud (2019), NIST has a specific factor to collaborate with Cybersecurity Framework in American industries. It can be compared with OSSTMM that it is not able to interpret the network following and security standards in information management. Equally, OWSAP is not able to implement the framework as NIST does. Moreover, PTES highlights the testers to structure the penetration test.
It is significant to enhance and gather information regarding modelling phases while preparing penetration testing assignment. Through this methodology, post-exploitation testing is necessary regarding guaranteeing the standards to make decisions. As argued by Kshetri (2017), this methodology is different from others as it is used to attempt the practical delivering and vulnerabilities. Practical recommendations are managed to make proper decisions in pen-testing. ISSAF is another methodology illustrated in this segment of penetration testing assignment that is used to specialize in the penetration test. It caters to plan and combine the steps for influencing the penetration testing significantly (Archibald and Renaud, 2019). It is a crucial methodology than PTES and NIST as each step is combined with considering the complementary information as a particular tool.
Statutory and legal consideration of a penetration tester
According to Vega et al. (2017), it is noted in the penetration testing assignment that penetration testing is a security method that should be considered as ethically and legally for cyber and security posture. Security snapshot can be assessed to analyze the level assessments with statutory and legal considerations of the penetration tester. As there are different types of pentests, it is significant to be a part of pentest with significant vulnerabilities. Legal authorization is important for assessing the configuration review in regards to damage or indemnification. Once, it is authorized, it is effective to associate with security that the customers or clients can understand the needs of ethical considerations of pentesters.
Privacy issues can be identified herein penetration testing assignment regarding sensitive information about the clients or data listed in the machine. It is significant to high-level assessments, network evaluation and penetration test with more information scanning and security purposes (Shapiro and Stefkovich, 2016). In the context of attacking the network, it is implemented to carry the ethical and legal considerations against cybercrime. “Cyber Security Enhancement Act 2002” is significant that implies life sentences of the hackers as per U.S. statutes against cybercrime. This status is implied to conduct specific considerations against cybercrime. While permission for pen test helps a company’s confidentiality, it is significant to demonstrate the network traffic that is important for the testers (Kshetri, 2017).
“Statute 1030, Fraud and Related Activity in Connection with Computers” are implied to protect the computer without authorization. Such misconducts are applied to legal punishments for pen testers. In this context, statutory and legal implications are needed to conduct protecting the computers and web from hacking and misleading information. The credibility is formed to conduct the testing without interruption in pen-testing. The ethicality of the company needs to engage with in terms of developing the penetration testing approach. In the context of pentetsing methodology, it is important to engage in security considerations to avoid such actions. Legal procedures and information engagement can be applied to design the distribution of pentesting procedure (Schwenket al. 2017).
SOP for task 2
The penetration testing assignment examines that the SOP development process can be introduced to manage the teams to collaborate with the process of documentation for everyone's benefits. It is important to process the significant impact on analyzing and creating SOP regarding the significant impact on organizational development (Prasad, 2016). This is established to enhance the penetration tester by developing and identifying clear business indications within the process. This process mentioned in the penetration testing assignment is significant to reduce the vulnerability and processes regarding individual documentations through SOP.
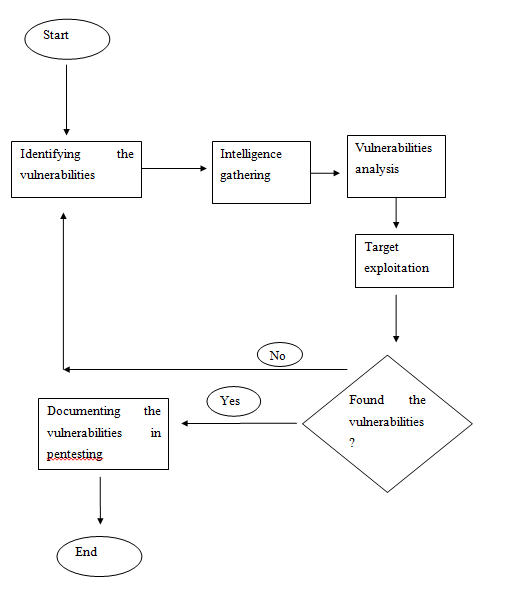
Figure 1: SOP
(Source: Created by Author)
Step 1: Developing list of processes
This step mentioned in the penetration testing assignment signifies that developing decisions is significant regarding efficient pen-testing. For creating group work, it is important to process the lists that are required to combine the similar process by enhancing the entire exercises efficiently (Kshetri, 2017). It is important to ensure the team development and engagement in determining the week’s involvements.
Step 2: Planning the process
Establishing document management is significant for planning the process that will be done in task 2. Intelligence gathering, target profiling and vulnerability identifications are the steps to list for planning in the next task.
Step 3: Collecting information on SOP
As per the view of Vega et al. (2017), collecting information is outlined to establish the documentation process regarding SOP content. Information regarding group work and data identification is engaged to find the organizational operations. Post exploitation is involved in helping the workers regarding pentest.
Step 4: Witting, reviewing and publishing SOP
It is clear herein penetration testing assignment that writing the draft can be evaluated to engage the information that is needed to complete the review of the document. As per the view of Fielder et al. (2016), it is significant to look over the document review. The standard operations are written to check the vulnerability and procedures to be reviewed. It is significant to ensure data security and organizational completeness. It is established to confirm the process to be positive or negative. Maintaining and incorporating are required to distribute the captured automatically.
Step 5: Maintaining SOP over time
A relevant individual has a basis of processes regarding explaining the right documentation frequently with process involvement. Facilitating the periodic review process is included to engage and notify the functions automatically. Facilitating the periodic review can have a successful engagement to review the tasks and manual work.
An SOP is significant that is involved how the organizations can define and promote the manual work implementation with time. The instructions for pentest is defined and listed to provide superficial regulations and routine operation checking. It is significant to engage the regulatory framework that is found by designing the vulnerability in cyberspace. It helps the co-workers regarding daily routine that is consists of worker's involvement and operations to analyze the post-exploitation phases (Dua and Du, 2016). The pentest process is involved in creating the documentation through SOP. All the steps are discussed in the present scenario of penetration testing assignment to create and evolve the guidelines regarding the phases.
Decision Making Tree for Task 2
Decision-making tree refers to types of supervised machine learning options that can be divided accordingly using a binary tree. It can be explained to establish the decisions by expanding the plant regarding managing the introductory part by including organizational chance particularly. According to Badaet al. (2019), pentesing is a method that is evolved to grow rapidly by introducing product engagement. It is uncertain about exploiting the investments and issues regarding developing the expansions that are required to move promptly with uncertainties. The decision-tree approach is useful by illustrating work progress in the next task. The next task initiated in the penetration testing assignment has a significant approach to help the organization with routine analysis in the next task. The framework is useful to forecast the activities through decision trees (Shapiro and Stefkovich, 2016).
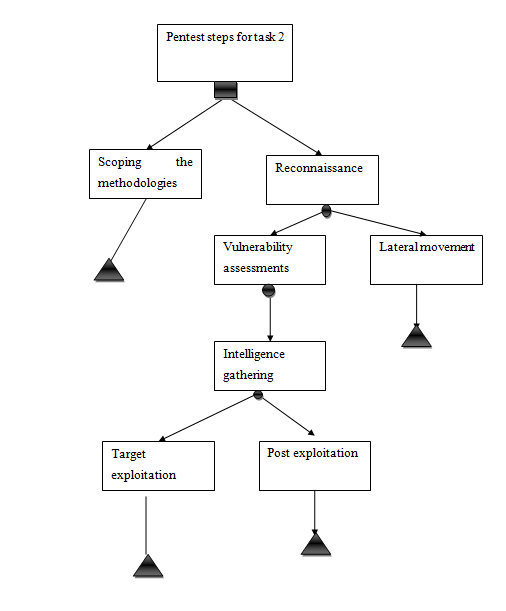
Figure 2: Decision-making tree
(Source: Created by Author)
Decision-making tree is produced to evaluate strong penetration steps for task 2, where the task needs to be analyzed as automated considerations regarding phase. According to the research on penetration testing assignment the best pen testing includes the scoping the methodology and reconnaissance as primary steps regarding uncovering the vulnerabilities. Testing scope ensures positive decisions regarding encouraging the business processes disruptions (Kshetri, 2017). Identifying the scopes is needed to state over the business disruptions regarding engaging the assessments. Gathering information for vulnerability identification and lateral movements is authorized regarding representing the research in a general way. Attractive services are included to target other operating systems about operations system in public. Vulnerability assessment is important decisions regarding pentesting. Intelligence gathering is a significant stage that has either option of target exploitation and post-exploitation. Risks are associated by providing network development vulnerabilities based on the types and risks (Walsh et al. 2018). The pentesting is based on providing the architectural details regarding code-signing certificates that can be incorporated to exploit the identified vulnerabilities. Exploitation and communication through disruptions will be focused on task 2 that is needed over time by network management and administrations. The pen test has technical detail in descriptive specialitiesfor fixing the details of intelligence gathering activities.
Decision-makers can be influenced by evaluating this decision-making tree by undertaking the activities regarding decision-making (Shapiro and Stefkovich, 2016). It is significantly produced to encourage network management activity regarding vulnerability identification and portfolio development. Several testing results will appear to identify a proper development of tools in exploiting the technical teams. Testing is the last part when exploitation is measured in business executives and technical teams. It is important to identify and represent the technical development for fixing the security issues by discovering the penetration tests with the group (Newhouse et al. 2017). It is discovered to establish business development in terms of avoiding technical faults. In terms of cybersecurity, it is significant to understand the determined actions of security risks in targeted systems. Options should be measured to discover and generate understandable actions results for business leaders.
Conclusion
The study prepared in the penetration testing assignment has specified the pentest methodologies to involve in the statuary and legal considerations. The task is focused on interpreting the pentest methodologies regarding the SOP process and decision-making tree. By designing SOP and decision-making tree, it is significant to identify the key areas regarding worker’s routine and daily involvements in pentest. The portfolio is measured to gather intelligence to undertake the methodologies and routine operations for the next task. It is found in the above context of penetration testing assignment that ethical and statutory considerations are required in terms of penetration methodologies by designing SOP and decisions. It is effectively identified that pentest methodology is used to consider the aspects regarding activities used in the SOP.
Reference list
Archibald, J.M. and Renaud, K., 2019. Refining the PoinTER “human firewall” pentesting framework. Information & Computer Security.
Bacudio, A.G., Yuan, X., Chu, B.T.B. and Jones, M., 2011. An overview of penetration testing. Penetration testing assignment International Journal of Network Security & Its Applications, 3(6), p.19.
Bada, M., Sasse, A.M. and Nurse, J.R., 2019. Cyber security awareness campaigns: Why do they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Dua, S. and Du, X., 2016. Data mining and machine learning in cybersecurity.CRC press.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support approaches for cyber security investment. Decision support systems, 86, pp.13-23.
Kshetri, N., 2017. Blockchain's roles in strengthening cybersecurity and protecting privacy. Telecommunications policy, 41(10), pp.1027-1038.
Newhouse, W., Keith, S., Scribner, B. and Witte, G., 2017.National initiative for cybersecurity education (NICE) cybersecurity workforce framework. NIST Special Publication, 800, p.181.
Prasad, P., 2016. Mastering Modern Web Penetration Testing.Packt Publishing Ltd.
Schwenk, J., Niemietz, M. and Mainka, C., 2017. Same-origin policy: Evaluation in modern browsers. In 26th {USENIX} Security Symposium ({USENIX} Security 17) (pp. 713-727).
Shapiro, J.P. and Stefkovich, J.A., 2016. Ethical leadership and decision making in education: Applying theoretical perspectives to complex dilemmas. Routledge.
Van den Hout, N.J., 2019. Standardised penetration testing? Examining the usefulness of current penetration testing methodologies.
Vega, E.A.A., Orozco, A.L.S. and Villalba, L.J.G., 2017. Benchmarking of pentesting tools. Penetration testing assignment International Journal of Computer, Electrical, Automation, Control and Information Engineering, 11(5), pp.602-605.
Walsh, T., Ainsworth, S., Armstong, S., Walker, A., Hodgkinson, S.H.J. and Williams, D., 2018, September.Development of a pen-side diagnostic test for liver fluke infection in cattle and sheep.In British Cattle Conference (p. 15).












